Patents
Literature
371results about How to "Clearly marked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
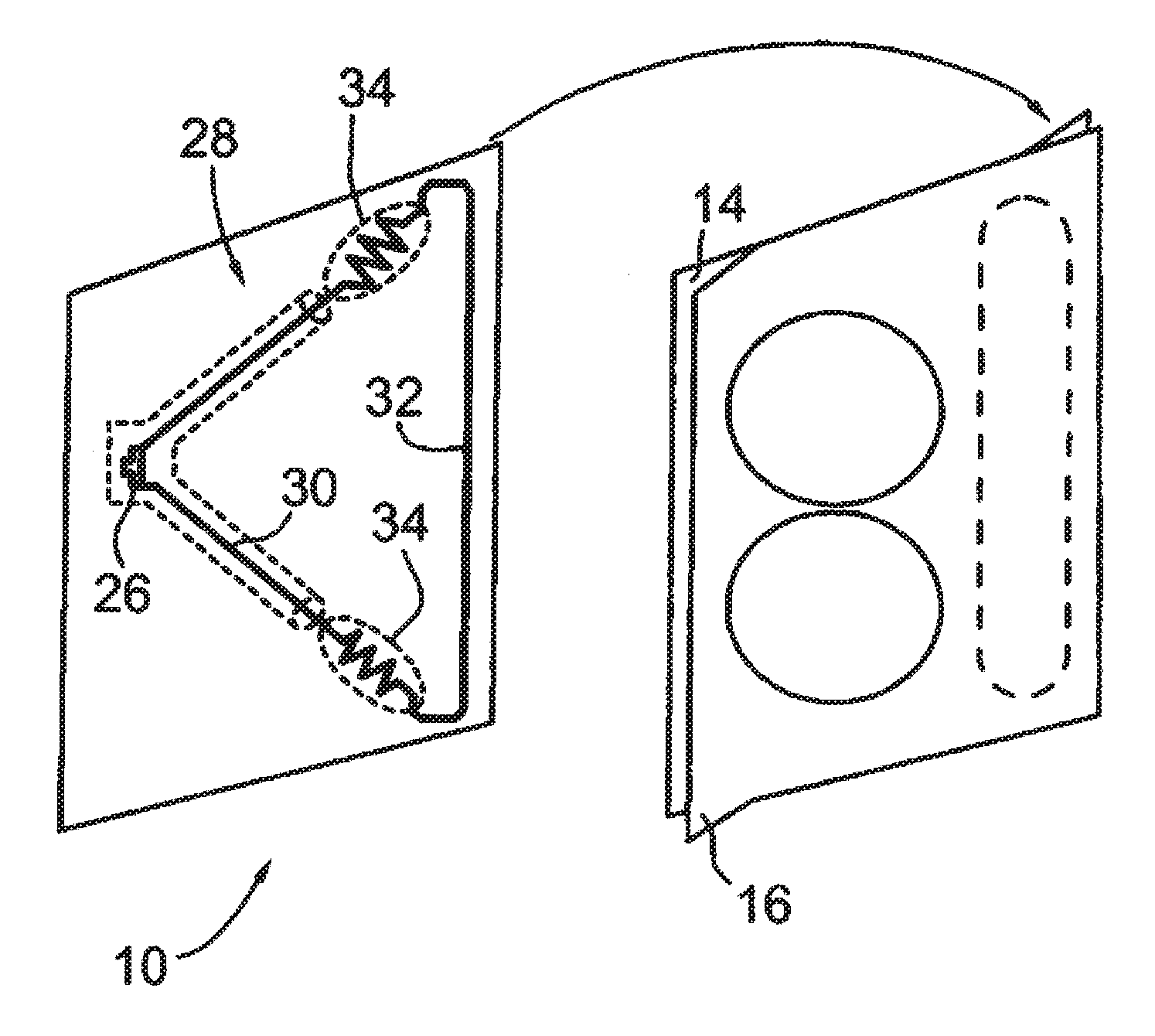
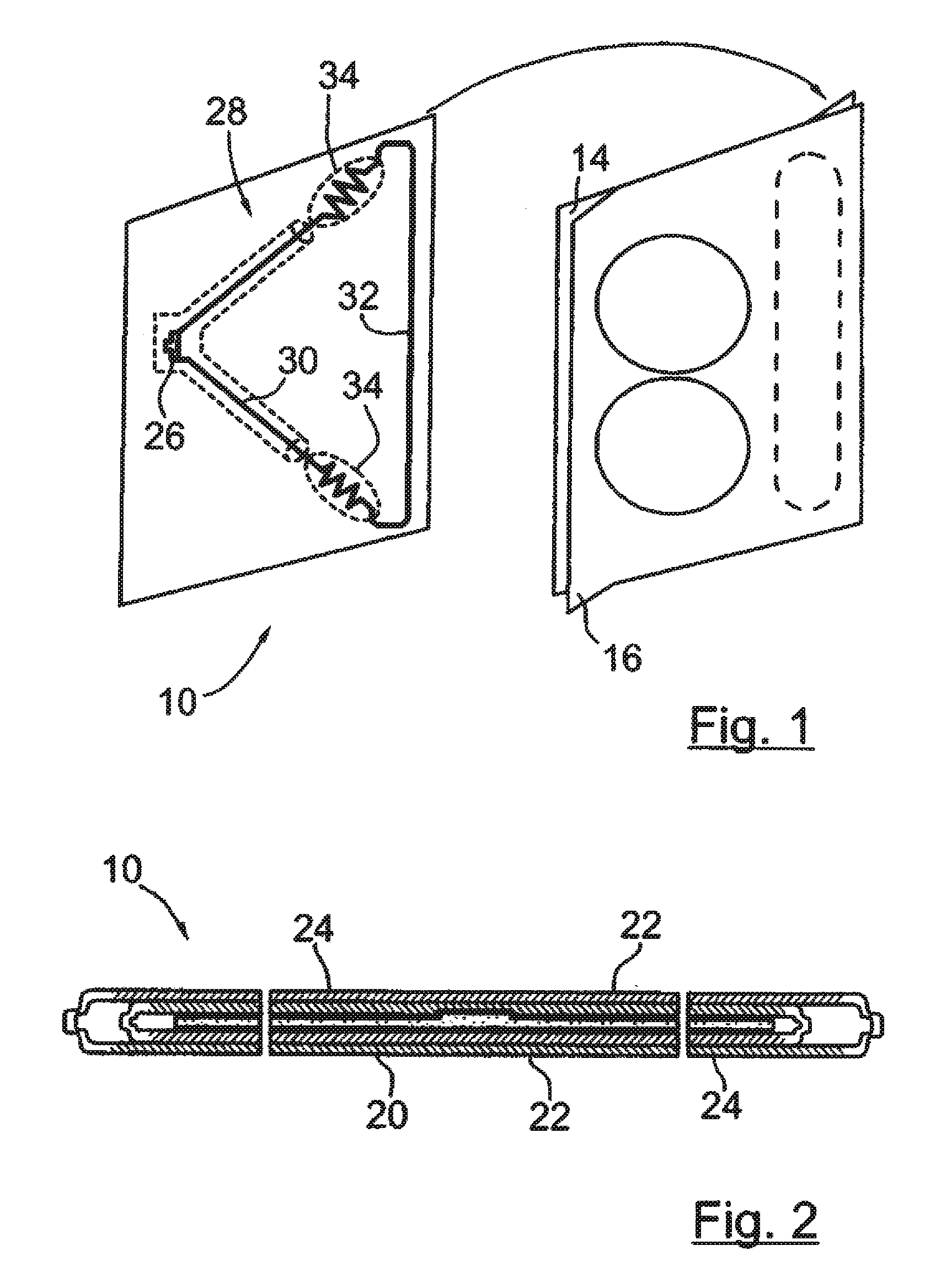
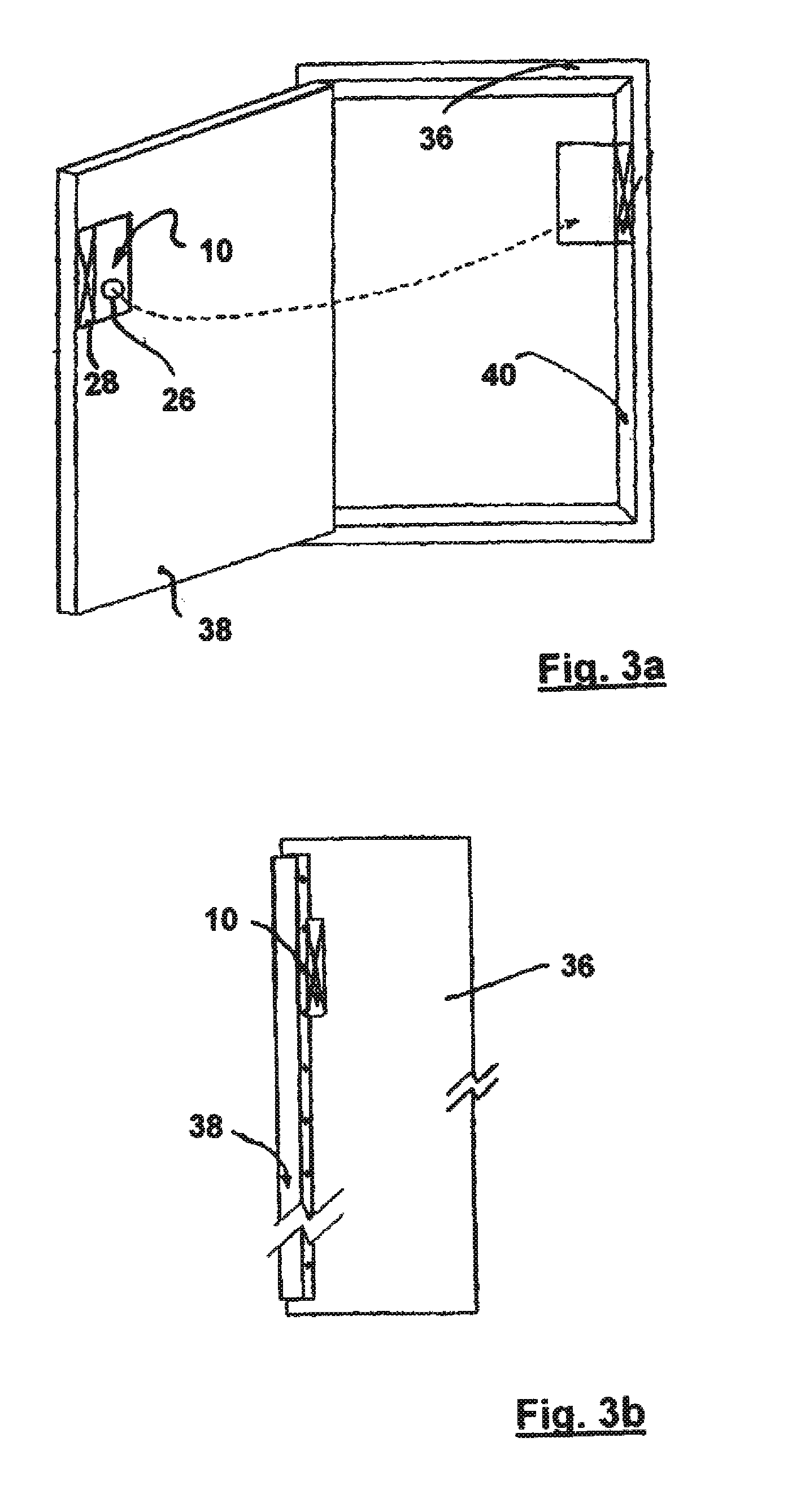
Passive tamper-resistant seal and applications therefor
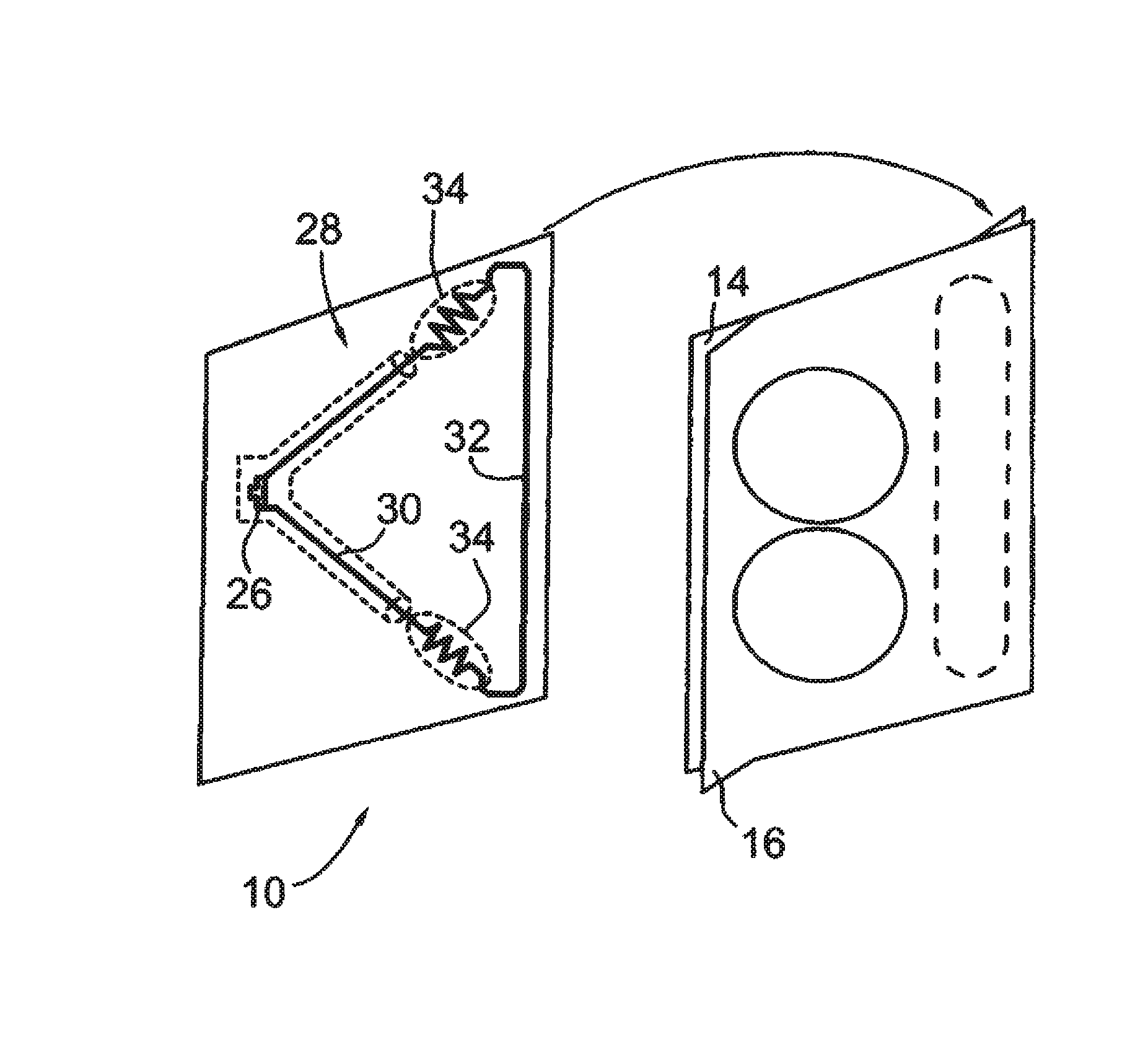
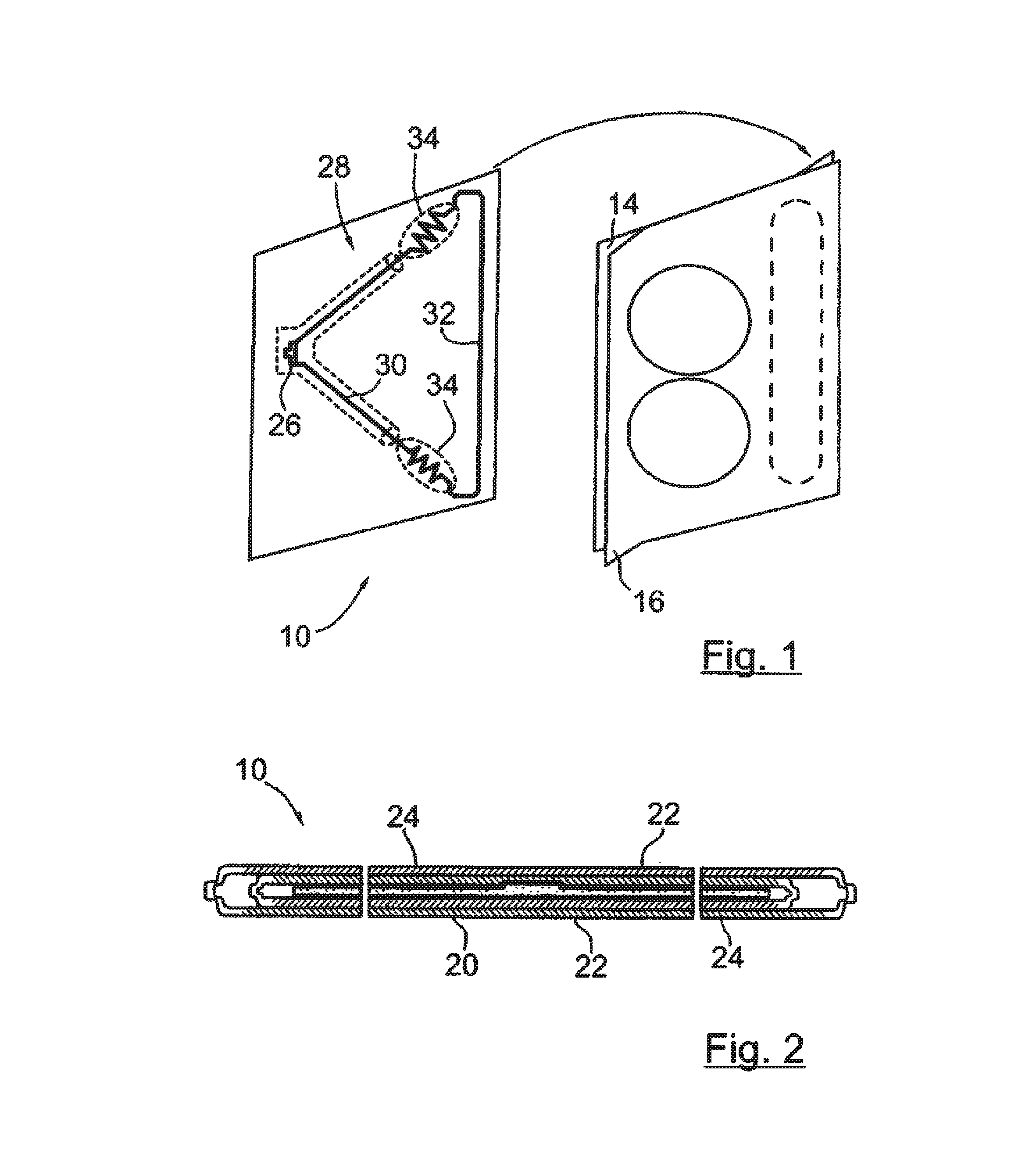
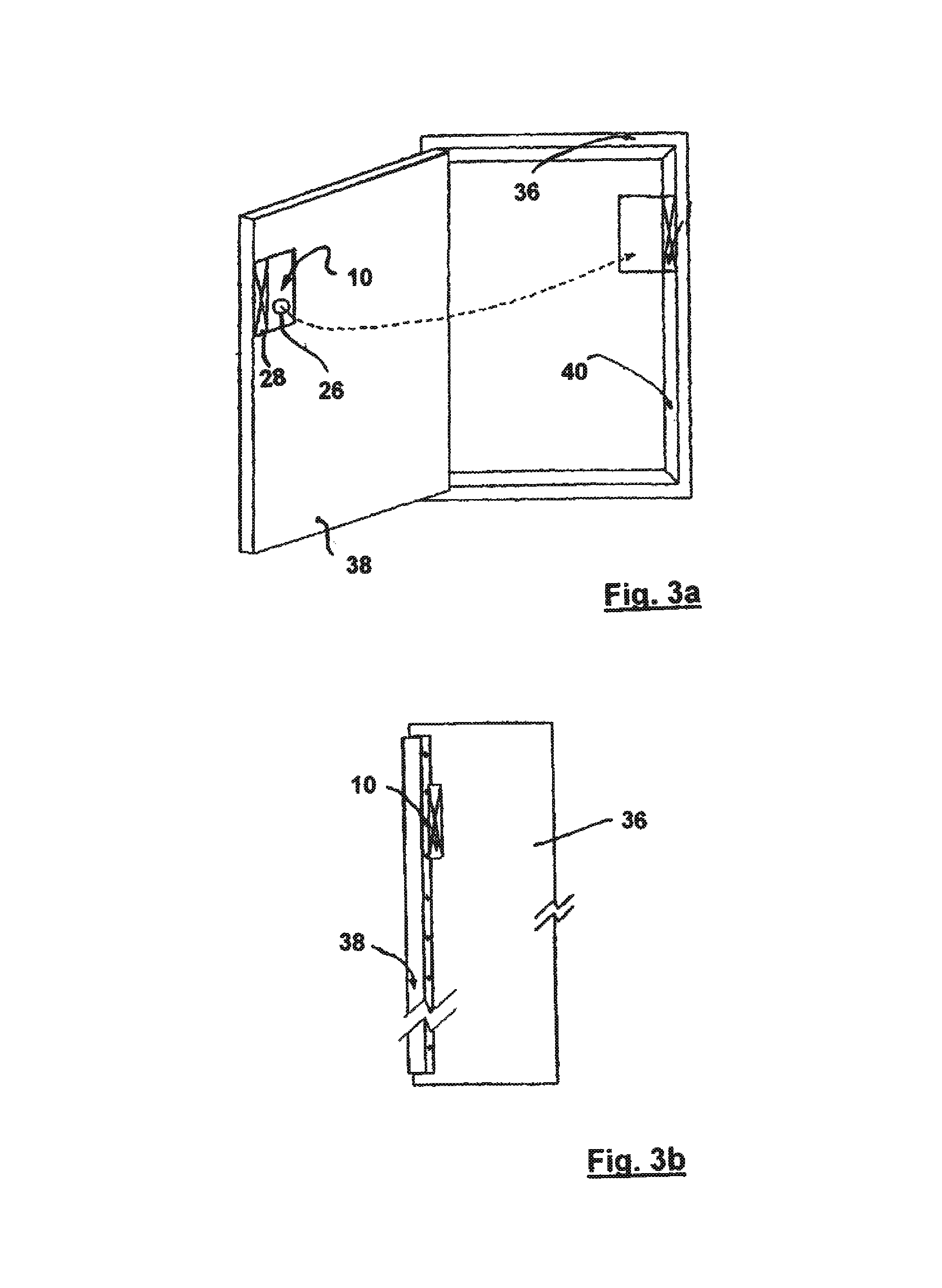
A radio frequency identification seal comprises an antenna including a main antenna portion and at least one break-away portion and an RFID tag coupled and tuned to the antenna. The RFID tag outputs a signature in response to a scanning signal when tuned to the antenna.
Owner:COVELEY SOLBYUNG
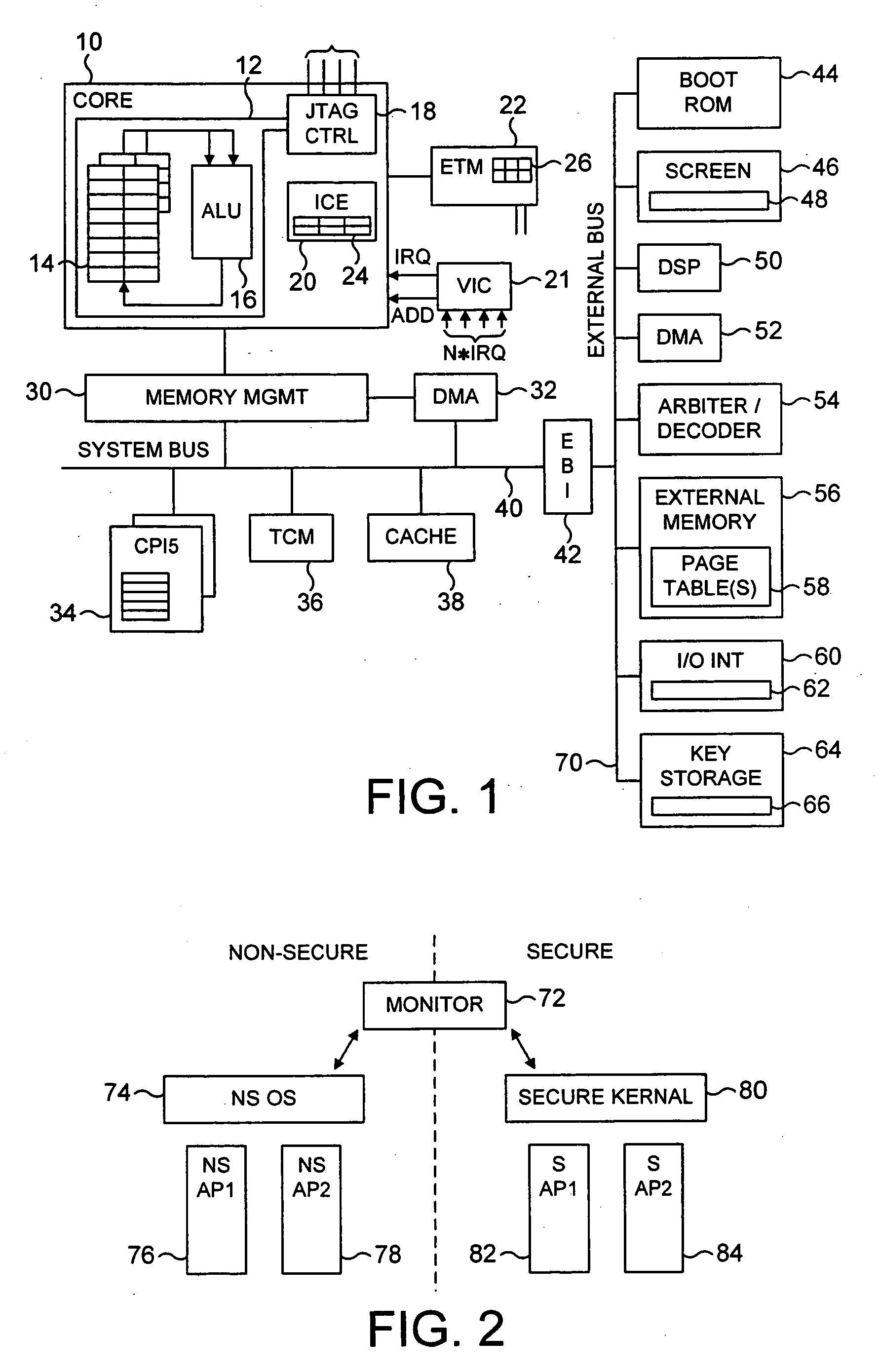
Apparatus and method for managing access to a memory
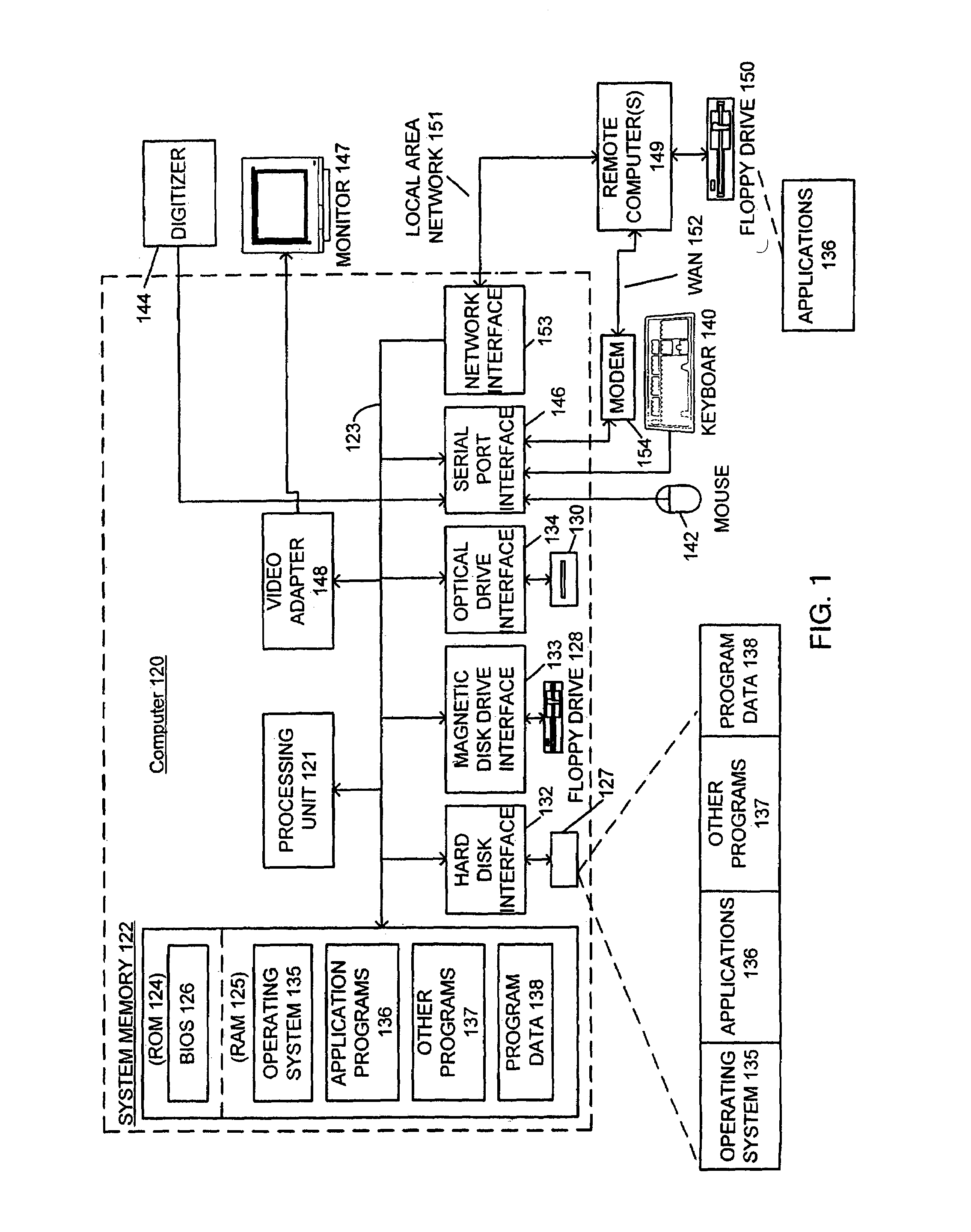
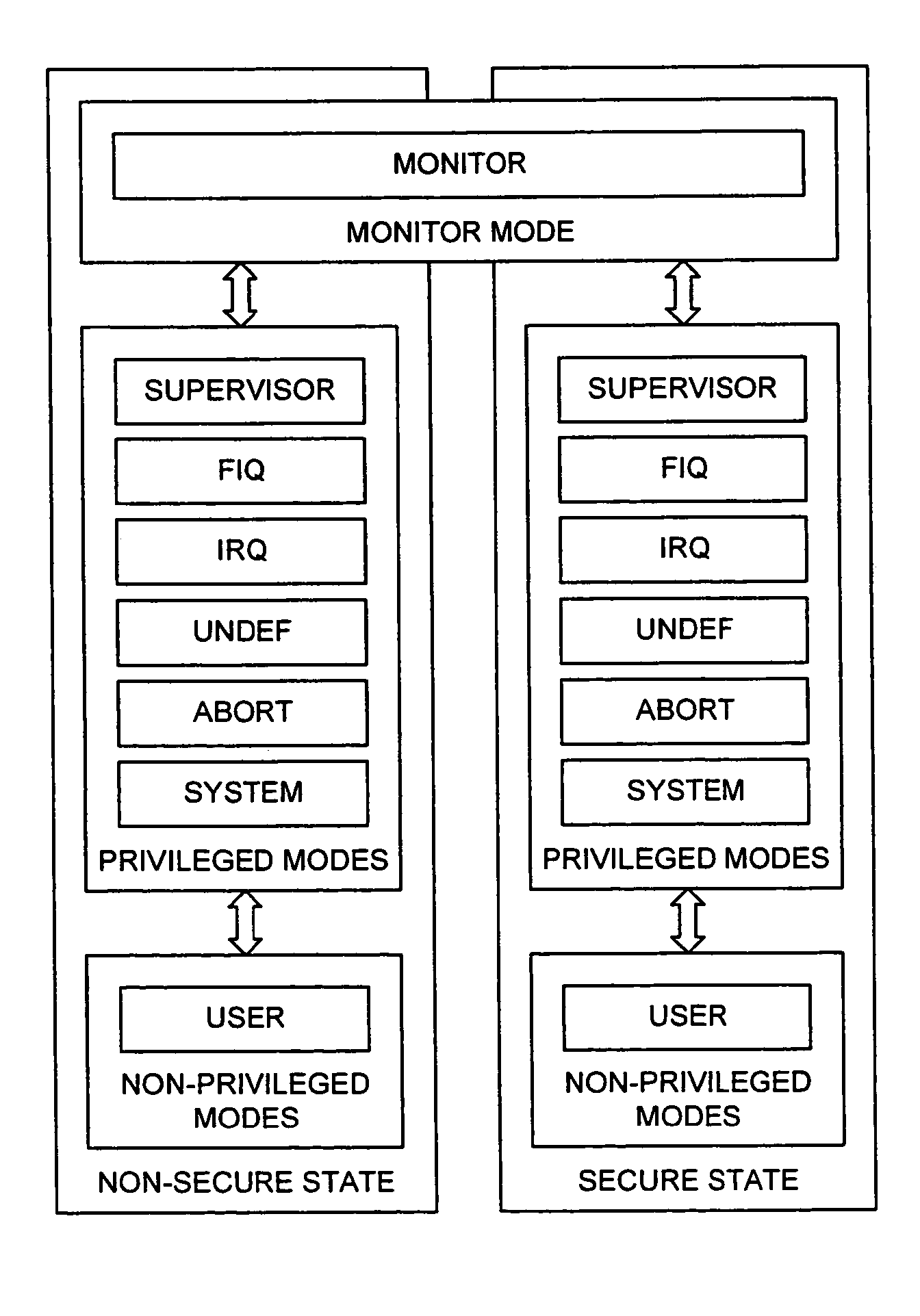
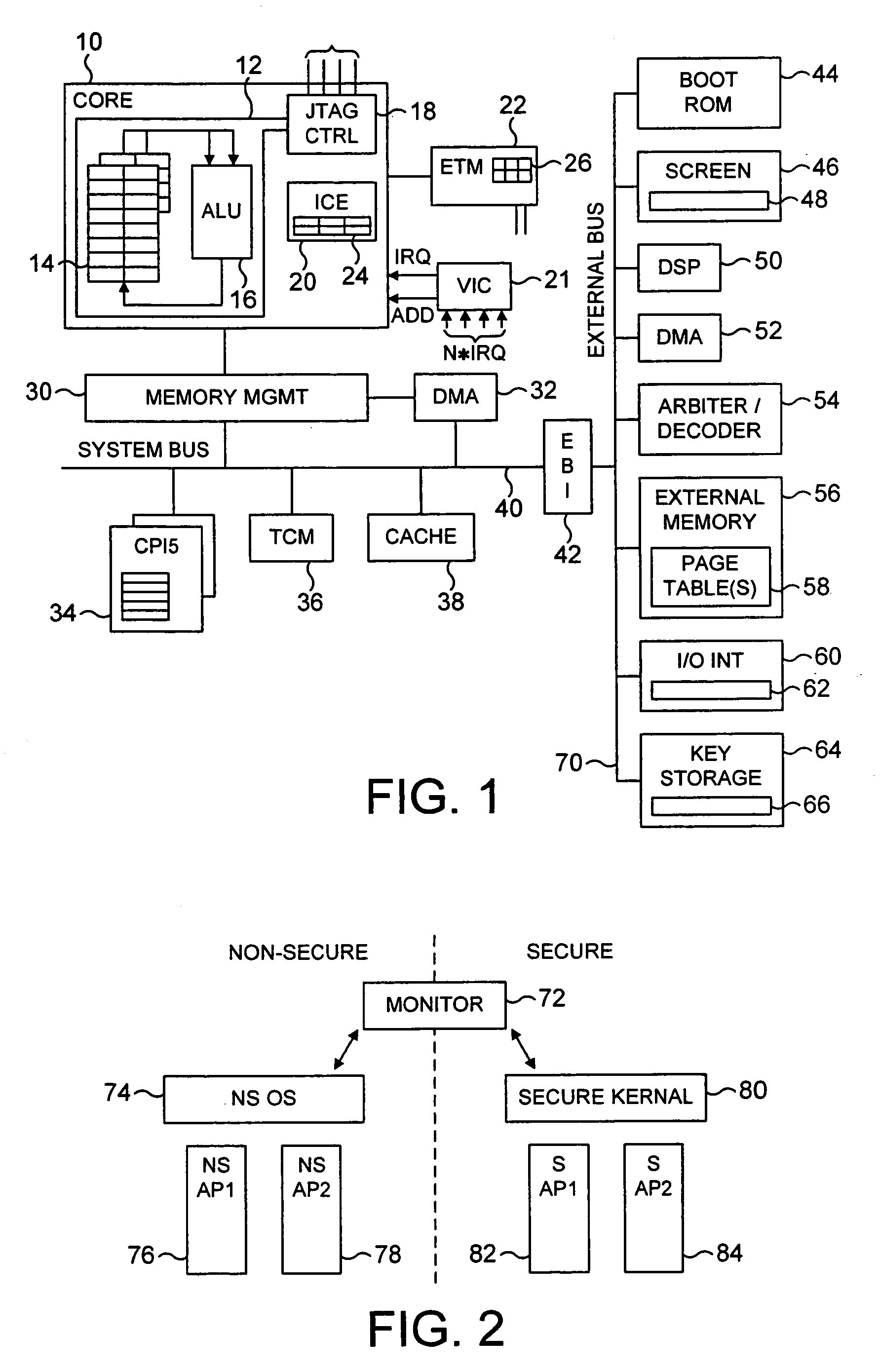
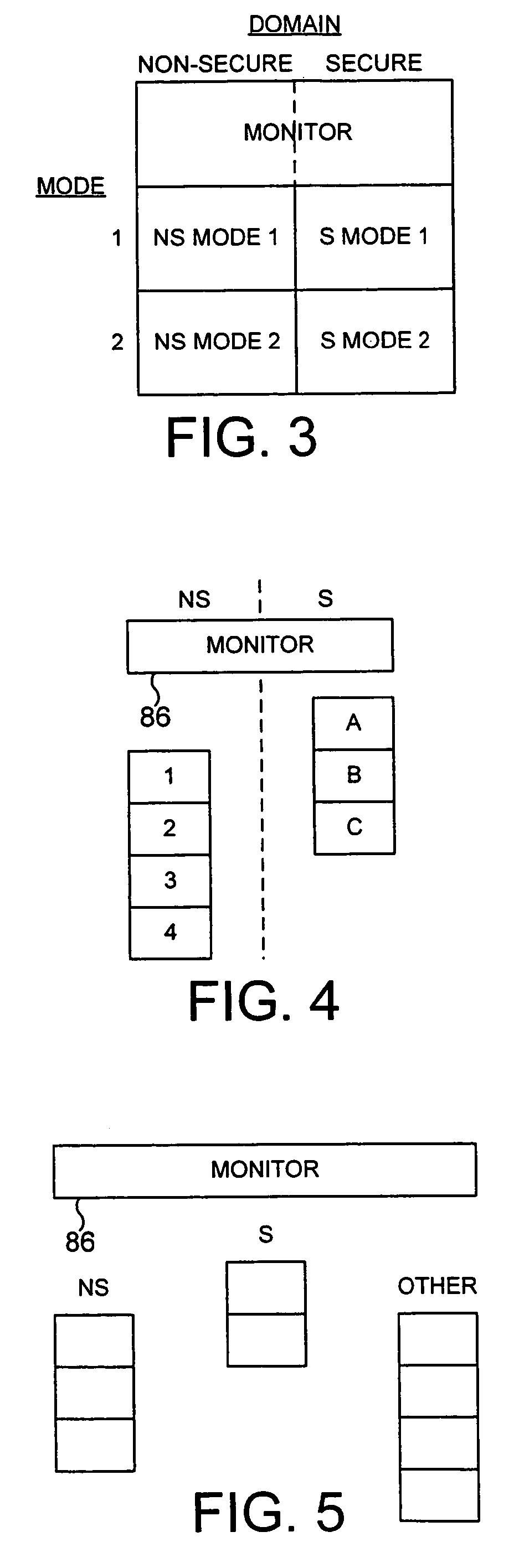
ActiveUS20040177269A1Performance is not affectedEasy to operateMemory architecture accessing/allocationDigital data processing detailsManagement unitMultiple modes
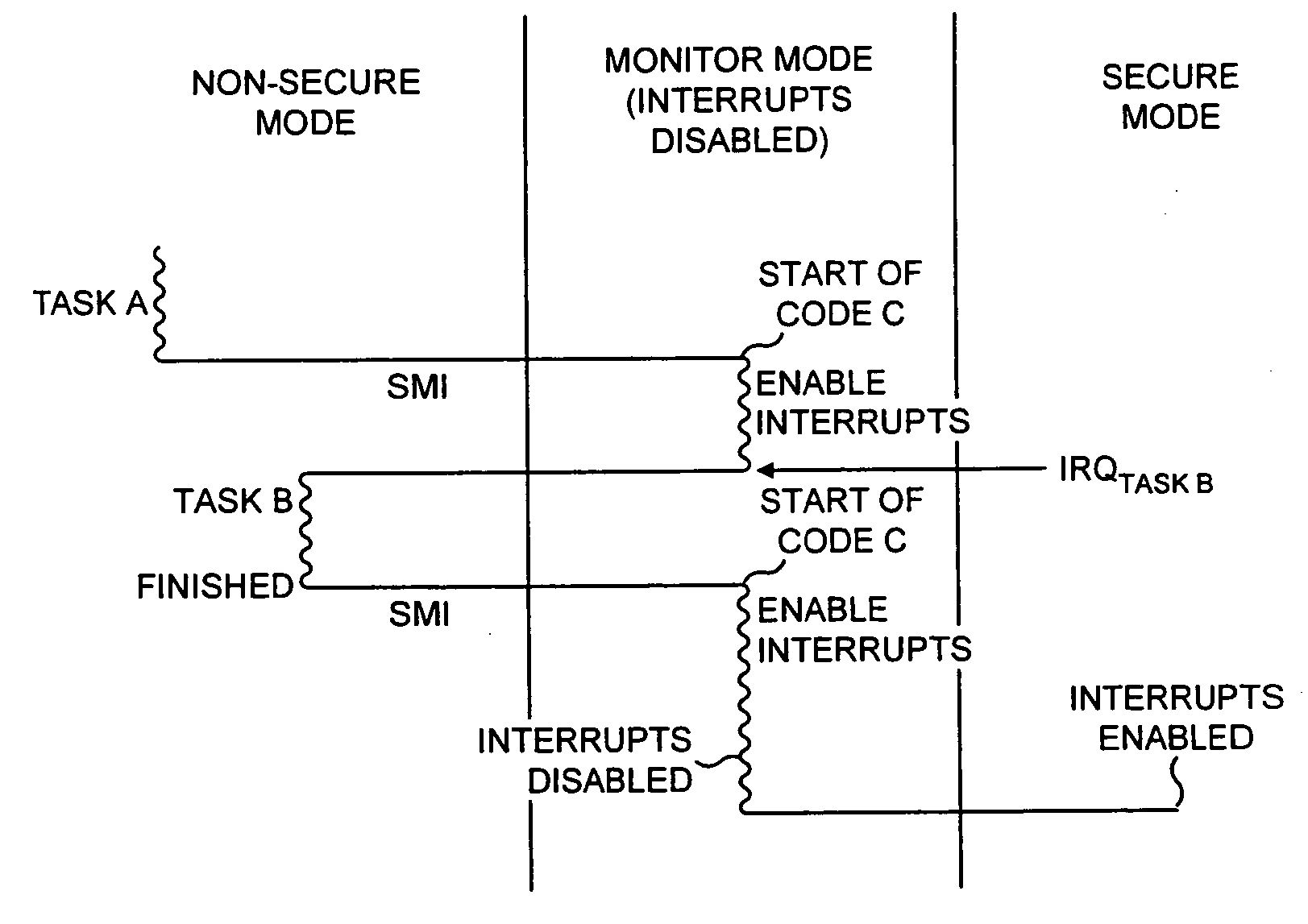
The present invention provides a data processing apparatus and method for managing access to a memory within the data processing apparatus. The data processing apparatus comprises a processor operable in a plurality of modes and a plurality of domains, said plurality of domains comprising a secure domain and a non-secure domain, said plurality of modes including at least one non-secure mode being a mode in the non-secure domain and at least one secure mode being a mode in the secure domain, said processor being operable such that when executing a program in a secure mode said program has access to secure data which is not accessible when said processor is operating in a non-secure mode. Further, a memory is provided for storing data required by the processor, and consists of secure memory for storing secure data and non-secure memory for storing non-secure data. The memory further contains a non-secure table and a secure table, the non-secure table being within the non-secure memory and arranged to contain for each of a number of first memory regions an associated descriptor, and the secure table being within the secure memory and arranged to contain for each of a number of second memory regions an associated descriptor. When access to an item of data in the memory is required by the processor, the processor issues a memory access request, and a memory management unit is provided to perform one or more predetermined access control functions to control issuance of the memory access request to the memory. The memory management unit comprises an internal storage unit operable to store descriptors retrieved by the memory management unit from either the non-secure table or the secure table, and in accordance with the present invention the internal storage unit comprises a flag associated with each descriptor stored within the internal storage unit to identify whether that descriptor is from the non-secure table or the secure table. By this approach, when the processor is operating in a non-secure mode, the memory management unit is operable to perform the predetermined access control functions for the memory access request with reference to access control information derived from the descriptors in the internal storage unit retrieved from the non-secure table. In contrast, when the processor is operating in a secure mode, the memory management unit is operable to perform the predetermined access control functions for the memory access request with reference to access control information derived from the descriptors in the internal storage unit retrieved from the secure table. This approach enables different descriptors to be used for the control of accesses to memory in either the secure domain or the non-secure domain, whilst enabling such different descriptors to co-exist within the memory management unit's internal storage unit, thereby avoiding the requirement to flush the contents of such an internal storage unit when the operation of the processor changes from the secure domain to the non-secure domain, or vice versa.
Owner:ARM LTD
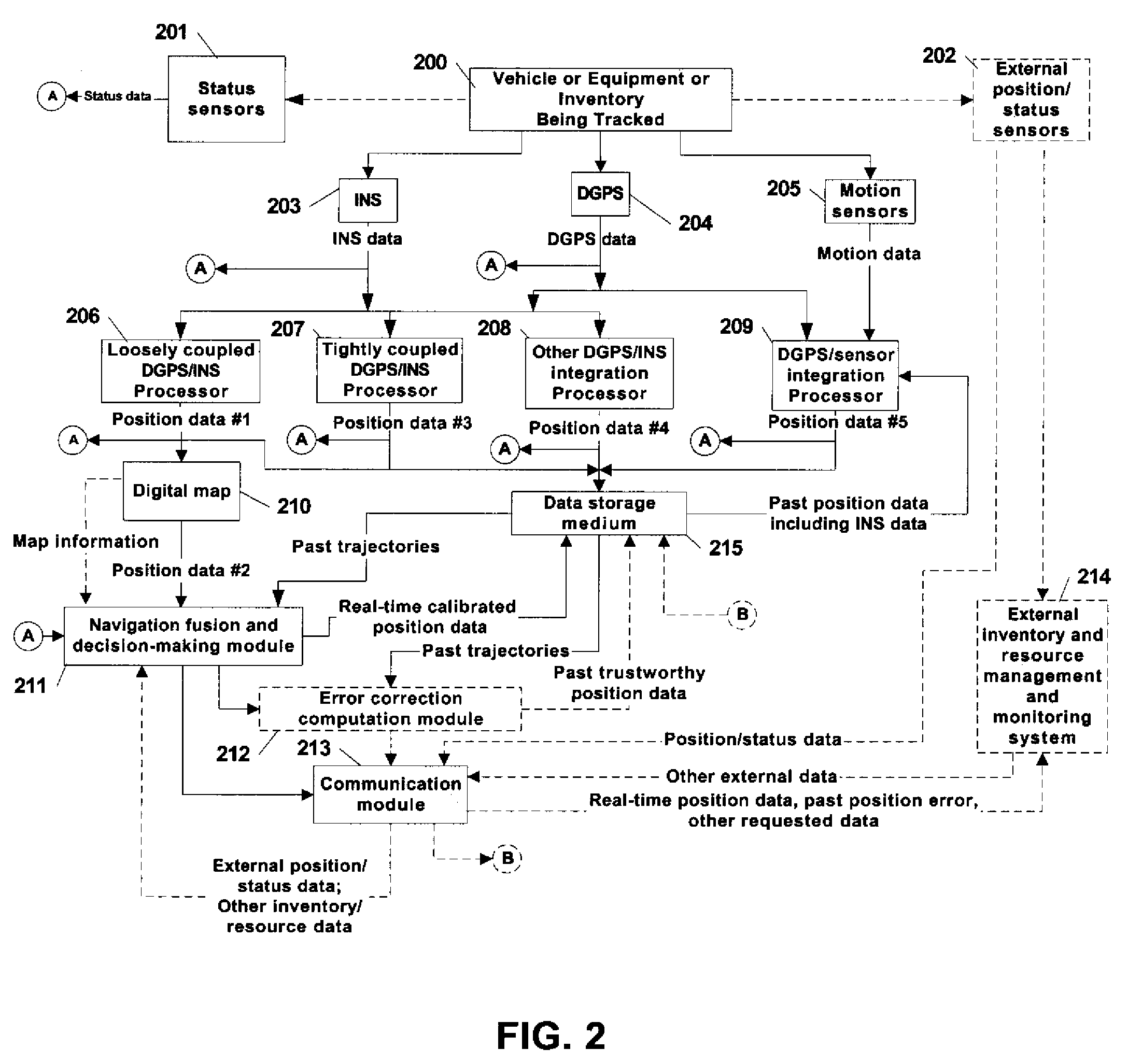
Automated asset positioning for location and inventory tracking using multiple positioning techniques
InactiveUS7646336B2Improve accuracyImprove data accuracyDirection finders using radio wavesPosition fixationCorrection algorithmPosition error
Owner:MI JACK PRODS
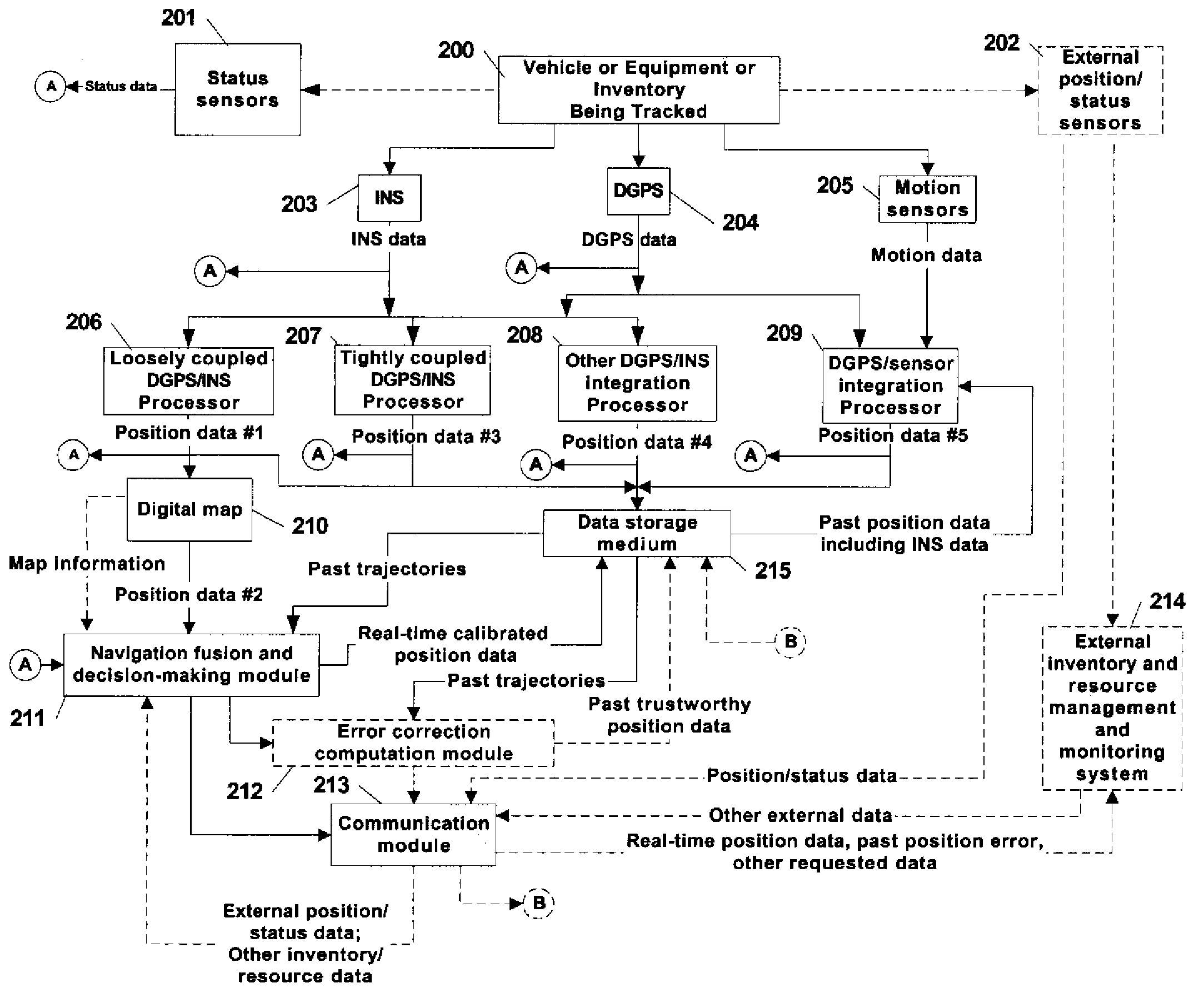
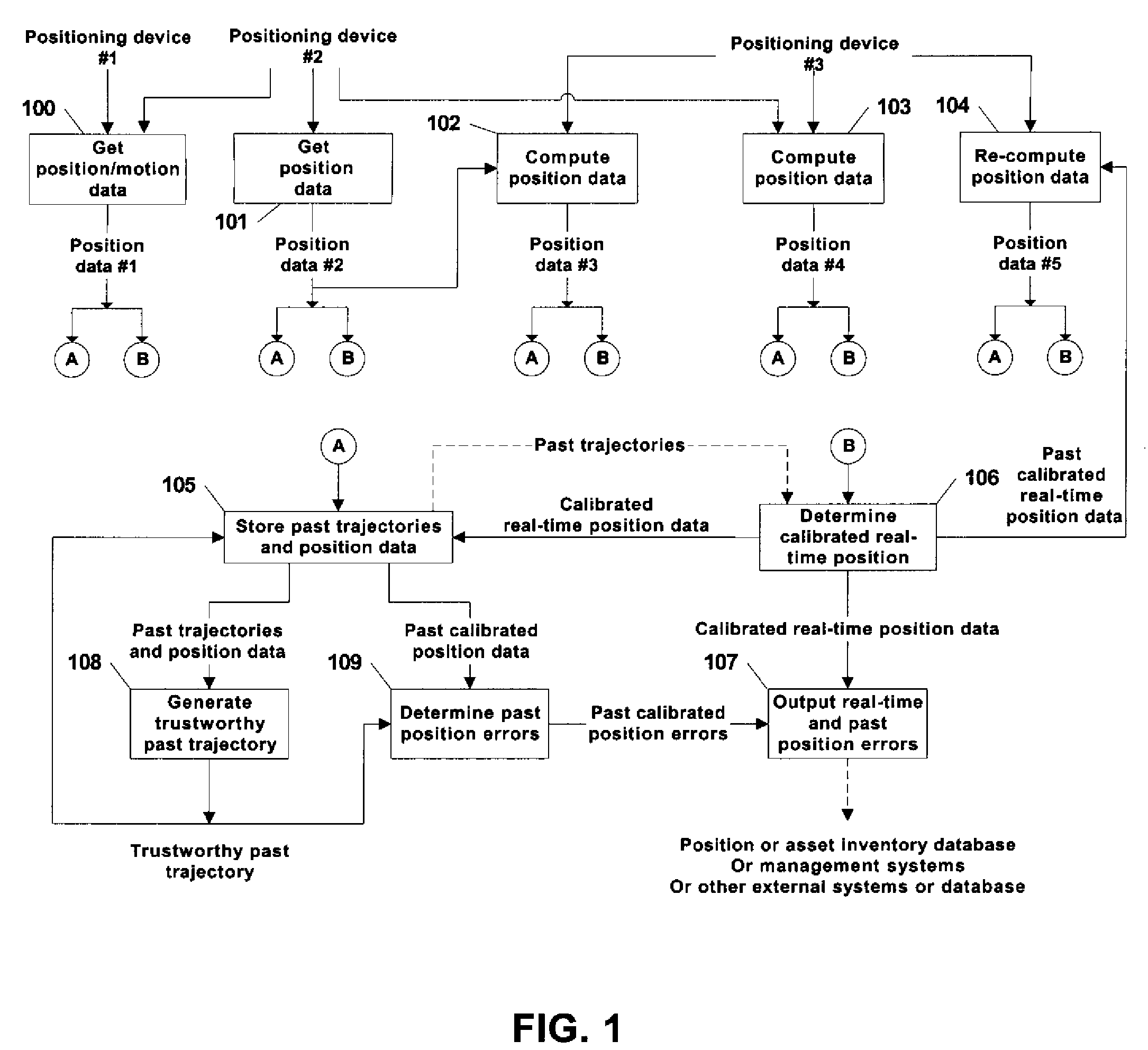
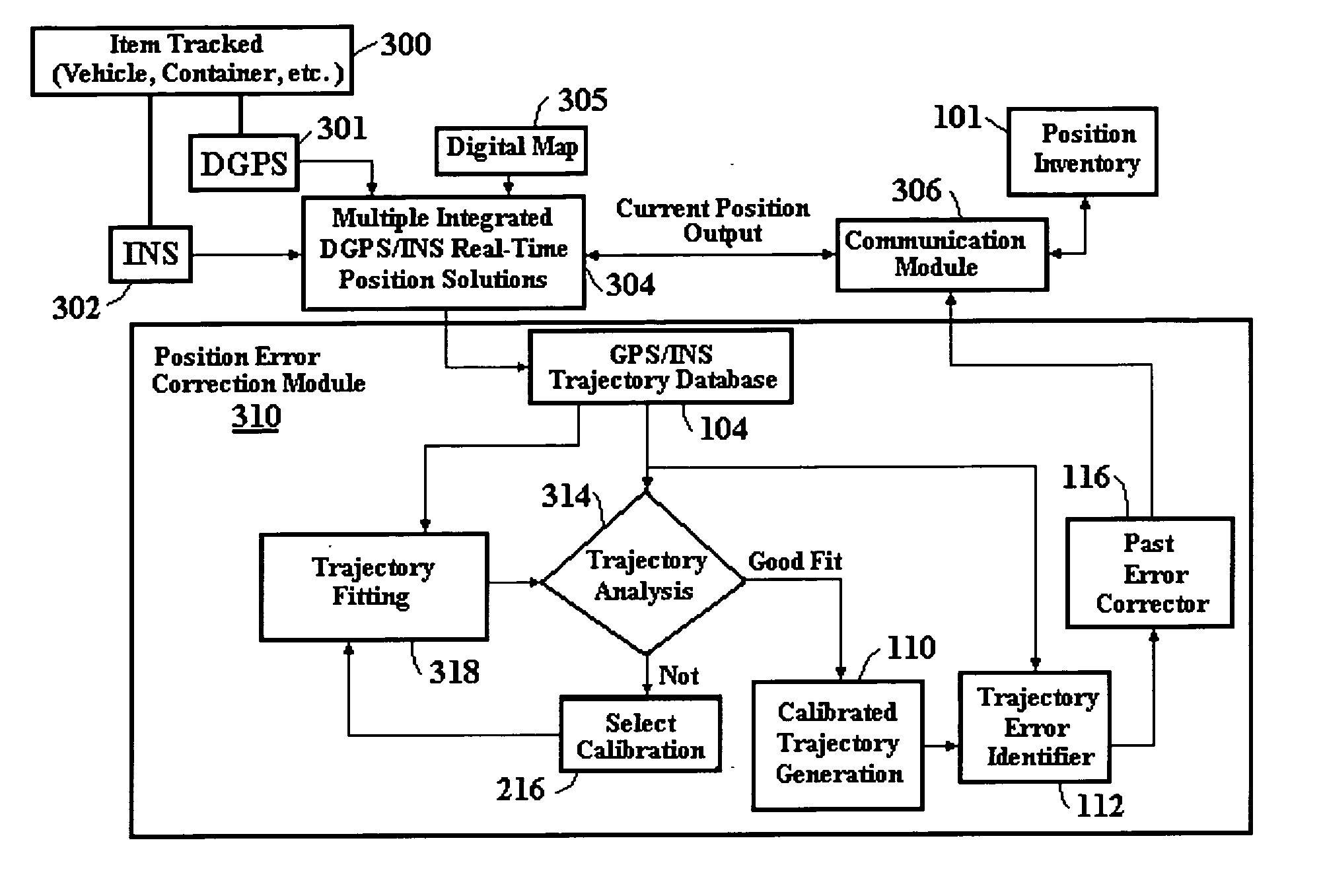
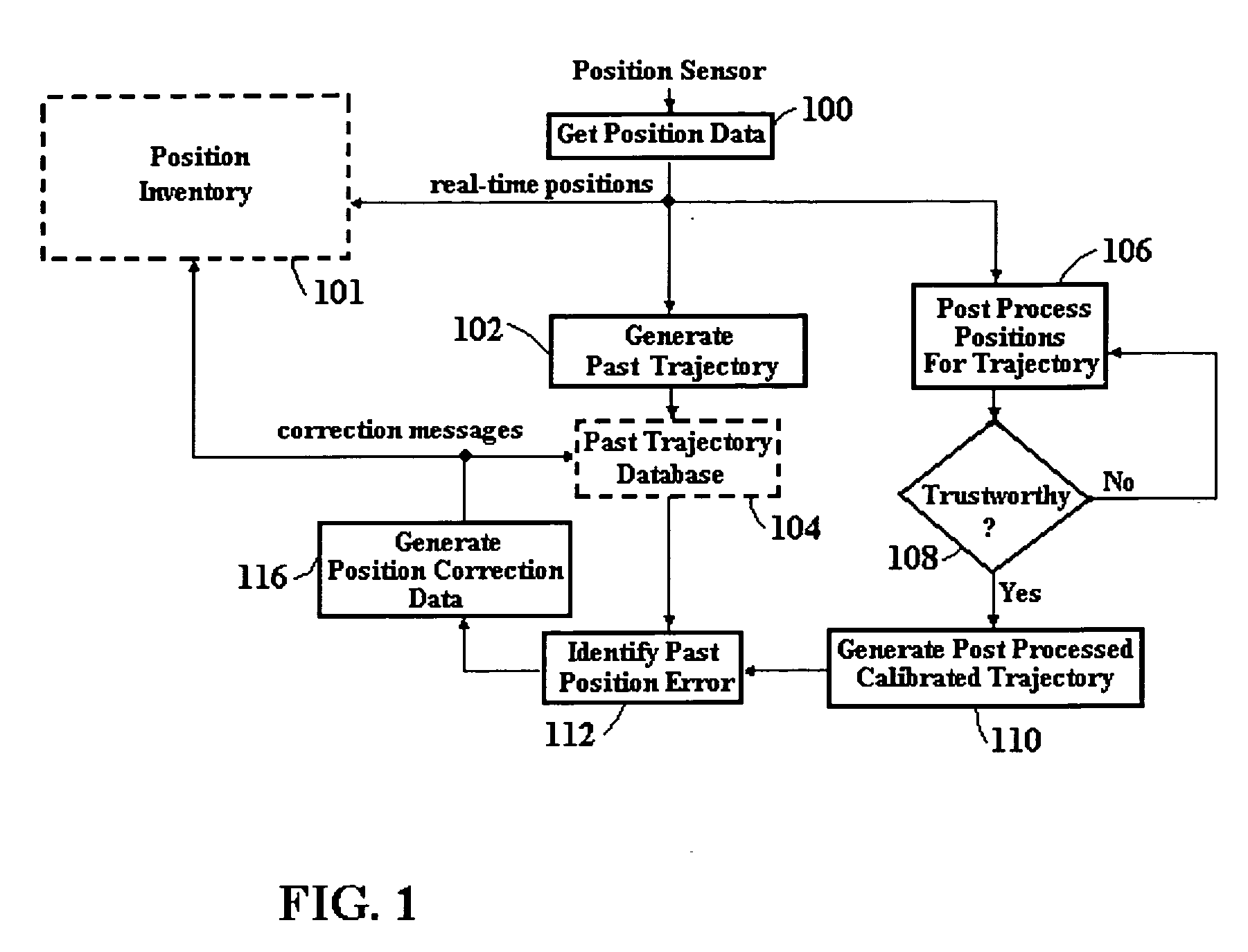
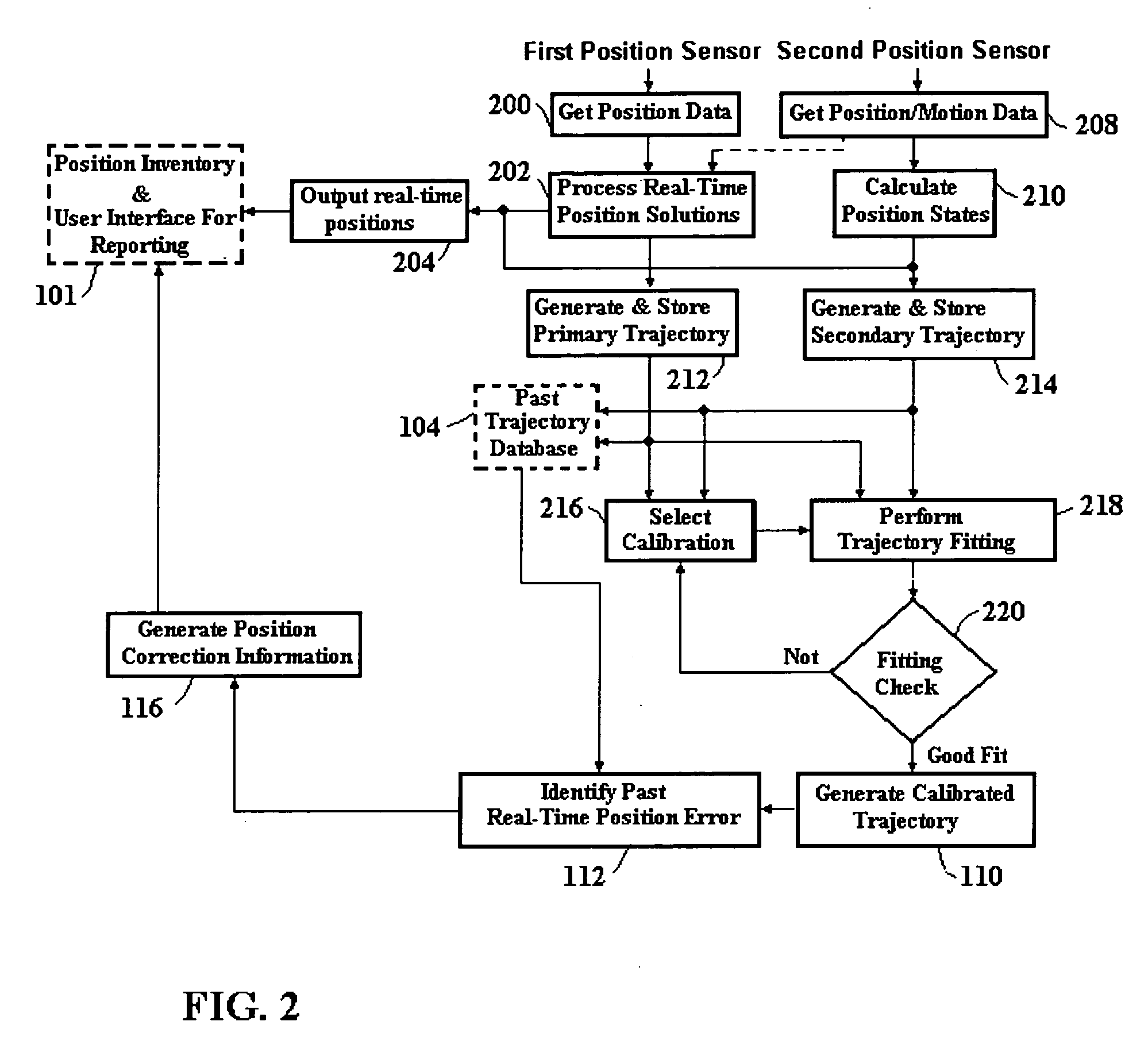
Automatic past error corrections for location and inventory tracking
ActiveUS20070010940A1Increase probabilityClearly markedNavigational calculation instrumentsPosition fixationPosition errorYard (length)
A system is provided for tracking and maintaining an inventory of location of containers that are stored on cargo ships or in a container yard. The system includes one or more sensors, such as GPS and INS sensors for obtaining real-time position information, as well as a processor configured to automatically provide post processing to recover lost data and to correct erroneous data, such as when real-time position signals are blocked or distorted, the post processing performed by estimating trajectories and correcting the location errors. Post-processed positioning techniques are continuously applied to the stored position data to iteratively determine calibrated position locations to provide calibrated second trajectory segments in a real-time fashion. The calibrated second trajectories are then used to identify the errors in the past real-time position data as soon as a segment of the second calibrated trajectory becomes statistically trustworthy. Corrections can be automatically made in inventory locations stored in a database to correct position errors for the containers.
Owner:MI JACK PRODS
Disturbance free update of data
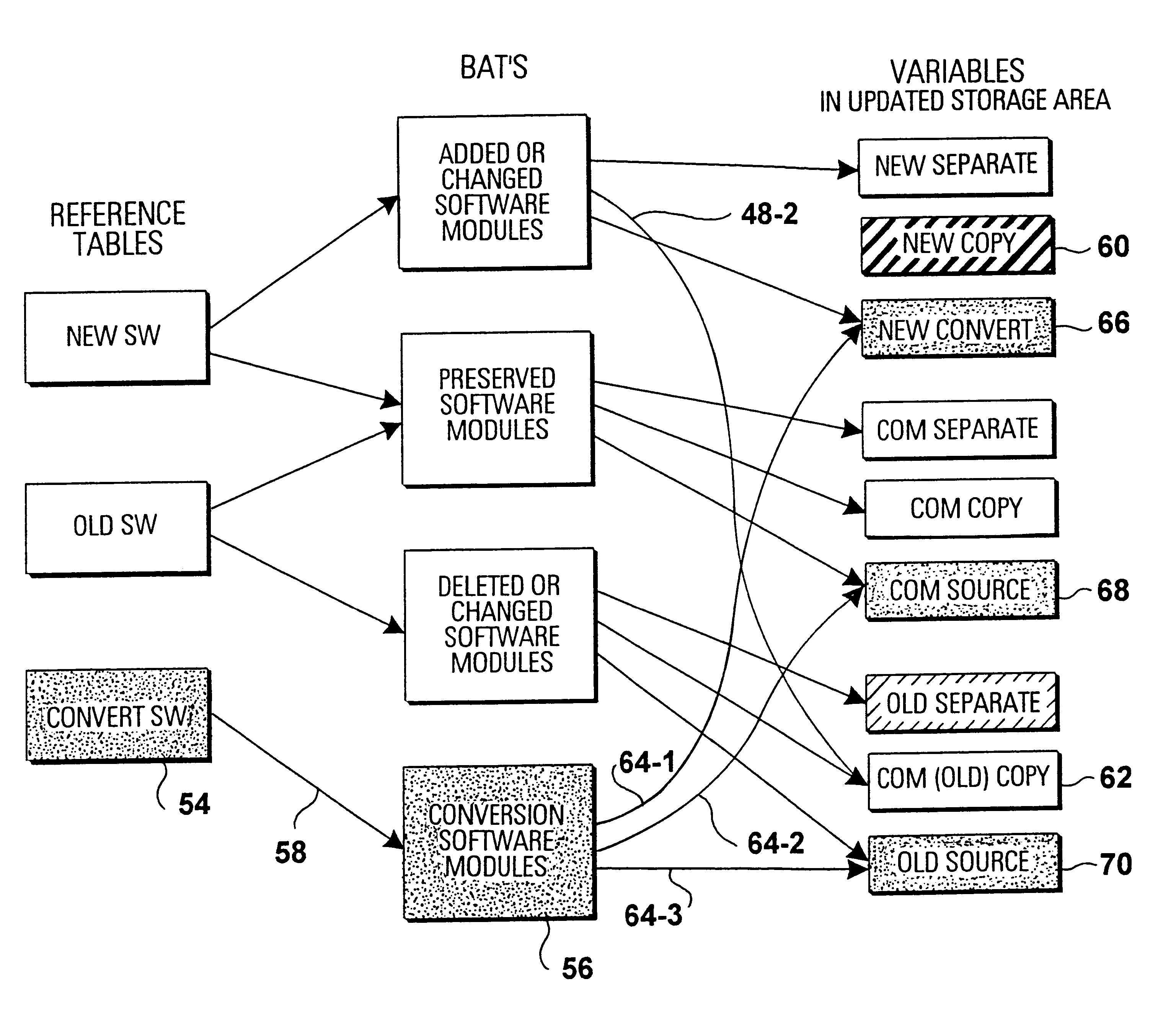
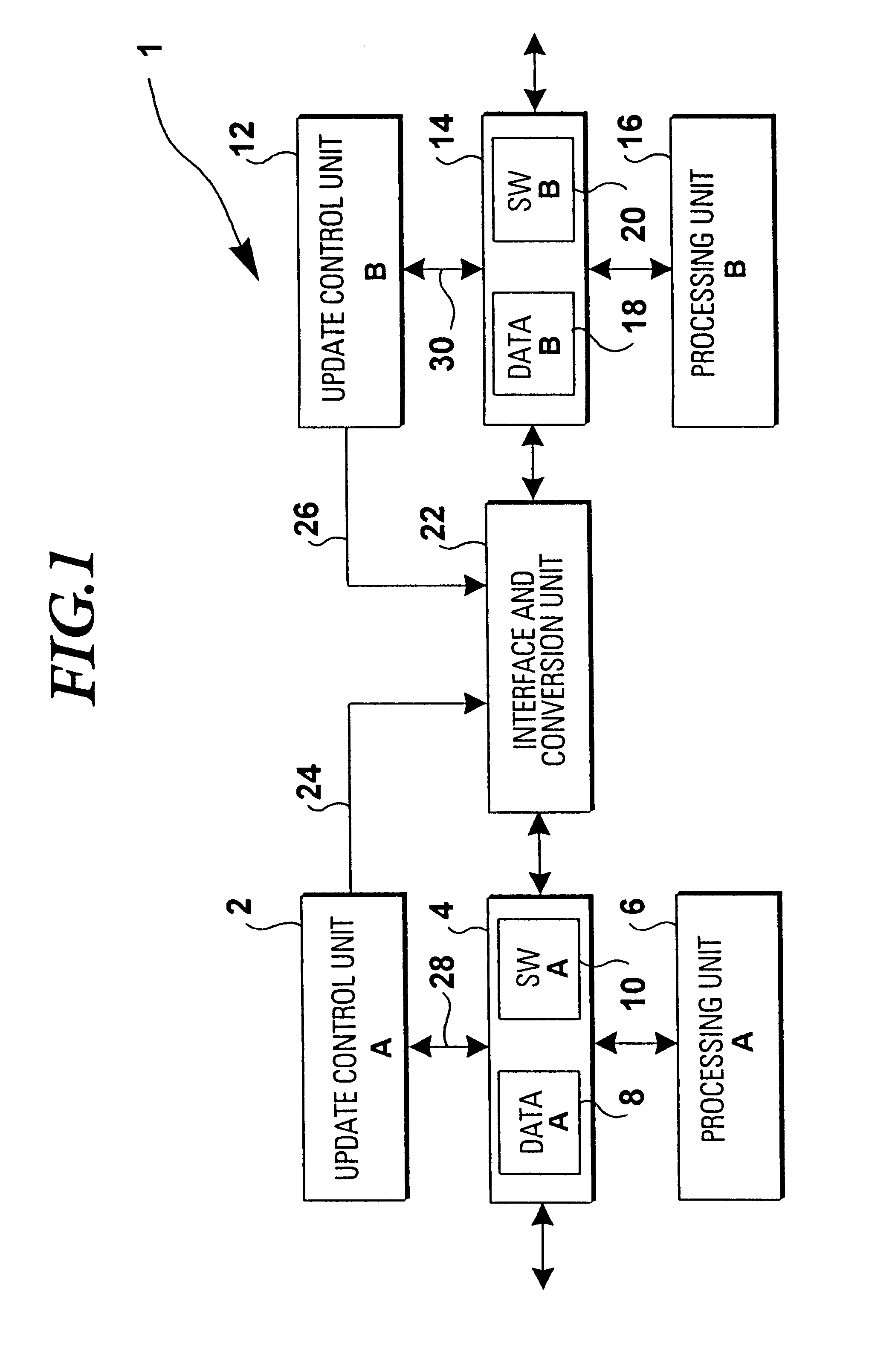
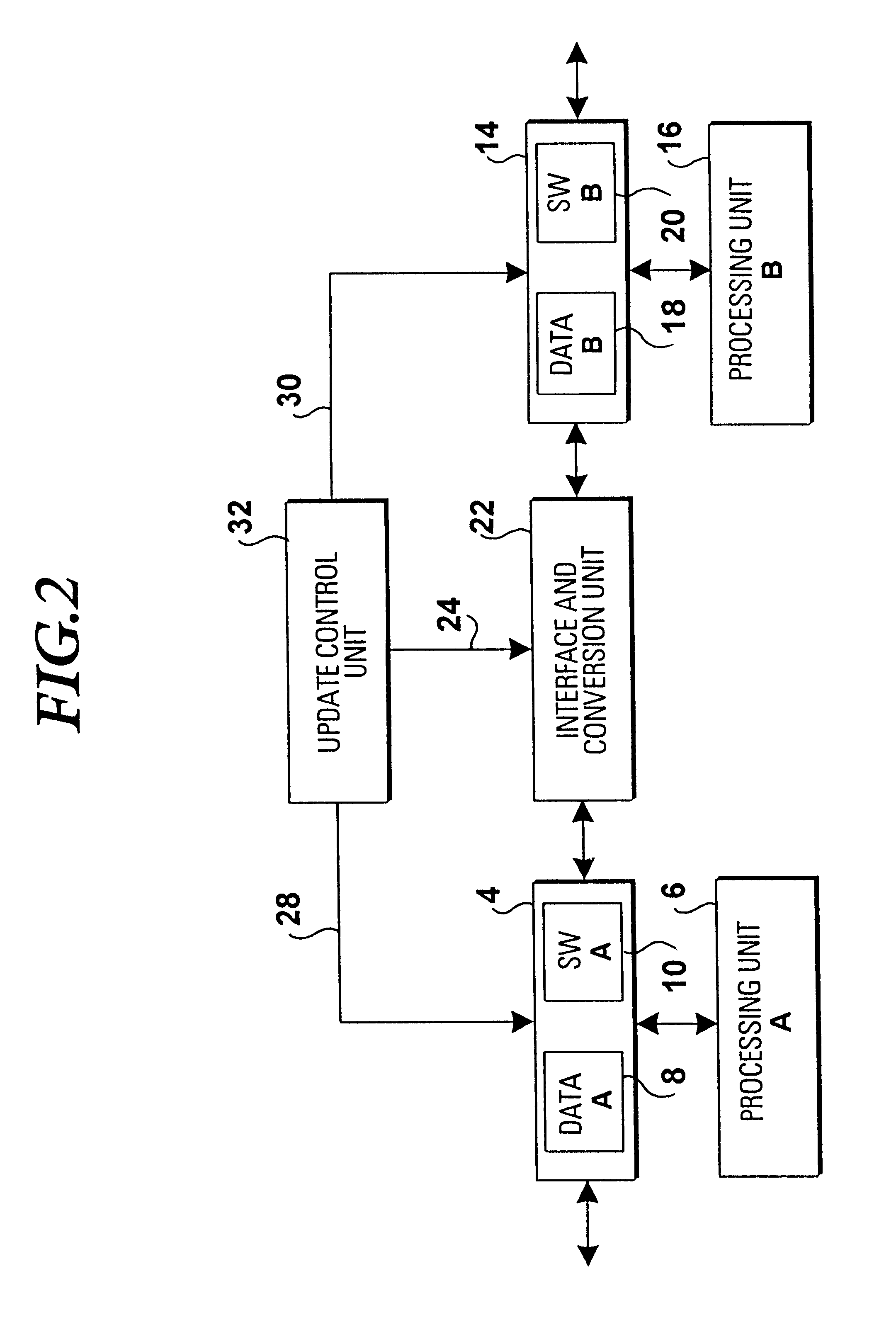
InactiveUS6347396B1Improve efficiencyReduce distractionsData processing applicationsSoftware engineeringOriginal dataData transmission
To improve the efficiency for an update process in a software processing device with a plurality of memory partitions (4,14) it is proposed to continue the execution of old software on original data stored in a first memory partition (4). In case the same state for data of old and new software is achieved (S4) an instant switch of services to the new software as far as the same state is achieved (S5) takes place. This processing is repeated (S6) until no data to be transferred remains (S6) in the first memory partition. Thus, the present invention allows for a considerable improvement of the update efficiency with reduced disturbances during data transfer.
Owner:TELEFON AB LM ERICSSON (PUBL)
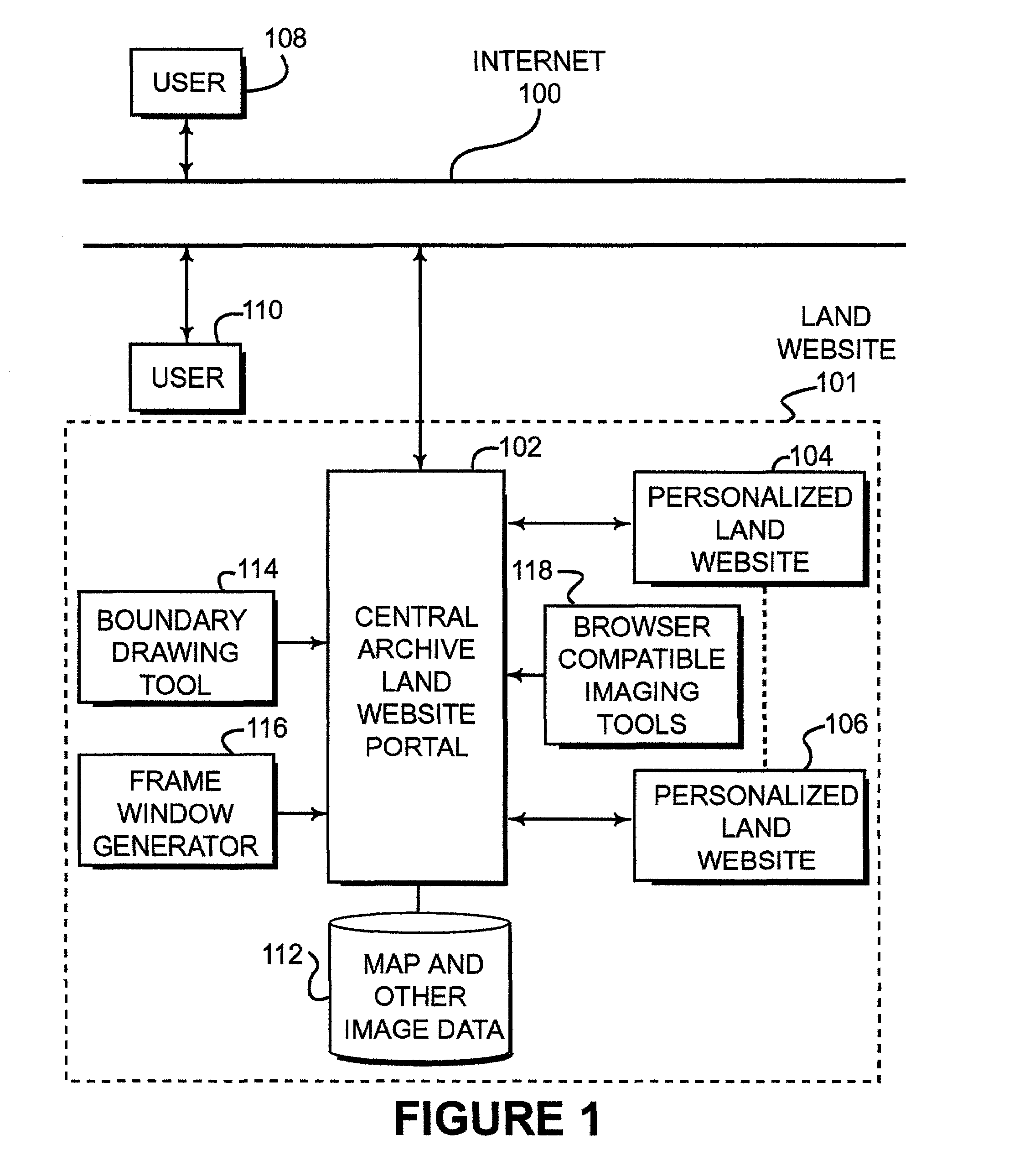
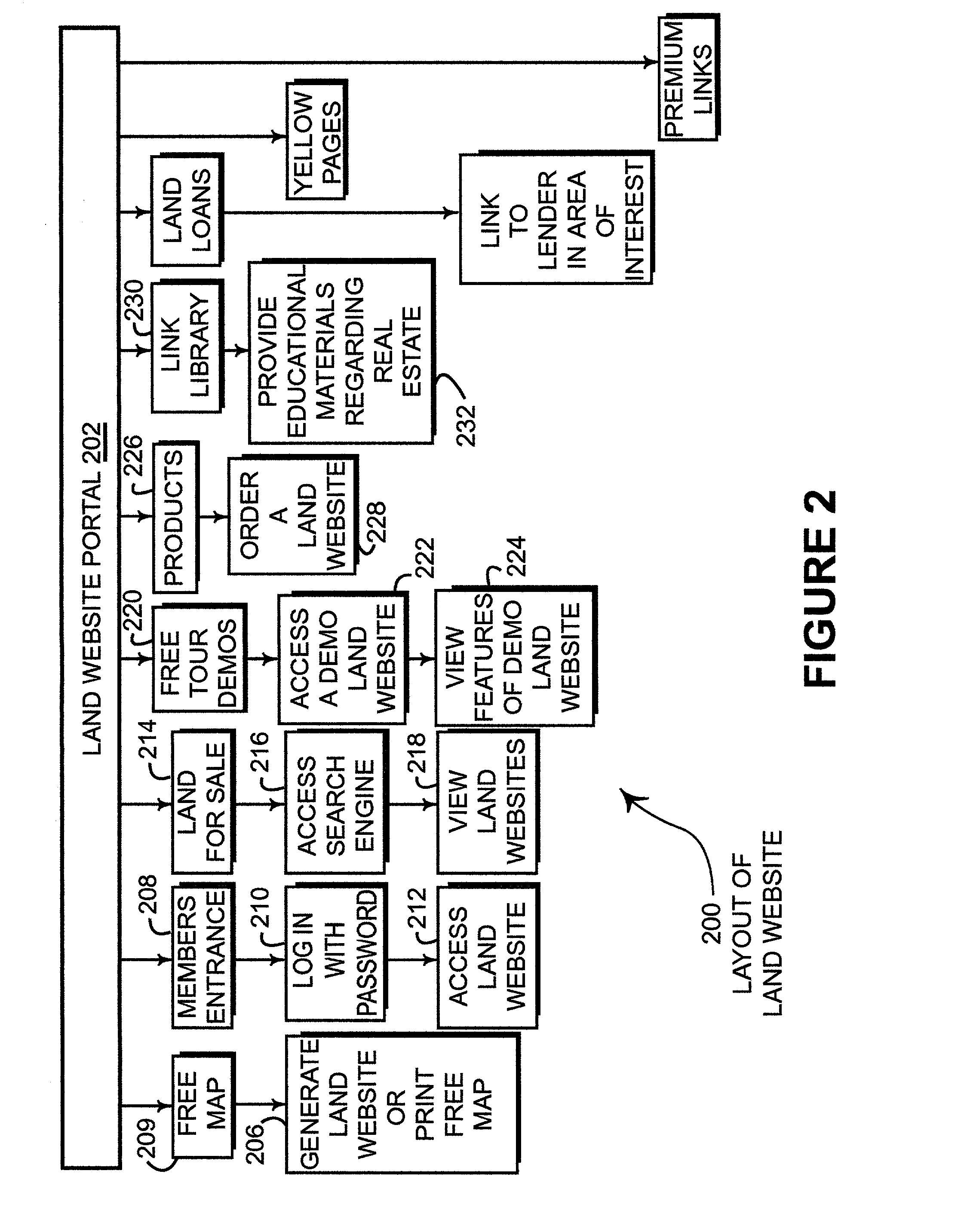
Identification, storage and display of land data on a website
ActiveUS7171389B2Optimize locationLimited accessInstruments for road network navigationRoad vehicles traffic controlPersonalizationDocument preparation
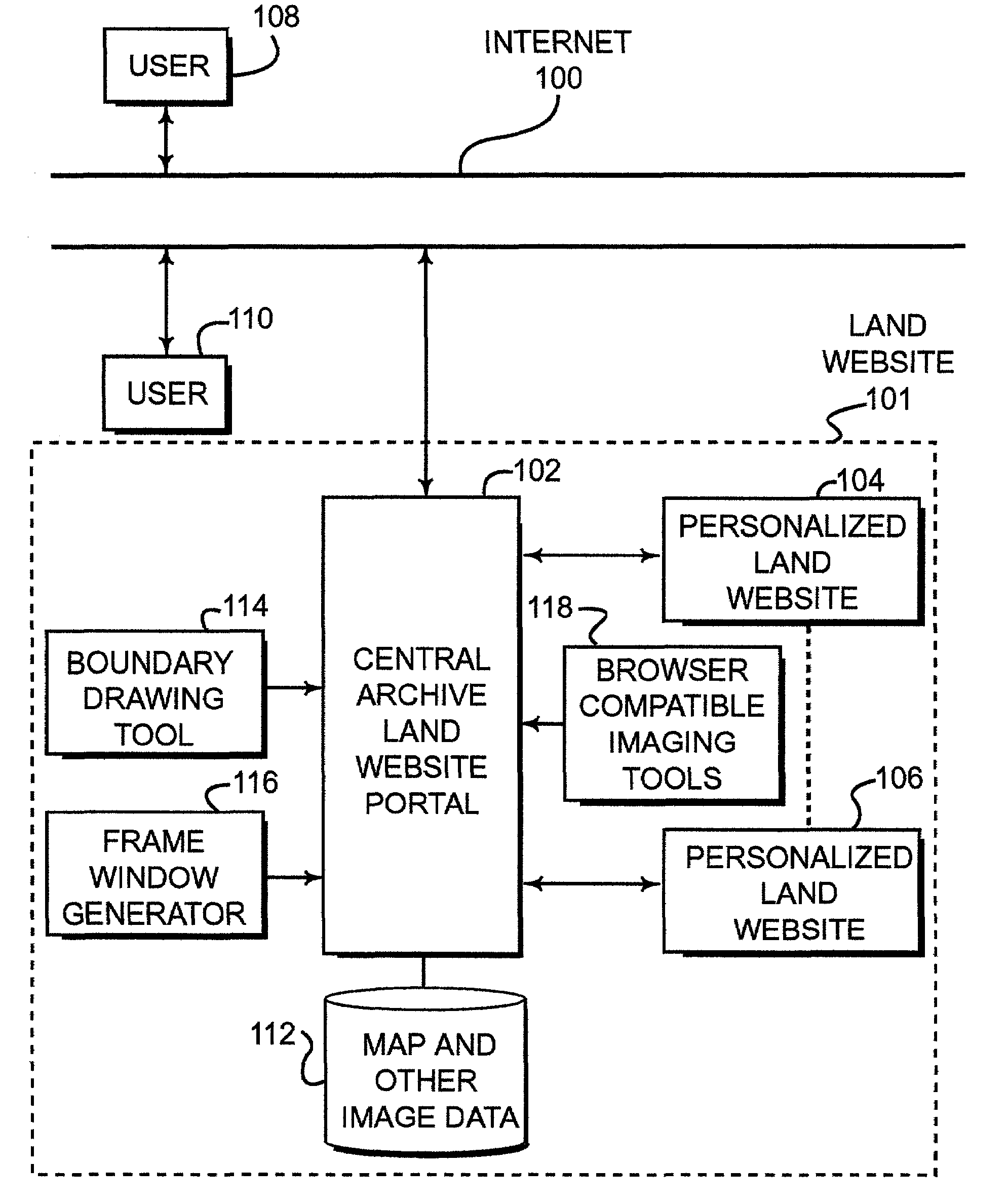
Disclosed is a land website that provides a personalized database on which data can be stored, retrieved, customized and communicated (e.g., by e-mail) relating to a particular piece of property. The database can be accessible via a password and a security code over the Internet and may be encrypted for transmission. Land websites can be established that contain image data, map libraries, virtual tours, legal descriptions, title information, e-documents, actual pictures of property and various other information. Unique 3-D imaging of composite images can be provided on the land website as well as fly-around composite 3-D images. The land website provides a unique way of packaging information relating to a piece of land in a single, accessible location. A boundary applet tool is provided on the land website portal that allows a user to simply and easily draw boundaries around the property of interest and then submit an order for more detailed information about the property of interest. Various map data and image data are provided to assist the user in drawing the boundaries. Acreage amounts are automatically calculated based upon the size and area drawn by the user. Properties of interest can be easily accessed by a global coordinate system or by searching on map data that is provided on a wide range of scales.
Owner:LANDNET CORP
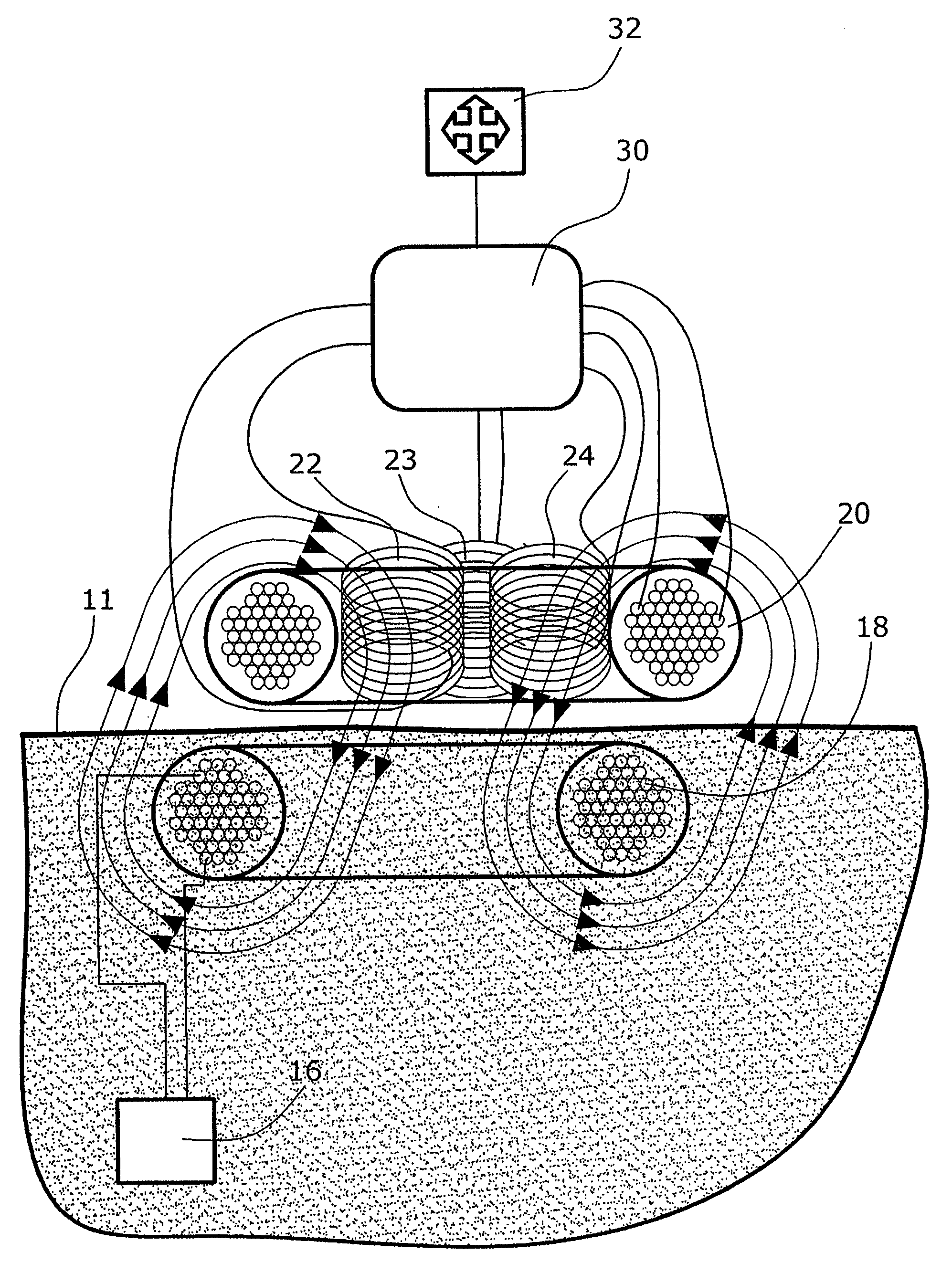
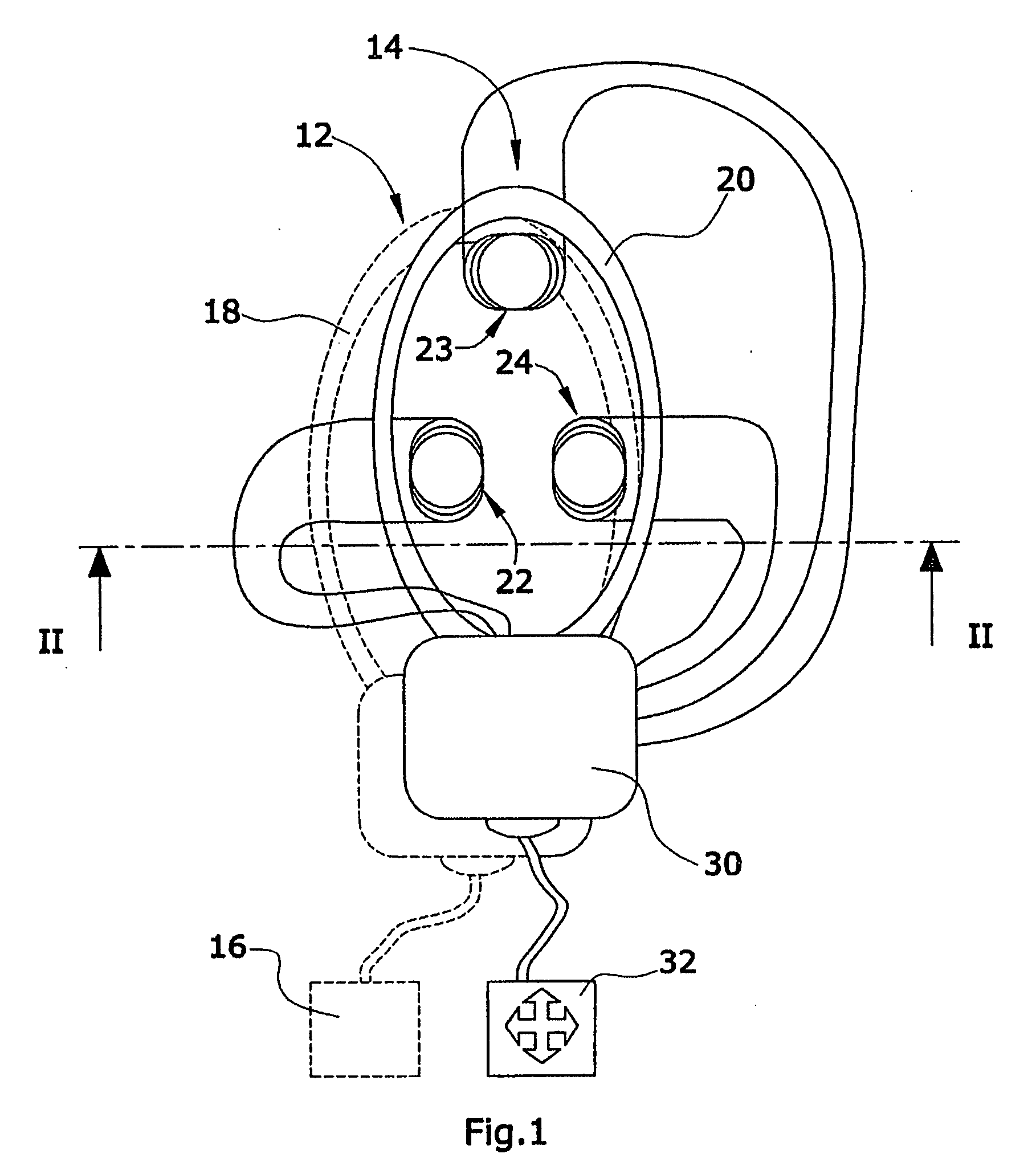
Transfer assembly
ActiveUS20080027293A1Easy transferRaise checkElectrotherapyCircuit arrangementsElectrical and Electronics engineeringEngineering
A transfer assembly comprising an intracorporeal transfer coil of an implant, and an extracorporeal transfer coil of an extracorporeal supply unit. The transfer coil of the implant has permanently associated therewith a transmitting element. The transfer coil of the supply unit has permanently associated therewith at least one receiving element. Further, the supply unit comprises an evaluation module connected with the receiving element and issuing a locating signal depending on an offset and / or a direction of offset of the transmitting element relative to the receiving element.
Owner:DEUTSCHES ZENTRUM FUER LUFT & RAUMFAHRT EV
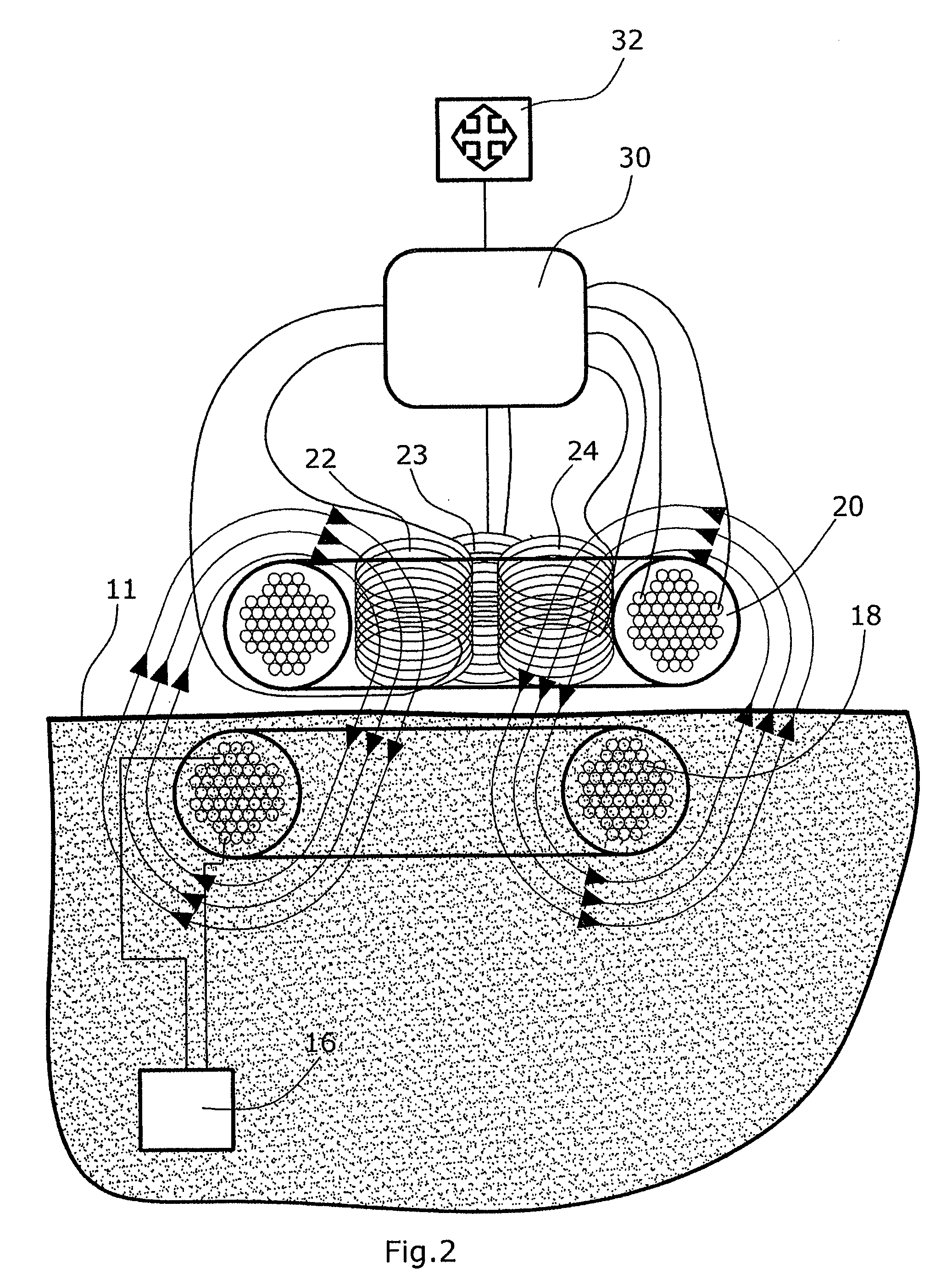
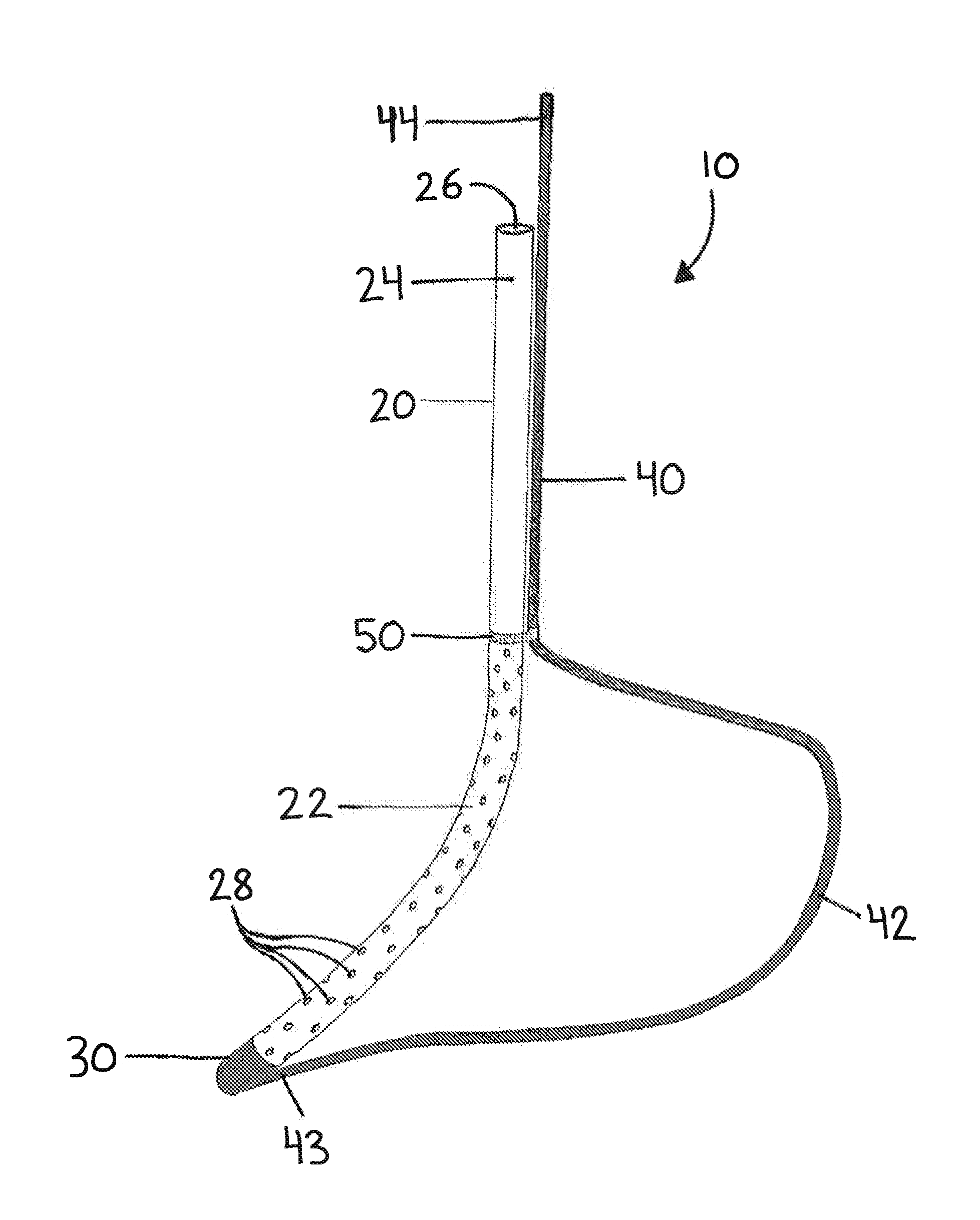
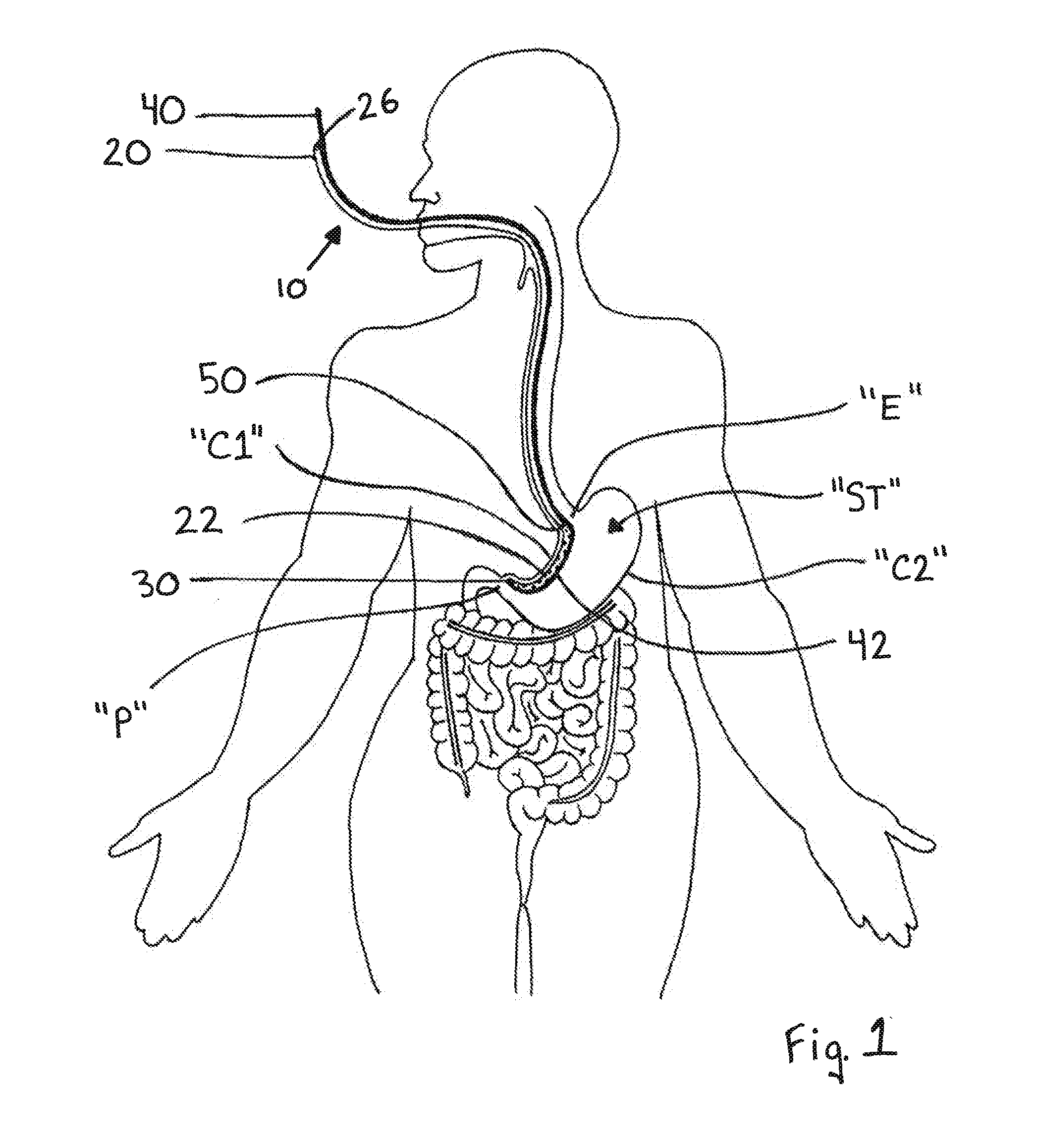
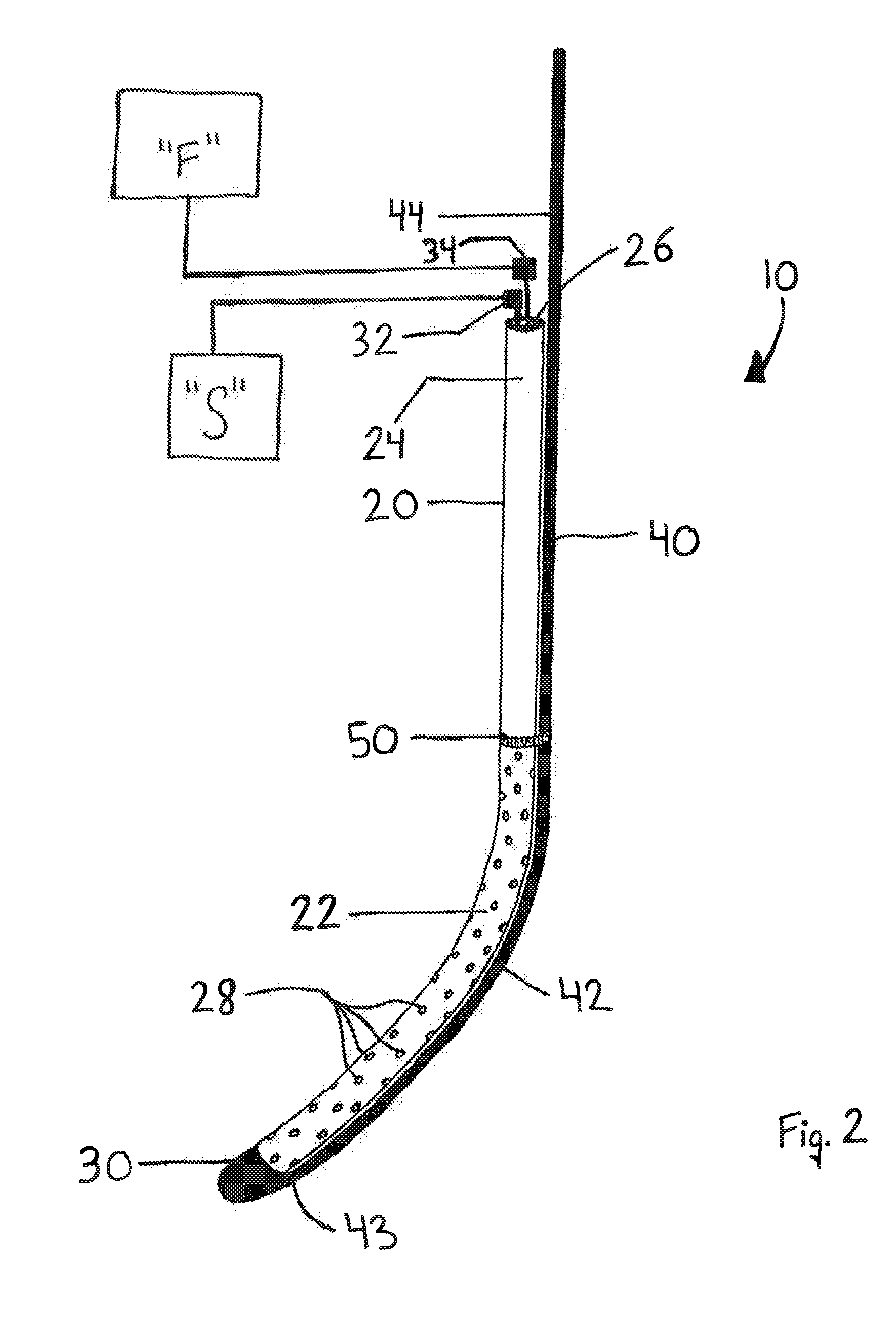
Devices and methods facilitating sleeve gastrectomy procedures
ActiveUS20140114121A1Clearly markedIntravenous devicesNon-surgical orthopedic devicesDistal portionSurgery procedure
A device for use in bariatric surgery includes a tube member, a coupling member, and a rod member. The tube member includes a proximal portion and a distal portion having a distal end. The coupling member is affixed to the tube member. The rod member includes a proximal portion and a distal portion having a distal end. The rod member is slidably coupled with the coupling member. The distal end of the rod member is fixedly coupled to the distal end of the tube member. The proximal portion of the rod member is translatable relative to the tube member to transition the distal portion of the rod member between a contracted position, wherein the distal portion of the rod member extends along the distal portion of the tube member, and a deployed position, wherein the distal portion of the rod member bows outwardly relative to the tube member.
Owner:TYCO HEALTHCARE GRP LP
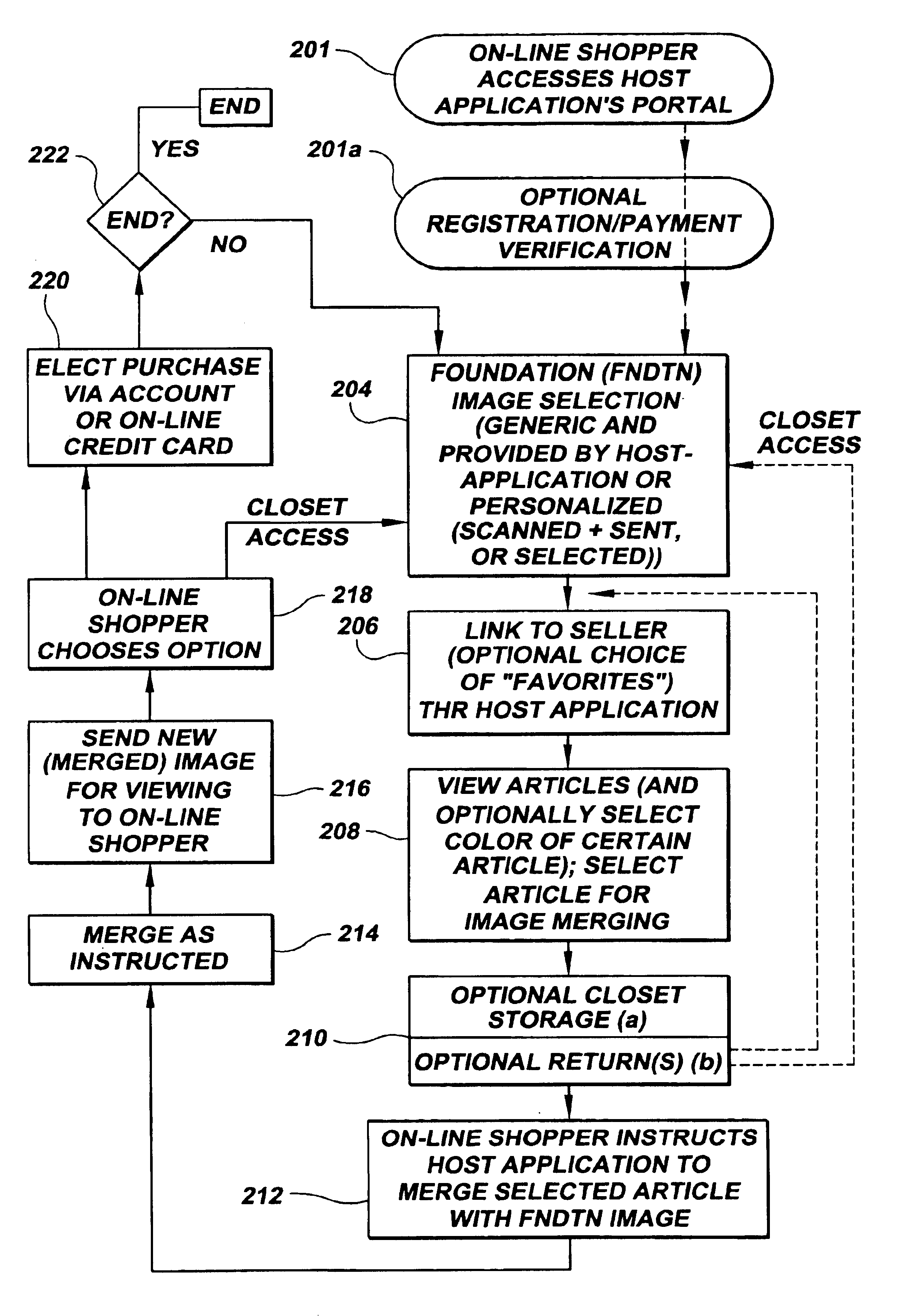
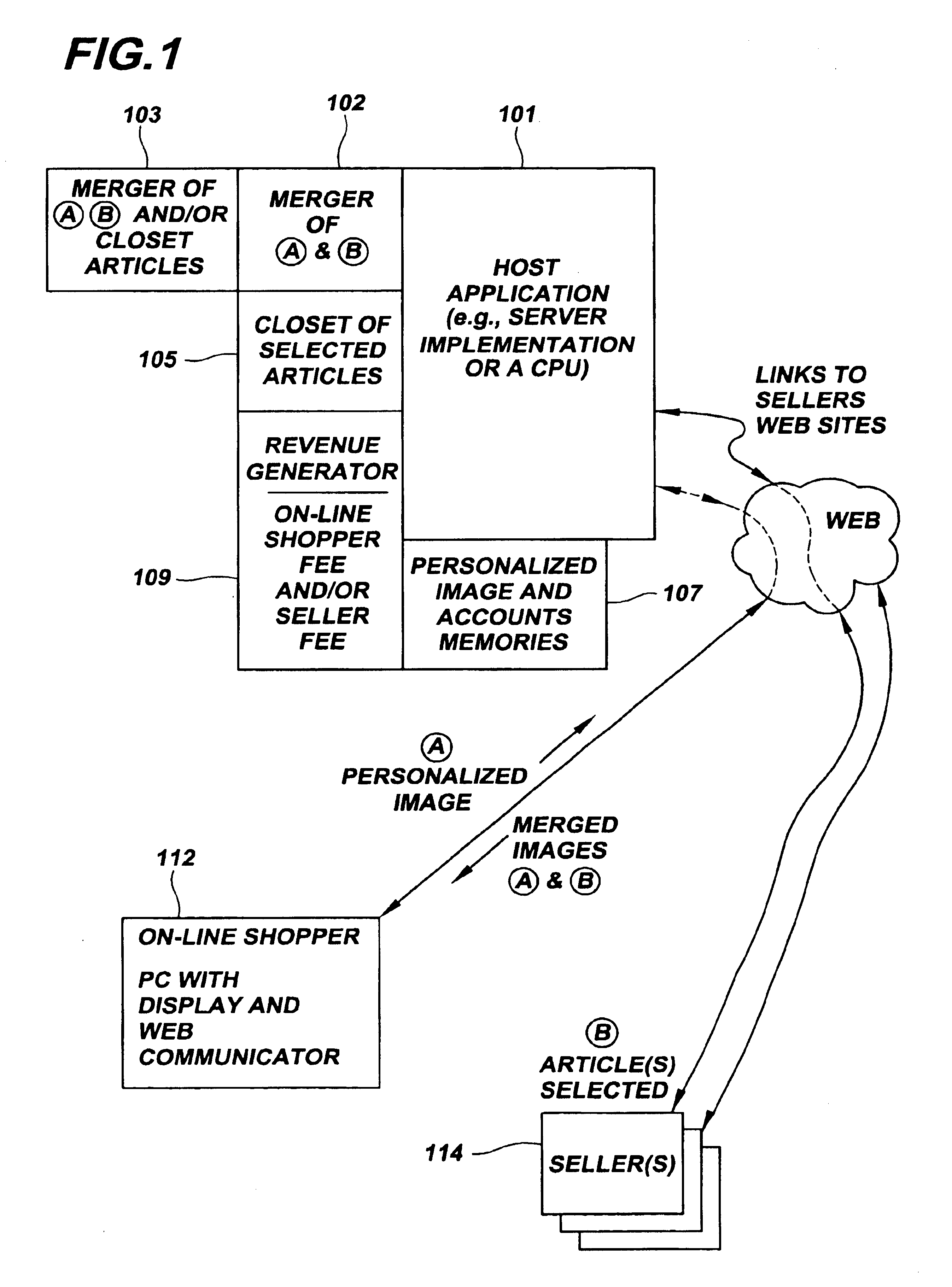
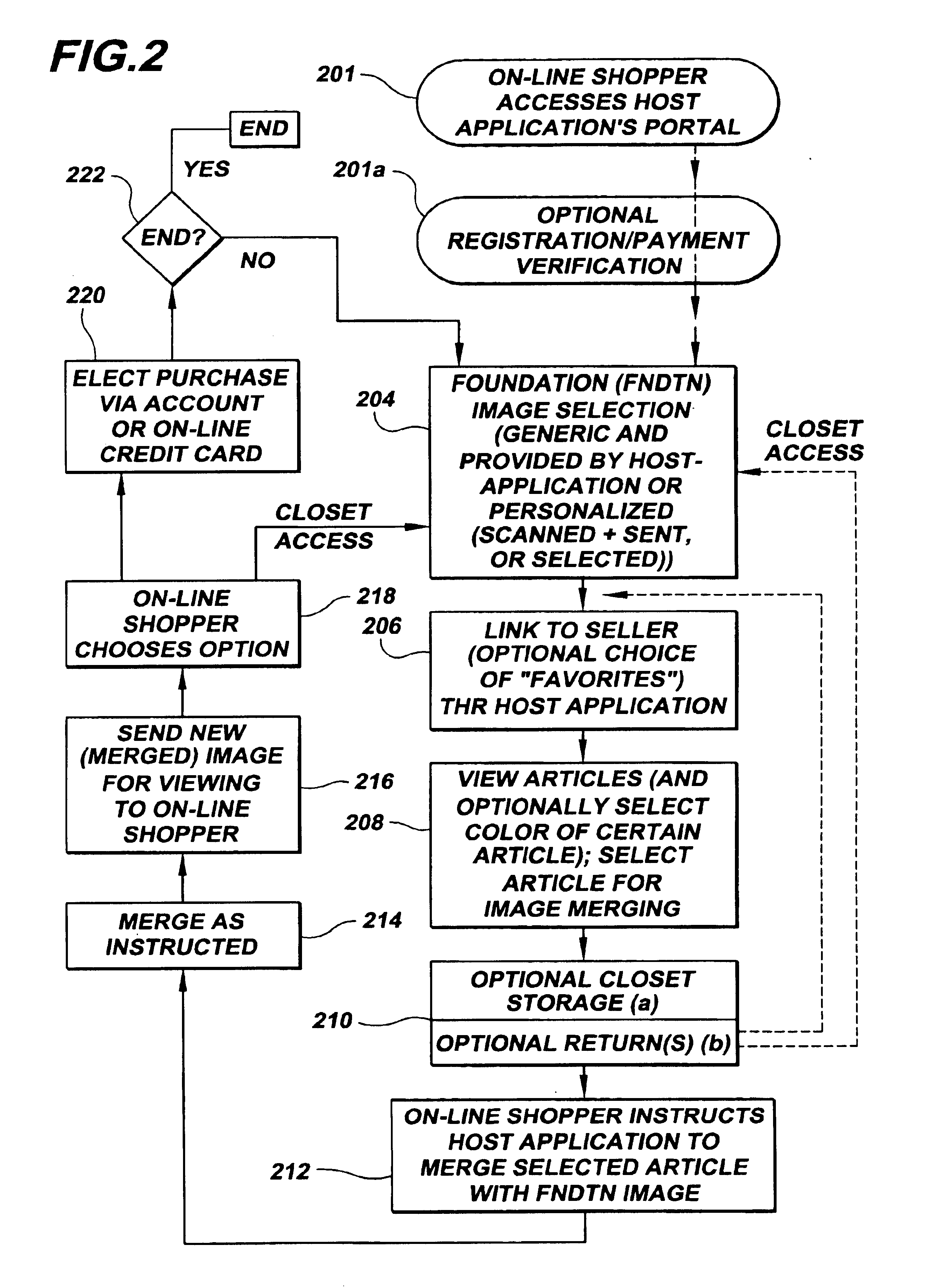
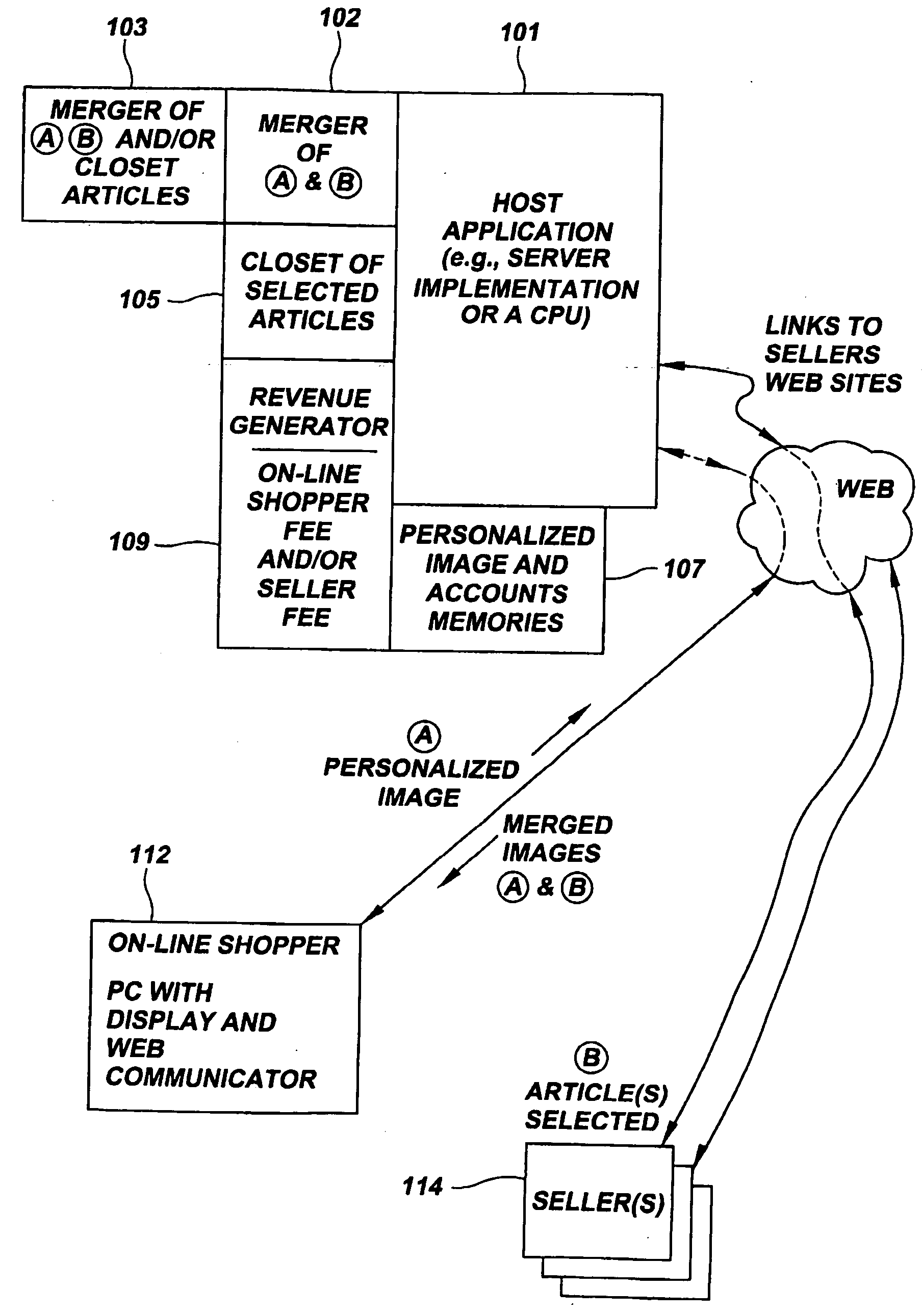
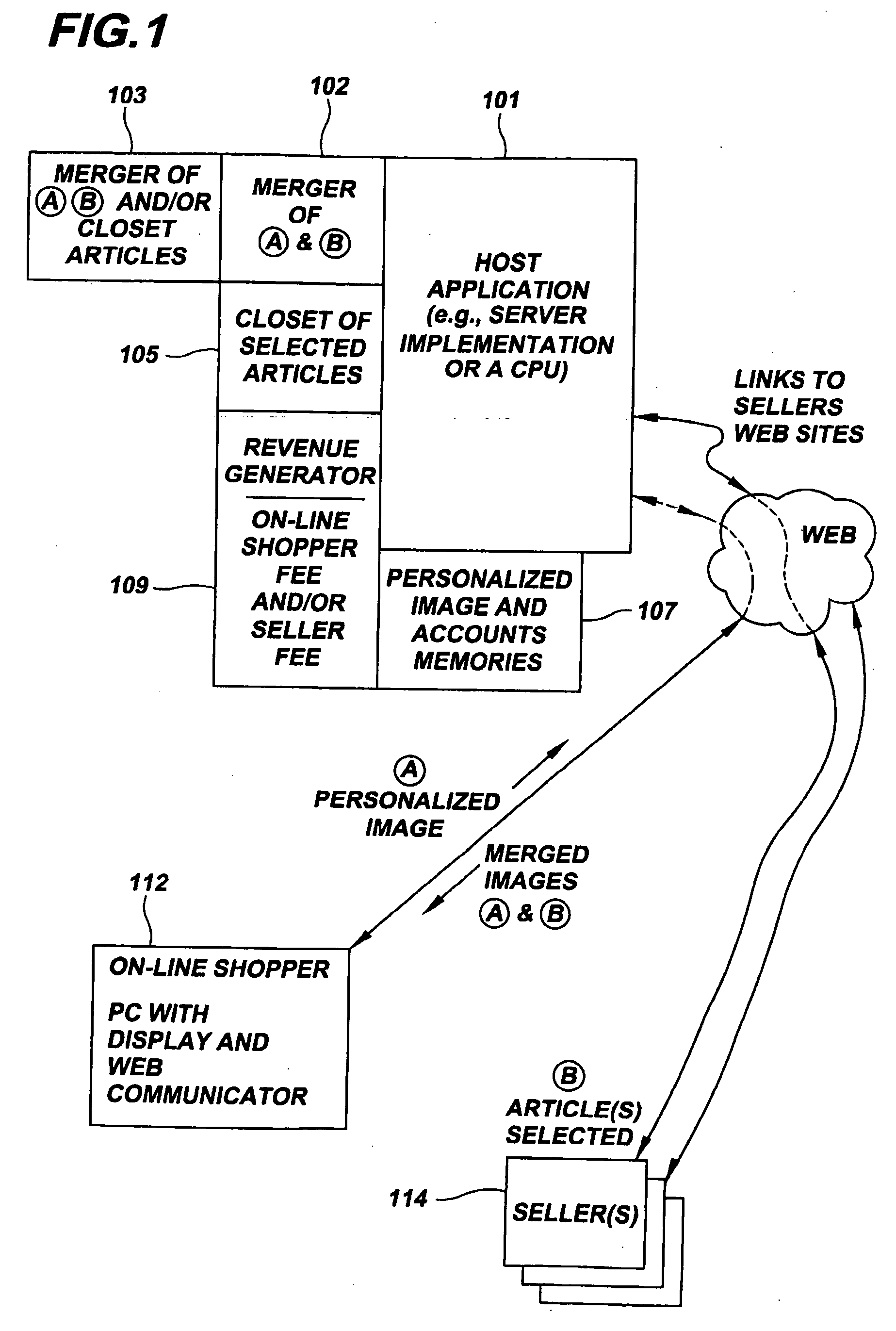
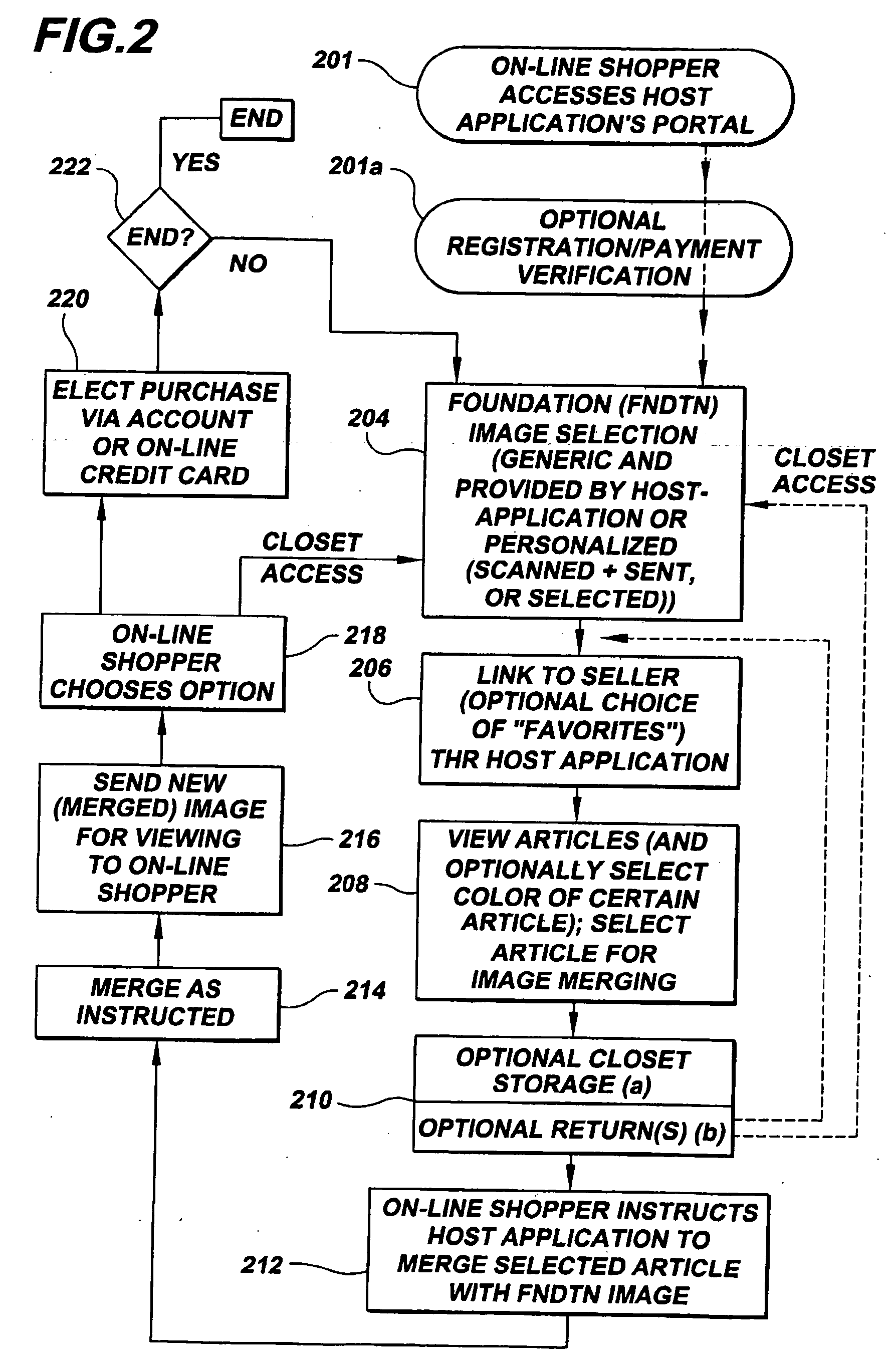
Merged images viewed via a virtual storage closet
InactiveUS6903756B1Improve shopping experienceClearly markedVisual presentationBuying/selling/leasing transactionsE-commerceImage View
An e-commerce method involves on-line viewing of a first article through a linking node for virtual merging on another structure. A particular application of the invention is directed to a method of on-line apparel shopping. The method includes providing a host-site accessible to an on-line viewer (customer) and web-linkable to a retailer having an apparel site. The retailer's apparel site has images of articles stored in a virtual closet. These articles can be apparel from retail stores for viewing over the web, and the on-line viewer is linked to the host-site. The consumer selects a structure, such as a photograph of a person captured in system memory, in response to a command received by the on-line viewer. Using the host-site, the viewer or customer is linked to the retailer's apparel site and images are passed from that site for view by the customer. Apparel is selected and virtually merged with the structure by forming an image including representations of both the structure and the selected apparel.
Owner:TAMIRAS PER PTE LTD LLC
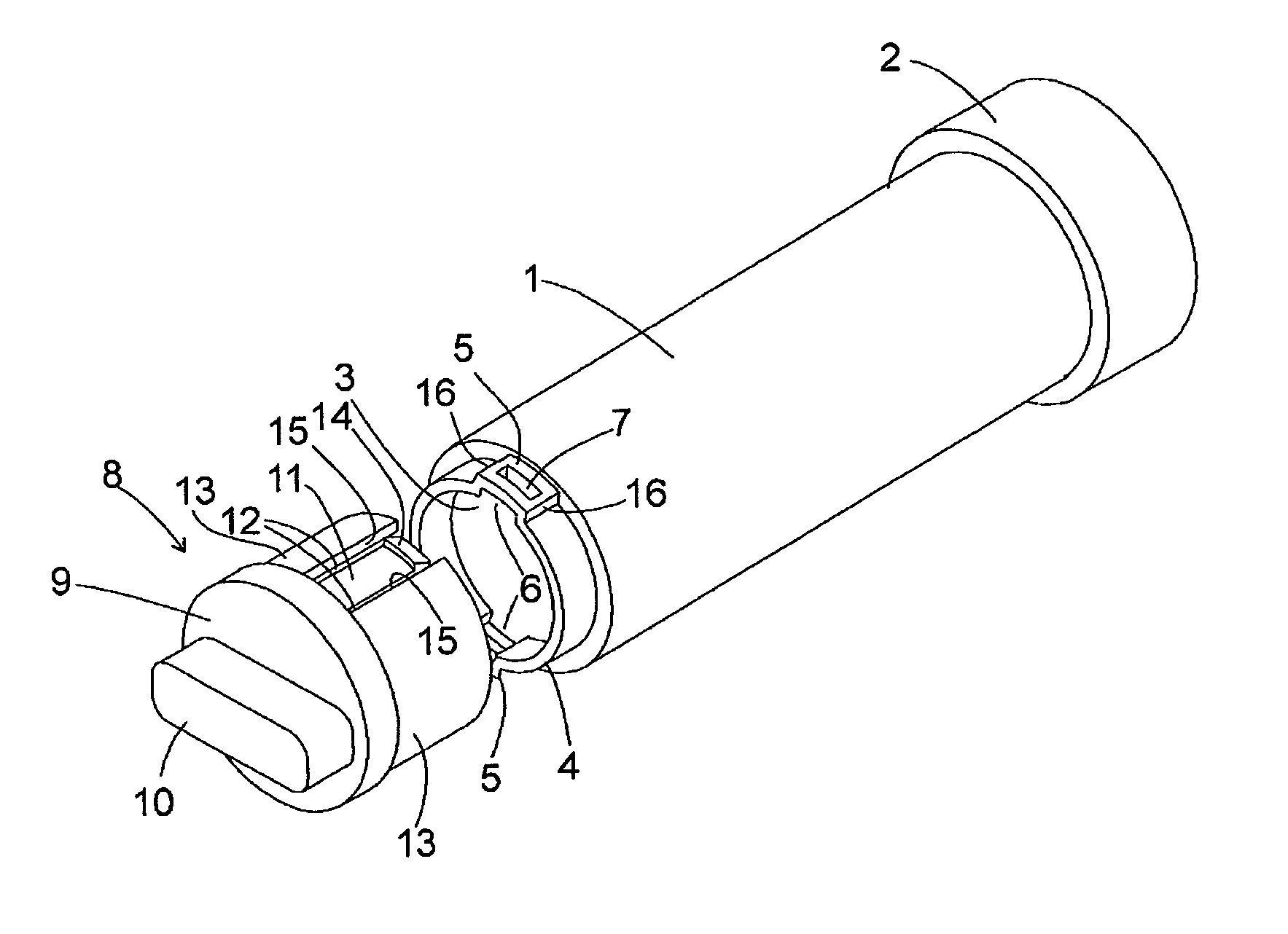
Endovascular treatment apparatus and method
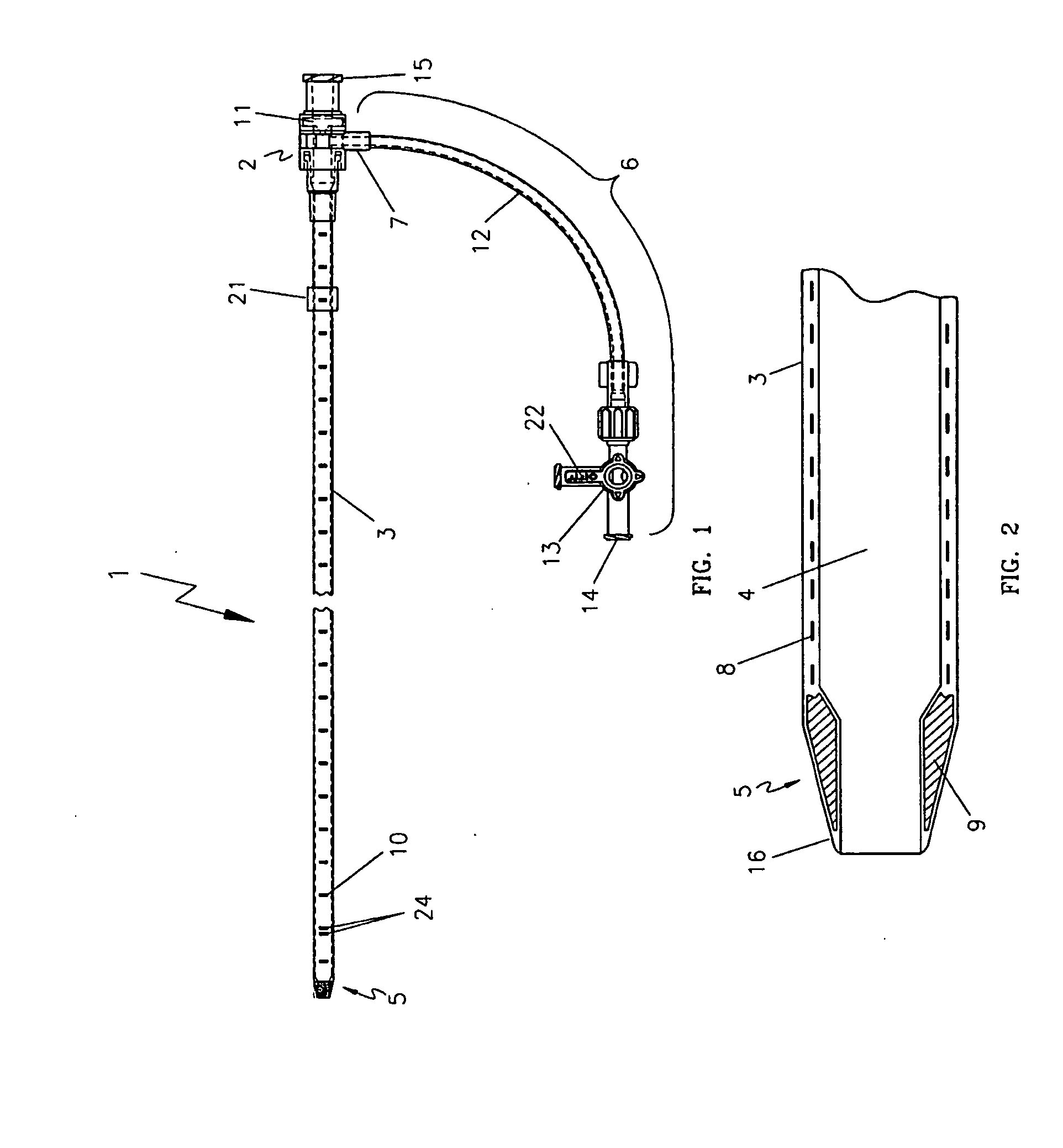
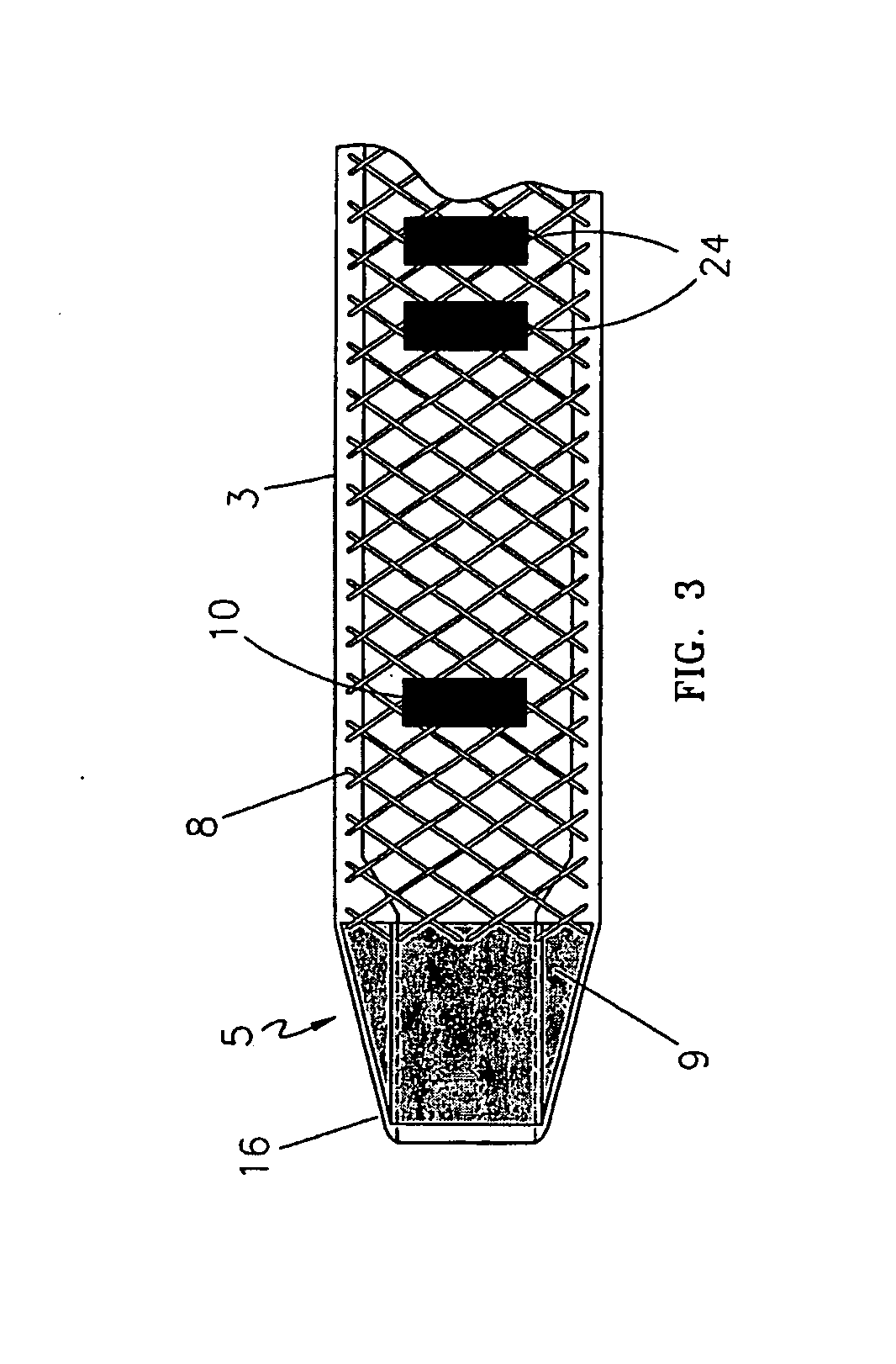
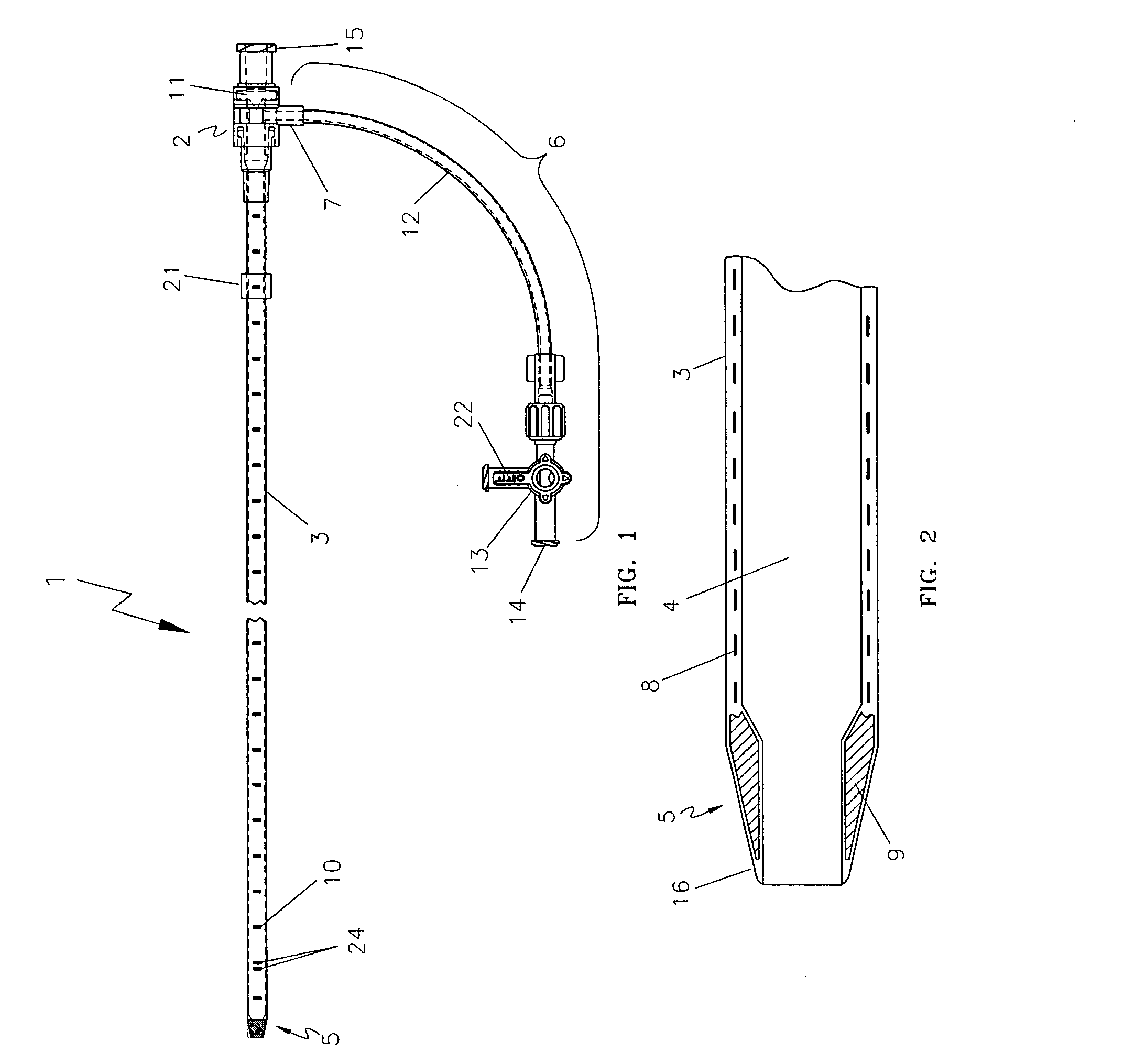
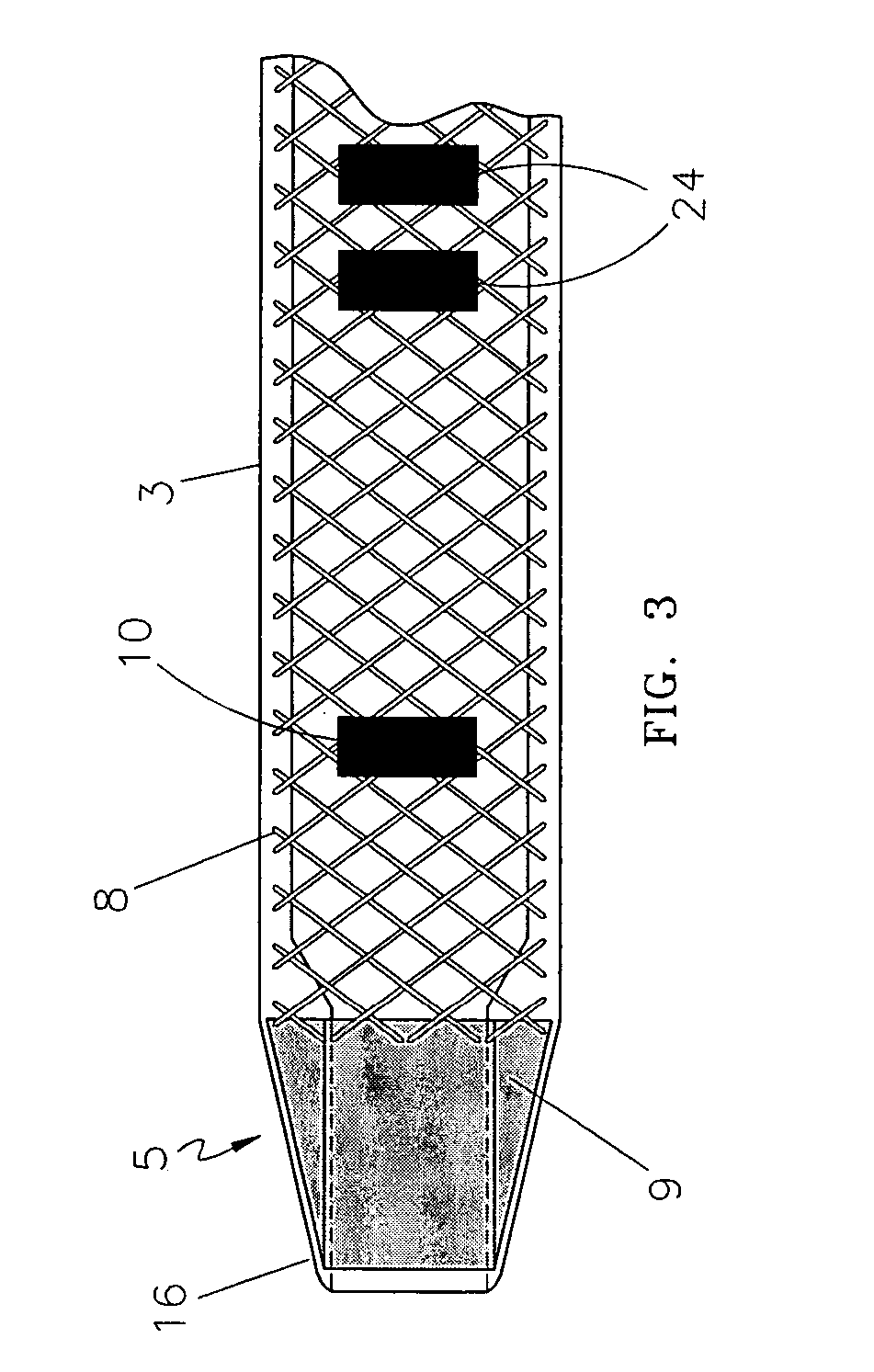
ActiveUS20080249399A1Clearly markedIncrease awarenessChiropractic devicesEye exercisersEndovascular treatmentFiber
An endovascular sheath device for use with a thermal treatment apparatus is provided. The device includes a longitudinal tube which is designed to receive a thermal treatment device and is designed to be inserted into a blood vessel. An ultrasonically visible reinforcement element is disposed along the length of the longitudinal tube. The reinforcement element such as a braided wire provides several functions including increased visibility under ultrasound, clearer identification of sheath tip, and increased durability to protect the fiber from needle punctures during tumescent injections into the perivenous space. The wire reinforcement also increases shaft torquability and kink resistance during sheath insertion and withdrawal.
Owner:ANGIODYNAMICS INC
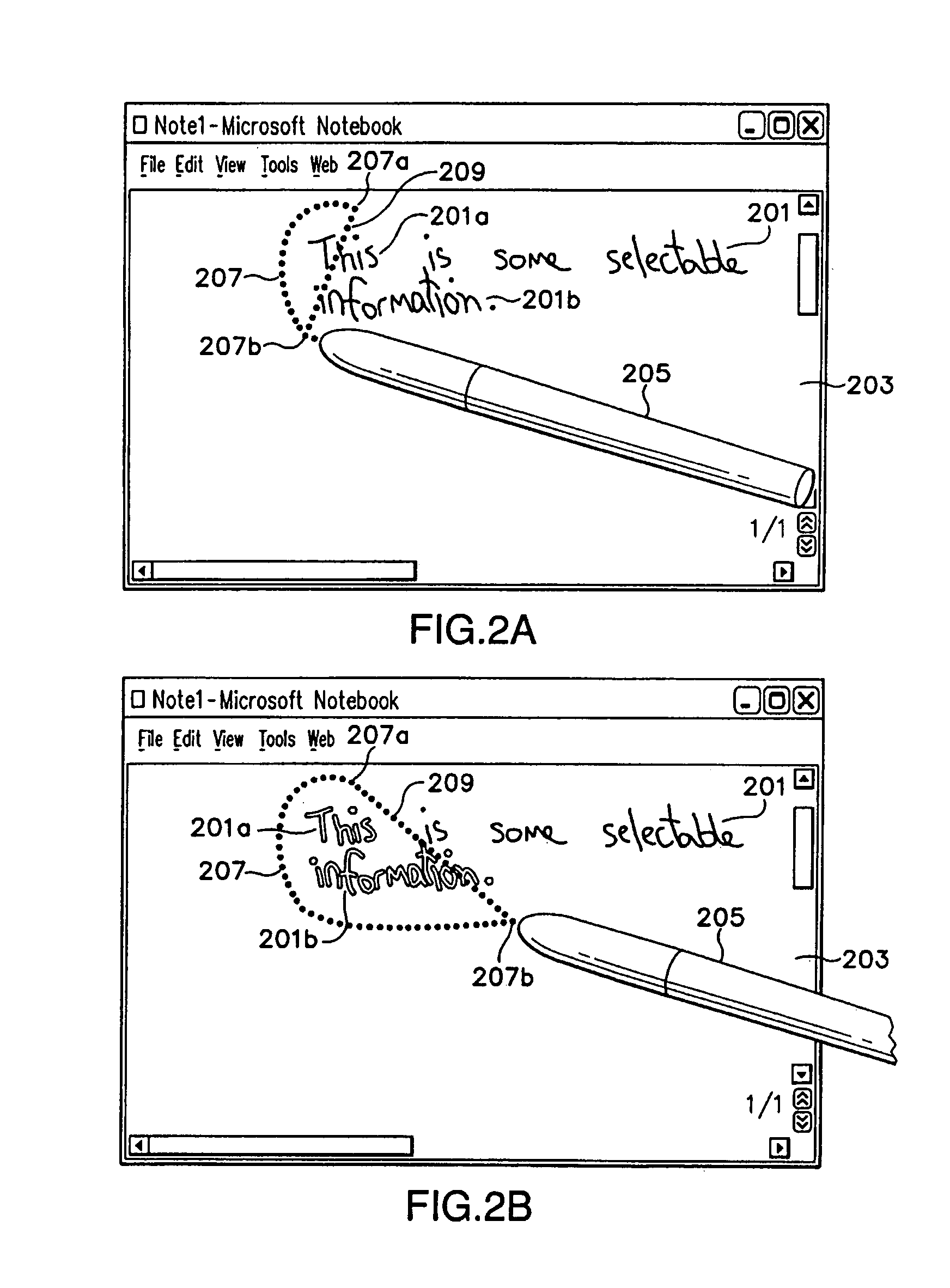
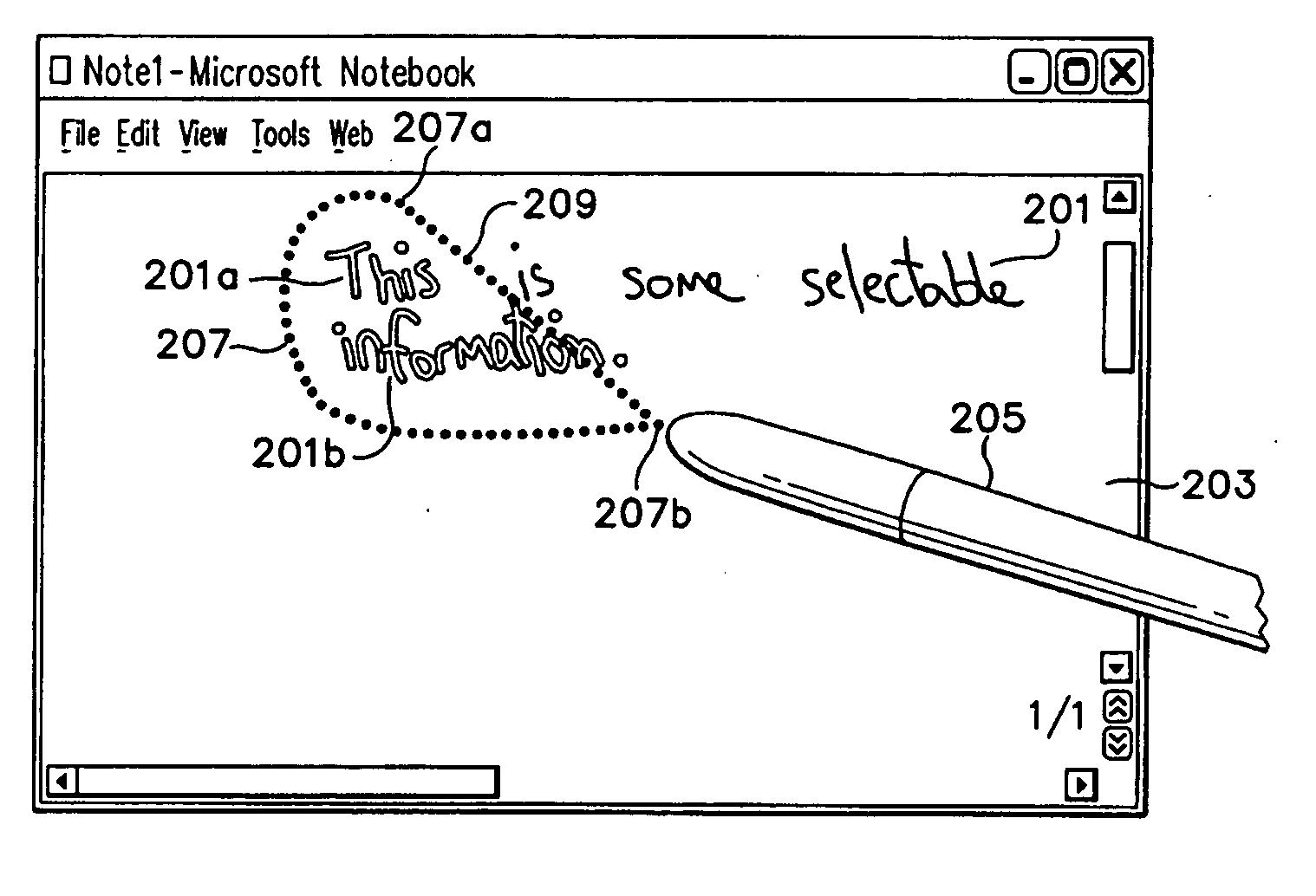
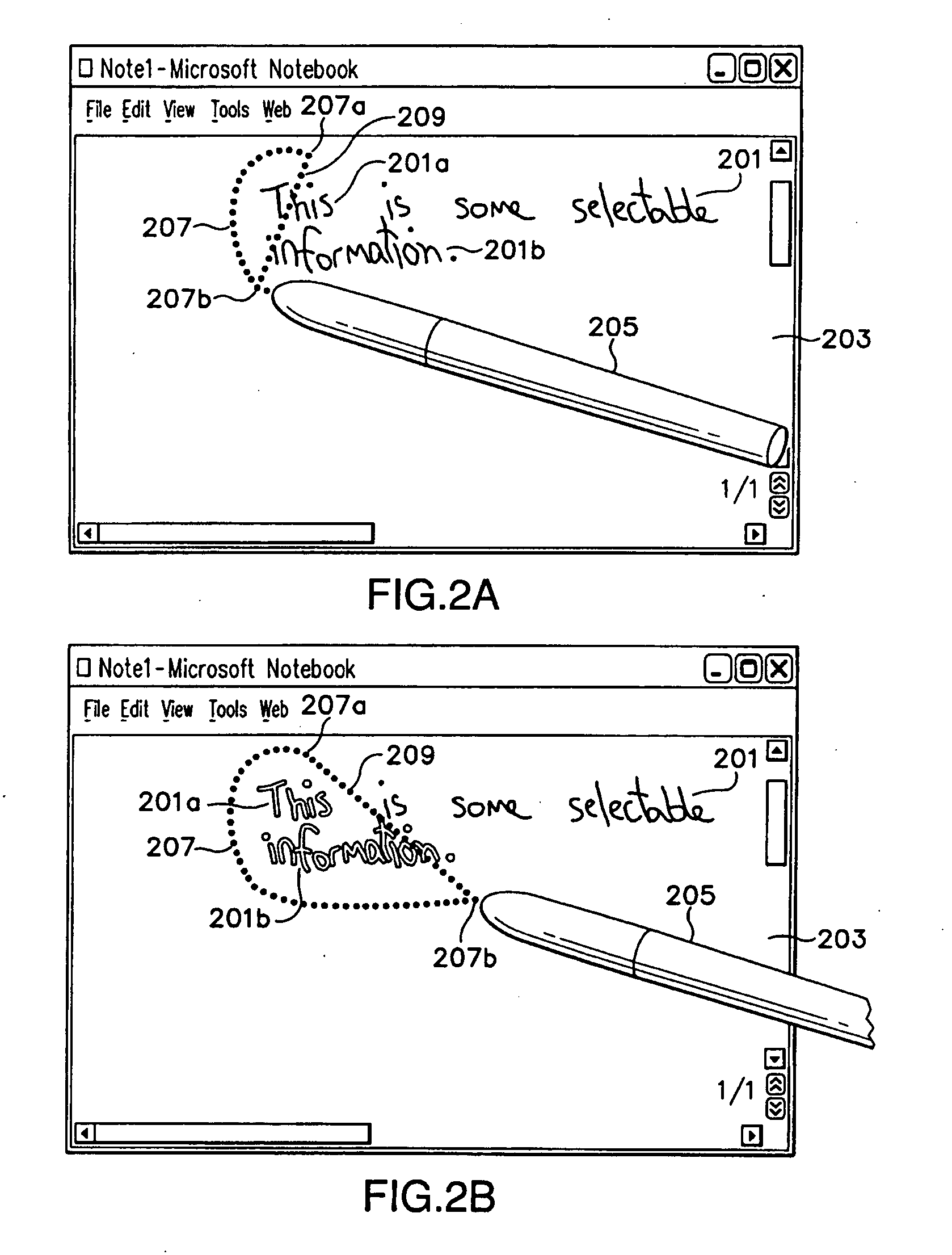
Lasso select
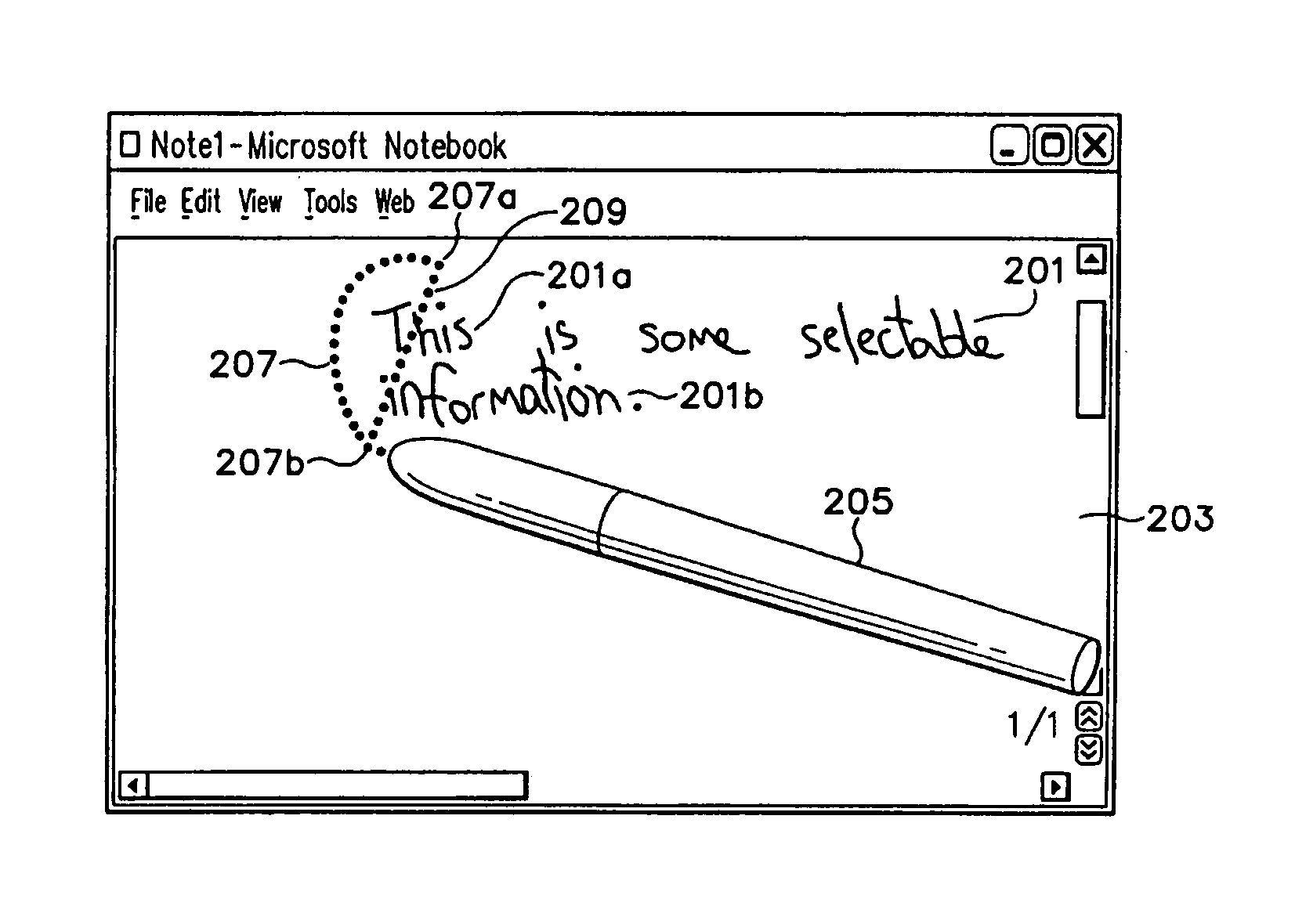
InactiveUS7299424B2Flexible choiceClearly markedCharacter and pattern recognitionInput/output processes for data processingGraphicsSoftware engineering
A lasso select tool that allows a user to draw a flexible line of selection ink in order to select one or more graphical objects for manipulation. As the user draws this selection line, the lasso select tool continuously redraws and displays a connection line connecting one end of the selection line with the opposite end of the selection line. This connection line thus graphically demonstrates to the user the area that is presently encompassed by the resulting lasso enclosure. Further, the lasso select tool will change the appearance of any object selected with the lasso enclosure. The lasso select tool also selects objects that are only substantially encompassed by the lasso enclosure. For example, the lasso select tool may select ink objects that are only 60% or more encompassed by the lasso enclosure.
Owner:MICROSOFT TECH LICENSING LLC
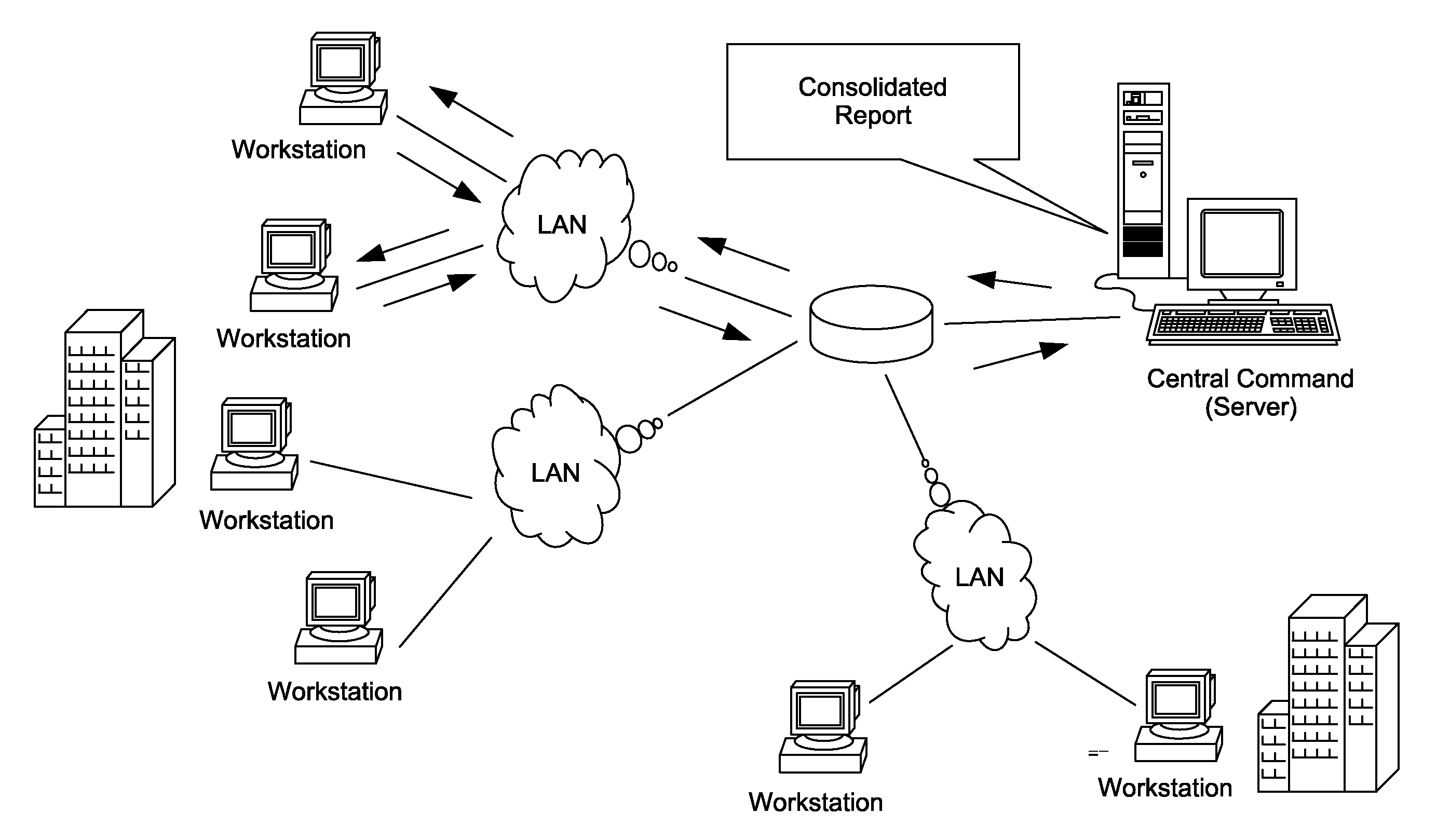
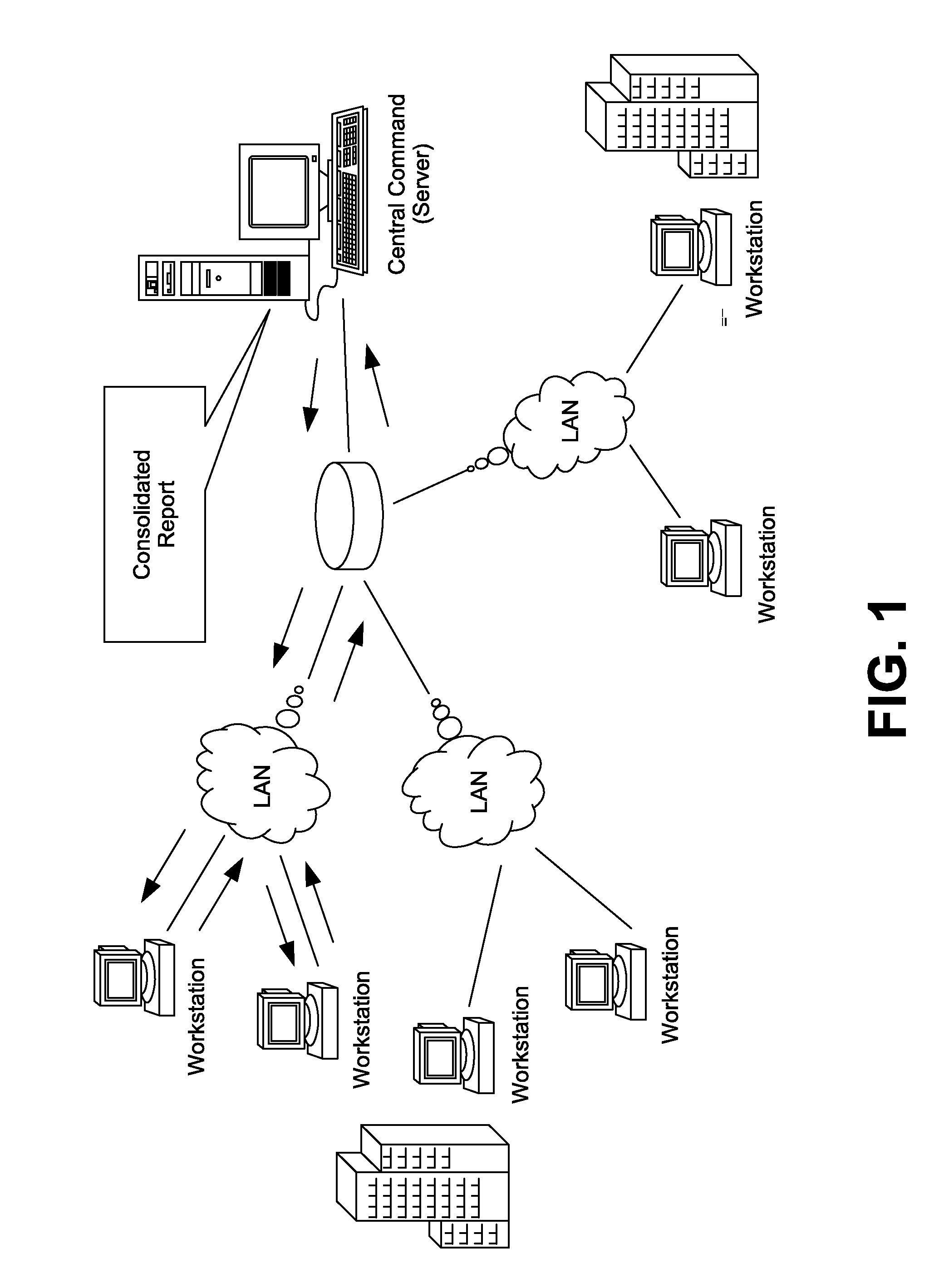
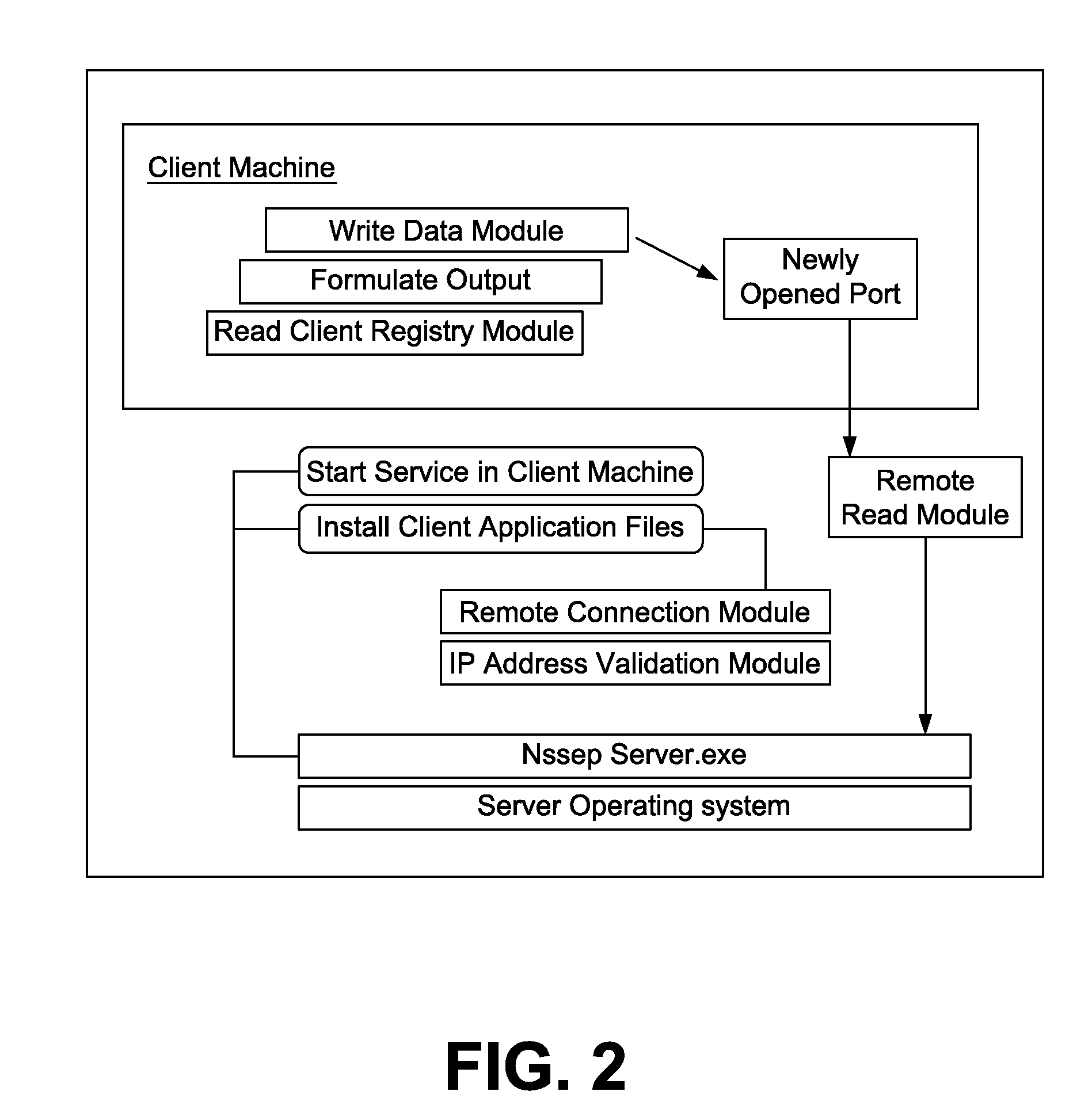
Network security scanner for enterprise protection
ActiveUS20080276295A1Improve virus prevention processImprove engineer-productivityPlatform integrity maintainanceTransmissionOperational systemNetwork connection
A method of monitoring levels of security conformity and preparedness of a plurality of network connected computing machines, obtains a report by remotely scanning the machines in segments. The machines might already be connected to commercial security software and a patch dispenser. The report includes definition dates and any files quarantined by the commercial security software, patch-management-software communication present and the patches received. The method uses the report and software (not installed on the scanned machines) to produce a Network Security Scanner for Enterprise Protection output to perform a security-preparedness audit of the scanned machines. The audit non-intrusively ascertains. If the scanned machines conform to user-defined fields and policies, and assists in selective security updating of the machines. The scanning, unrecognized by the scanned machines may be configured to suit their OS, and done periodically as desired. A computer readable medium executing the method is included.
Owner:WIPRO LTD
Lasso select
InactiveUS20050198591A1Flexible choiceClearly markedCharacter and pattern recognitionInput/output processes for data processingGraphicsComputer science
A lasso select tool that allows a user to draw a flexible line of selection ink in order to select one or more graphical objects for manipulation. As the user draws this selection line, the lasso select tool continuously redraws and displays a connection line connecting one end of the selection line with the opposite end of the selection line. This connection line thus graphically demonstrates to the user the area that is presently encompassed by the resulting lasso enclosure. Further, the lasso select tool will change the appearance of any object selected with the lasso enclosure. The lasso select tool also selects objects that are only substantially encompassed by the lasso enclosure. For example, the lasso select tool may select ink objects that are only 60% or more encompassed by the lasso enclosure.
Owner:MICROSOFT TECH LICENSING LLC
Endovascular treatment apparatus and method
An endovascular sheath device for use with a thermal treatment apparatus is provided. The device includes a longitudinal tube which is designed to receive a thermal treatment device and is designed to be inserted into a blood vessel. An ultrasonically visible reinforcement element is disposed along the length of the longitudinal tube. The reinforcement element such as a braided wire provides several functions including increased visibility under ultrasound, clearer identification of sheath tip, and increased durability to protect the fiber from needle punctures during tumescent injections into the perivenous space. The wire reinforcement also increases shaft torquability and kink resistance during sheath insertion and withdrawal.
Owner:ANGIODYNAMICS INC
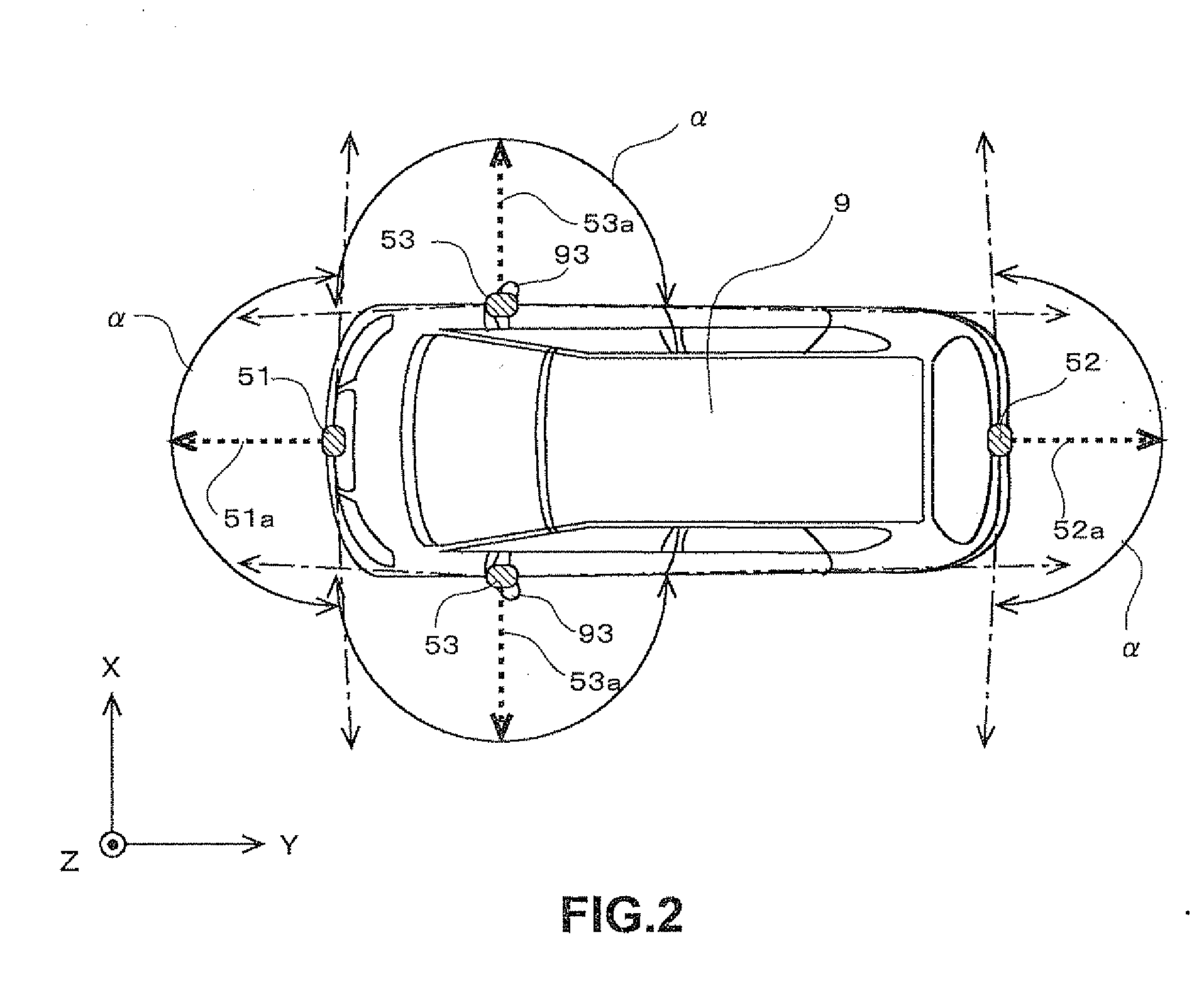
Vehicle guidance assembly and method
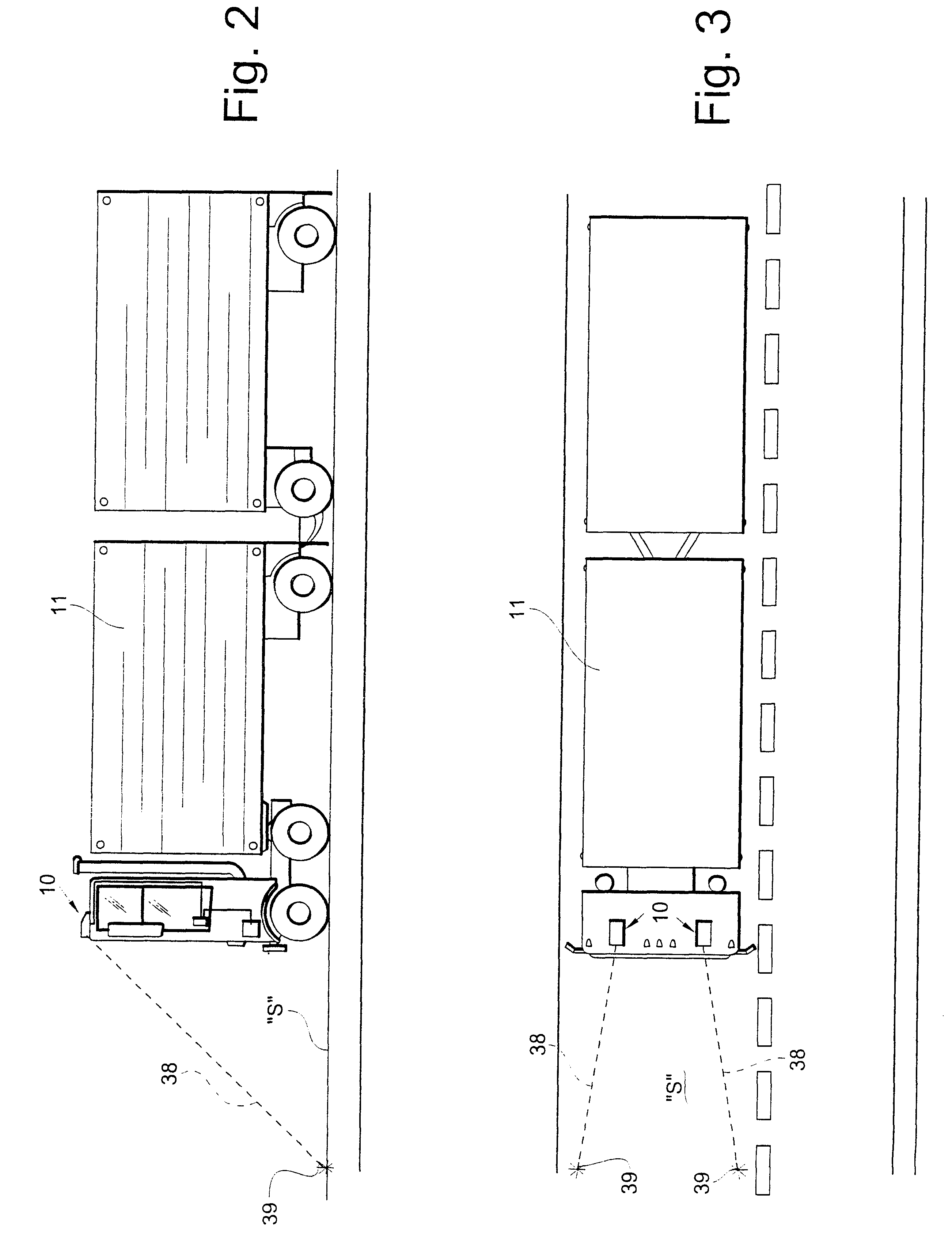
InactiveUS6198386B1Easy to viewEasy to adjustClosed circuit television systemsOptical signallingMobile vehicleEngineering
A vehicle guidance assembly visually indicates the anticipated path of a moving vehicle to a driver of the vehicle. The assembly includes an image projection device for projecting a visual image outwardly from the vehicle and downwardly onto a surface to be travelled by the vehicle. The image defines a reference mark on the surface for being readily viewed by the driver. A mounting member mounts the image projection device on a surface of the vehicle.
Owner:WHITE II LOCKE
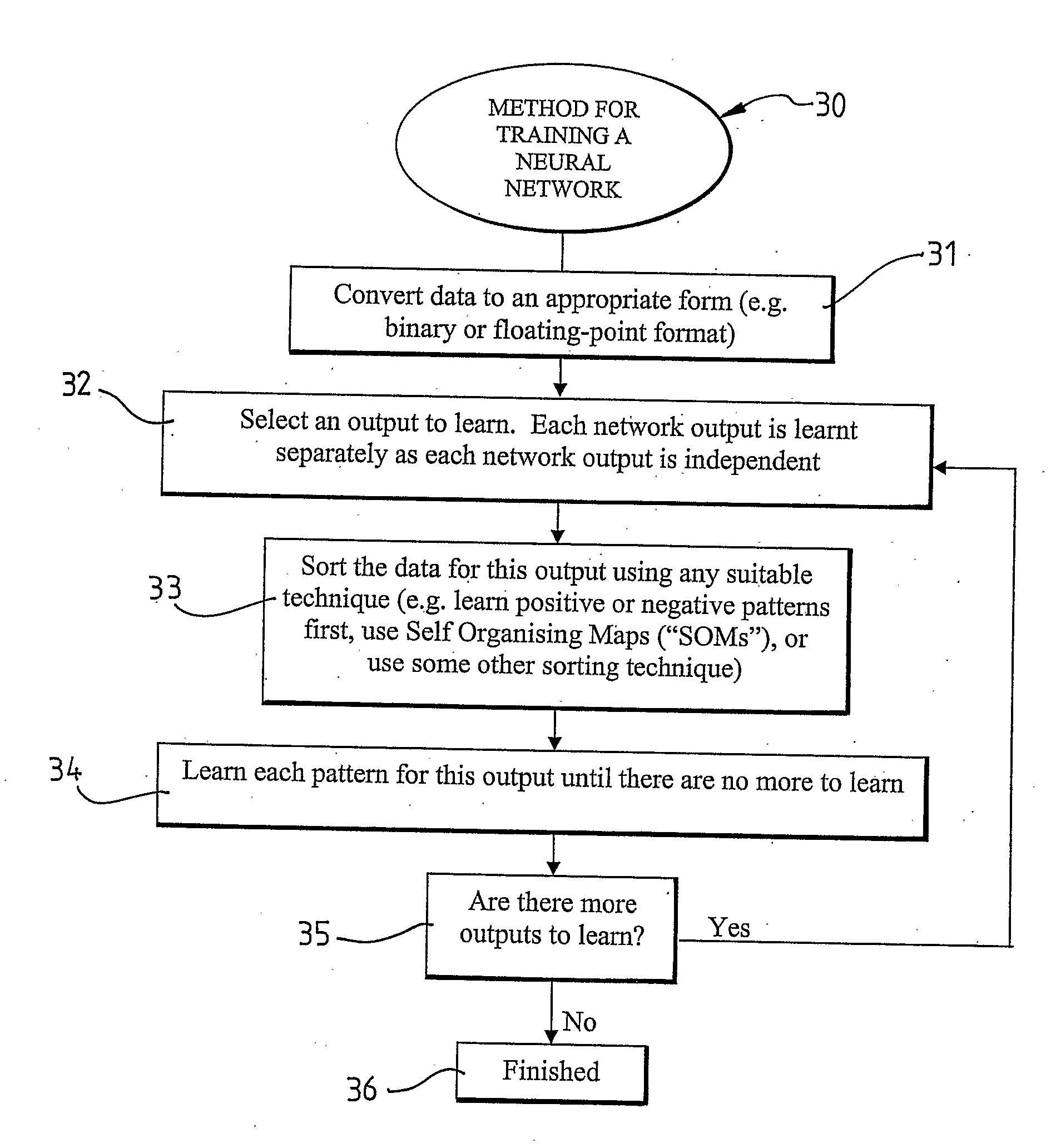
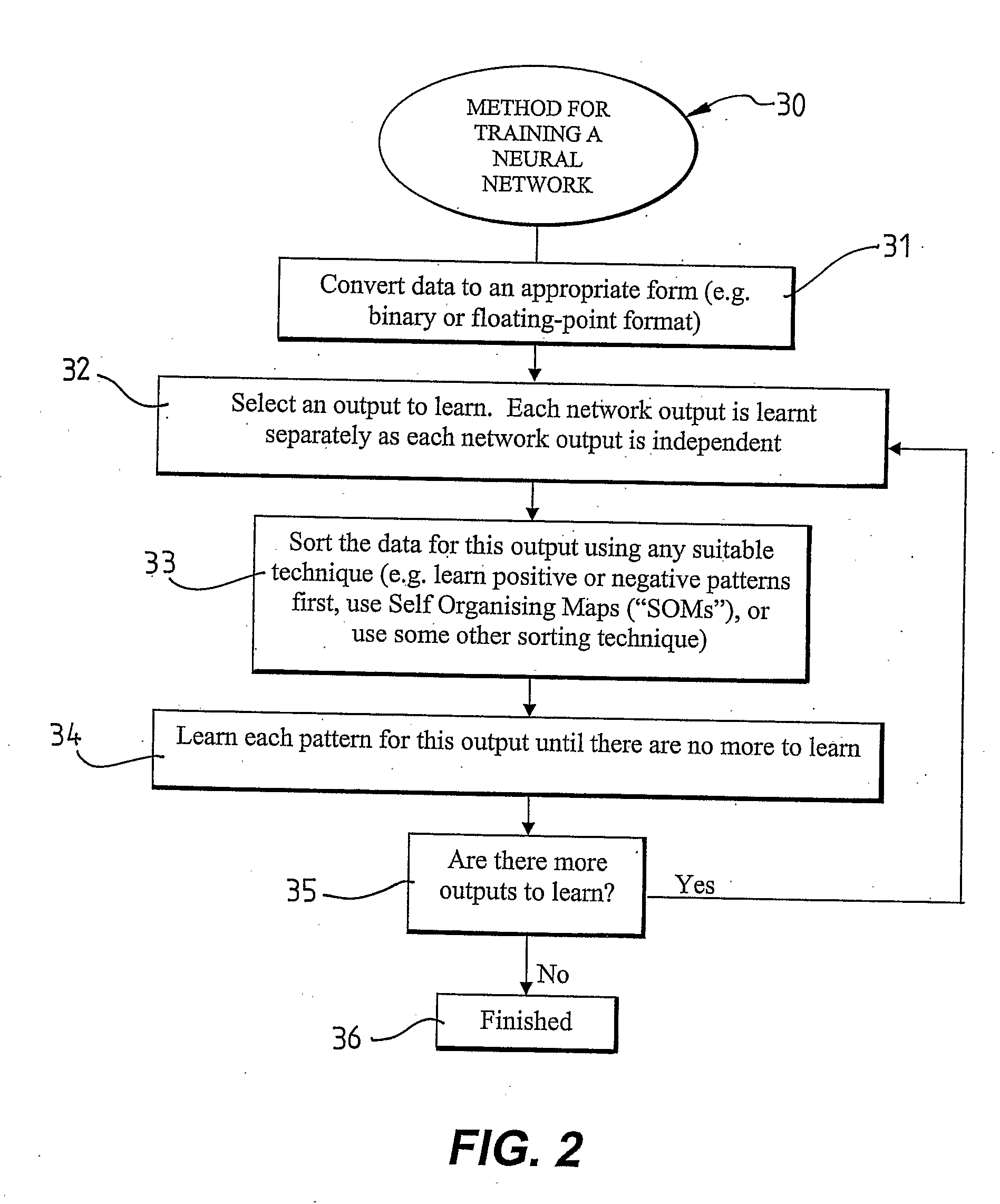
Method for Training Neural Networks
ActiveUS20080281767A1Simple processSimple taskDigital computer detailsProcessor architectures/configurationHidden layerData set
The present invention provides a method (30) for training an artificial neural network (NN). The method (30) includes the steps of: initialising the NN by selecting an output of the NN to be trained and connecting an output neuron of the NN to input neuron(s) in an input layer of the NN for the selected output; preparing a data set to be learnt by the NN; and, applying the prepared data set to the NN to be learnt by applying an input vector of the prepared data set to the first hidden layer of the NN, or the output layer of the NN if the NN has no hidden layer(s), and determining whether at least one neuron for the selected output in each layer of the NN can learn to produce the associated output for the input vector. If none of the neurons in a layer of the NN can learn to produce the associated output for the input vector, then a new neuron is added to that layer to learn the associated output which could not be learnt by any other neuron in that layer. The new neuron has its output connected to all neurons in next layer that are relevant to the output being trained. If an output neuron cannot learn the input vector, then another neuron is added to the same layer as the current output neuron and all inputs are connected directly to it. This neuron learns the input the old output could not learn. An additional neuron is added to the next layer. The inputs to this neuron are the old output of the NN, and the newly added neuron to that layer.
Owner:GARNER BERNADETTE
Apparatus and method for managing access to a memory
ActiveUS7487367B2Performance is not affectedEasy to operateMemory architecture accessing/allocationEncryption apparatus with shift registers/memoriesManagement unitComputer science
The present invention provides a data processing apparatus and method for managing access to a memory within the data processing apparatus. The data processing apparatus comprises a processor operable in a plurality of modes and a plurality of domains, said plurality of domains comprising a secure domain and a non-secure domain, said plurality of modes including at least one non-secure mode being a mode in the non-secure domain and at least one secure mode being a mode in the secure domain, said processor being operable such that when executing a program in a secure mode said program has access to secure data which is not accessible when said processor is operating in a non-secure mode. Further, a memory is provided for storing data required by the processor, and consists of secure memory for storing secure data and non-secure memory for storing non-secure data. The memory further contains a non-secure table and a secure table, the non-secure table being within the non-secure memory and arranged to contain for each of a number of first memory regions an associated descriptor, and the secure table being within the secure memory and arranged to contain for each of a number of second memory regions an associated descriptor. When access to an item of data in the memory is required by the processor, the processor issues a memory access request, and a memory management unit is provided to perform one or more predetermined access control functions to control issuance of the memory access request to the memory. The memory management unit comprises an internal storage unit operable to store descriptors retrieved by the memory management unit from either the non-secure table or the secure table, and in accordance with the present invention the internal storage unit comprises a flag associated with each descriptor stored within the internal storage unit to identify whether that descriptor is from the non-secure table or the secure table. By this approach, when the processor is operating in a non-secure mode, the memory management unit is operable to perform the predetermined access control functions for the memory access request with reference to access control information derived from the descriptors in the internal storage unit retrieved from the non-secure table. In contrast, when the processor is operating in a secure mode, the memory management unit is operable to perform the predetermined access control functions for the memory access request with reference to access control information derived from the descriptors in the internal storage unit retrieved from the secure table. This approach enables different descriptors to be used for the control of accesses to memory in either the secure domain or the non-secure domain, whilst enabling such different descriptors to co-exist within the memory management unit's internal storage unit, thereby avoiding the requirement to flush the contents of such an internal storage unit when the operation of the processor changes from the secure domain to the non-secure domain, or vice versa.
Owner:ARM LTD
Optical grain sorter
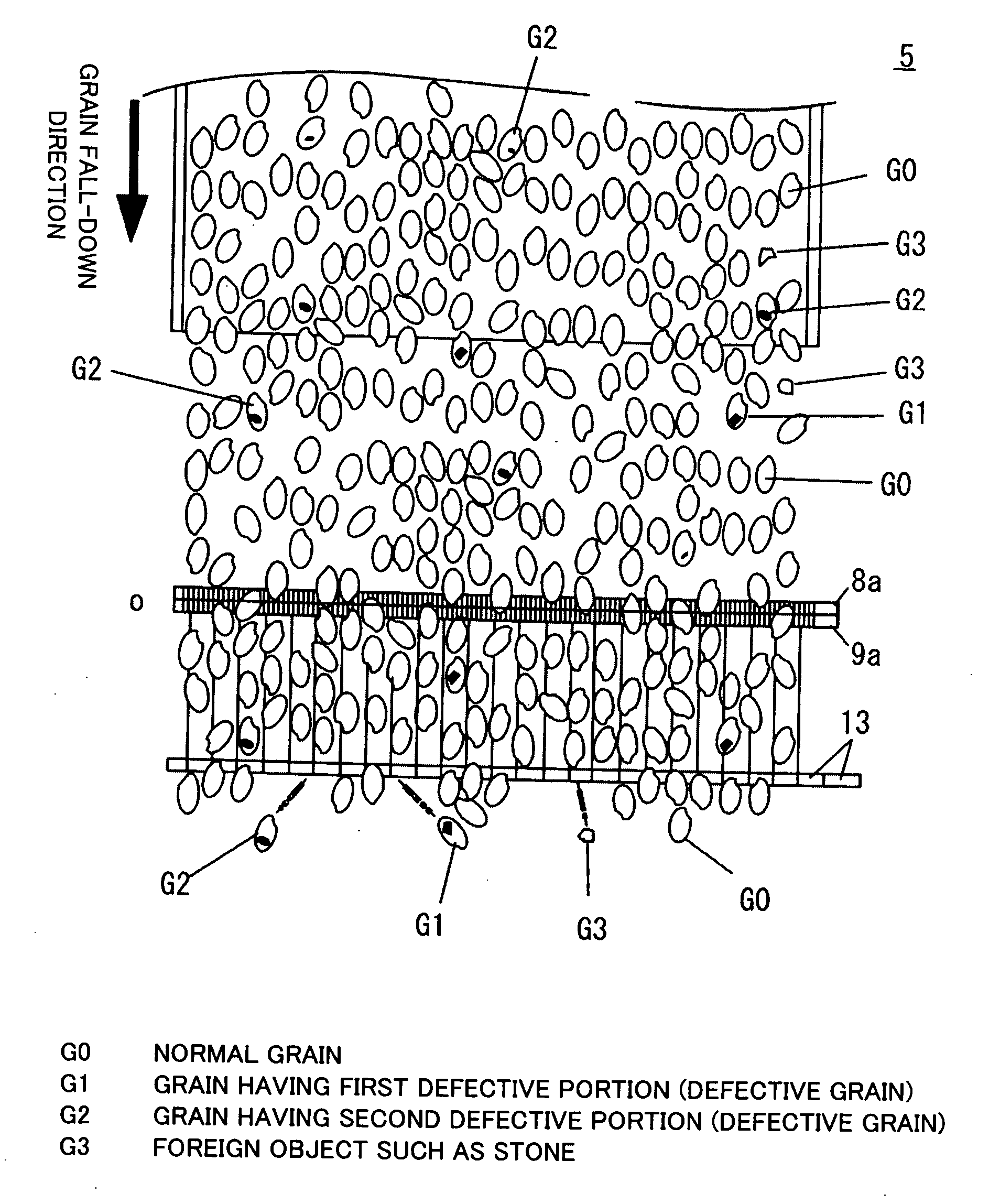
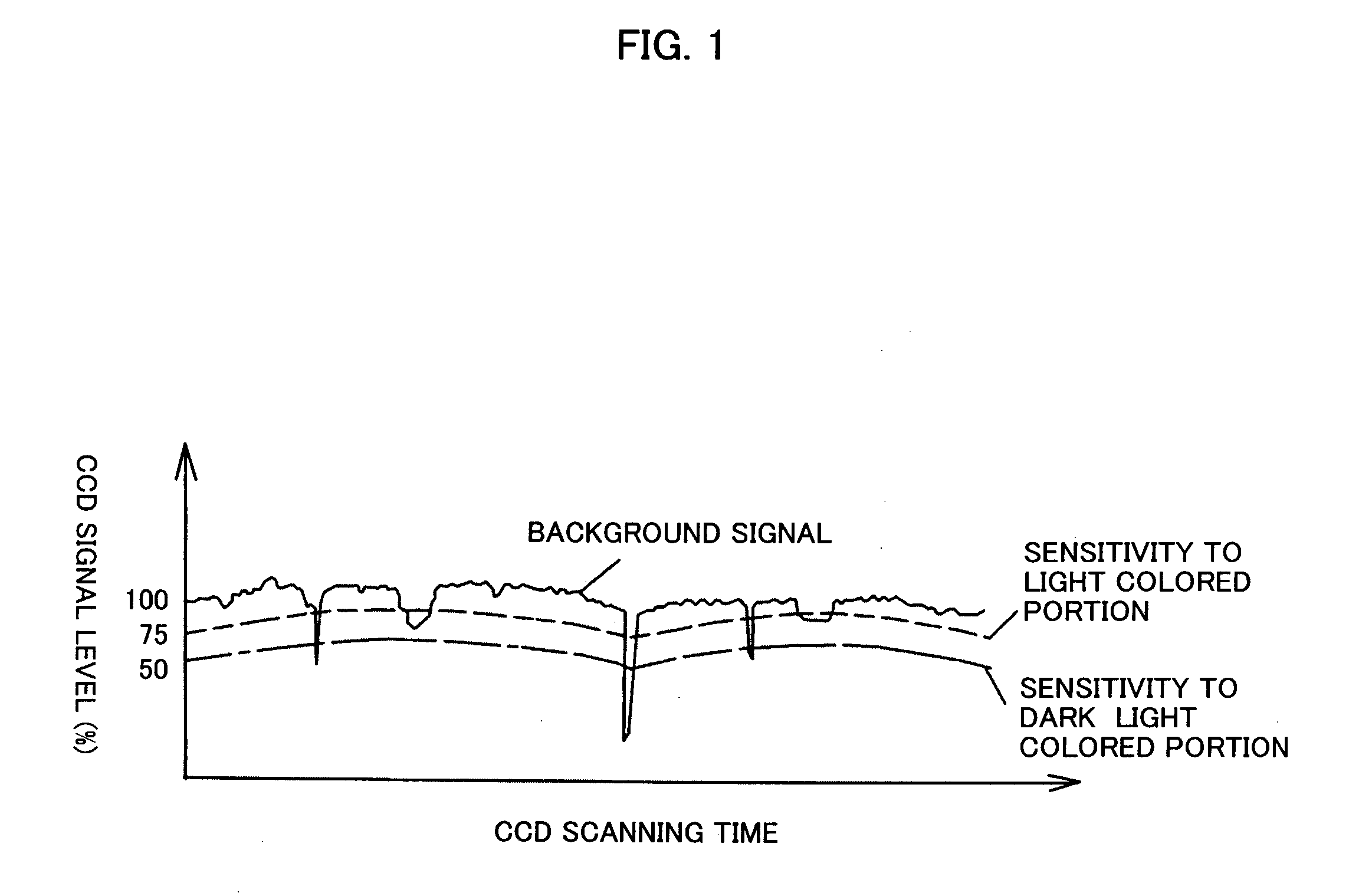
InactiveUS20090050540A1Clearly markedEasy to implementInvestigating moving fluids/granular solidsSeparation devicesLine sensorComputer graphics (images)
A grain images obtained by CCD line sensors are processed by binarization processing to obtain contour images of grains and images of colored portions in the grains. The images are displayed on a monitor screen of an operating panel 30. The contour images and the images of the colored portions are displayed in a superposed state. Box frames generated by a highlight display circuit in control means 12 are simultaneously displayed by being superposed on the contour images having defective portions, thus producing a highlight display of defective grains. The defective grains include a grain having a light colored portion and a grain having a dark colored portion.
Owner:SATAKE CORP
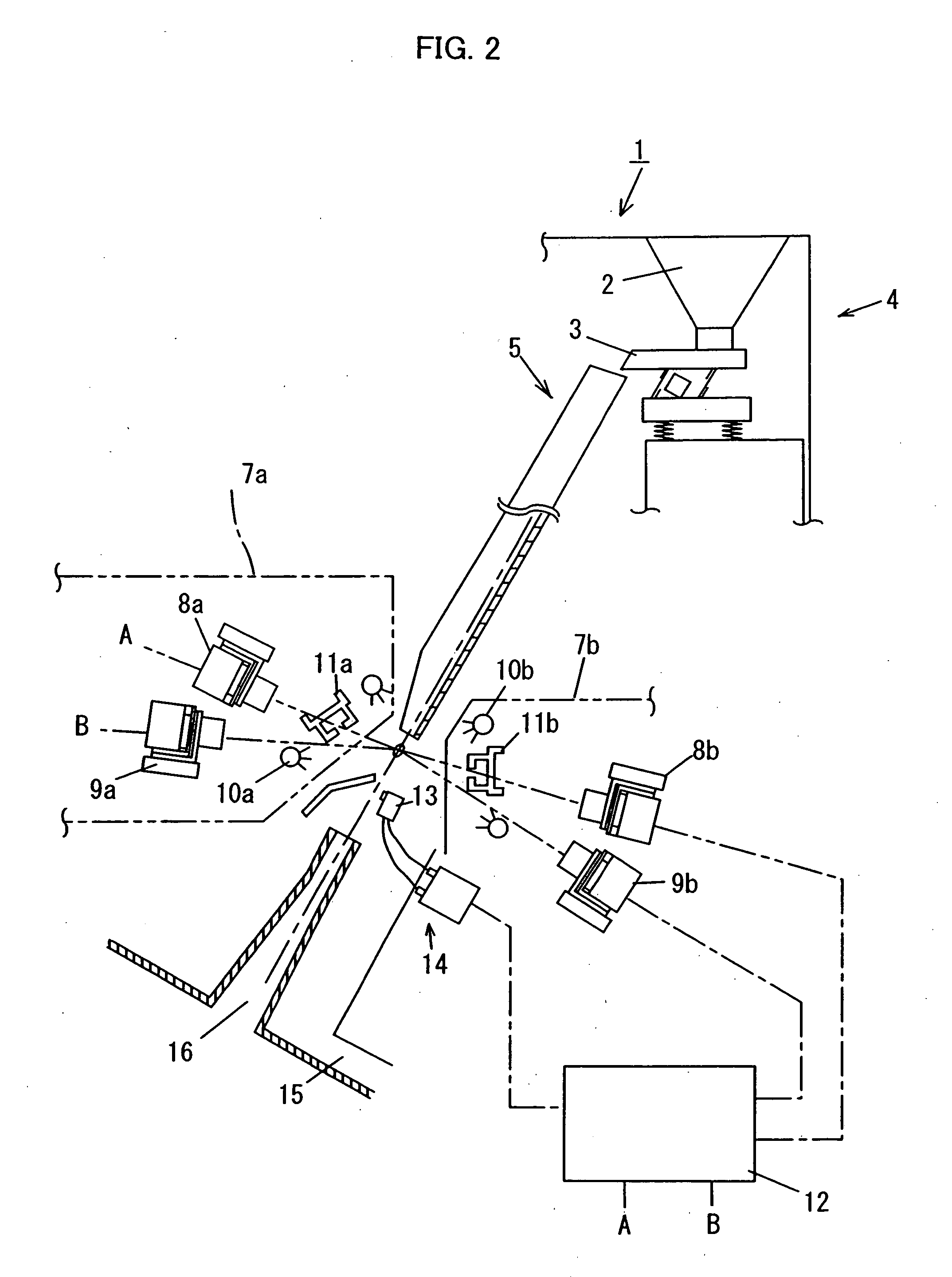
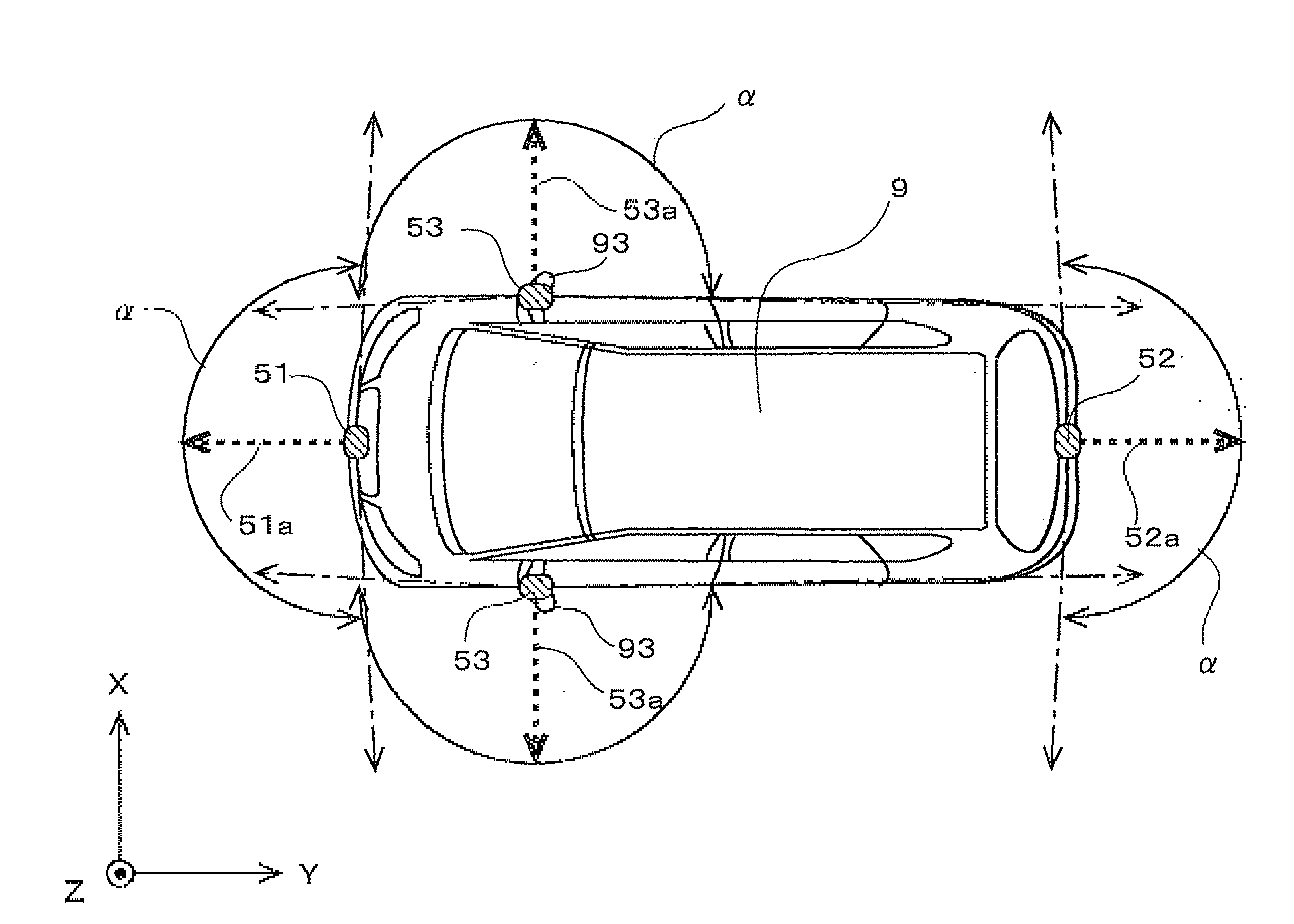
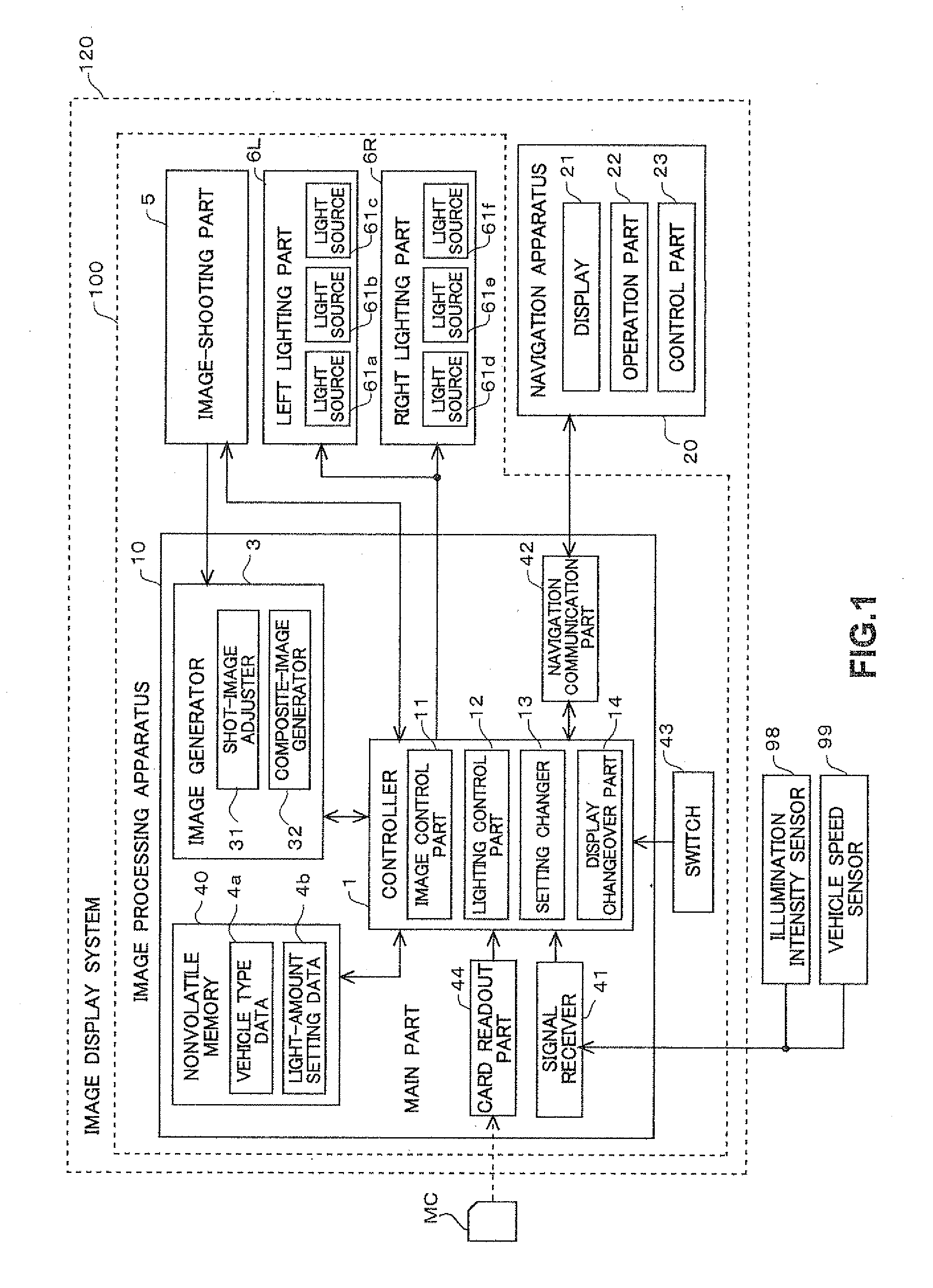
Image display system
InactiveUS20120002050A1Clearly markedEasy to changeRoad vehicles traffic controlColor television detailsLight sourceUser needs
An image display system includes a plurality of light sources respectively illuminating a plurality of divided regions. A user can change each of a plurality of light-amount parameters respectively specifying an amount of light to be output by each of the plurality of light sources by an operation on a change screen. Therefore, the user can illuminate each of the plurality of divided regions with an amount of light that he / she desires. As a result, the user can illuminate and definitely identify a subject difficult for the user to see and a subject to which the user needs to pay attention.
Owner:FUJITSU GENERAL LTD
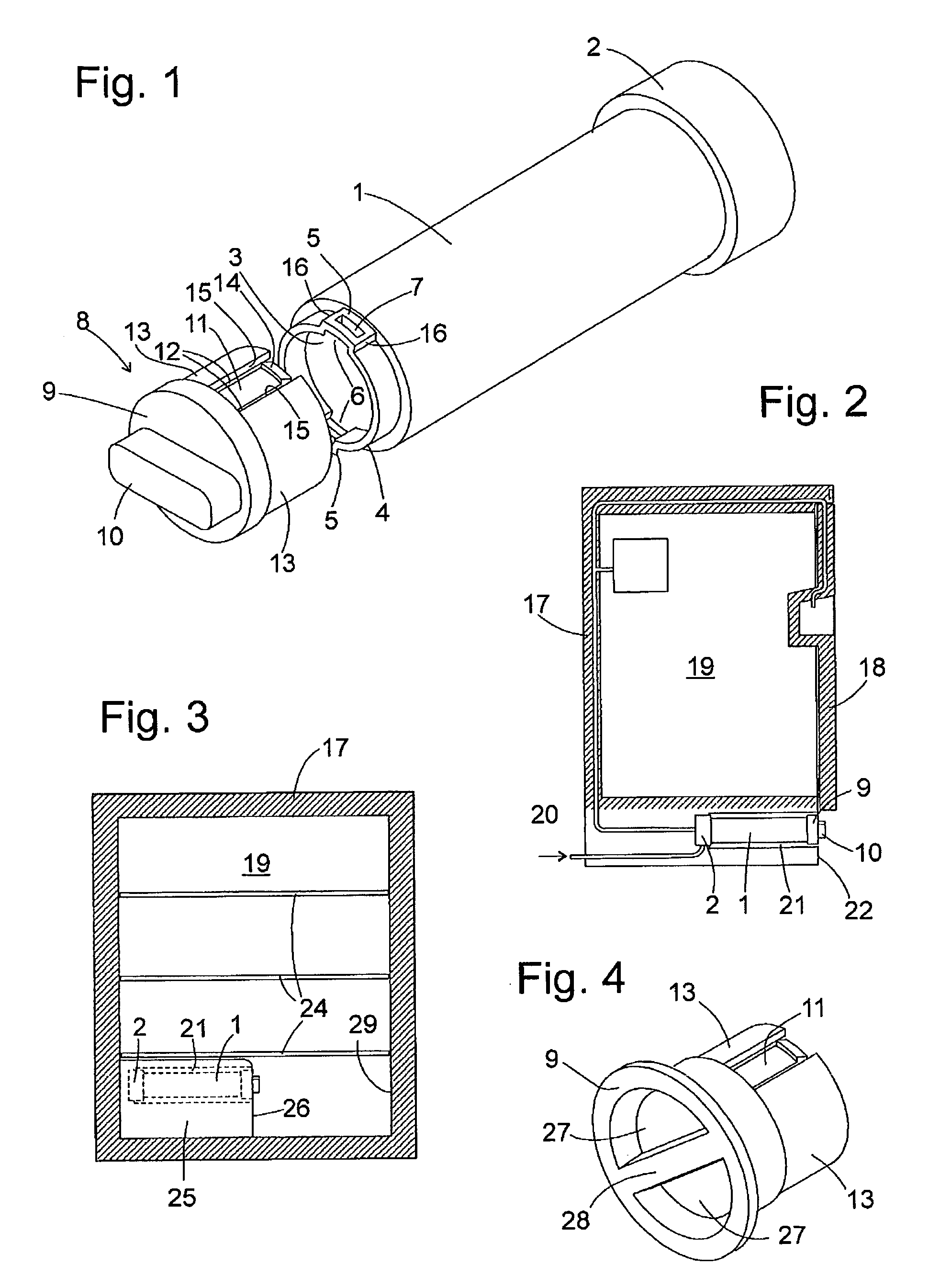
Refrigeration device and water filter for said device
InactiveUS8354024B2Clearly markedLighting and heating apparatusDomestic refrigeratorsWater filterEngineering
A water filter for a refrigeration appliance has a housing (1), which contains a filter material and has a fitting for mounting in a filter socket (2) at one end. A grip portion (8) is attached to an opposite end (3) of the housing (1).
Owner:BSH BOSCH & SIEMENS HAUSGERAETE GMBH
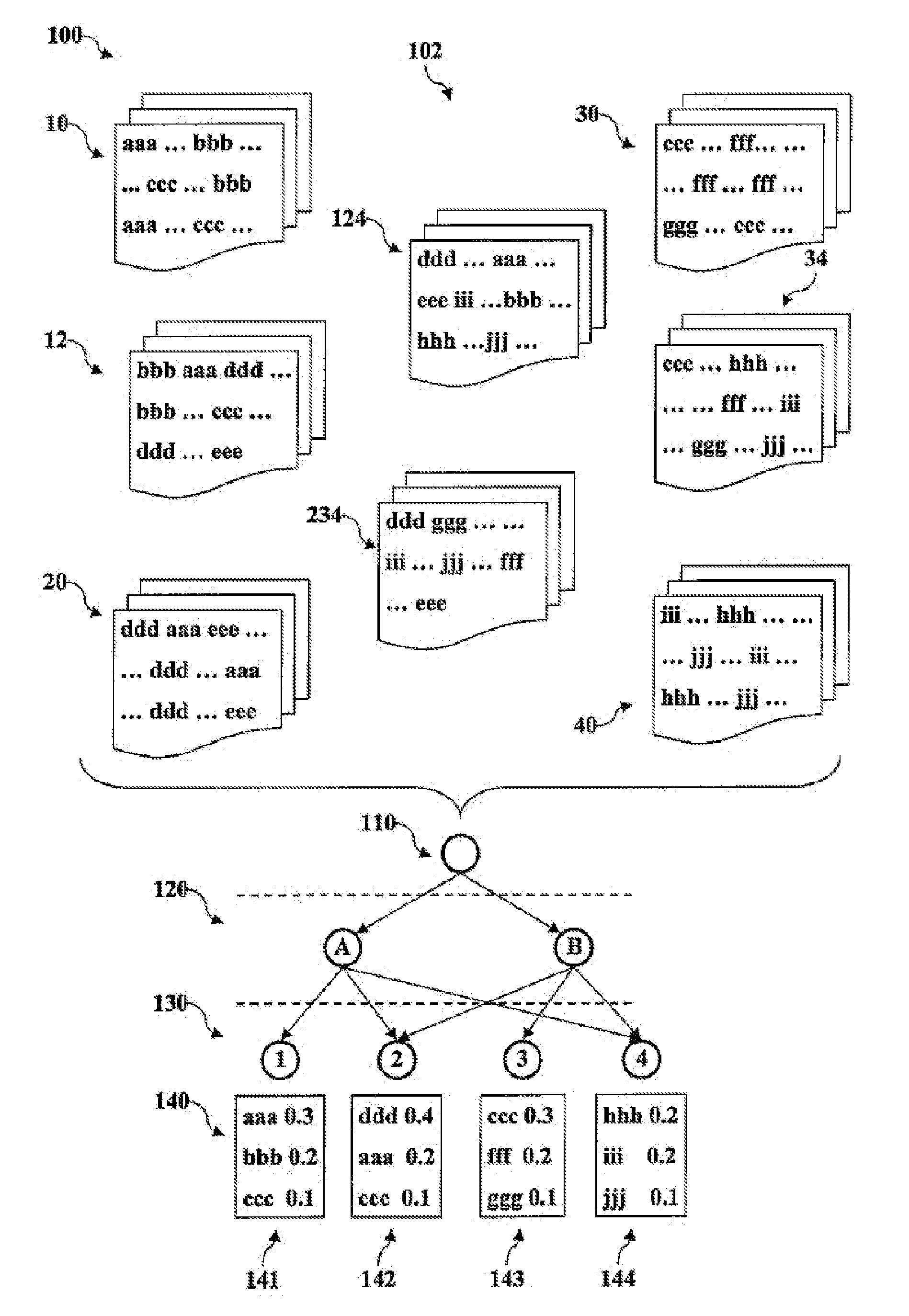
System and method for identifying and visualising topics and themes in collections of documents
InactiveUS20150046151A1Clearly markedSemantic analysisSpecial data processing applicationsSubject matterDocument preparation
Owner:BAE SYSTEMS AUSTRALIA
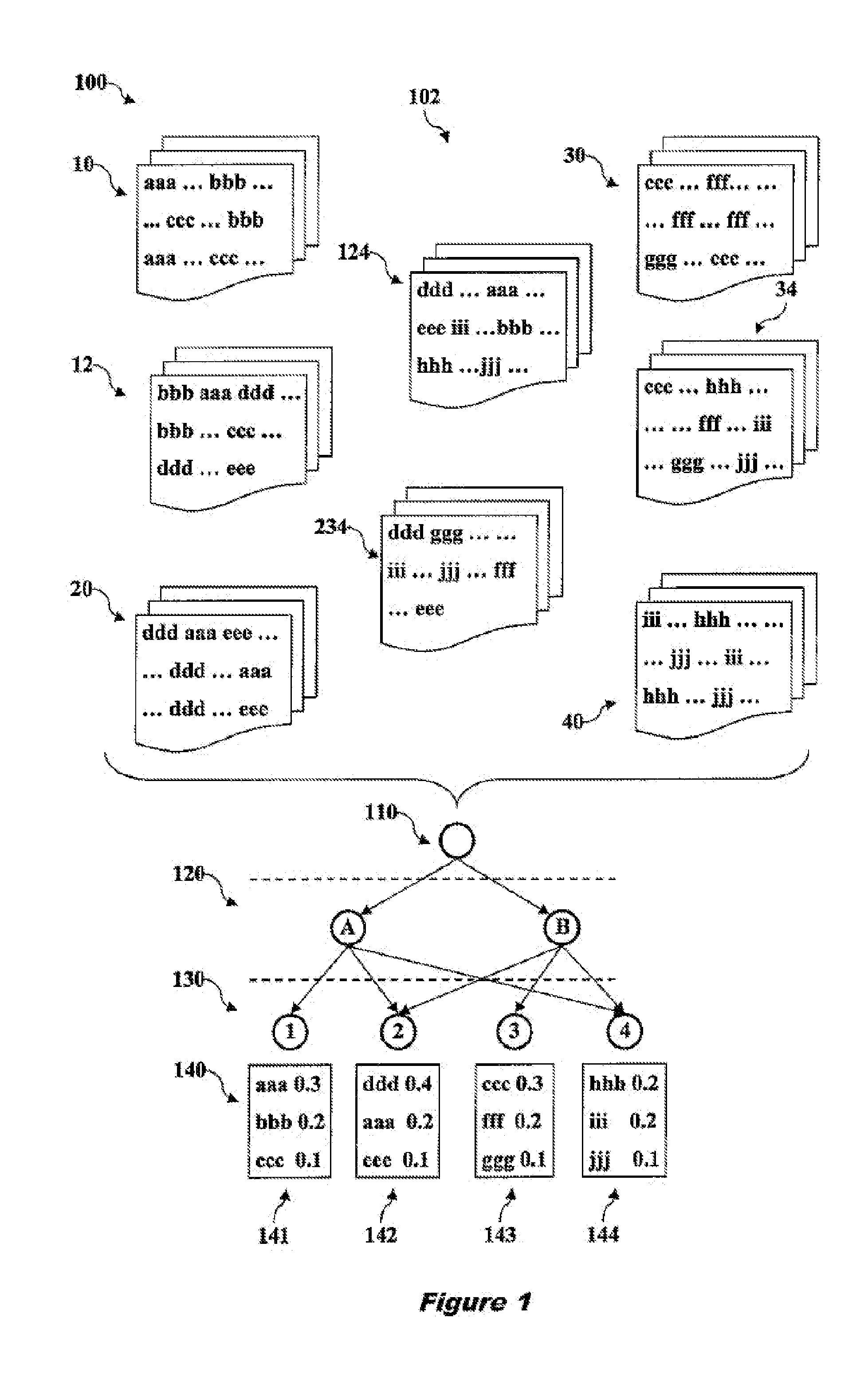
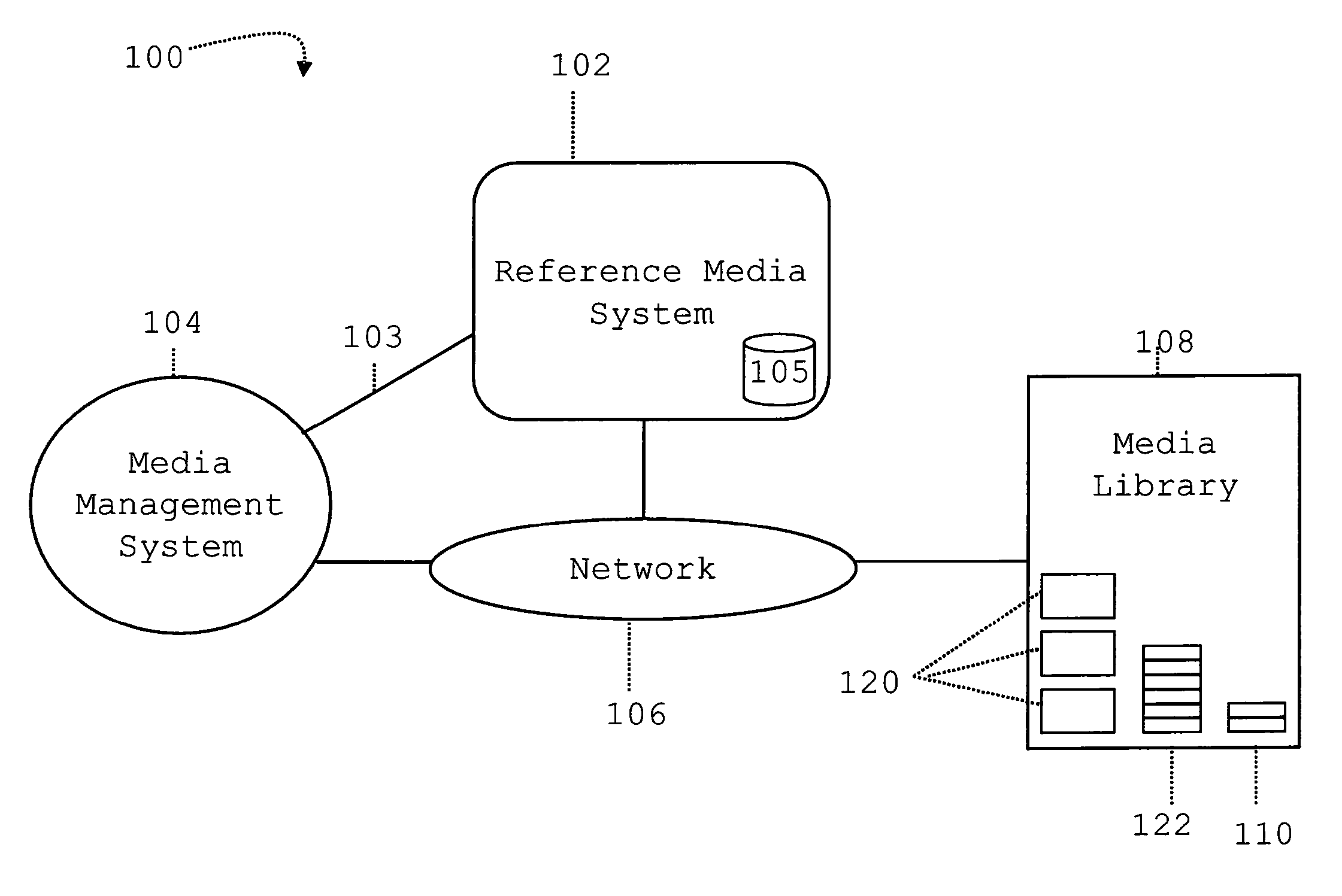
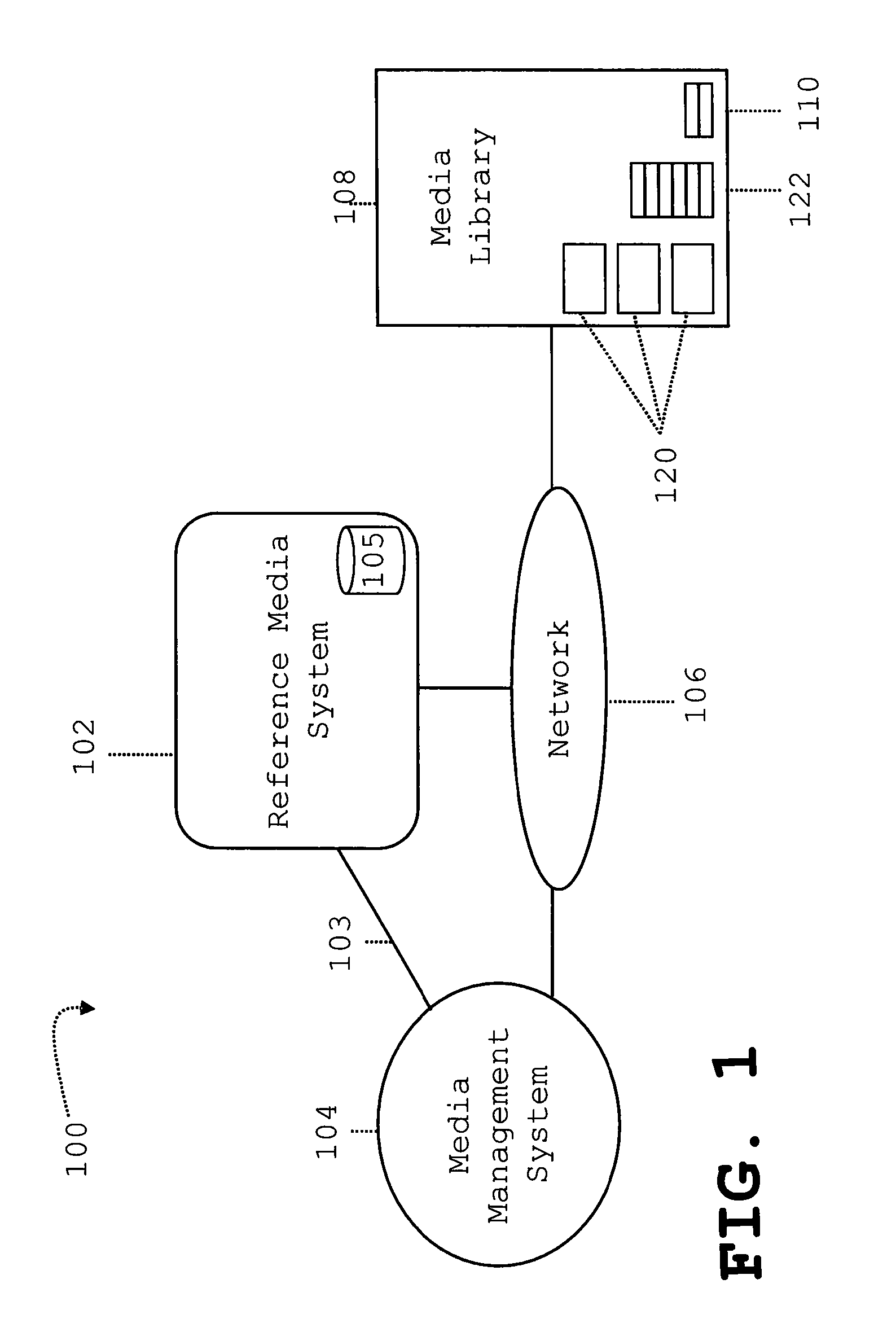
Monitoring and Analyzing the Storage Quality and the Drive Hardware Performance of a Media Library
InactiveUS20090059757A1Clearly markedWith balanceCombination recordingOptical discsManagement systemRemovable media
A method and infrastructure are provided for monitoring and analyzing the storage media quality and the drive hardware performance of a media library. The media library comprises a plurality of removable storage media, a plurality of drive units for said storage media and means for moving said storage media to and from appropriate drive units. The media library is managed by a management system being connected to said media library. At least one reference medium of a known and proven quality to compare the performance of at least one of said storage media in a given drive unit with the performance of said reference medium in said given drive unit and / or to test the performance of at least one given drive unit of said media library when acting on said reference medium.
Owner:IBM CORP
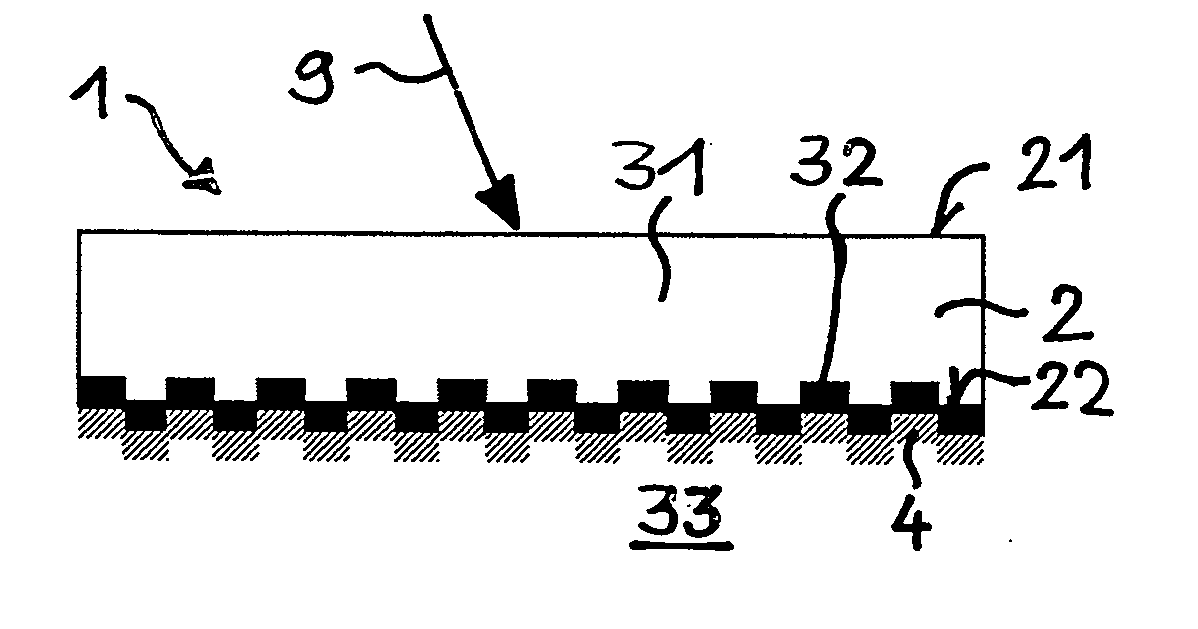
Diffractive optical security device
InactiveUS20070081246A1High level of security against counterfeitingMitigate such drawbackDiffraction gratingsInformation cardsRefractive indexMirror image
The diffractive optical device (1) can be used as a security device in the fields of authentication, identification and security. It comprises a zero-order diffractive color filter (3). The diffractive color filter may consist of a microstructured high-index layer (32) embedded between two low-index layers (31, 33). A mirror layer (4) for reflecting towards the diffractive color filter (3) at least part of light transmitted through the diffractive color filter (3) are provided beneath the diffractive color filter. Thanks to the mirror layer (4), the device (1) has a much higher reflected intensity and much more complex spectra than prior-art diffractive color filters.
Owner:CSEM CENT SUISSE DELECTRONIQUE & DE MICROTECHNIQUE SA RECH & DEV
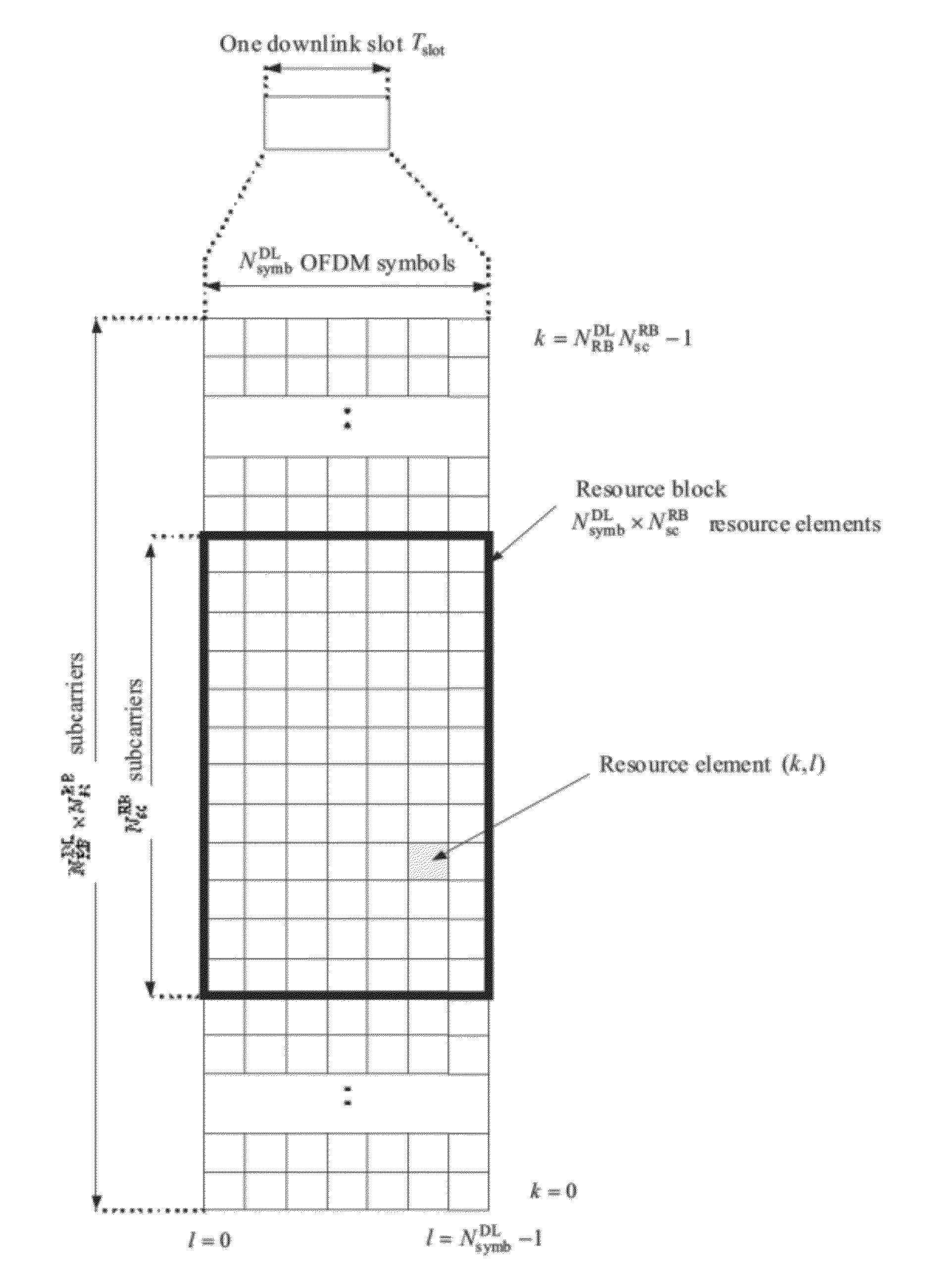
Implicit component carrier determination for aperiodic channel quality reports
ActiveUS20120307757A1Efficient use ofEfficient and flexibleTransmission path divisionSignal allocationCarrier signalEngineering
The present invention relates to triggering, in a terminal of a communication system, channel quality feedback reporting for at least one of plural component carriers of the communication system available for downlink transmission. The at least one component carrier is selected based on the downlink traffic of the terminal. Reporting of the channel quality information is triggered by dedicated control information received by the terminal.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
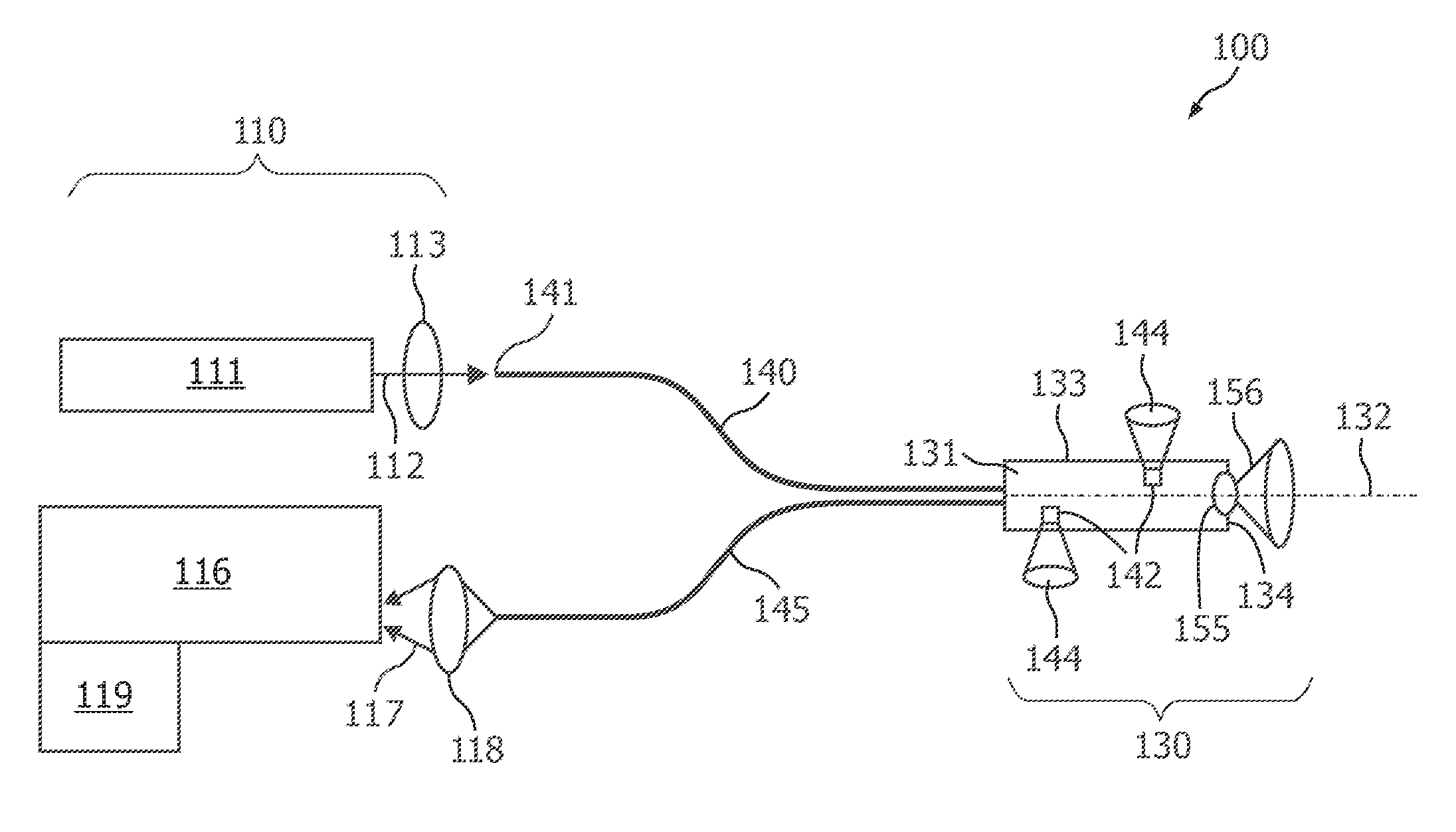
Obtaining optical tissue properties
InactiveUS20090326385A1Minimize the numberImprove accuracyDiagnostics using spectroscopyCatheterFiberOptical tomography
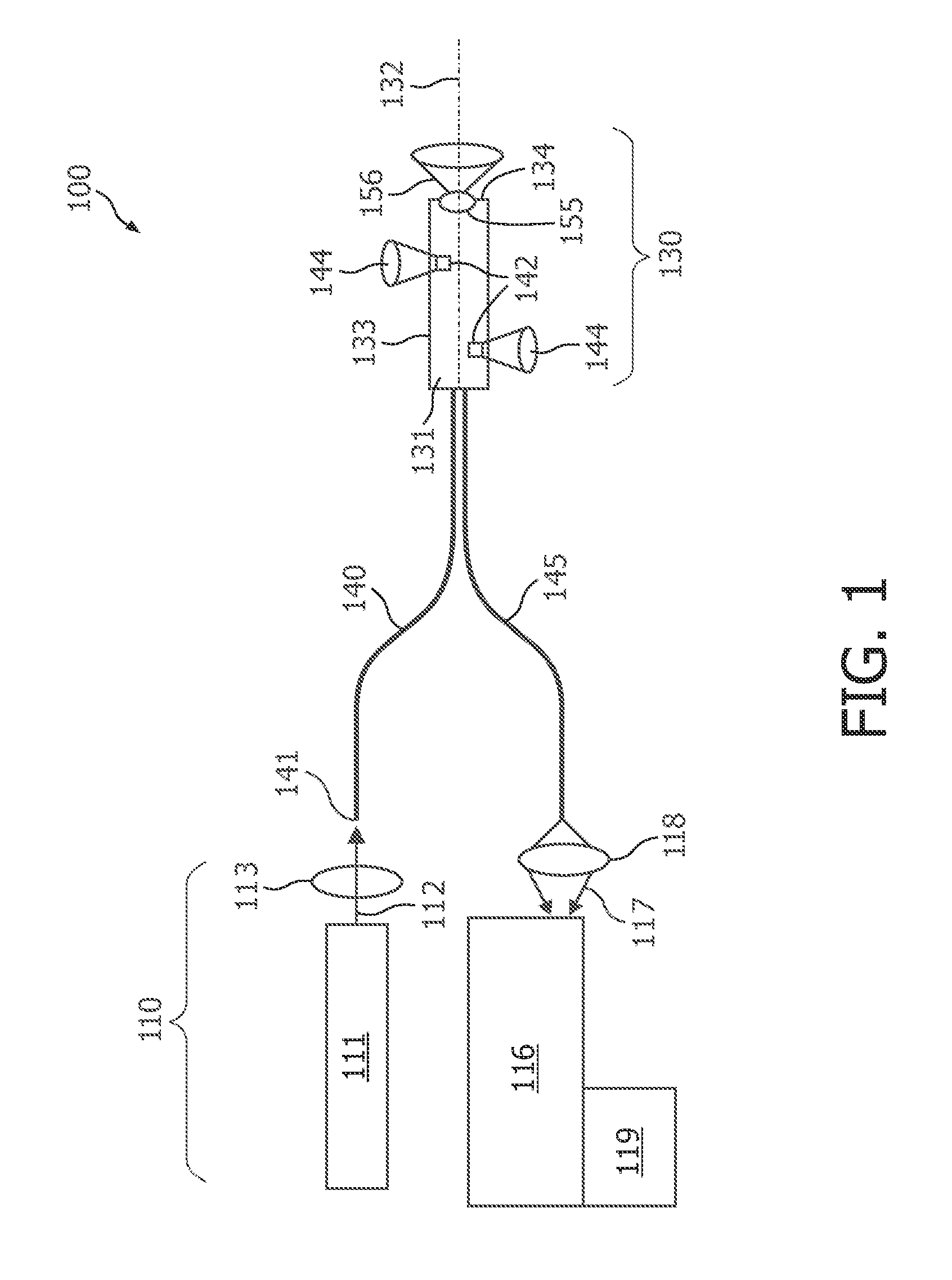
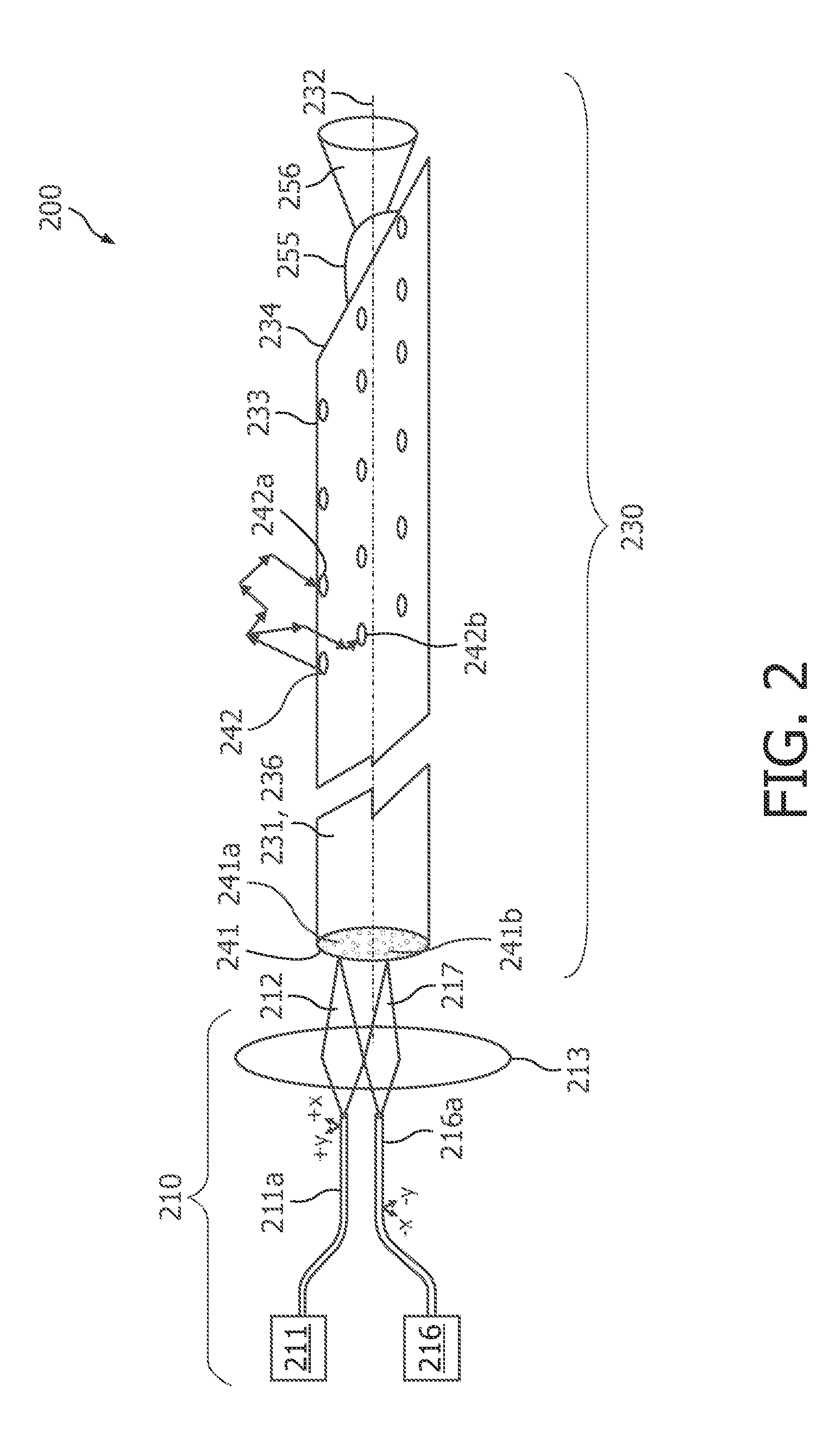
This application describes a medical device (230) for obtaining optical tissue properties of a target material. The medical device (230) comprises an elongated body (231) having a longitudinal axis (232) and an optical fiber being integrated within the elongated body (231). The optical fiber has a second fiber end (242, 242a, 242b), which is arranged at a side wall (233) of the elongated body (231) and which provides a lateral field of view with respect to the longitudinal axis (232). According to an embodiment many optical fibers are integrated each having an optical outlet (242, 242a, 242b) around the elongated body (231). Using the outlets (242, 242a, 242b) to do diffuse optical tomography and also use optical fibers to do an optical inspection, one can get information on the presence of tumors in a volume around the medical device (230) and a tissue characterization in the vicinity of the medical device (230). Thereby, an optical biopsy may be carried out, wherein no real tissue is removed. According to another embodiment an optical detection system is integrated into a real biopsy needle (330) allowing inspection and taking real biopsy simultaneously.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
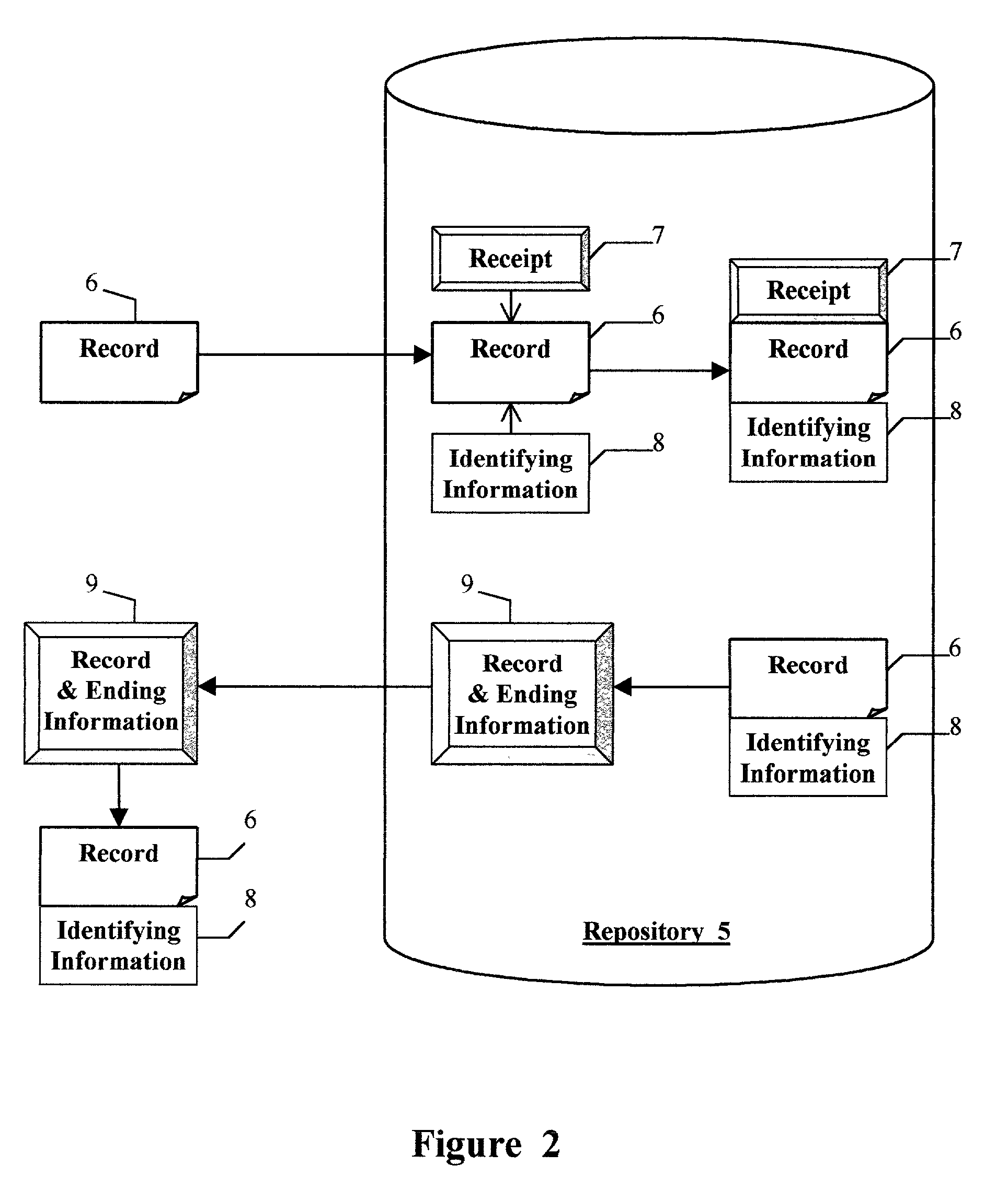
System for obtaining signatures on a single authoritative copy of an electronic record
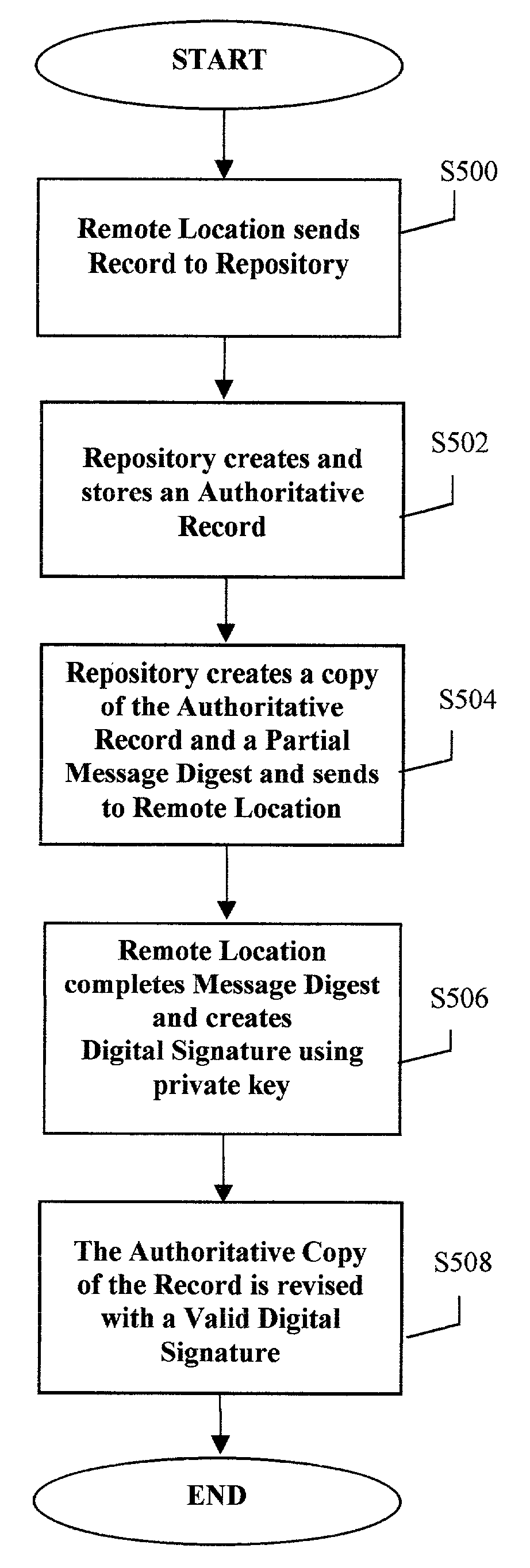
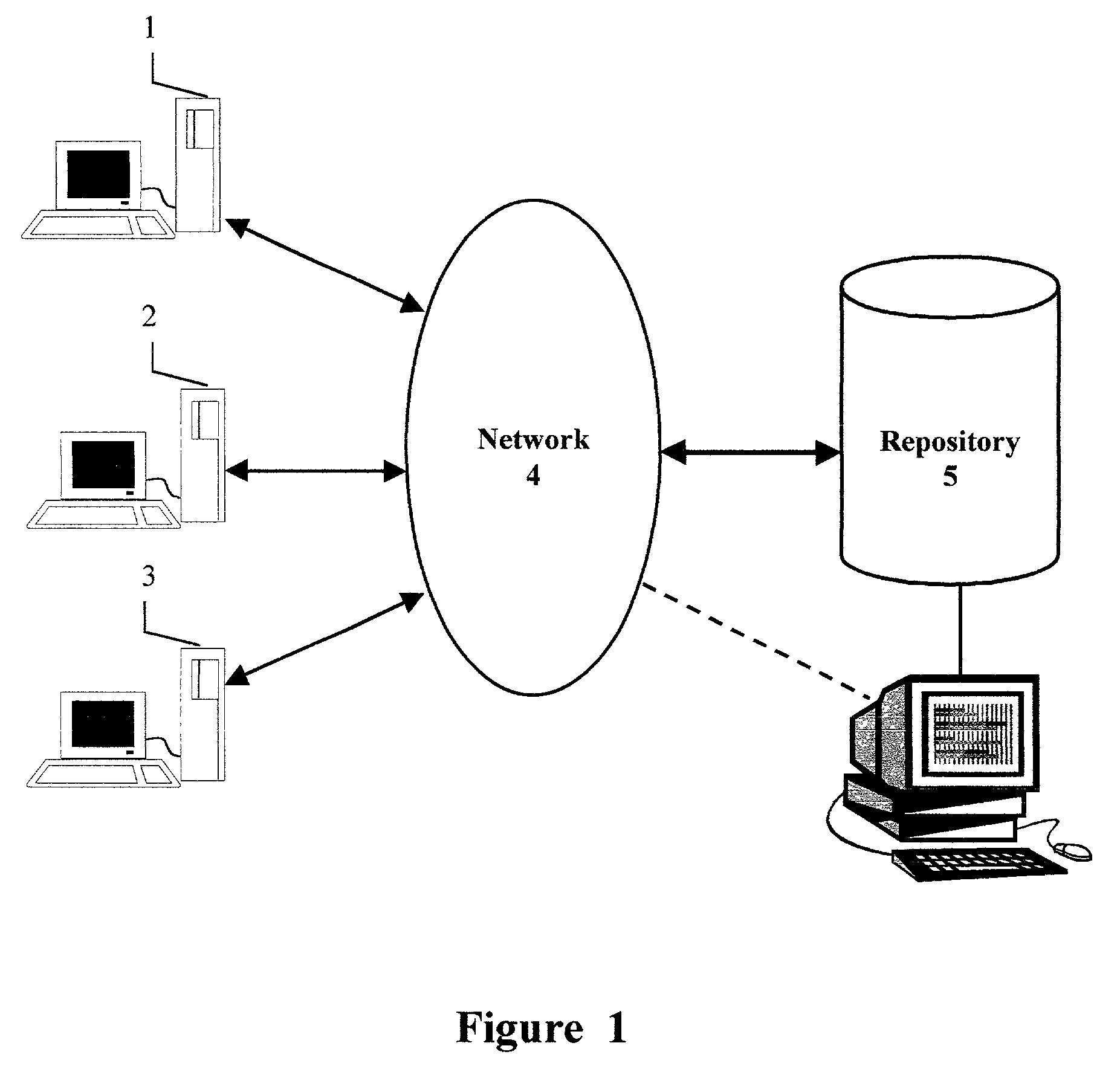
ActiveUS7146500B2Clearly markedDigital data processing detailsUser identity/authority verificationDigital signatureControl software
A method and apparatus for maintaining control of a record which may have transferable value wherein the system provides for digitally signing a record in a partially-trusted distributed environment and allows a single unique authoritative copy to be held at a repository. The system meets the uniqueness and retainability requirements of current legislation relating to electronic transactions and allows electronic records to receive the same legal enforceability as paper documents. One or more secure servers along with maintenance control software provide the secure environment for parties wishing to complete electronic transactions to form legally enforceable agreements.
Owner:COMPASS TECH MANAGEMENT
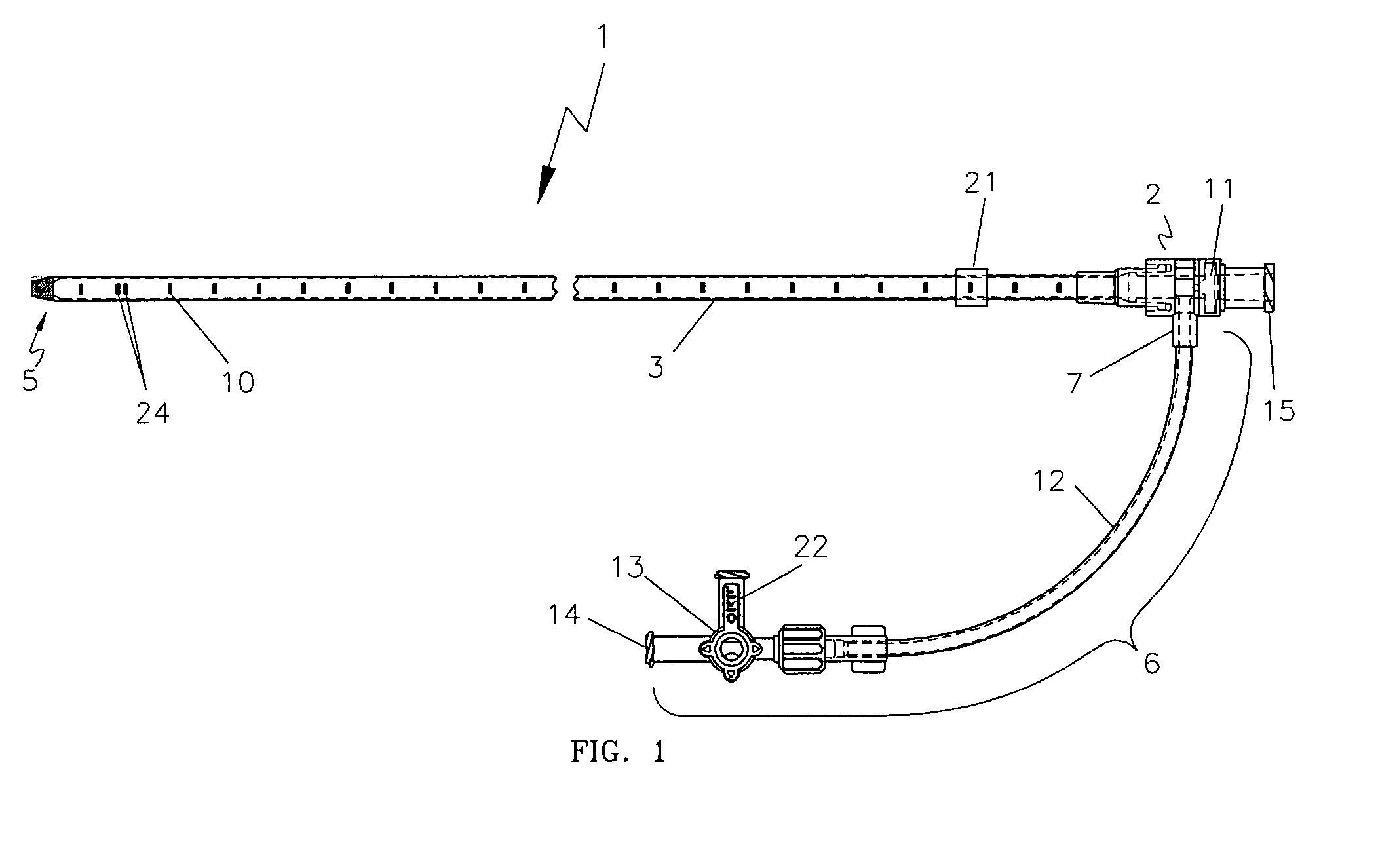
Passive Tamper-Resistant Seal And Applications Therefor
ActiveUS20120235815A1Clearly markedBurglar alarm with fastening tamperingContainer decorationsEngineeringRadio frequency
A radio frequency identification seal comprises an antenna including a main antenna portion and at least one break-away portion and an RFID tag coupled and tuned to the antenna. The RFID tag outputs a signature in response to a scanning signal when tuned to the antenna.
Owner:COVELEY SOLBYUNG
Steel bar binding space distance identification device
ActiveCN103174296AAccurate steel bar binding spacingClearly markedBuilding material handlingIdentification deviceRebar
The invention provides a steel bar binding space distance identification device which comprises two locating clips, an upper connecting piece, a lower connecting piece, a scaleplate and vernier pens. The scaleplate is arranged between the upper connecting piece and the lower connecting piece. The two locating clips are arranged at two ends of the scaleplate, the upper connecting piece and the lower connecting piece. Short tail clip head portions of the two locating clips are connected with the lower connecting piece. Long tail clip tail portions of the two locating clips are connected with the upper connecting piece. The scaleplate is provided with a plurality of vernier pens. The steel bar binding space distance identification device is convenient to operate and high in efficiency. A conventional steel bar binding space distance line-drawing identification needs two persons for matching operation, and when the steel bar binding space distance identification device is used for steel bar binding space distance line-drawing identification, only one person is needed. When the steel bar binding space distance identification device is used for steel bar binding space distance line-drawing identification, working efficiency can be improved by 8-10 times.
Owner:SINOHYDRO BUREAU 14 CO LTD
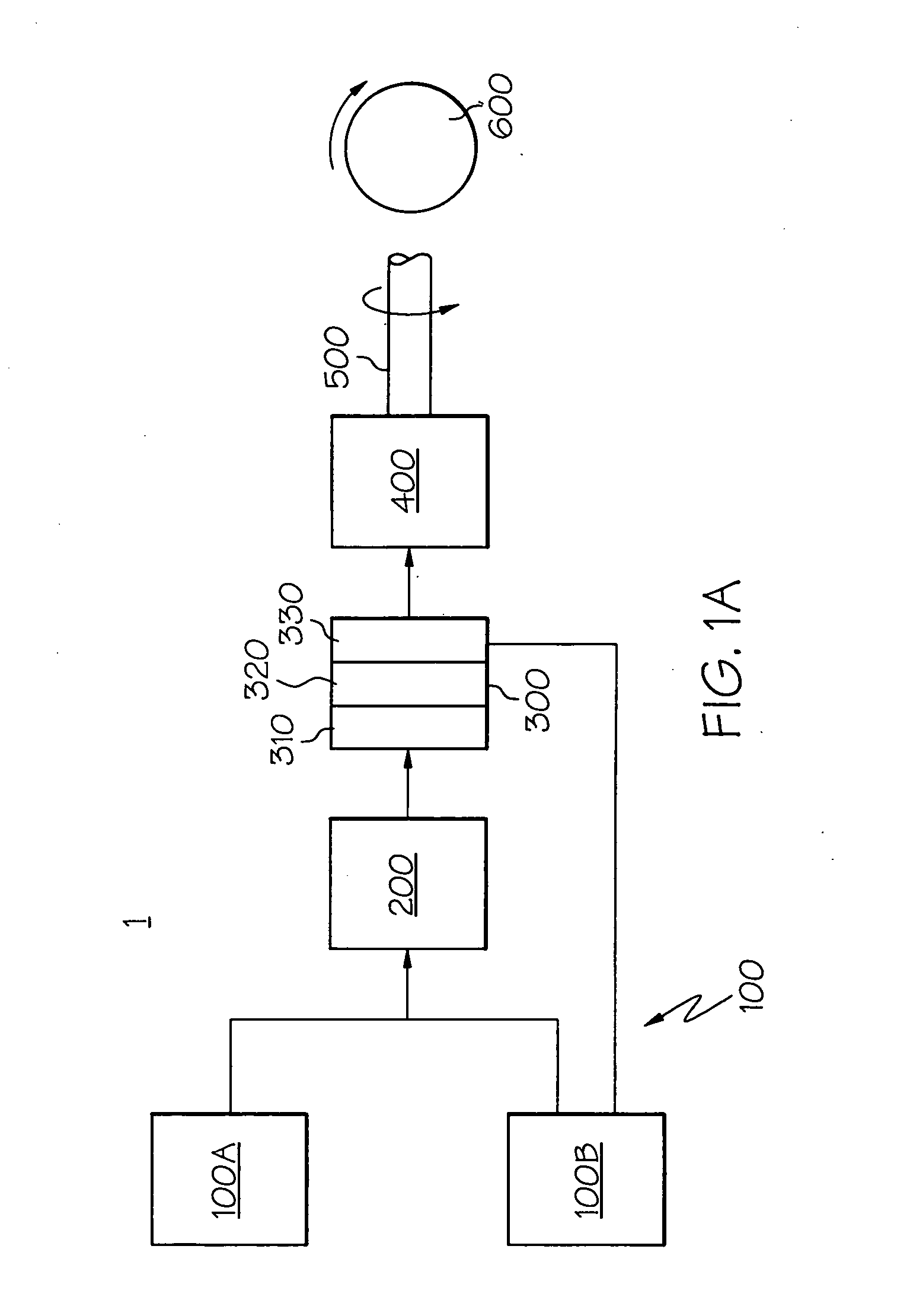
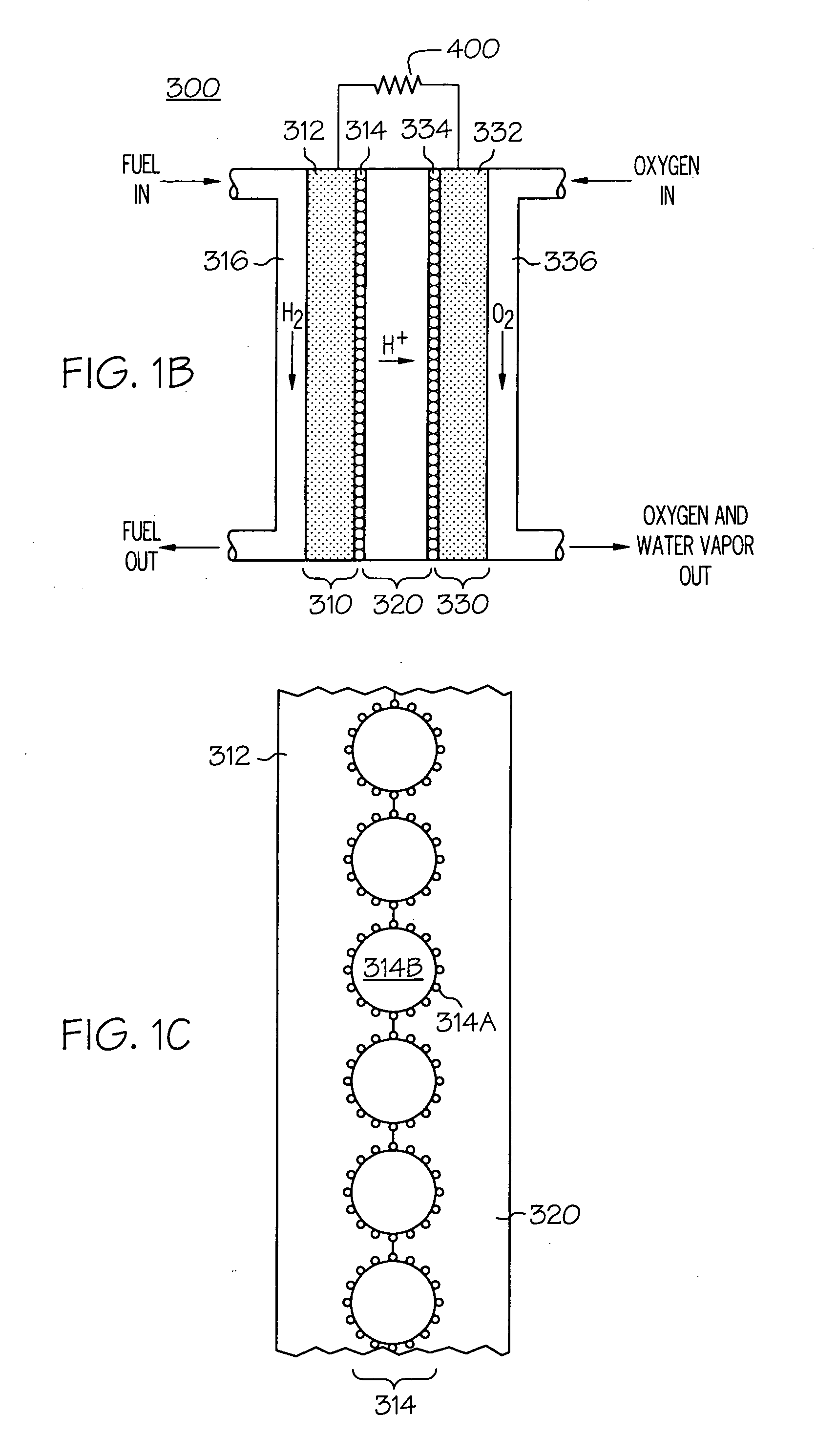
Fuel cell shutdown and startup using a cathode recycle loop
InactiveUS20050058860A1Simple configurationEasy to operateFuel cell heat exchangeSolid electrolyte fuel cellsFuel cellsHydrogen
A method and device for operating a fuel cell system. A recirculation loop coupled to a fuel cell cathode ensures that fluids passing through the cathode are recycled, thereby enabling reaction between residual oxygen in the recycled fluid and fuel that has been introduced into the recirculation loop until a reduced voltage level across the fuel cell is achieved. Attainment of the reduced voltage level indicates that the recycled fluid is substantially oxygen-free, yielding an inerting fluid. Thereafter, this compound, followed by air, or air directly can be used to purge the fuel cell's anode and related flowpath during system shutdown. Similarly during system startup, hydrogen can then be introduced into the fuel cell's anode and then air into the cathode and related flowpath for normal operation. The placement of a purge valve allows the anode to be purged with air without re-introducing air into the cathode.
Owner:GM GLOBAL TECH OPERATIONS LLC
Merged images viewed via a virtual storage closet
InactiveUS20050071257A1Improve shopping experienceClearly markedBuying/selling/leasing transactionsSpecial data processing applicationsE-commerceImage View
An e-commerce method involves on-line viewing of a first article through a linking node for virtual merging on another structure. A particular application of the invention is directed to a method of on-line apparel shopping. The method includes providing a host-site accessible to an on-line viewer (customer) and web-linkable to a retailer having an apparel site. The retailer's apparel site has images of articles stored in a virtual closet. These articles can be apparel from retail stores for viewing over the web, and the on-line viewer is linked to the host-site. The consumer selects a structure, such as a photograph of a person captured in system memory, in response to a command received by the on-line viewer. Using the host-site, the viewer or customer is linked to the retailer's apparel site and images are passed from that site for view by the customer. Apparel is selected and virtually merged with the structure by forming an image including representations of both the structure and the selected-apparel.
Owner:TAMIRAS PER PTE LTD LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com