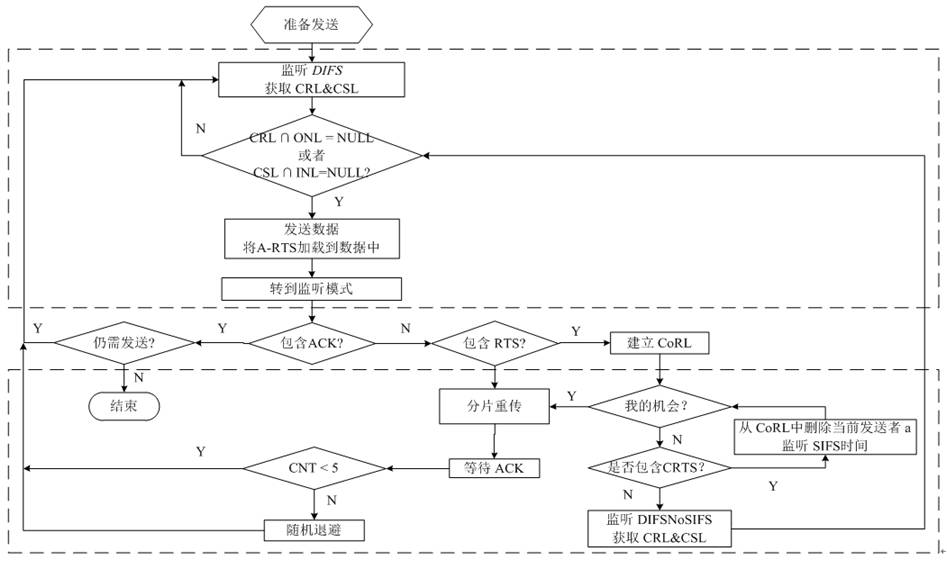
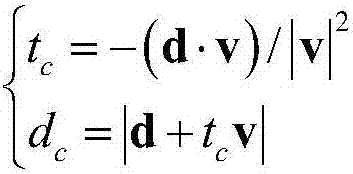Patents
Literature
60 results about "Collision domain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
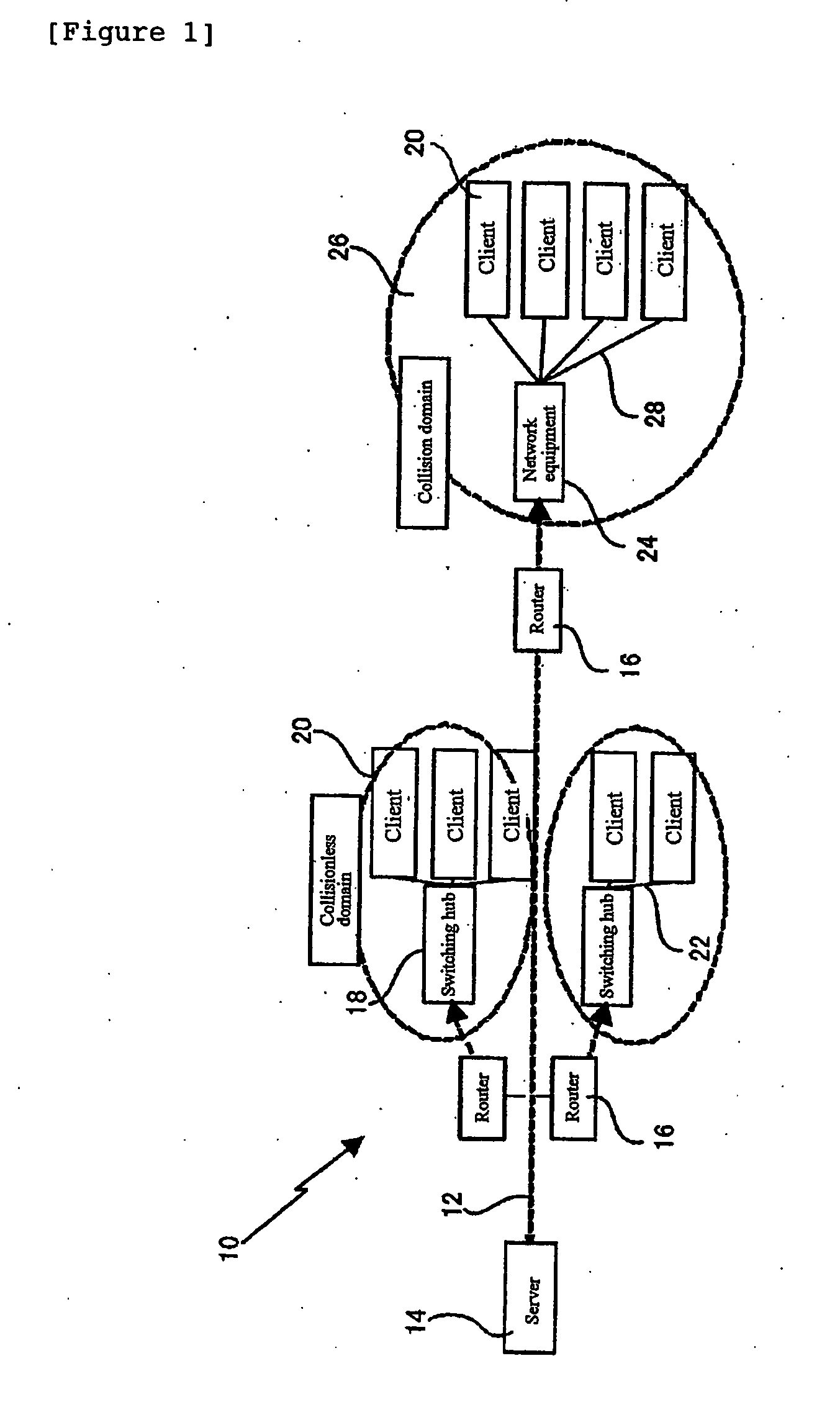
A collision domain is a network segment connected by a shared medium or through repeaters where simultaneous data transmissions collide with one another. The collision domain applies particularly in wireless networks, but also affected early versions of Ethernet. A network collision occurs when more than one device attempts to send a packet on a network segment at the same time. Members of a collision domain may be involved in collisions with one another. Devices outside the collision domain do not have collisions with those inside.
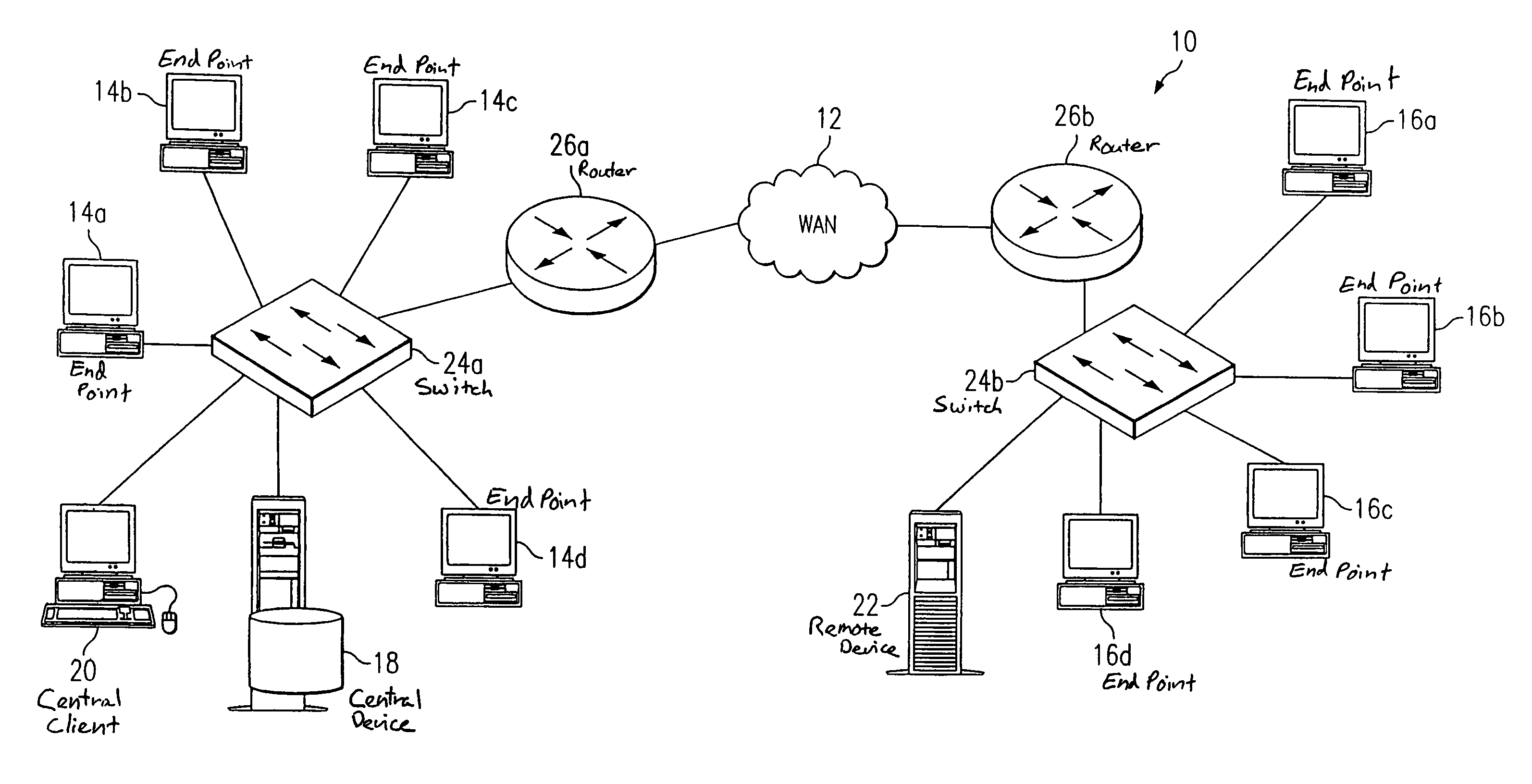
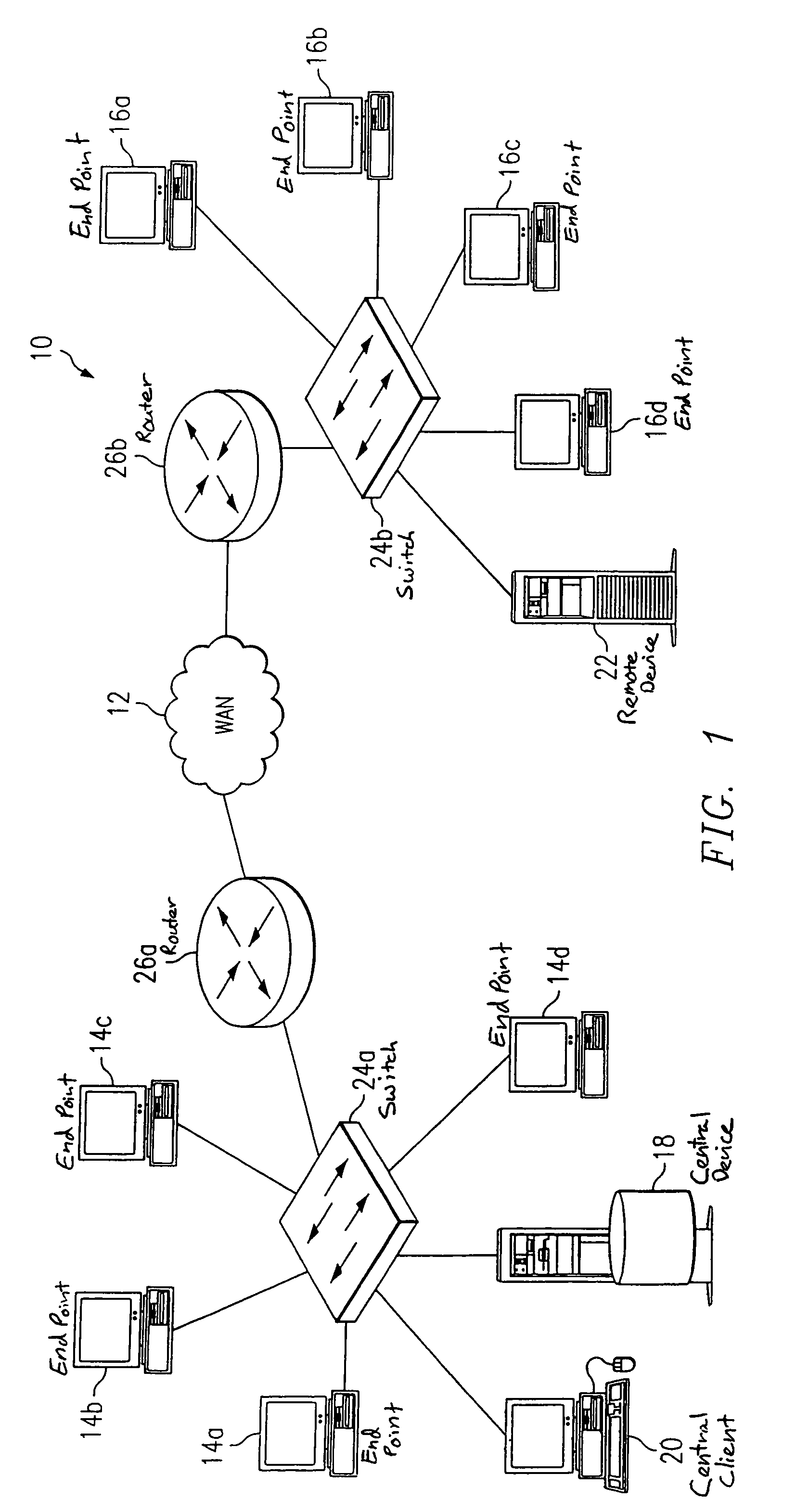
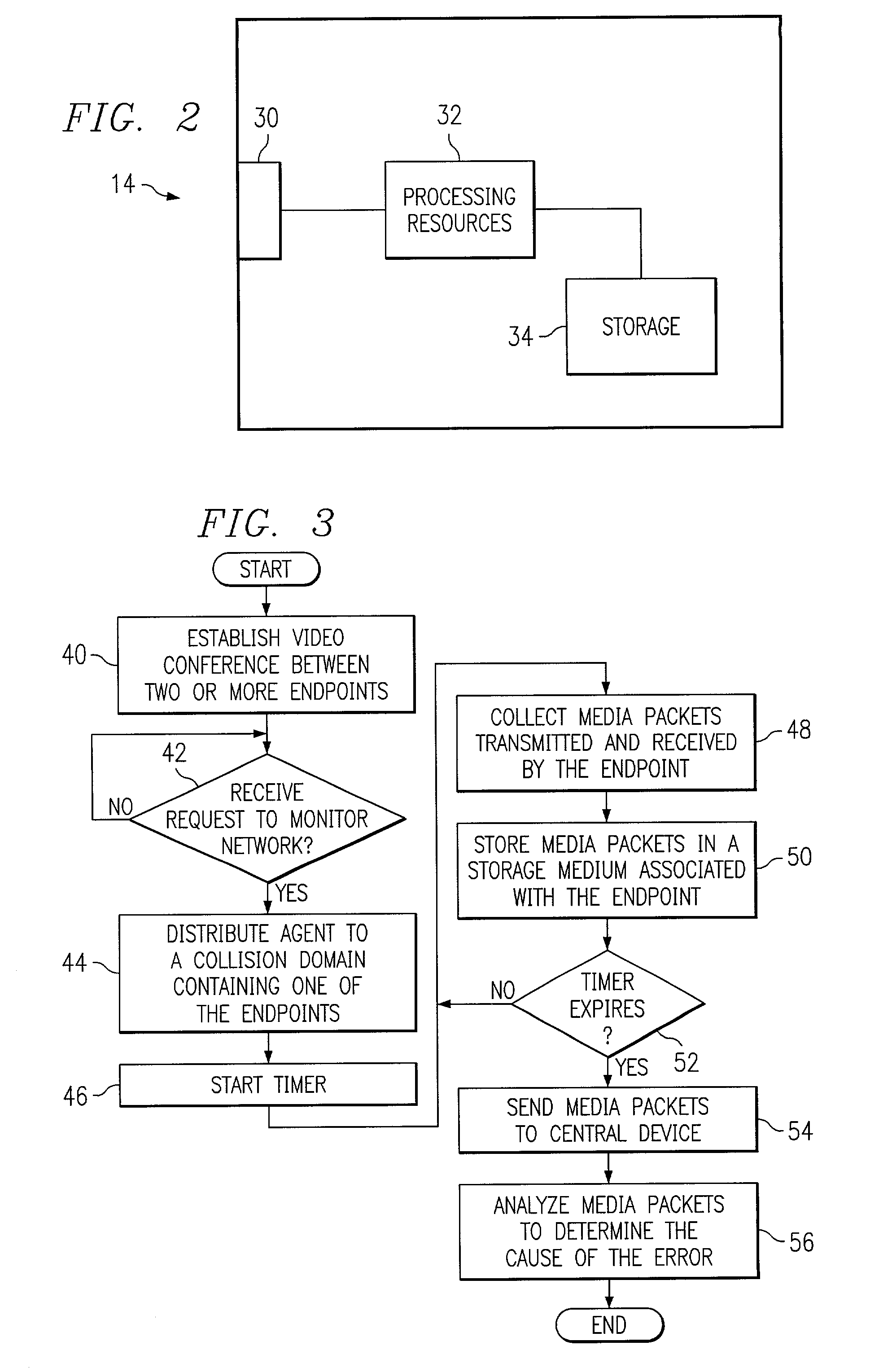
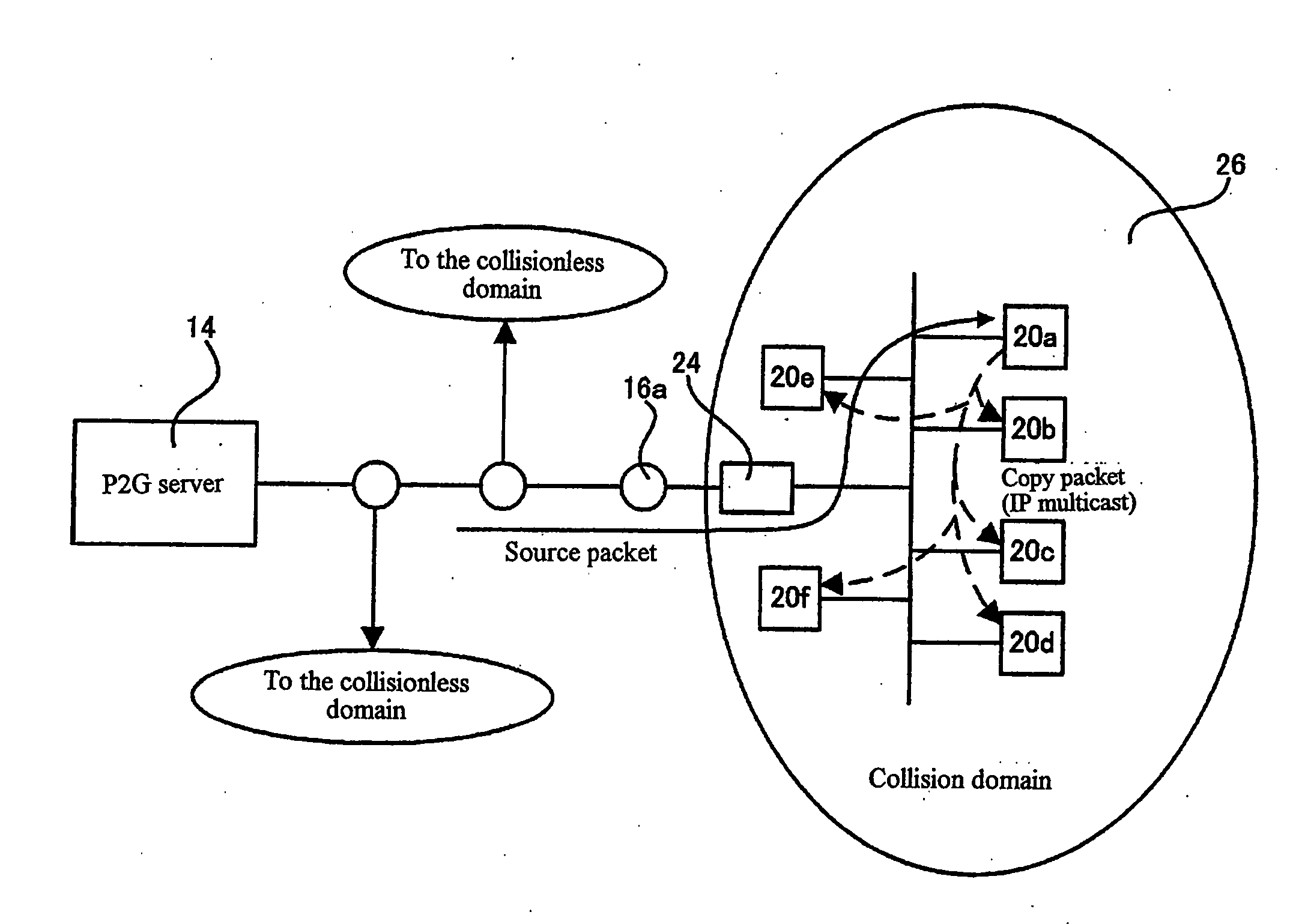
System and method for identifying errors in a video conference conducted on a packet-based network
InactiveUS7061871B2Reduce network trafficPrecise processSpecial service provision for substationMultiplex system selection arrangementsCollision domainTimer
Owner:CISCO TECH INC
Digital content delivery, server and client
InactiveUS20050021817A1Improve efficiencyEasy to takeSpecial service provision for substationMultiple digital computer combinationsDigital contentNumber content
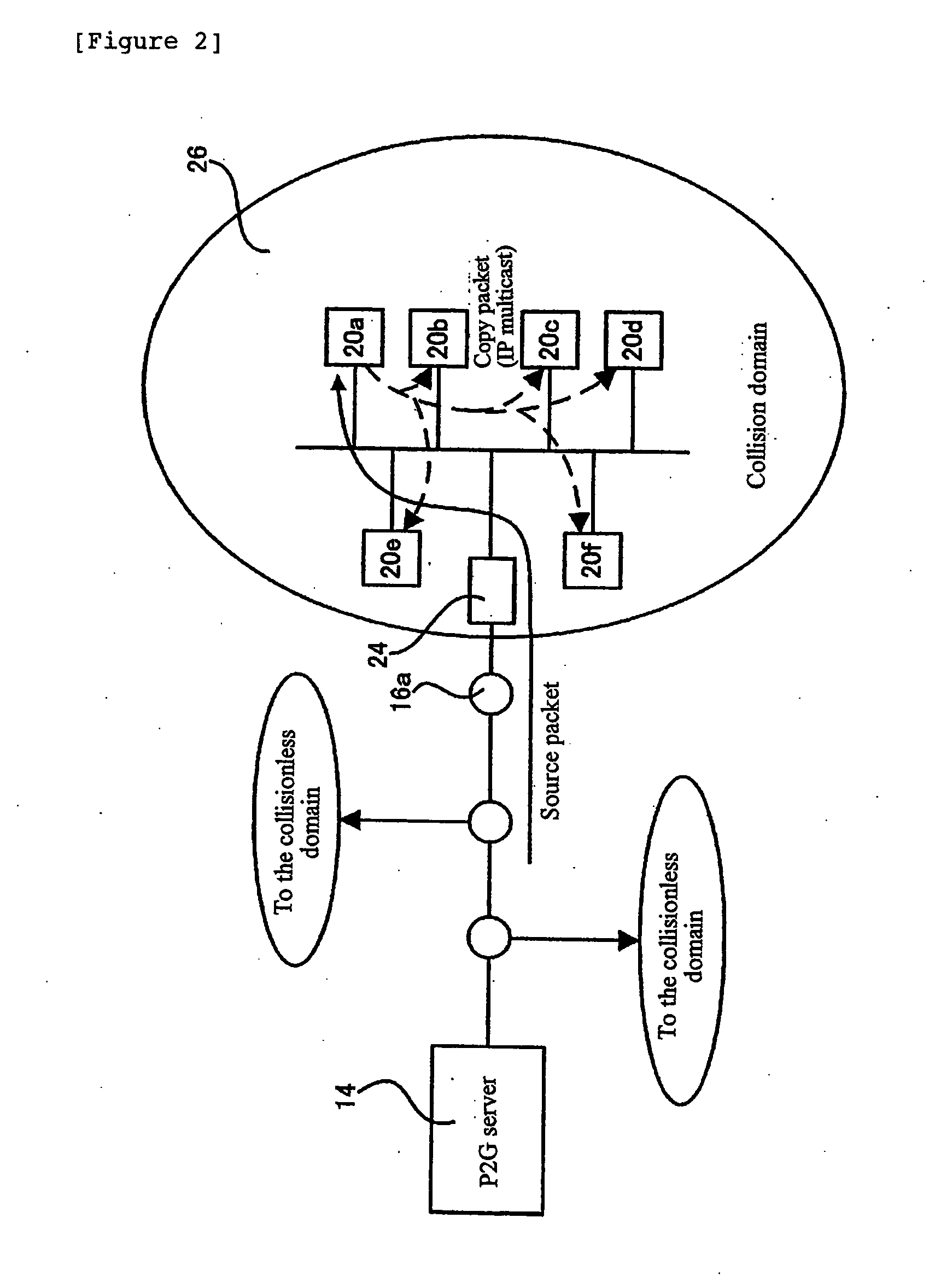
Has the same digital content shared by all clients connected to local networks just by sending the smallest packet required to reconstitute the digital content from a server. A digital content delivery system of the present invention includes clients for constituting second networks and connected to a first network and receiving and providing the digital content. A server includes a client list for storing address identification values of the clients participating in the second network constituted as a collision domain and a device for randomly selecting client identification values registered with the client list, and sends to a selected client a packet as a minimum unit for constituting the digital content in response to the selection.
Owner:IBM CORP
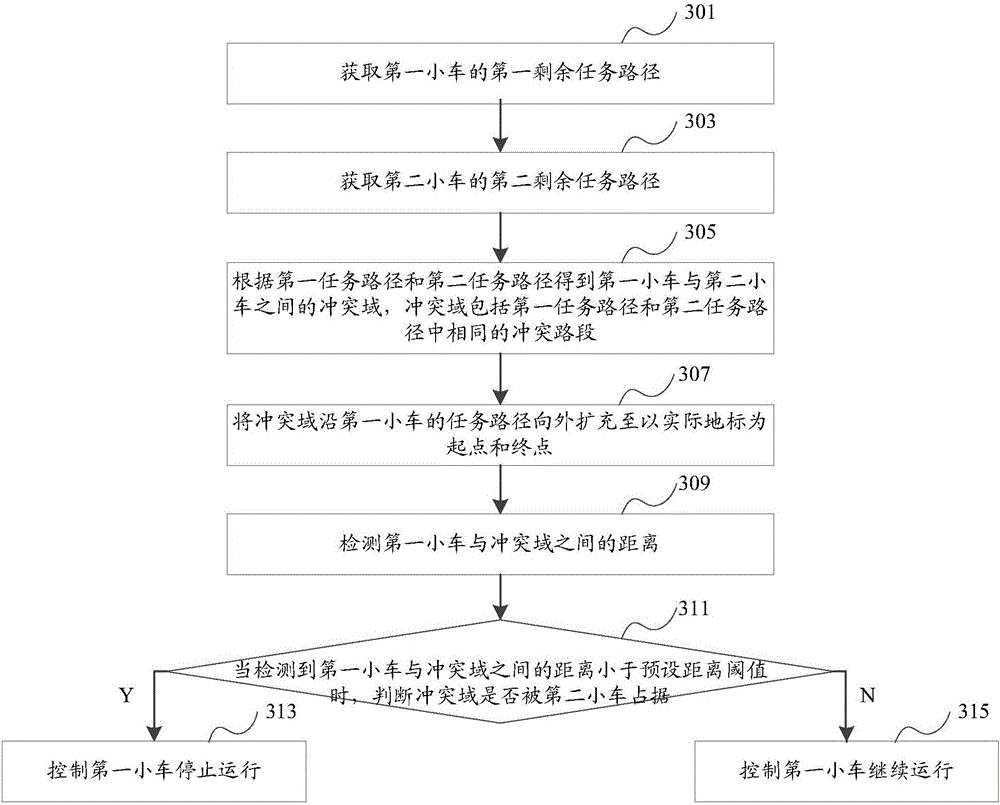
AGV (automated guided vehicle) traffic control method and apparatus
ActiveCN106547271AReduce waiting timeImprove operational efficiencyPosition/course control in two dimensionsAutomated guided vehicleCollision domain
Owner:深圳市大族机器人有限公司
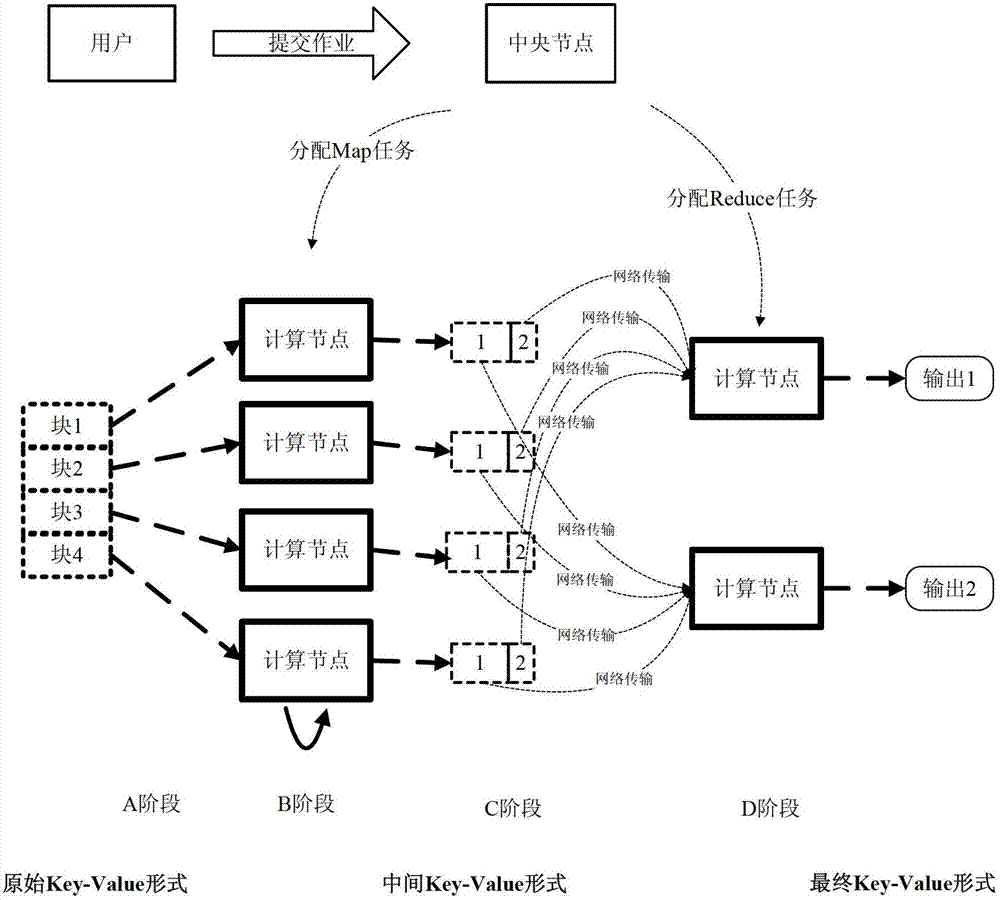
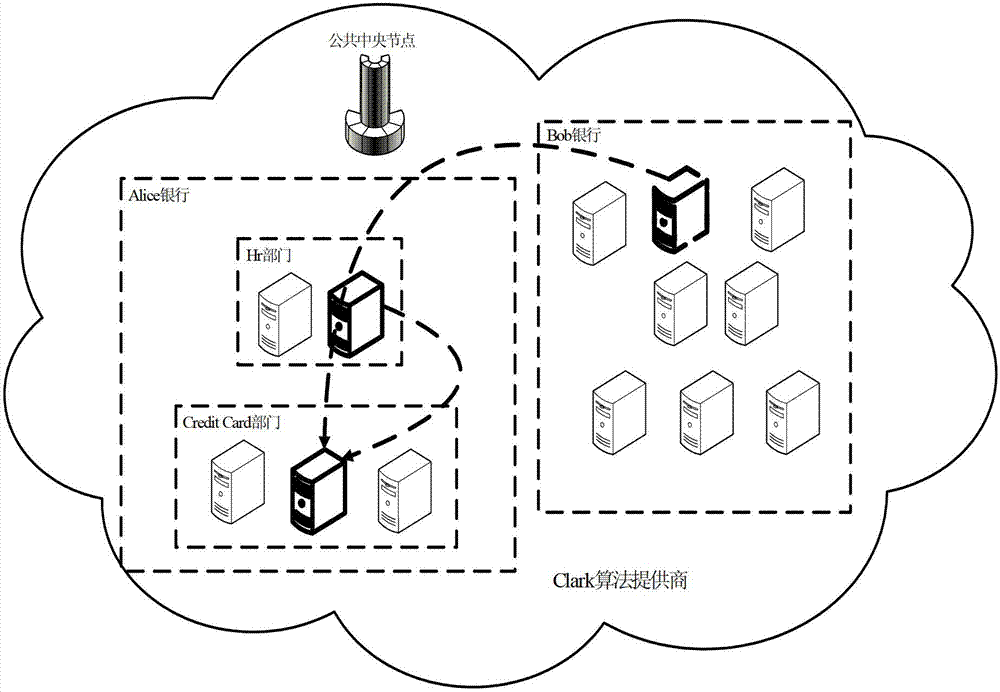
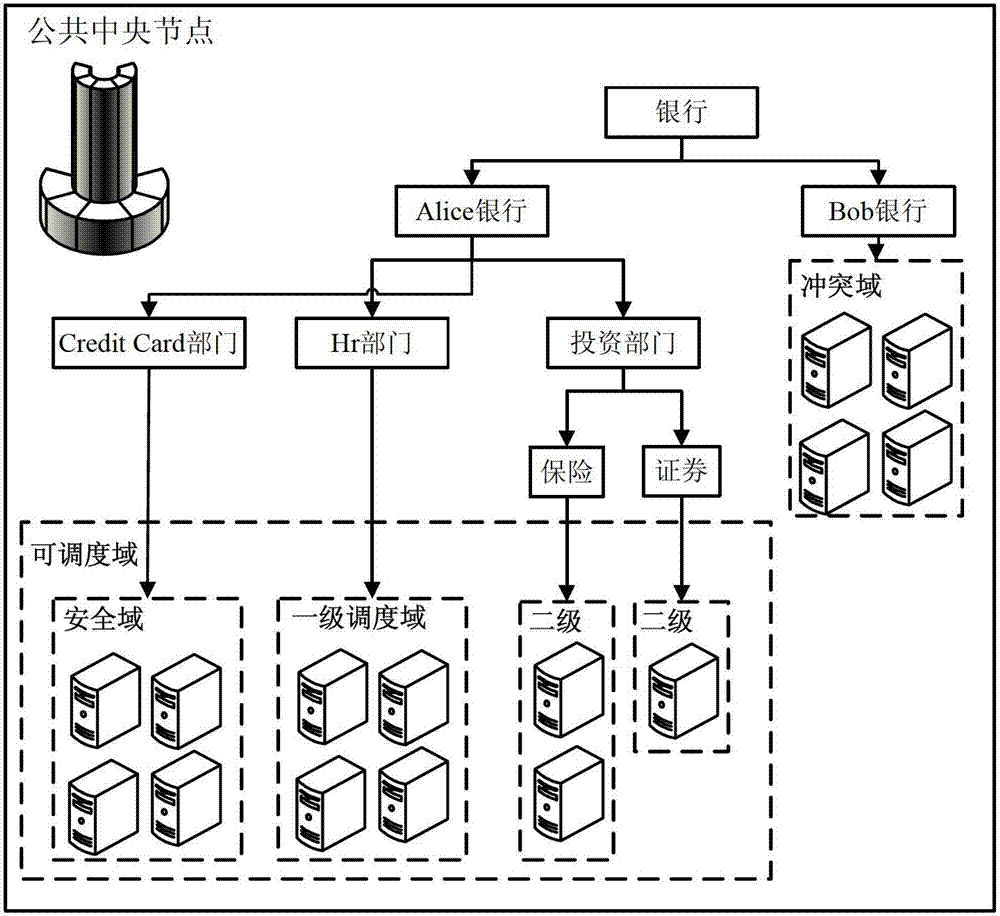
Task scheduling method and system based on MapReduce mechanism
InactiveCN102769615AIntegrity guaranteedReduce performance overheadTransmissionSecurity domainCollision domain
The invention provides a task scheduling method and a task scheduling system based on a MapReduce mechanism. The method comprises the following steps of: carrying out regional division on computing nodes in a MapReduce cloud computing environment, wherein a security domain, a scheduling domain and a collision domain are included; scheduling Map subtasks in a MapReduce task onto computing nodes of the security domain, and scheduling a copy of each Map subtask onto a computing node of the scheduling domain; and carrying out Hash verification on execution environments and partial intermediate results of the Map subtasks and the copies of the Map subtasks, wherein Reduce subtasks respectively utilize an execution environment verification value and an intermediate result verification value generated in a Map subtask stage to verify a self execution environment and input data. Due to the utilization of the method and the system, an operation environment of a task submitted by a common user can be effectively isolated from a malicious user, and the completeness of a task computing result can be ensured in a high-efficient way.
Owner:PEKING UNIV
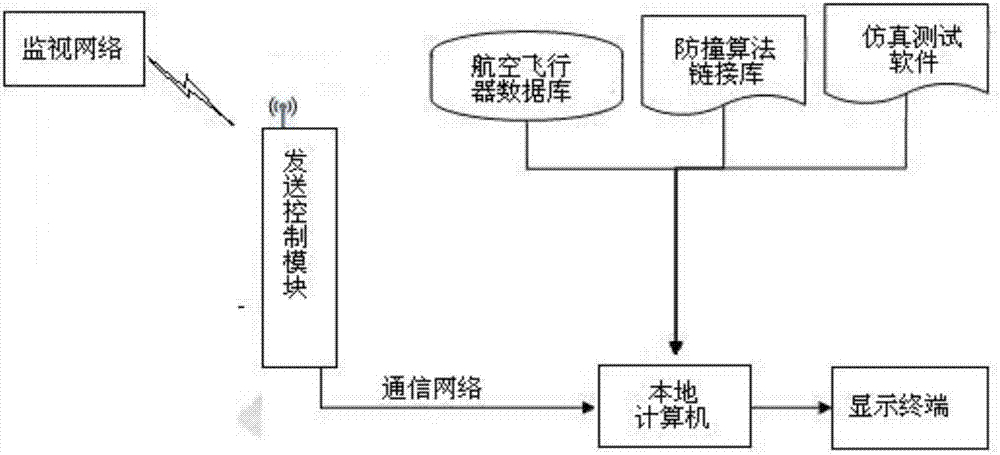
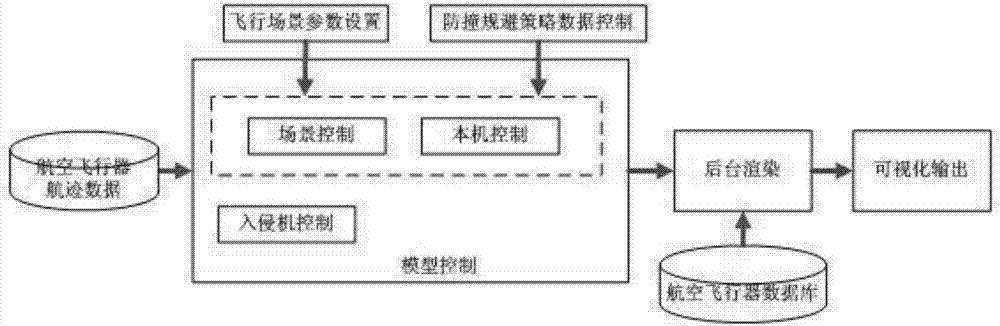
Flight vehicle anti-collision algorithm verification testing method and flight vehicle anti-collision algorithm verification testing system
ActiveCN106997693AReduce riskLow costDesign optimisation/simulationSpecial data processing applicationsAviationFlight vehicle
The invention relates to the aviation flight field, and discloses a flight vehicle anti-collision algorithm verification testing method. The flight vehicle anti-collision algorithm verification testing method comprises steps that step1, track data is acquired; step2, simulation scene parameters are set; step3, by adopting a cylindrical security domain establishing method, an evasion domain and a collision domain are established automatically; step 4, a track collision point is calculated, and when the anti-collision evasion conditions of the evasion domain and the collision domain are satisfied, an anti-collision algorithm is started; step5, the anti-collision evasion performance of the anti-collision algorithm is tested; step 6, anti-collision evasion decision data is acquired, and self-adapting of anti-collision evasion decision data is carried out; step7, a display way is selected for the display and the output of the anti-collision evasion decision data; step 8, the evasion track of the anti-collision evasion decision data is evaluated and calculated; step 9, the data of the above mentioned steps 1-8 is stored, and a flight process is displayed in a real-time manner. The anti-collision evasion testing process having advantages of low costs, low risks, and high efficiency is realized. The invention also discloses a flight vehicle anti-collision algorithm verification testing system.
Owner:四川九洲空管科技有限责任公司
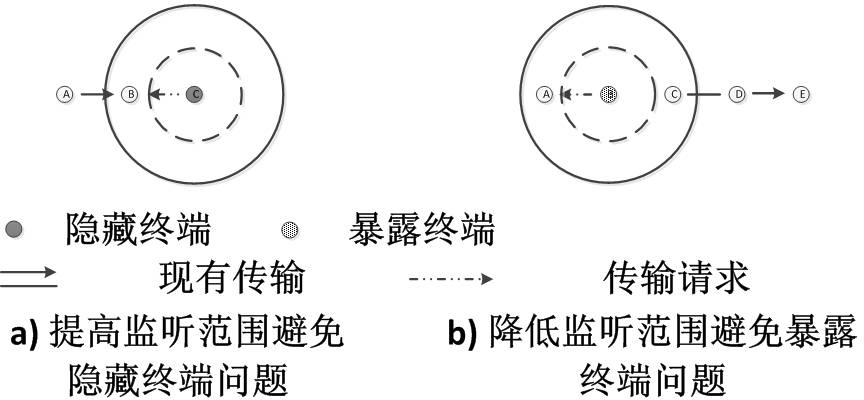
Method for optimizing hidden terminal based on physical layer interference information
ActiveCN102571675ADoes not affect bandwidthWill not interfere with each otherMulti-frequency code systemsData informationControl signal
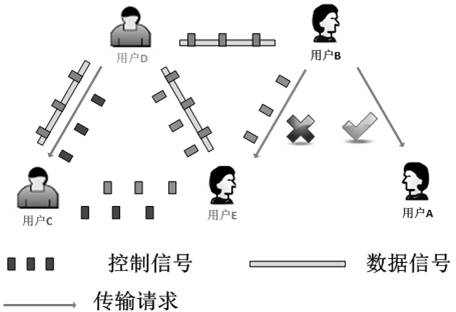
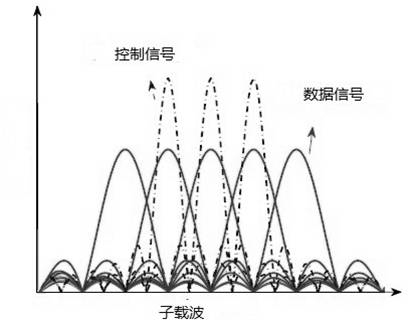
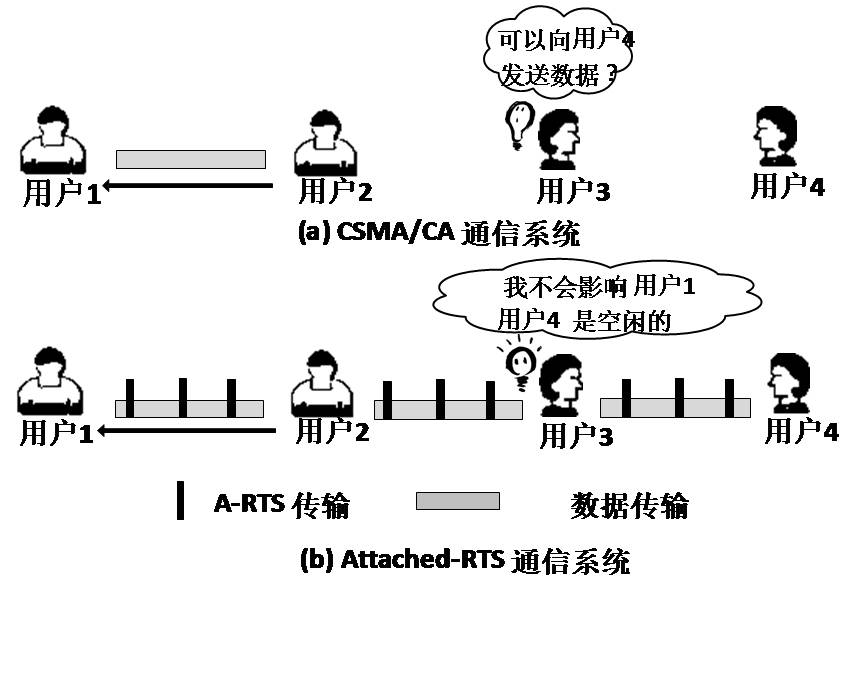
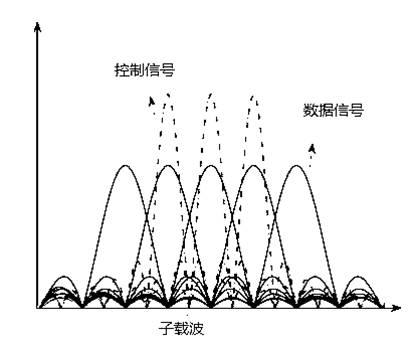
The invention relates to a communication method for solving problems due to a hidden terminal in a wireless network based on a wireless interference cancellation technique and a node full-duplex mode. Under a wireless local area network physical layer, wireless network nodes are coded into special interference signals by an OFDM (Orthogonal Frequency Division Multiplexing) technology, and overlapped into data signals in the air by means of ''attachment''. The control information and the data information can be transmitted in parallel, thus, the resource consumption on control information can be saved. The nodes for receiving the data information can remove the interference signals by an interference canceling technology in order to obtain the original data. The node for receiving the control information can demodulate the control signal from the mixed signal by an energy detecting technology, so as to obtain the physical address of the node which is transmitting in a collision domain, as well as establishing a relative node list. By inquiring the transmitting state and the receiving state of adjacent nodes, the node can determine whether it is the hidden terminal, so as to avoid transmission of conflict data and increase channel utilization rate.
Owner:GUANGZHOU HKUST FOK YING TUNG RES INST
Time slot protocol
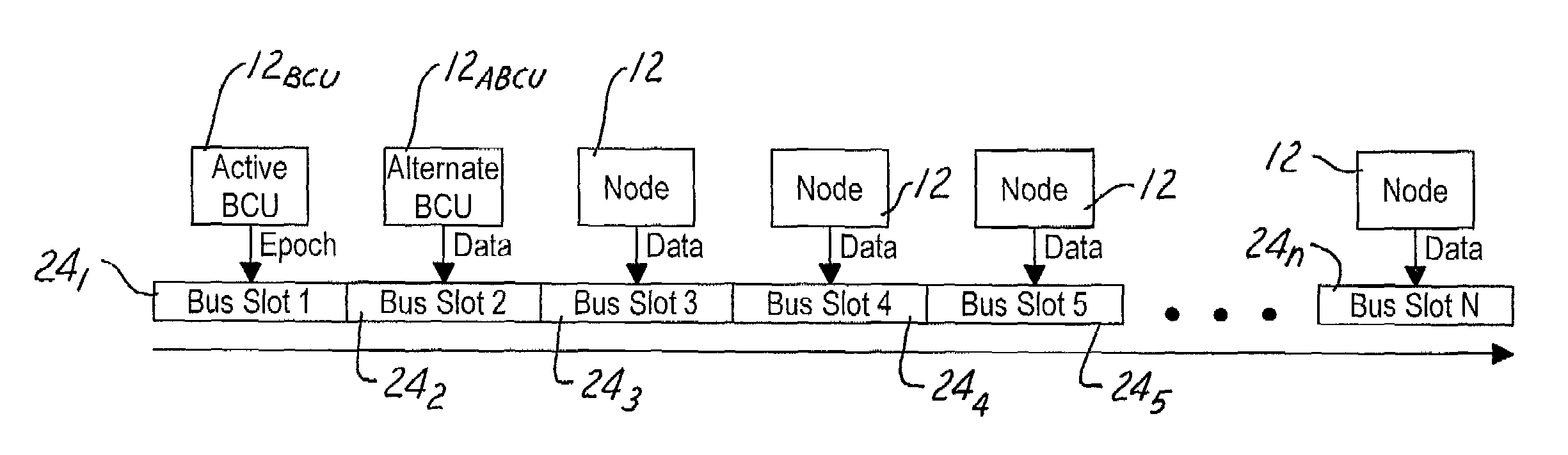
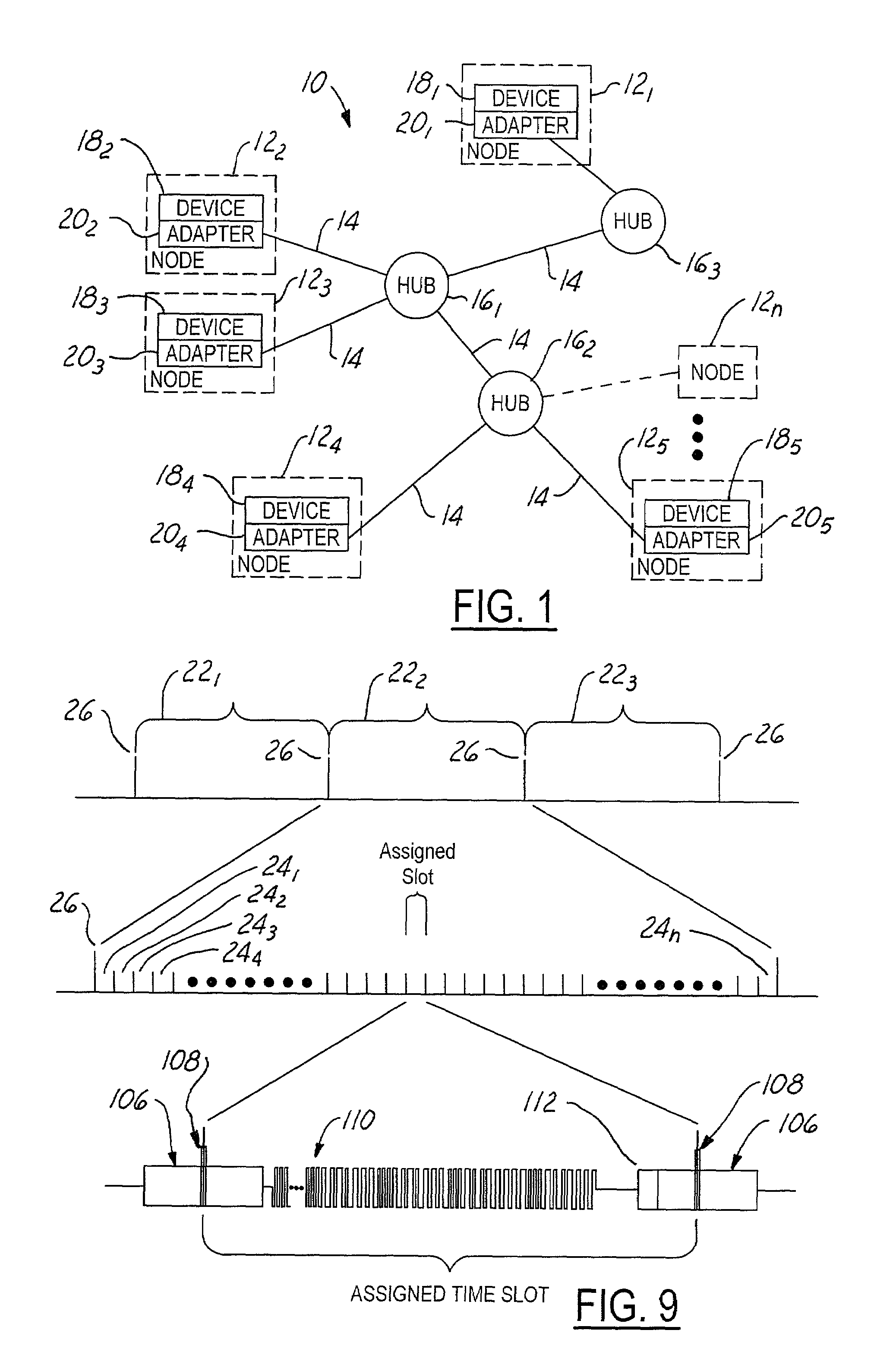
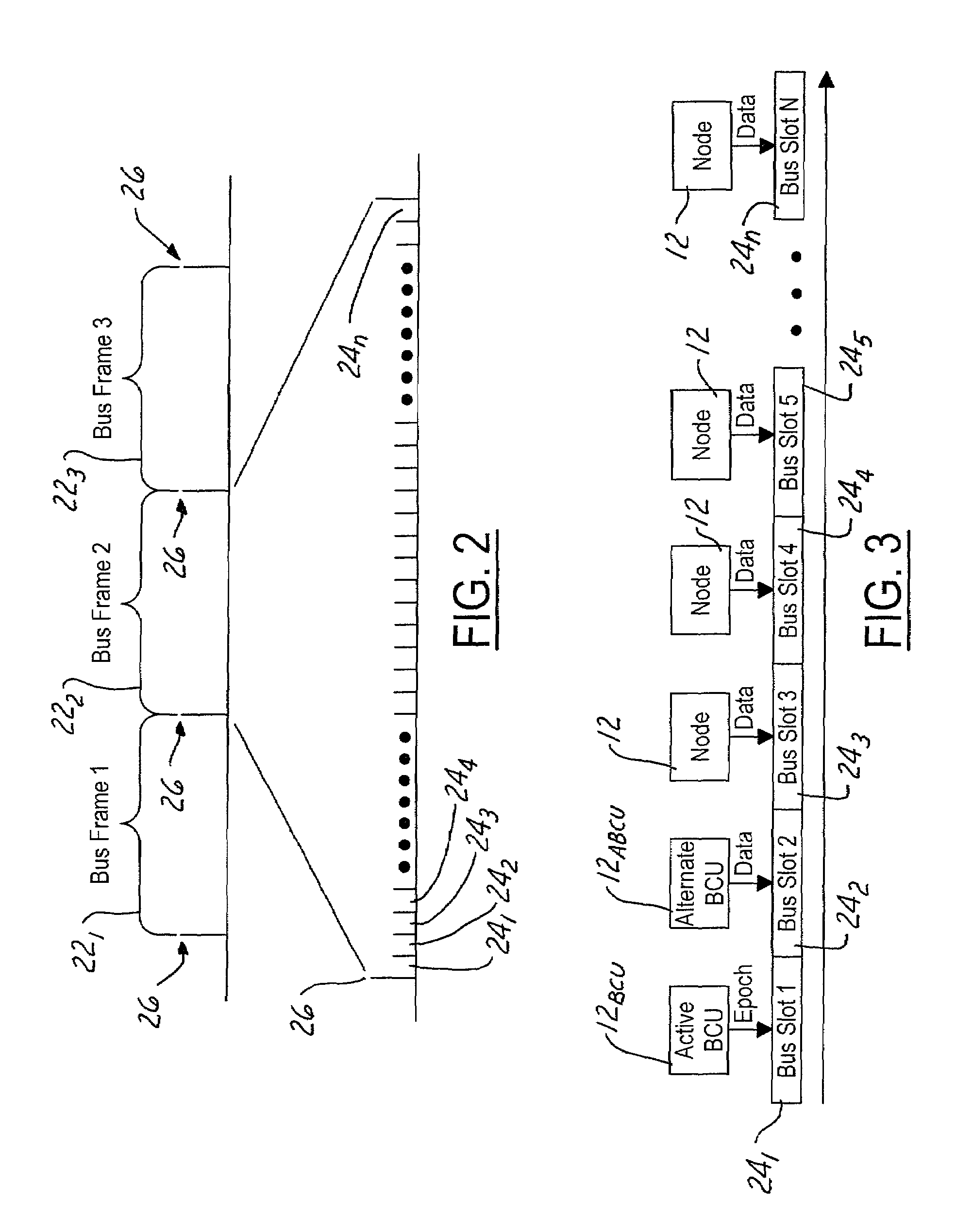
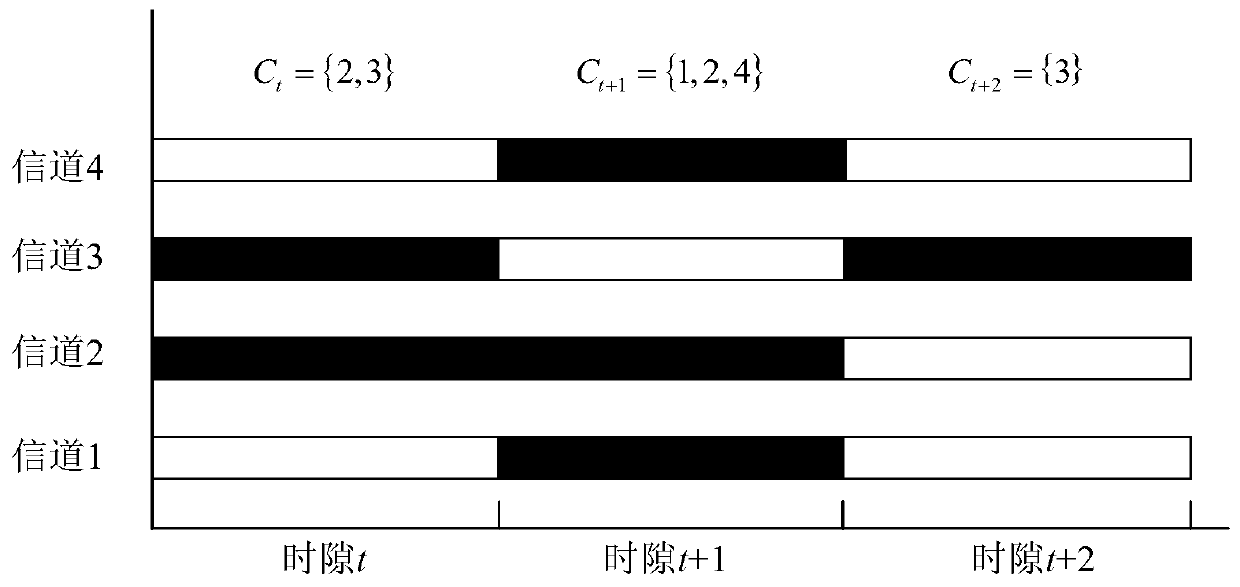
ActiveUS7486693B2Improve bus utilizationMore bandwidthTime-division multiplexMultiple digital computer combinationsCollision domainTime-division multiplexing
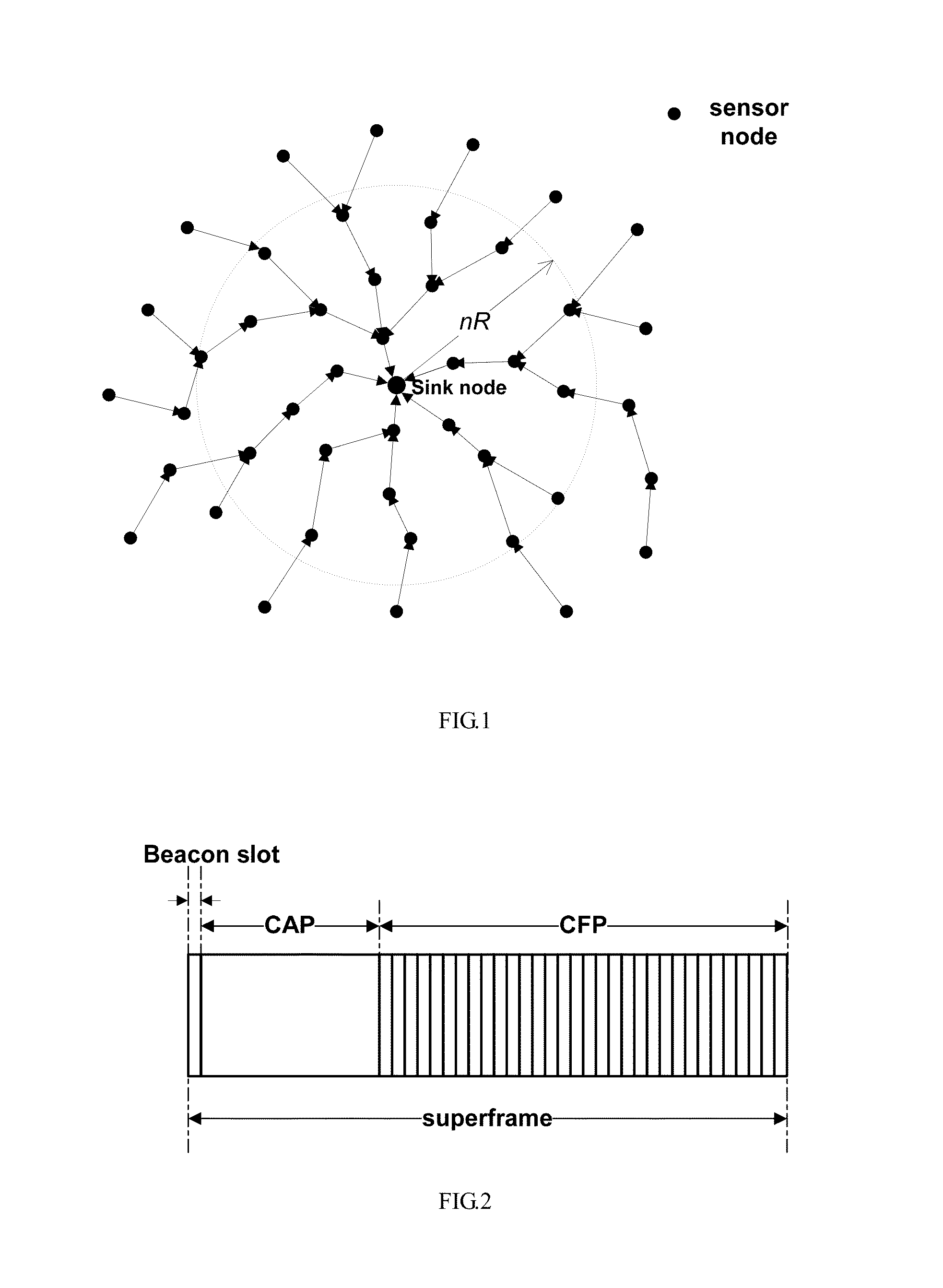
A computing network uses Time Division Multiplexing (TDM) to divide the time on a bus into a plurality of frames, each frame having a plurality of time slots. Each time slot is assigned no more than one of the plurality of devices within a collision domain, the assignments indicating the identity of the device permitted to transmit packets onto the network during the assigned time slot. A bus cadence unit simultaneously sends an epoch packet initiating the frame. The epoch packet contains a time slot assignment table containing the time slot assignments, the device identification, as well as a time slot offset and duration. Each device on the network is configured to measure a frame interval between repeating epoch packets. The measured frame interval is further processed in each receiving node to obtain a calibrated frame interval. The calibrated frame interval is used to accurately synchronize transmissions of data from the various devices onto the network. A time slot protocol governor in each node controls access to the bus to only the assigned time slot or slots using the calibrated frame interval to reduce or eliminate synchronization errors.
Owner:SMITHS AEROSPACE INC
Multi-laser AGV avoidance method
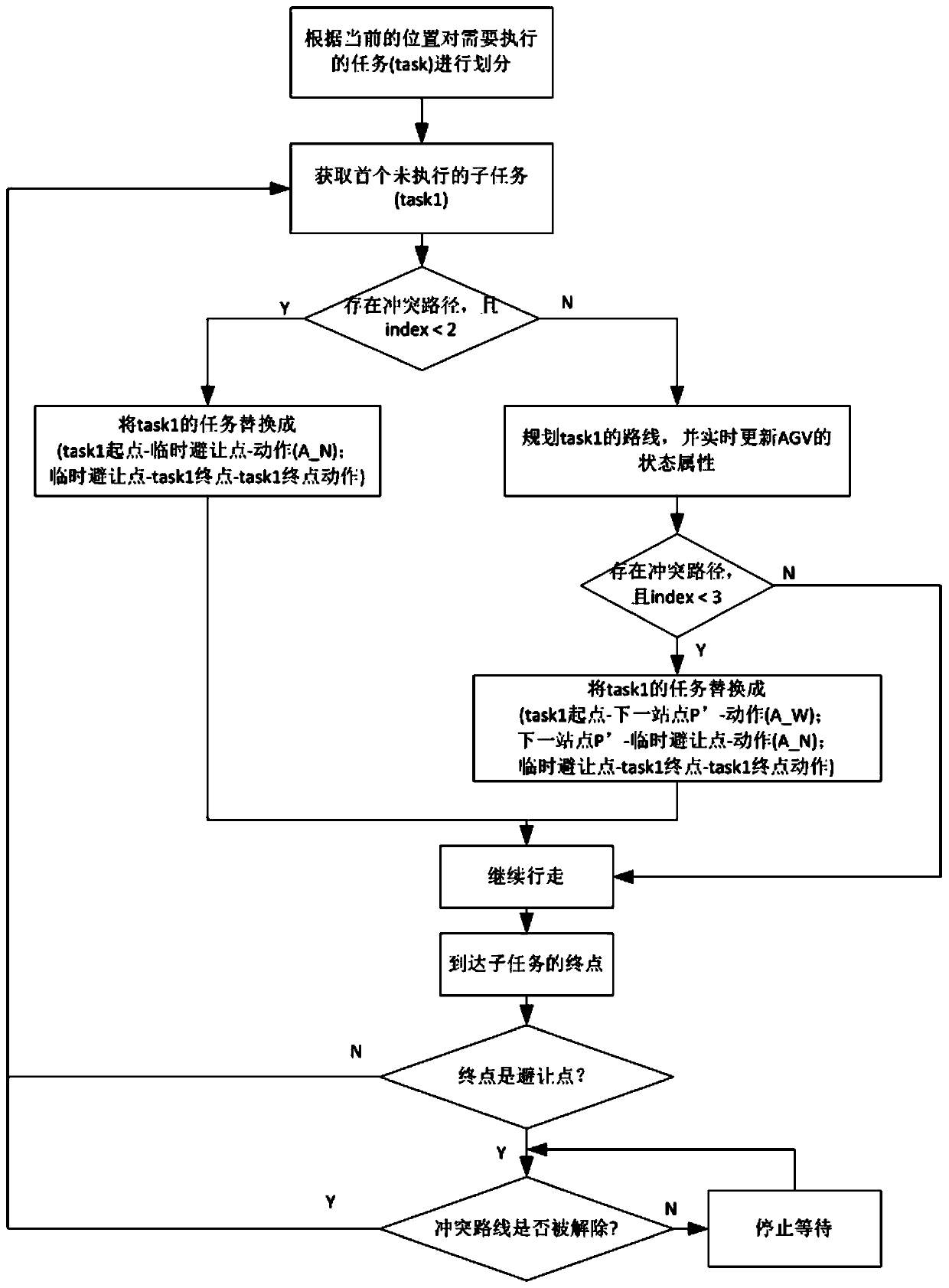
ActiveCN111026128AImprove operational efficiencyGuaranteed reliabilityPosition/course control in two dimensionsVehiclesCollision domainOperations research
The invention discloses a multi-laser AGV avoidance method. The method comprises steps of constructing an environment model, and setting stations and operation routes of laser AGVs; subdividing tasksand adding the subdivided tasks to a task attribute table of the laser AGVs; planning a route of a first unexecuted task in the task attribute table according to the path planning strategy, and updating t attributes of the AGV; in the driving process of the laser AGV, updating the information attribute of the laser AGV in real time,comparing the information attribute with task attributes of otherlaser AGVs, and determining whether the laser AGV needs to be driven to a temporary avoidance point or not; if so, changing a task attribute table of the AGV; if not, continuing to execute the tasks;if the AGV drives to a temporary avoidance point, determining whether a conflict domain is removed or not. The method is advantaged in that the situation that vehicles wait for each other or get stuckin opposite directions is avoided; the subtasks are redivided in real time according to the running state, the waiting time of the laser AGV is shortened, and the dynamic avoiding function is achieved.
Owner:WUHU HIT ROBOT TECH RES INST
Network communication quintuple fast matching algorithm based on improved automatic state machine
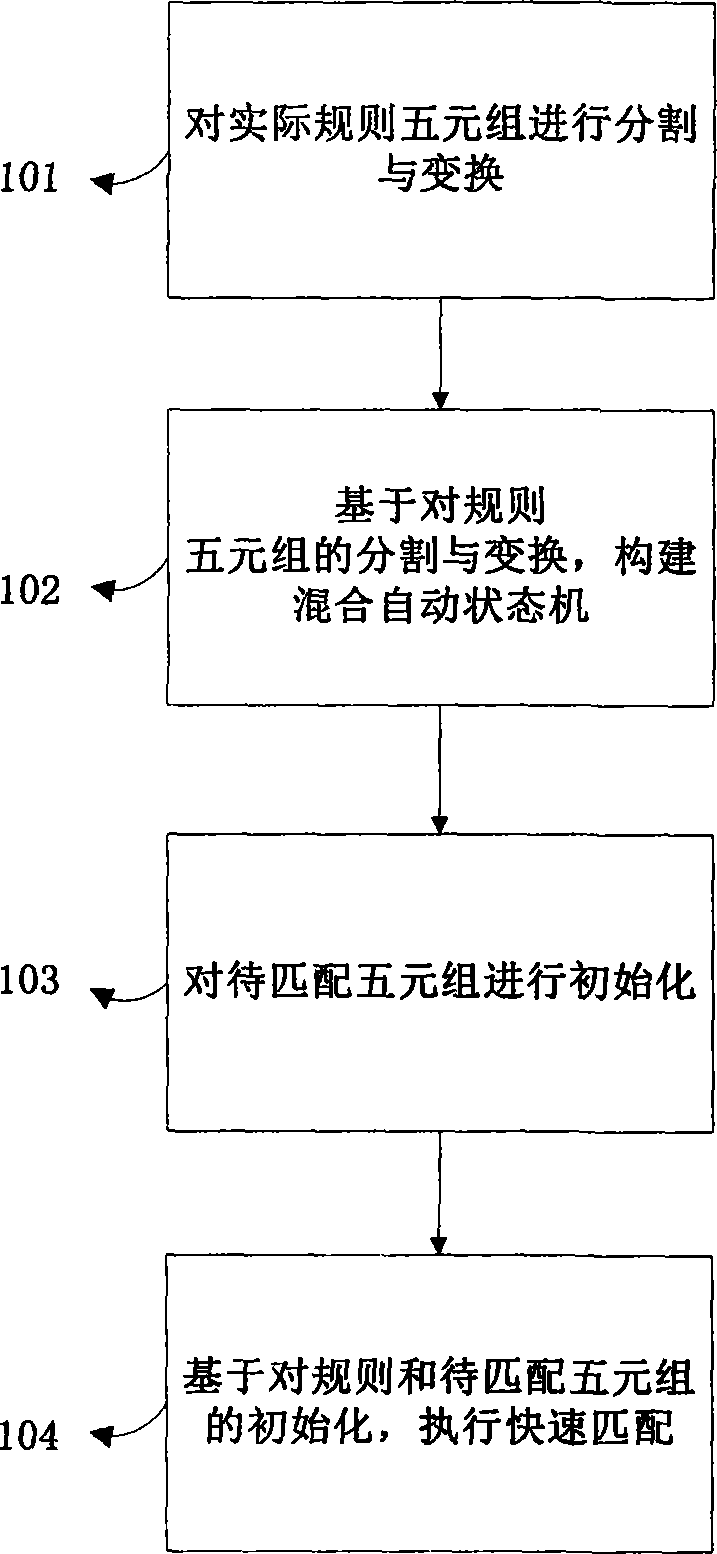
ActiveCN104283736AImplementation supportPrevent missData switching networksMatch algorithmsTheoretical computer science
The invention discloses a network communication quintuple (a source IP, a target IP, a source port, a target port and a protocol number) fast matching algorithm based on an improved automatic state machine. According to the algorithm, a quintuple unit dividing module, a mixture automatic state machine module, an asterisk wildcard mapping module and a matching rule calculating module are adopted, wherein the quintuple unit dividing module is used for establishing a mismatching collision domain, the mixture automatic state machine module is used for achieving uniform matching of point data and section data, the asterisk wildcard mapping module is used for solving the asterisk wildcard matching problem in matching, and the matching rule calculating module is used for reducing redundancy operation caused by asterisk wildcard mapping. The algorithm is characterized in that static parameters in the quintuple are extracted as mush as possible to establish an ordinary automatic state machine, and a larger collision domain is established; for section type parameters, a chain table is added behind the automatic state machine, a mixture automatic state machine structure is formed, and supporting for the section type parameter matching is achieved; the asterisk wildcard matching problem is solved through asterisk wildcard mapping, a replacement rule is precisely matched, and the amount of redundancy calculation is reduced. The algorithm can be widely applied to an intrusion detection system, a network blacklist and whitelist library, a network data analyzing product and other products.
Owner:CHENGDU WANGAN TECH DEV
An electronic mutual inductor data transmission method based on CAN bus
ActiveCN101150475AReduce redundancyIncrease profitMulti-frequency code systemsBus networksTransformerFourier transform on finite groups
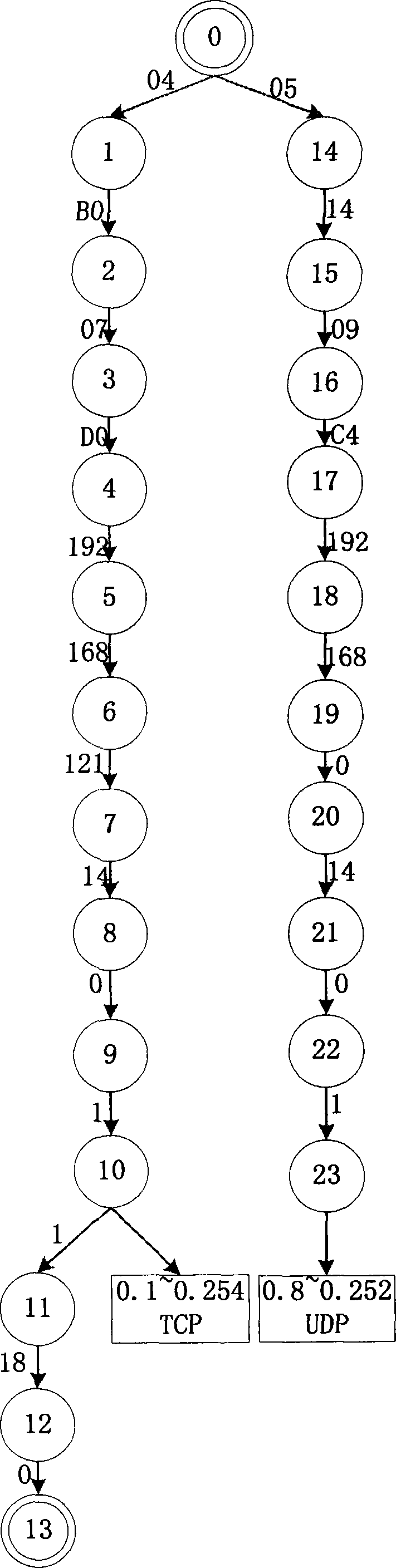
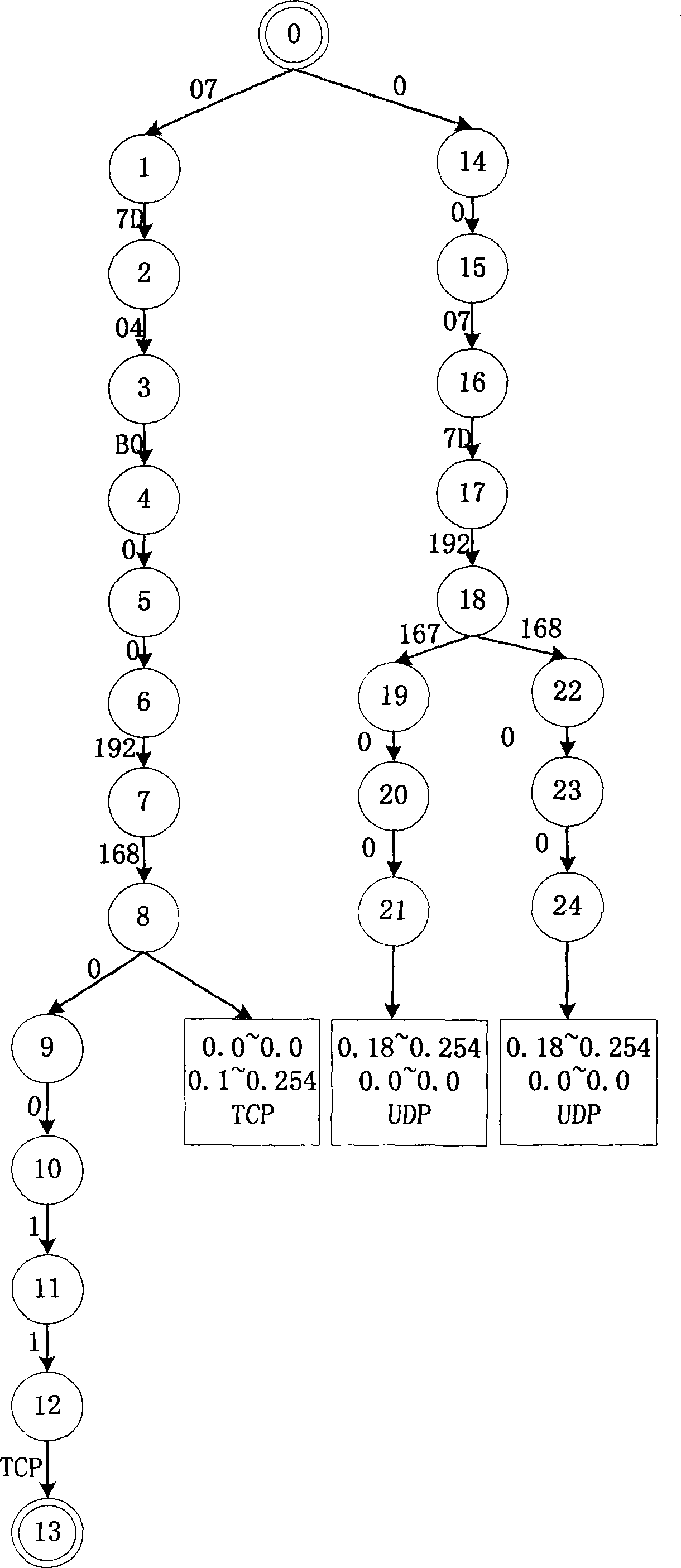
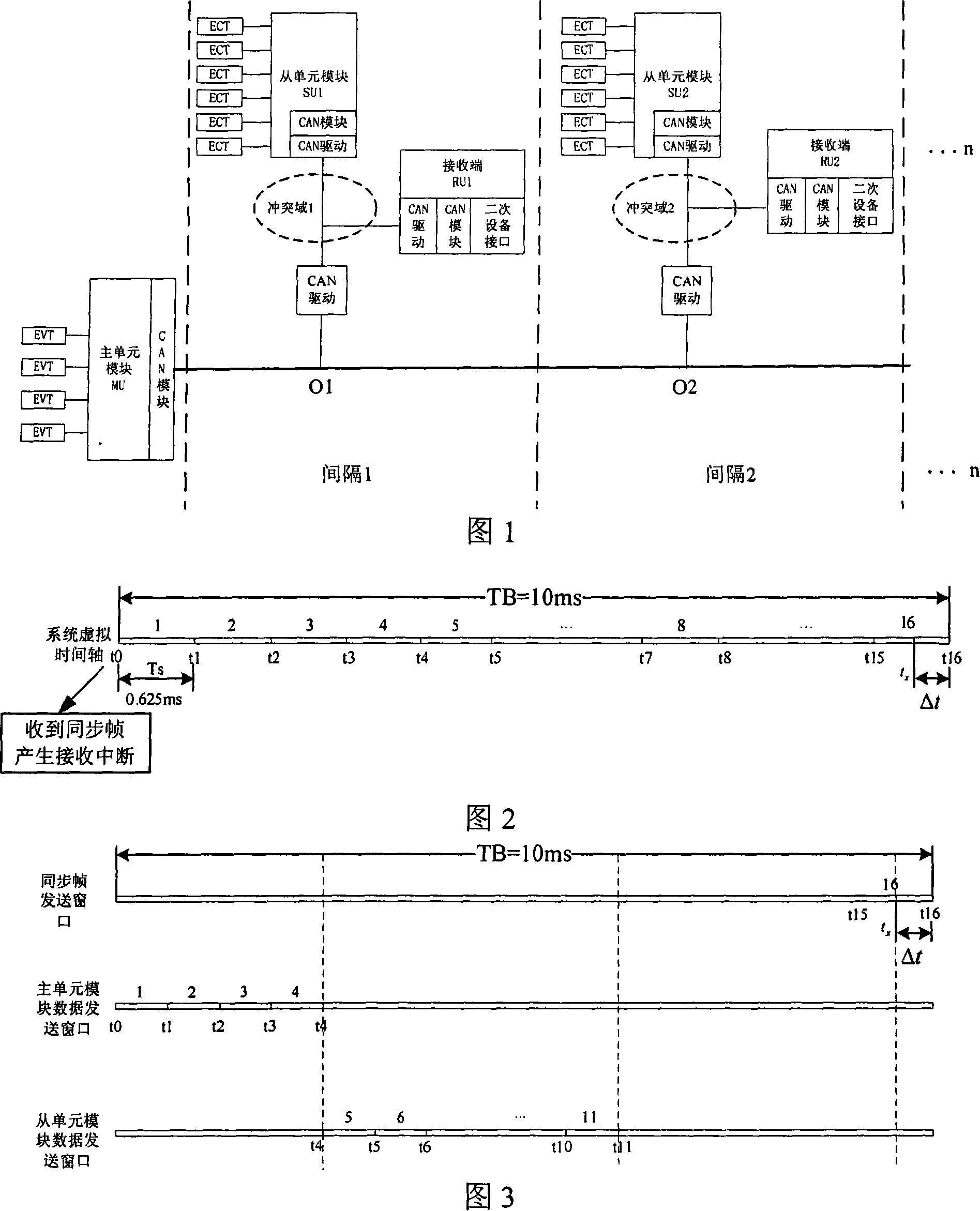
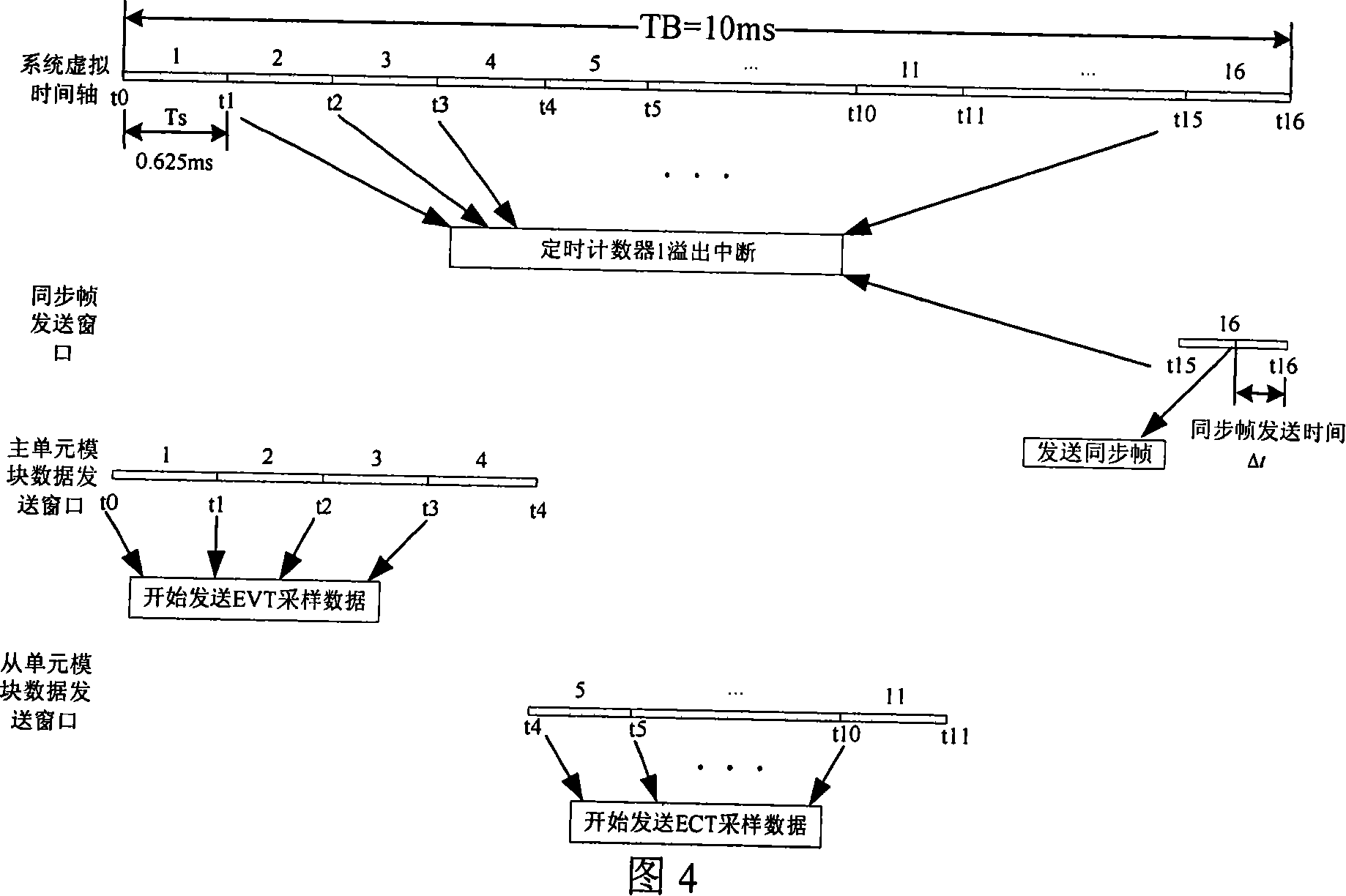
The invention discloses a data transmission method for an electronic transformer based on a CAN bus, which consists of the following four technical proposals: the dividing method for collision domain based on the CAN bus connection, a processing method for data transmission, a soft synchronization method for data sampling and data transmission method with time-triggered mechanism. The invention adopts the fundamental wave and harmonic wave transmission formats of the Fourier transformation, effective value transmission format or real-time wave transmission format and combines the collision domain dividing method in order to achieve the transmission and sharing of system sampling data under conditions of low transmission rate. The use of collision domain dividing method theoretically realizes the unlimited quantity of connection points. The utilization of data transmission method with time-triggered mechanism and the introduction of system virtual time realizes the soft synchronization in data sampling, which eliminates the hardware synchronization transmission cable and reduces the system cost and the wire-connecting complexity.
Owner:XIAN HIGH VOLTAGE APP RES INST CO LTD
Method and apparatus for assigning slot
InactiveUS20150071158A1Reduce calculationIncrease profitNetwork topologiesBroadcast transmission systemsRound complexityCollision domain
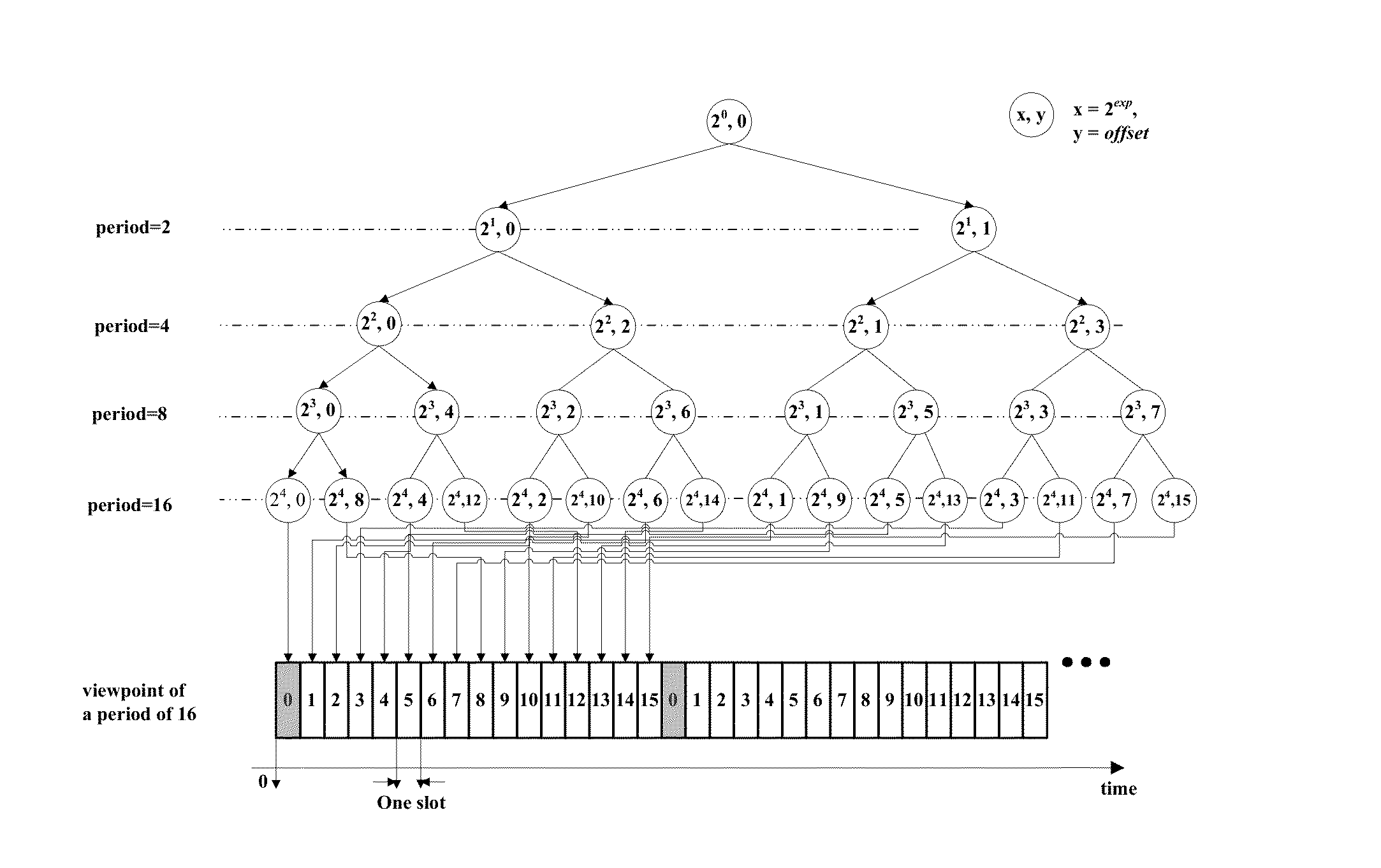
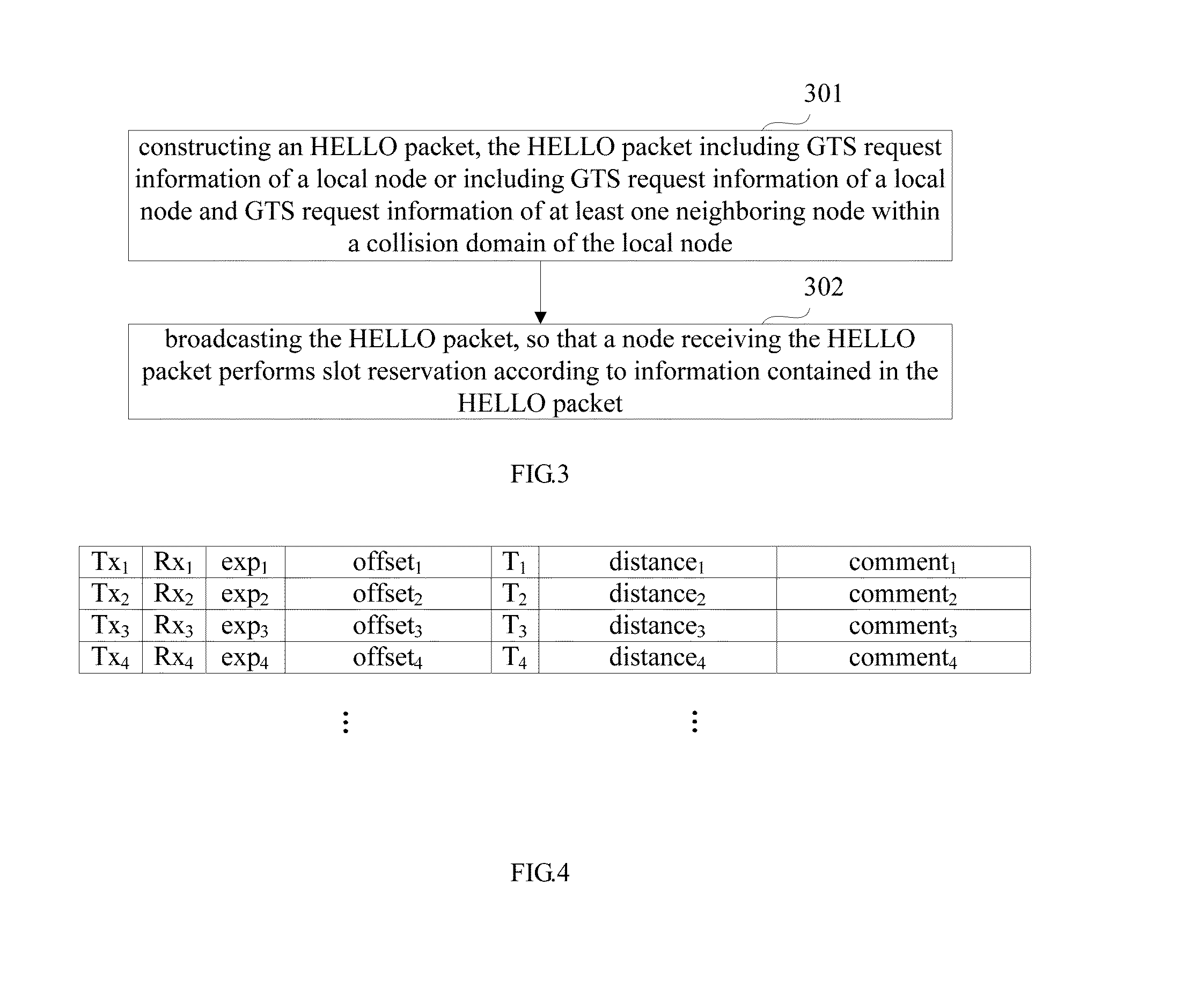
Embodiments of the present invention provide a method and apparatus for assigning slot. The method includes: constructing an HELLO packet, the HELLO packet including GTS request information of a local node or including GTS request information of the local node and GTS request information of at least one neighboring node within a collision domain of the local node; and broadcasting the HELLO packet, so that a node receiving the HELLO packet performs slot reservation according to information contained in the HELLO packet. With the method and apparatus for assigning slot provided by the embodiments of the present invention, no central controller is needed any longer in comparison with a centralized slot assignment method, complexity of calculation is lowered, and utilization of slot is improved.
Owner:FUJITSU LTD
Power control-based Ad Hoc network MAC (Media Access Control) layer channel allocation method
The invention discloses a power control-based wireless MAC (Media Access Control) layer channel allocation method, which belongs to the field of Ad Hoc networks. In a multi-channel Ad Hoc network, two transceivers are used by a network node, of which one is fixedly arranged in a control channel, and the other one jumps between different data channels. An RTS (Request To Send) frame and a CTS (Clear To Send) frame are transmitted at the control channel by using the maximum power; a DATA frame and an ACK (Acknowledgement) frame are transmitted at the data channels by using the minimum power. The minimum power is calculated according to the minimum receiving power threshold which can be correctly received and decoded by a receiving node. The transmitting powers of all nodes in a same collision domain are divided into different grades, and then a corresponding data channel is selected according to the grade of the minimum power, so that links with larger transmitting power difference are allocated to different channels, the adverse effect of asymmetric links in the same channel can be relieved, and the network throughput and the unit energy consumption throughput are improved. The concrete implementation CAPC (Channel Assignment with Power Control) protocol can be used as an MAC layer protocol of the channel selected by Ad Hoc network node equipment.
Owner:DALIAN UNIV OF TECH
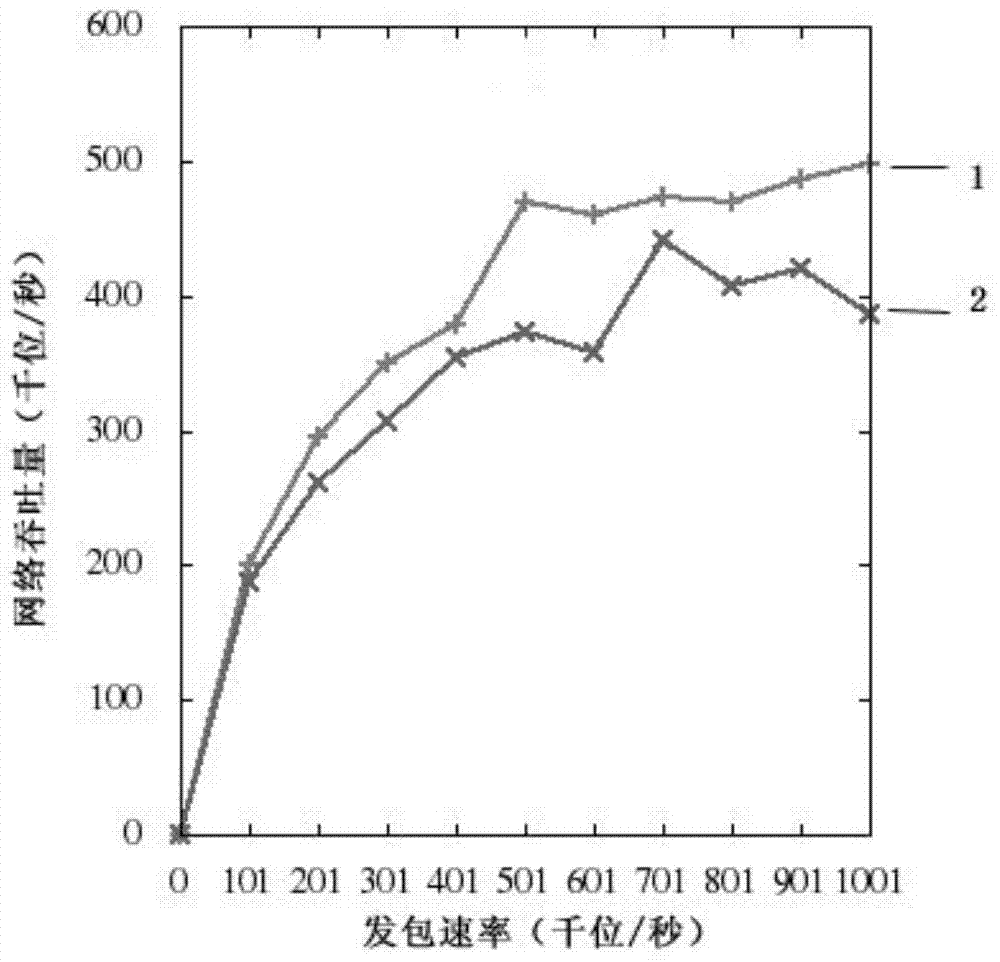
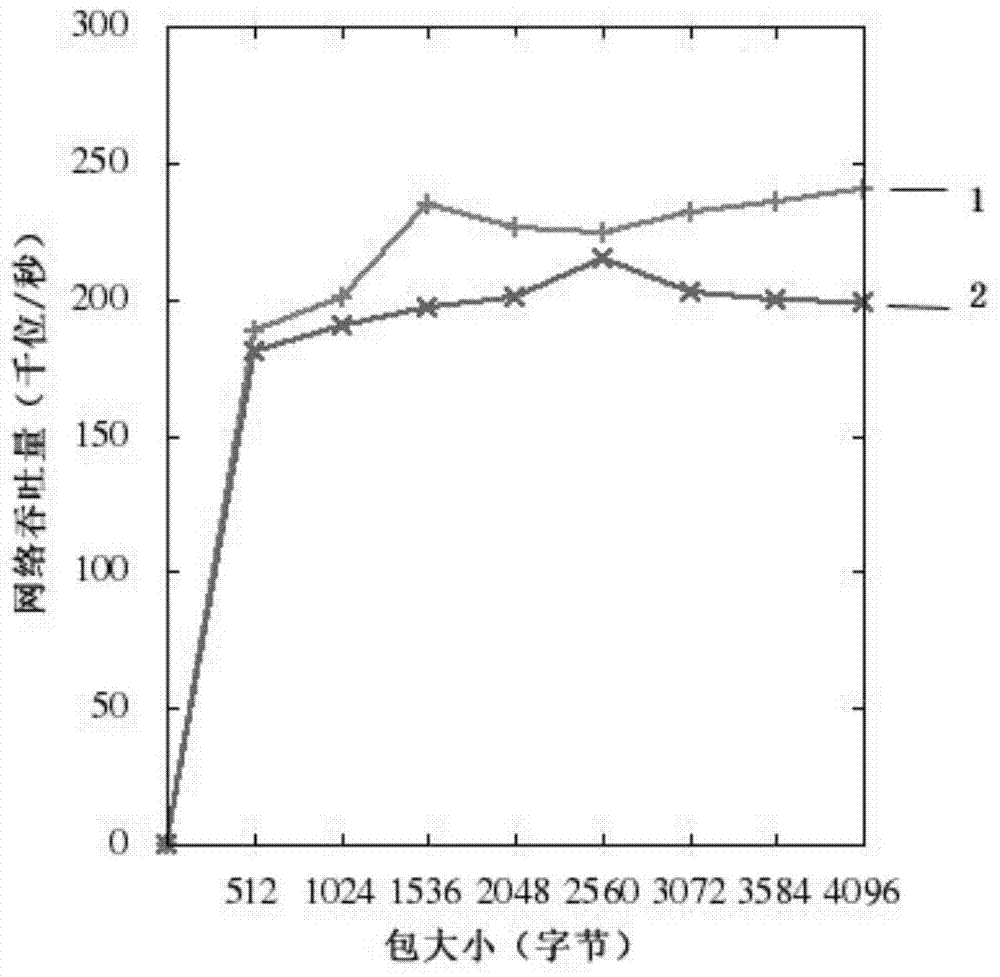
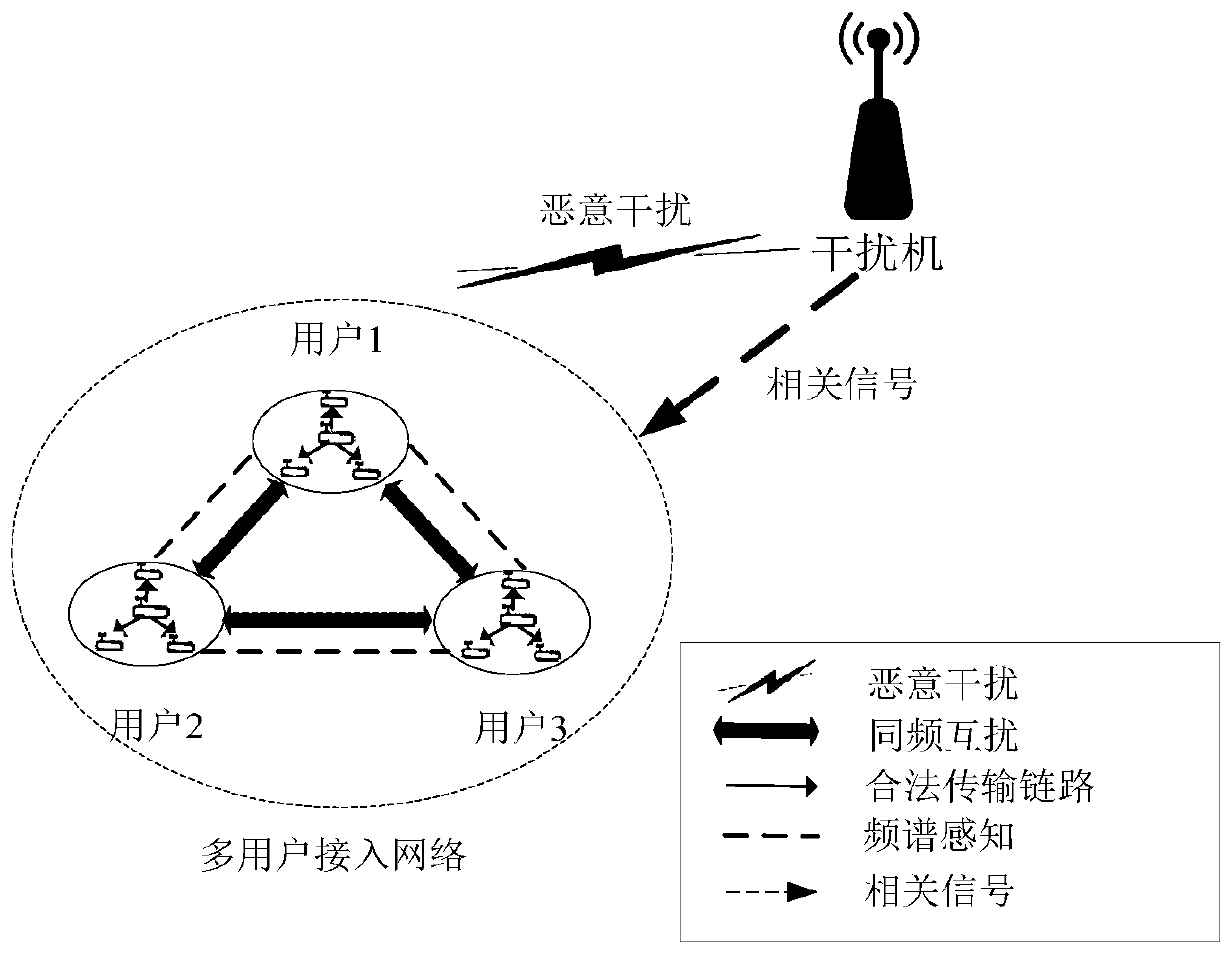
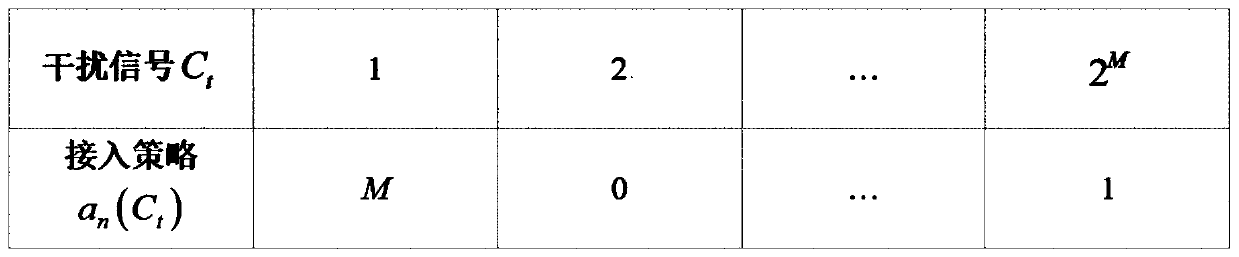
Multi-user anti-interference channel access system and dynamic spectrum collaborative anti-interference method
ActiveCN110891276AEfficient solutionError prevention/detection by using return channelOrthogonal multiplexInterference (communication)Interference resistance
The invention discloses a multi-user anti-interference channel access system and a dynamic spectrum collaborative anti-interference method. According to the system, a distributed wireless network is considered, a plurality of communication users exist in the network, and the outside of the network is attacked by malicious interference; users in the same conflict domain in the network can judge interference signals at the moment through broadband spectrum sensing, and select communication channels through distributed channel decisions, so that malicious interference is avoided, and same-frequency mutual interference is avoided. The method comprises the following steps: firstly, a communication party observes an interference signal and takes the interference signal as a coordination signal;the own user is guided to select frequency and transmit data according to the coordination signal and the corresponding channel access strategy table; after transmission, a judgment is made whethertransmission succeeds or not according to whether ACK feedback is received or not; and finally, the channel access strategy table is updated according to the transmission condition. The model is complete with clear physical significance and high anti-interference capability so that same-frequency mutual interference is avoided, and the channel transmission efficiency of the distributed wireless network is improved.
Owner:ARMY ENG UNIV OF PLA
Methods and circuits for stacking bus architecture
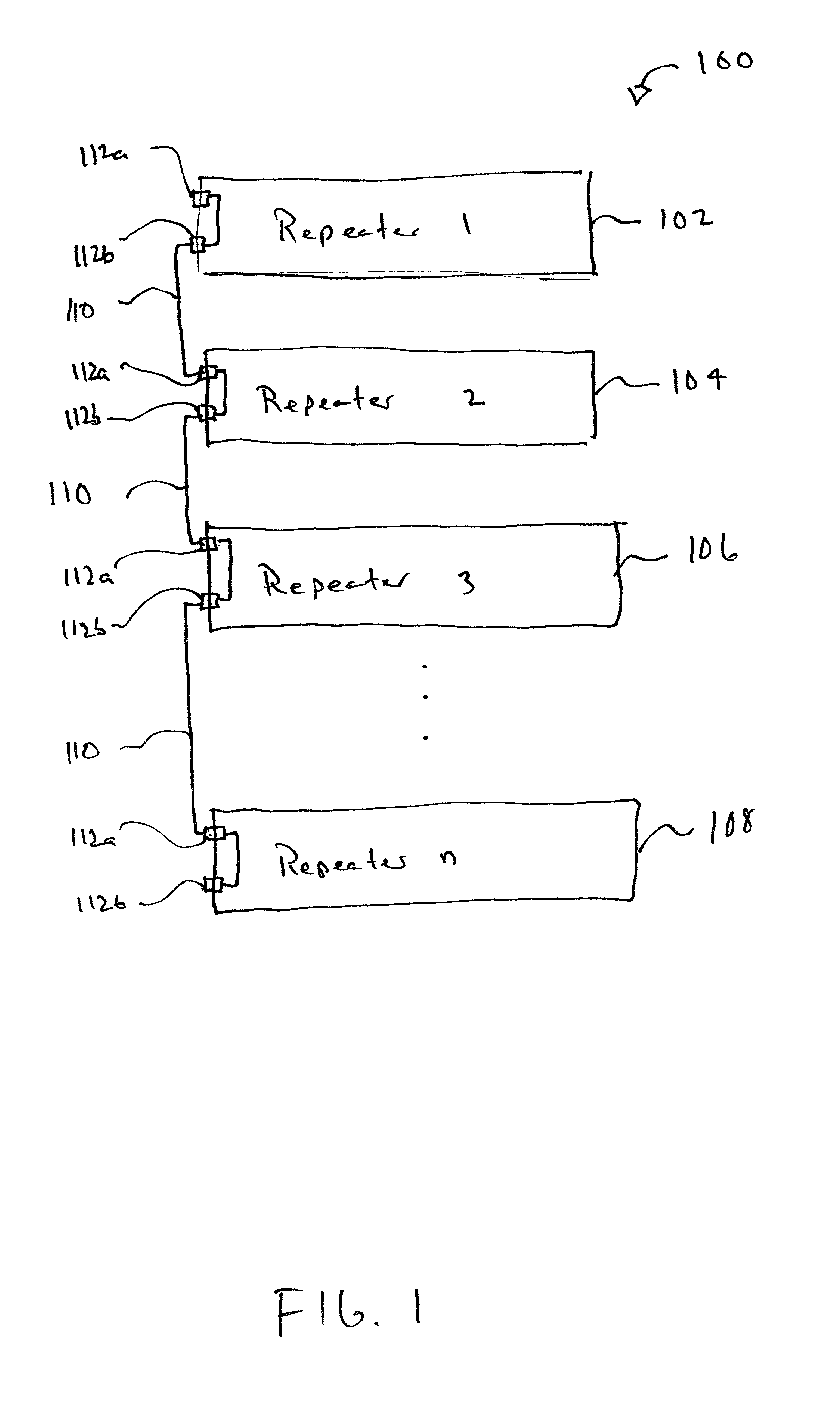
InactiveUS20010032283A1Frequency-division multiplex detailsUnauthorized memory use protectionEngineeringCollision domain
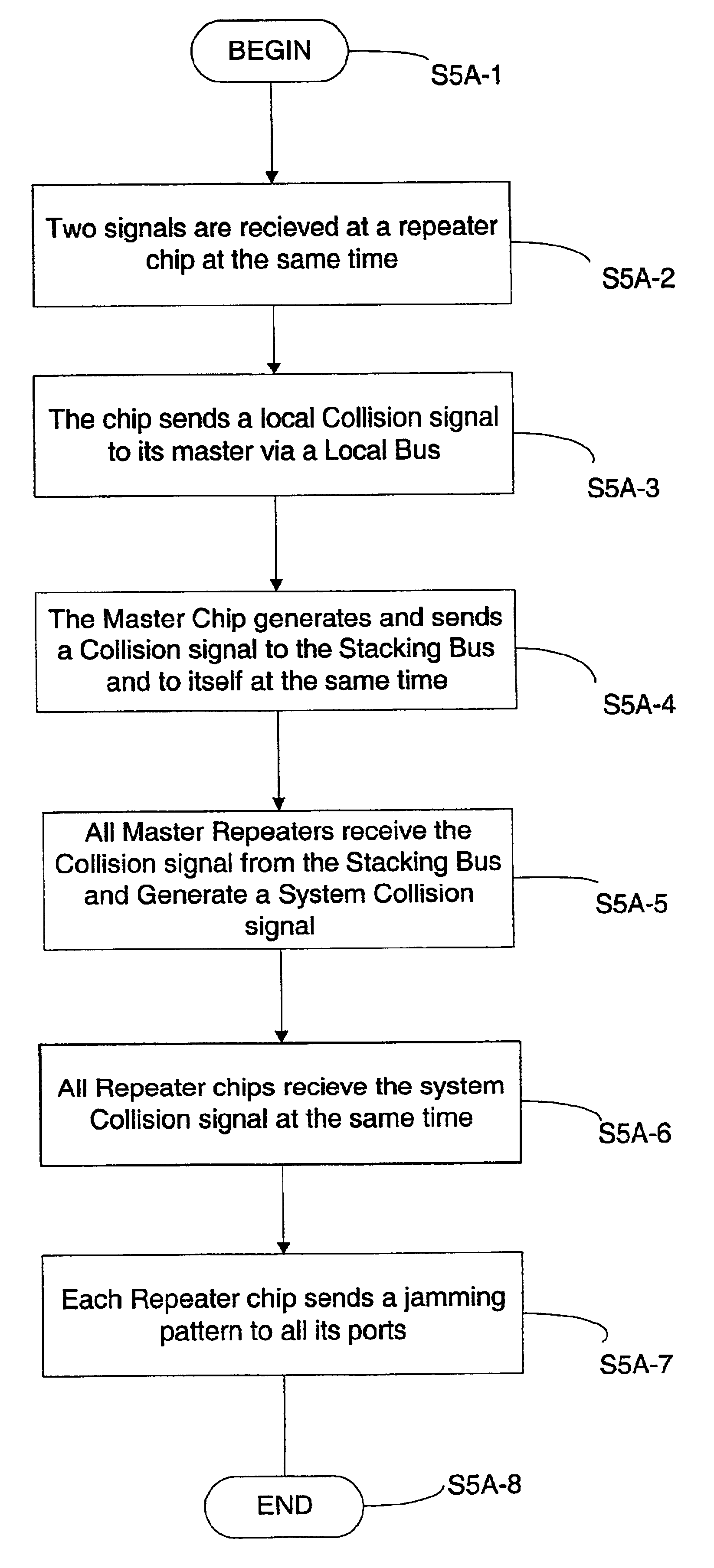
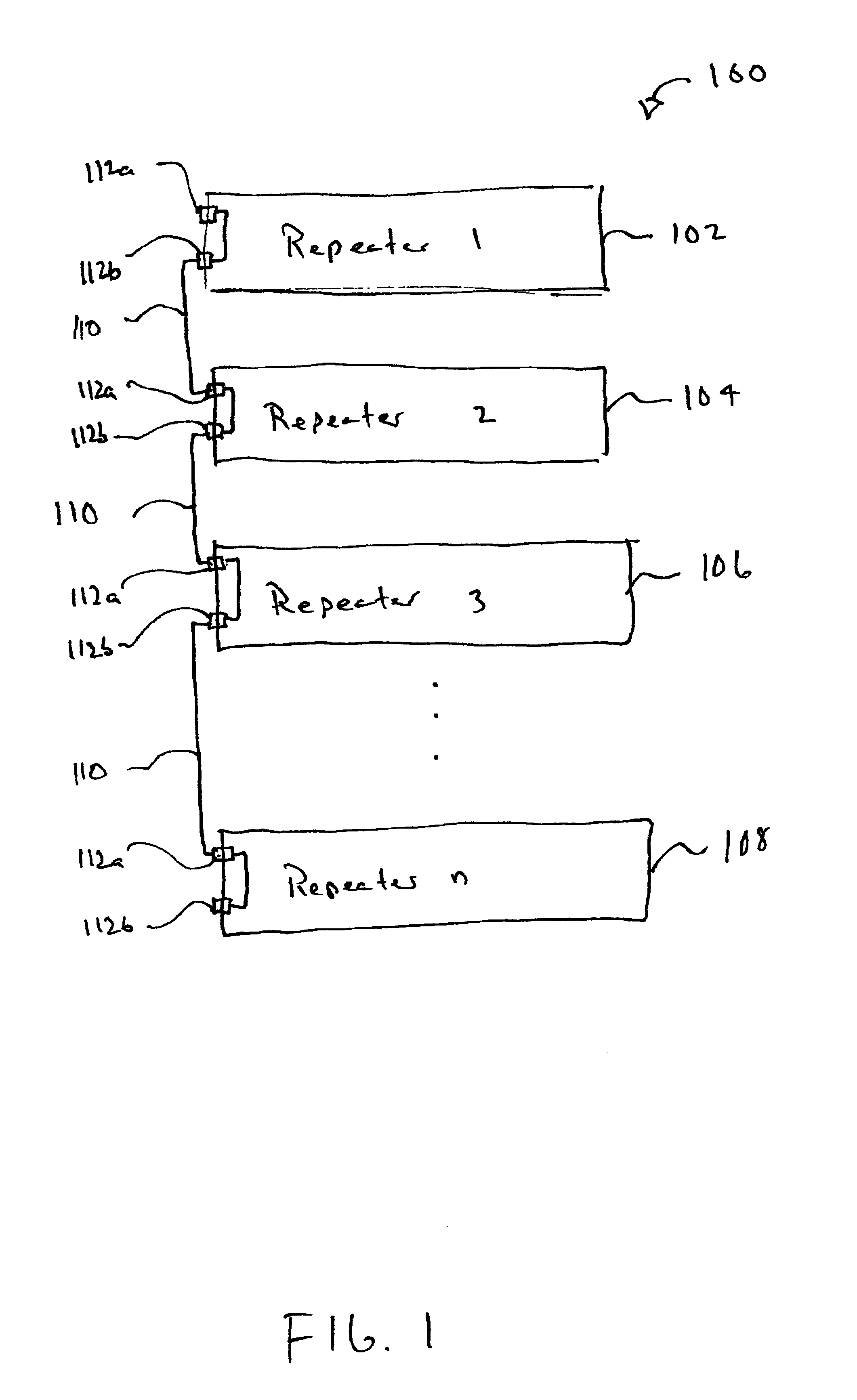
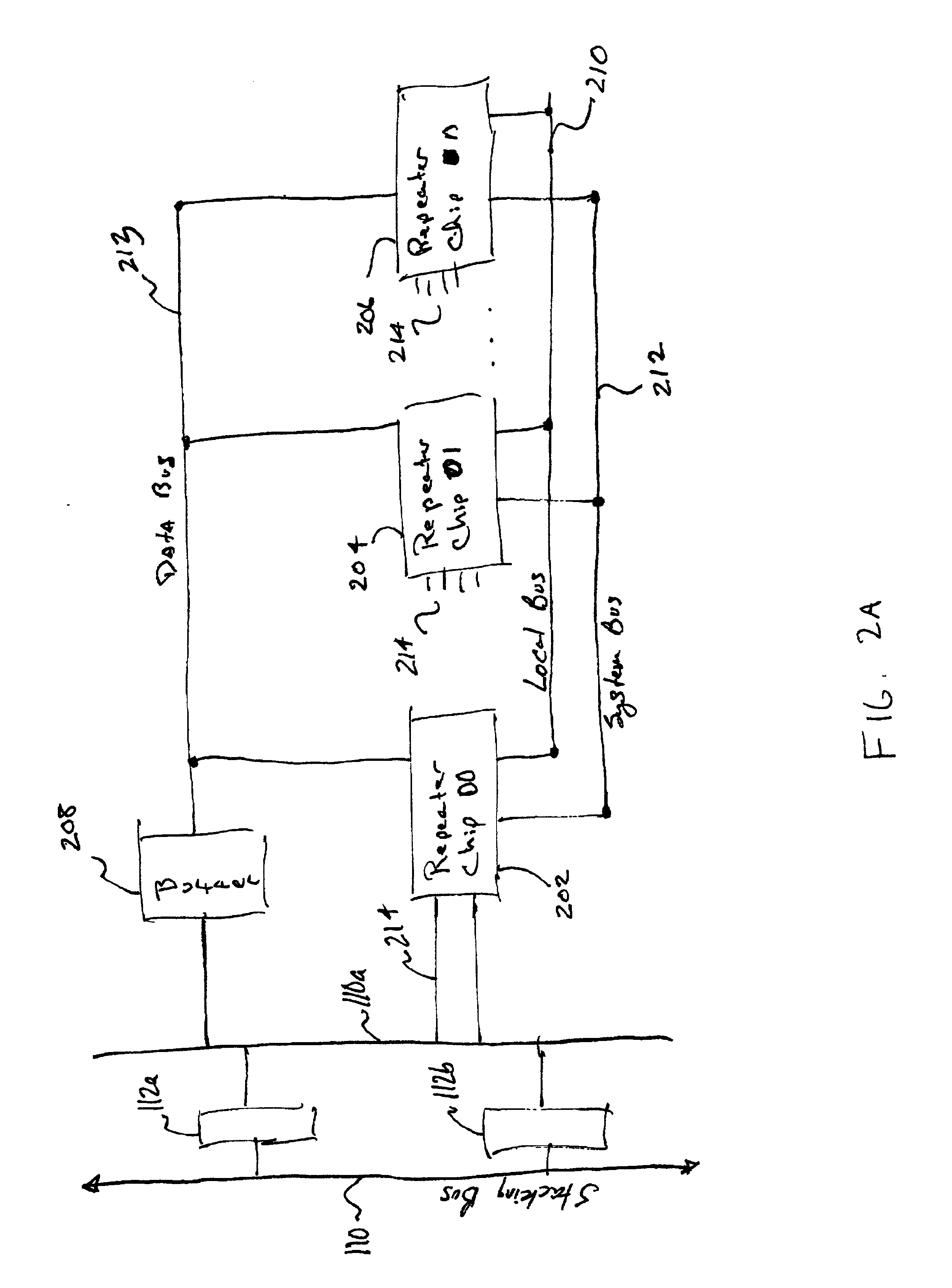
A system for connecting multiple repeaters into a single collision domain comprising a first repeater, a second repeater and a stacking bus. The first repeater has a plurality of network ports. The second repeater also has a plurality of network ports. The stacking bus connects the first repeater and the second repeater and is configured to relay status signals between the first and said second repeaters.
Owner:AVAGO TECH INT SALES PTE LTD
Channel switching mode generating and allocating method for multi-channel wireless radio multi-hop network
ActiveCN101394317AImprove performanceGood conflict domain divisionData switching by path configurationAccess timeDistribution method
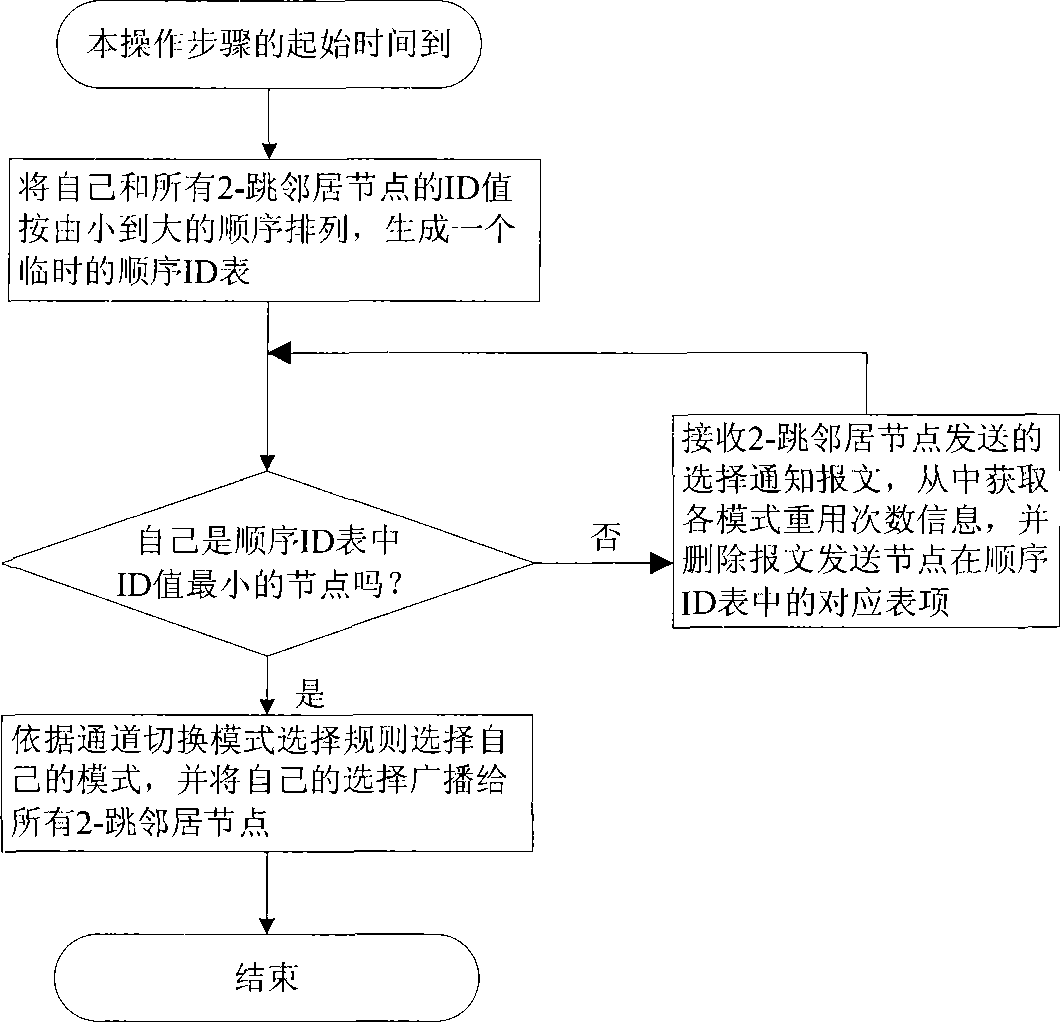
The invention relates to a channel switching mode generation and distribution method for a multi-channel wireless multi-hop network, which comprises the steps of setting up a channel switching mode generation method to stipulate how to generate a channel switching mode; and distributing a channel switching mode for each node in the network by using a channel switching mode distribution method based on the generation method. The channel switching mode distribution method is carried out on the nodes in a distributive concurrent execution manner, and the nodes in the network are equally distributed into all available channels in each time slot together with the potential competitive nodes thereof by following the distributed channel switching mode. In the synchronous channel switching-based media access control method, the method can be used to ensure that in each time slot, the nodes in the network are equally distributed into all available channels together with the 2-hop neighbor nodes thereof, so that the network can obtain better collision domain division effect and higher degree of concurrent transmission, thereby effectively reducing the channel access time of nodes and message conflict.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Methods and circuits for stacking bus architecture
InactiveUS6920520B2Increase collisionFrequency-division multiplex detailsUnauthorized memory use protectionEngineeringCollision domain
Owner:AVAGO TECH INT SALES PTE LTD
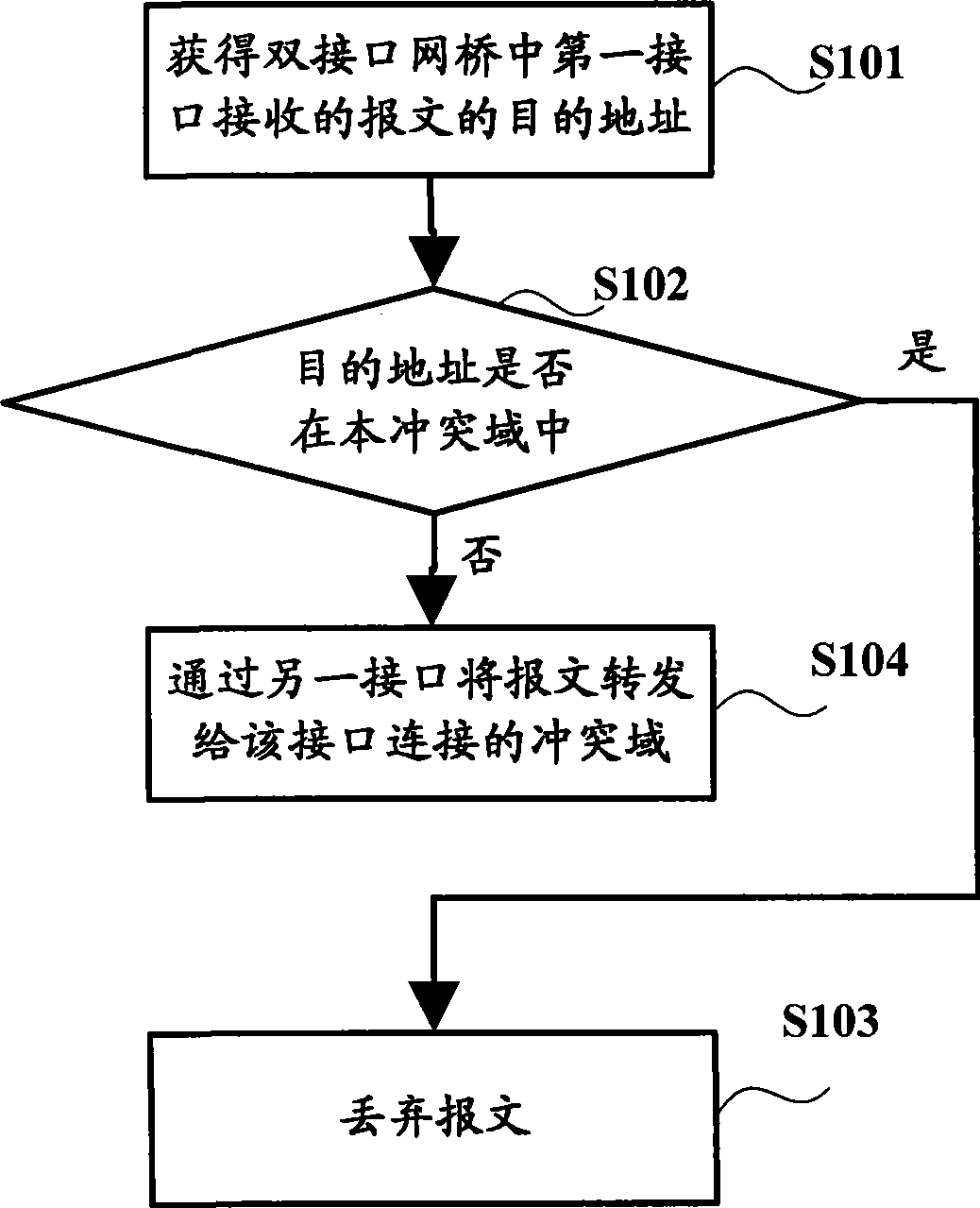
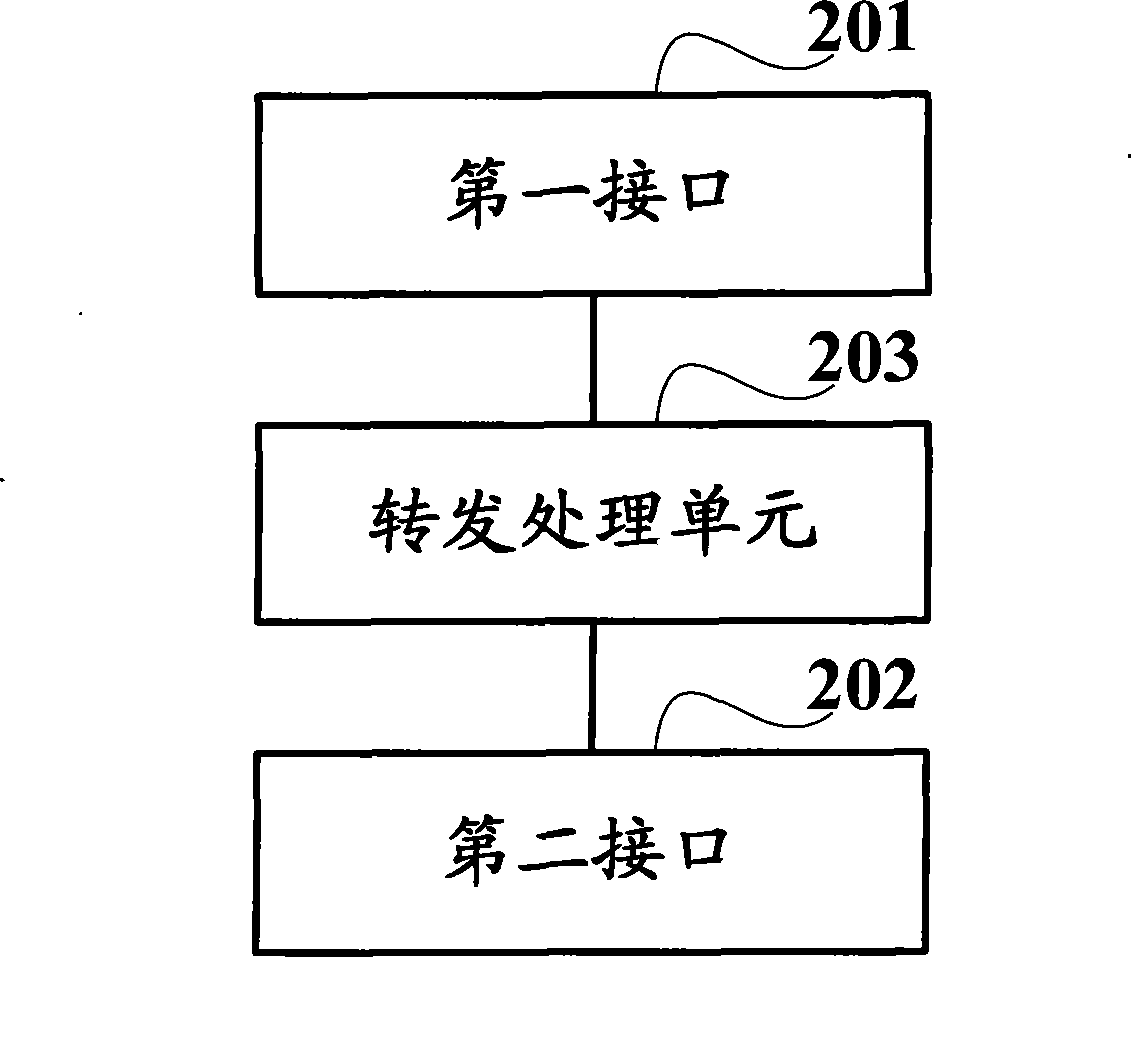
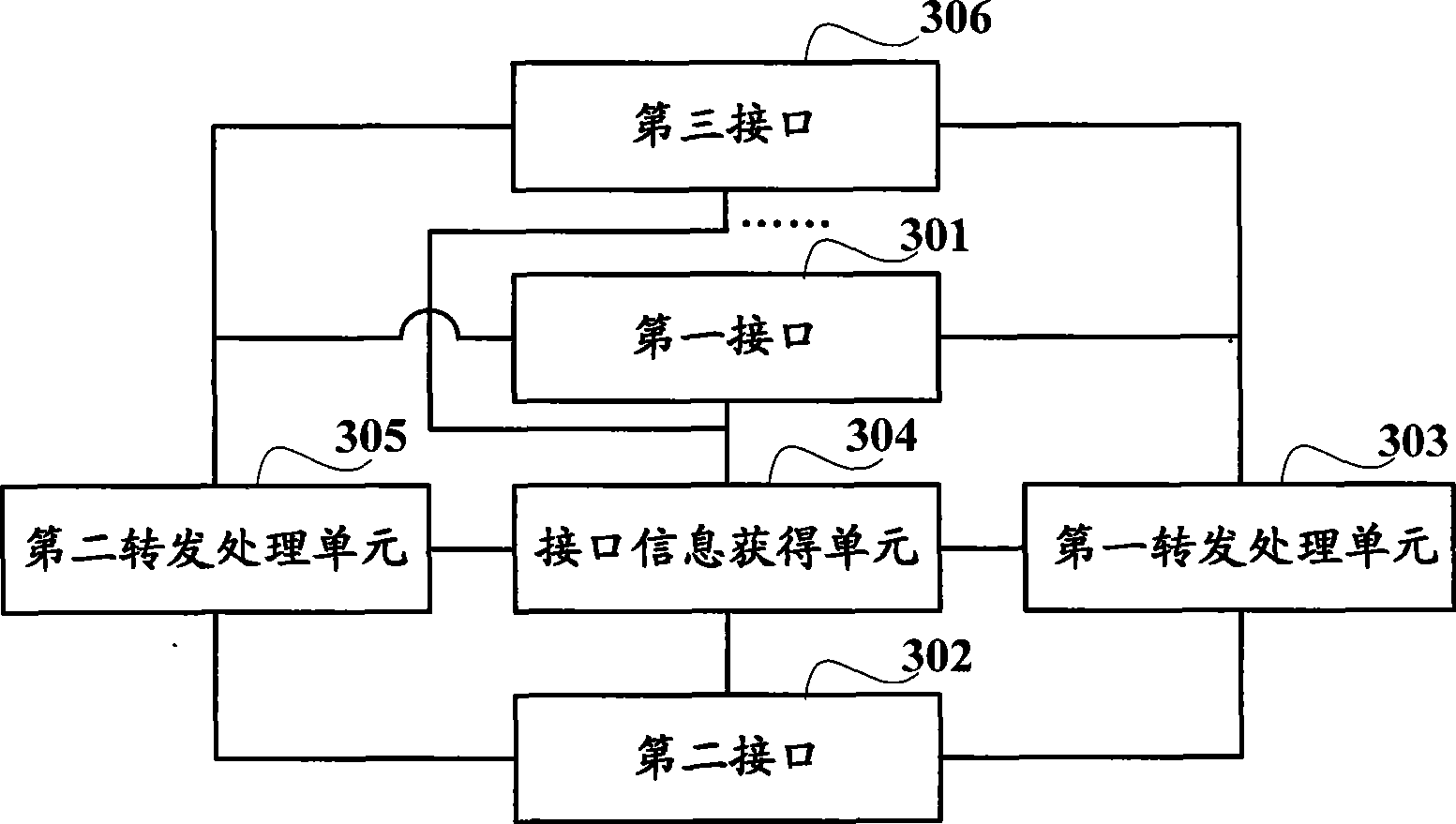
Method for forwarding packet by network bridge and network bridge therefor
ActiveCN101459601AImprove forwarding speedSimplify the addressing processNetworks interconnectionCollision domainComputer science
The invention discloses a method for transmitting messages by a network bridge and a network bridge, which relate to the technical field of communication. The method for transmitting messages by a network bridge with double interfaces comprises obtaining destination address of messages from the message received by a first interface in the network bridge with double interfaces, searching the destination address in the a first address table of a collision domain connected with the first interface, and transmitting the messages to the collision domain connected with the second interface through the second interface in the double interfaces when the first address table can not find the destination address. The method and the network bridge simplify the searching process, reduce resource consumption, and improve the transmitting speed of the messages.
Owner:RUIJIE NETWORKS CO LTD
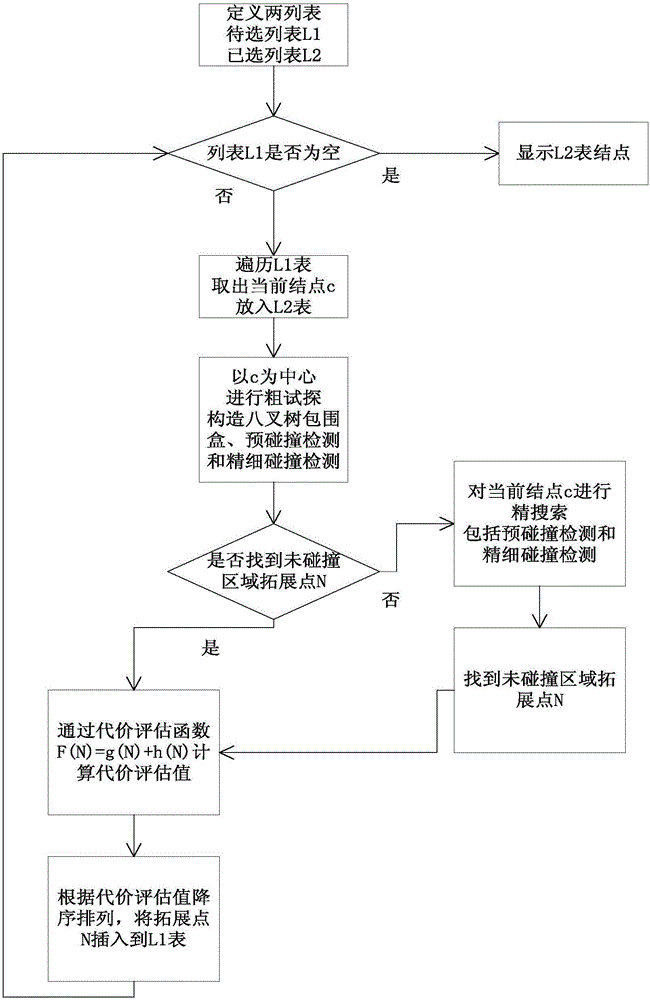
Route planning optimization method based on collision detection of hierarchical bounding volume for three-dimensional complex scene
InactiveCN106780762AImprove planning effectivenessImprove stabilityImage data processingCost evaluationAlgorithm
The invention discloses a route planning optimization method based on collision detection of a hierarchical bounding volume for a three-dimensional complex scene. The method comprises the steps that (1) two lists, namely a to-be-selected list L1 and a selected list L2 are defined; (2) the list L1 is traversed sequentially, and a current node c is extracted and put in the list L2 to indicate that non-collision domain expansion points are searched for the current node c; (3) rough probing is performed with the node c being a center, wherein rough probing mainly includes setting the dimensions and partition size of the bounding volume and performing pre-collision detection and fine collision detection along a certain direction; (4) whether rough probing succeeds or not is judged, if yes, a next node in the list L1 is skipped to, and otherwise fine search is performed on the current node c, pre-collision detection and fine collision detection are performed along a set direction, and non-collision domain expansion points N are recorded; (5) the non-collision domain expansion points N are subjected to A* cost evaluation and descending ordering and are interposed into the list L1; and (6) the list L1 is traversed cyclically to find out a minimum value of cost evaluation to serve as a current node, and the steps are repeated to the end. Through the route planning optimization method based on collision detection of the hierarchical bounding volume for the three-dimensional complex scene, the route planning effect and planning efficiency are effectively improved. The technical scheme is adopted to solve technical problems.
Owner:ZHEJIANG UNIV OF TECH
Exposed terminal optimizing method on basis of physical layer interference information
ActiveCN102612161ADoes not affect bandwidthValid encodingError prevention/detection by using return channelWireless communicationOriginal dataData information
The invention relates to a communication method, which is based on interference elimination technology and used for solving the problems of exposed terminals in the wireless network. An exposed terminal optimizing method is based on the OFDM (orthogonal frequency division multiplexing) modulation technology, encodes wireless network node information into interference signals by communication interference technology from the physical layer of the wireless local area network. Interference signals carrying node information, namely control information, are overlapped into original data signals in an 'accessory' manner and are transmitted with data information synchronously. By the transmission mode, resource consumption of the control information can be saved greatly, raw data receiving nodes acquire raw data by eliminating interference signals by the interference offset technology, and control information receiving nodes demodulate the control information from the interference signals by energy detection so as to acquire transmitting node lists. Whether the nodes are exposed terminals or not can be judged by the nodes according to a neighbor table acquired from a routing layer, the total throughput of the network can be increased by increasing parallel connections in a collision domain, and space multiplexing rate is increased.
Owner:GUANGZHOU HKUST FOK YING TUNG RES INST
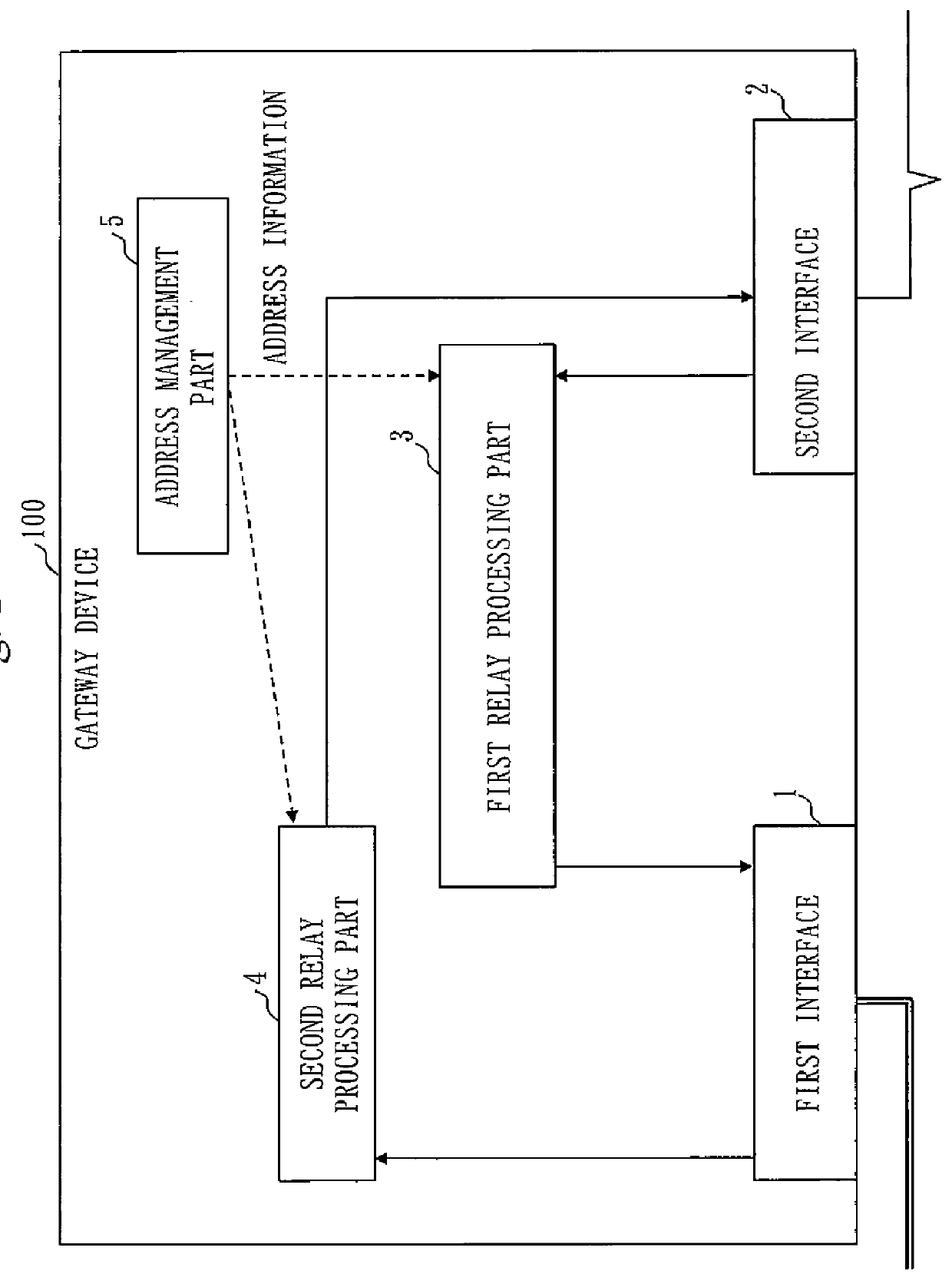
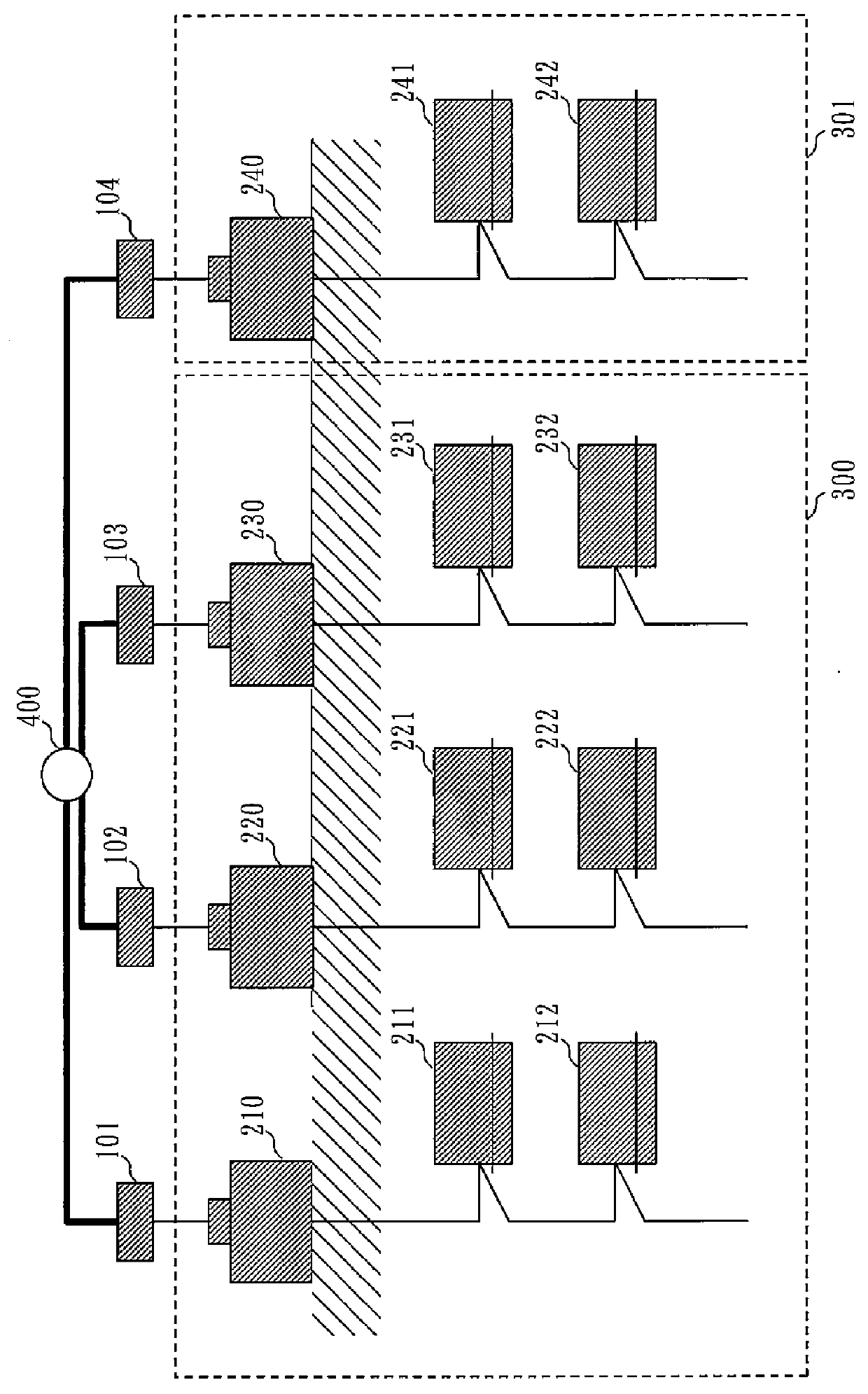
Gateway device, network system including gateway device, air-conditioning outdoor unit, and air-conditioning network system
InactiveUS20160036600A1Special service provision for substationMechanical apparatusCollision domainMulticast communication
A gateway device includes an address manager that manages address information enabling transmission via a second interface of an own gateway device and another gateway device, a first relay that, if the data received by the second interface is multicast data, adds to the multicast data received, address information and a header conforming to a protocol of a non-band-sharing network, and outputs the multicast data to a first interface, and a second relay that, if the data received by the first interface includes address information, extracts only multicast data from data conforming to the protocol of the non-band-sharing network, and transmits the multicast data to the second interface. Even when collision domain for N (N is 2 or more) of facility networks having different address architectures is to be divided using (N+1) or more of gateways, multicast communication that match the area of the address architecture can be realized.
Owner:MITSUBISHI ELECTRIC CORP
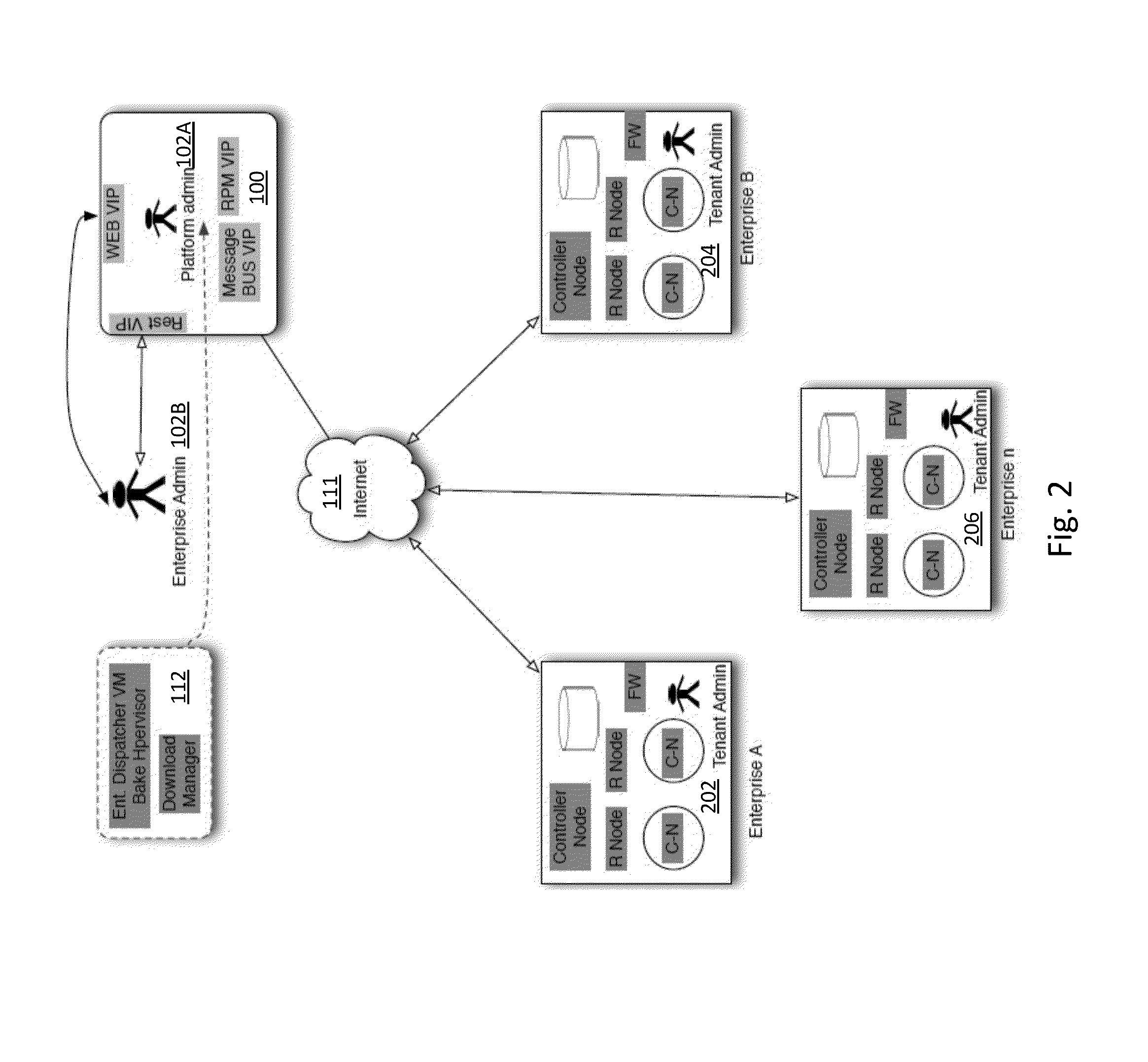
METHOD AND APPARATUS FOR CREATING SOFTWARE DEFINED CLOUD COLLISION DOMAIN NETWORKS USING A tELASTIC CONTROLLER
InactiveUS20150067130A1Quick configurationDigital computer detailsData switching networksVirtualizationSystems management
Method and Apparatus for rapid scalable unified infrastructure system management platform are disclosed by discovery of compute nodes, network components across data centers, both public and private for a user; assessment of type, capability, VLAN, security, virtualization configuration of the discovered unified infrastructure nodes and components; configuration of nodes and components covering add, delete, modify, scale; and rapid roll out of nodes and components across data centers both public and private..
Owner:CONNECTLOUD
Complex part laser cladding interference detection and track correction method
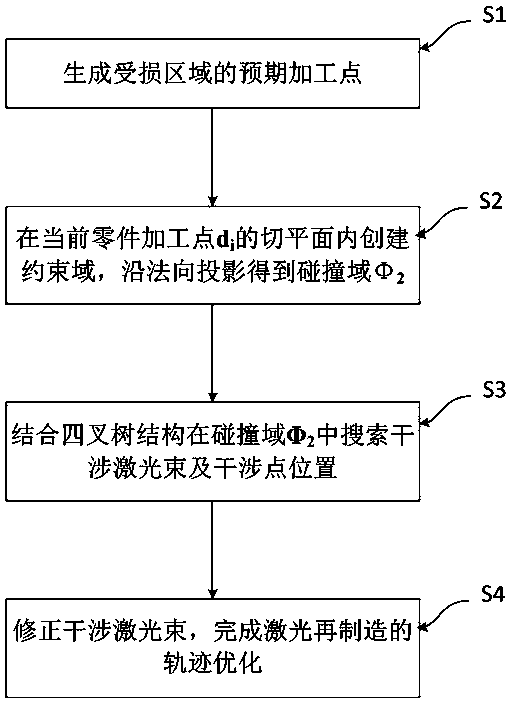
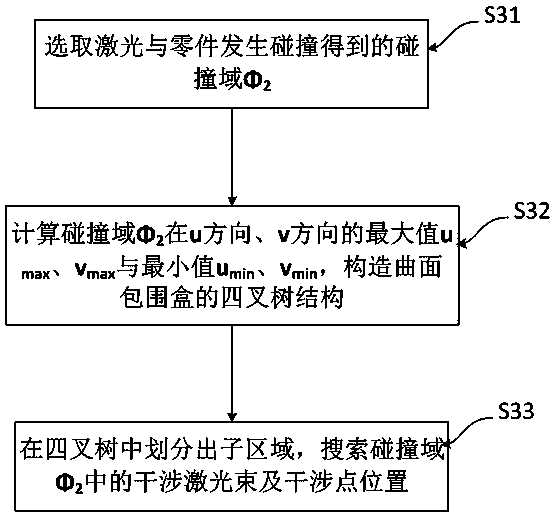
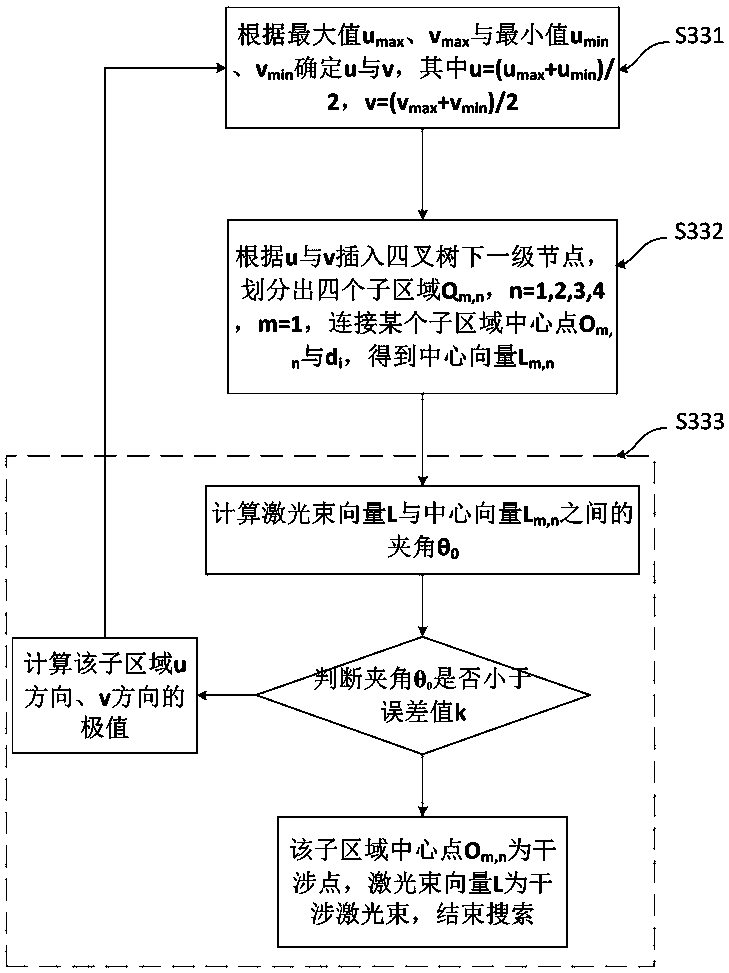
ActiveCN110543709AAvoid interferenceIncrease the scope of applicationIncreasing energy efficiencySpecial data processing applicationsManufacturing technologyOptoelectronics
The invention relates to the technical field of laser cladding, in particular to a laser cladding interference detection and track correction method for complex parts. The method comprises the following steps: S1, generating an expected processing point of a damaged area; S2, creating a constraint domain in the tangent plane of the current part machining point di, and obtaining a collision domainphi2 through normal projection; S3, searching an interference laser beam and an interference point position in a collision domain phi2 in combination with a quadtree structure; and S4, correcting theinterference laser beam, and completing track optimization of laser remanufacturing. According to the method, a constraint domain is created in a tangent plane of a current part machining point; projecting along the normal direction is performed to obtain a collision domain; interference laser beams and interference point positions are quickly searched in a collision domain in combination with a quadtree structure; and according to the laser remanufacturing method, posture correction is carried out on the interference laser beam, track optimization of laser remanufacturing is completed, and therefore the phenomenon that the laser beam interferes with other parts is avoided, the parts and laser equipment are protected, the application range of the laser remanufacturing technology is widened, and machining safety is improved.
Owner:XINJIANG UNIVERSITY
Wireless router version upgrading method based on DR election
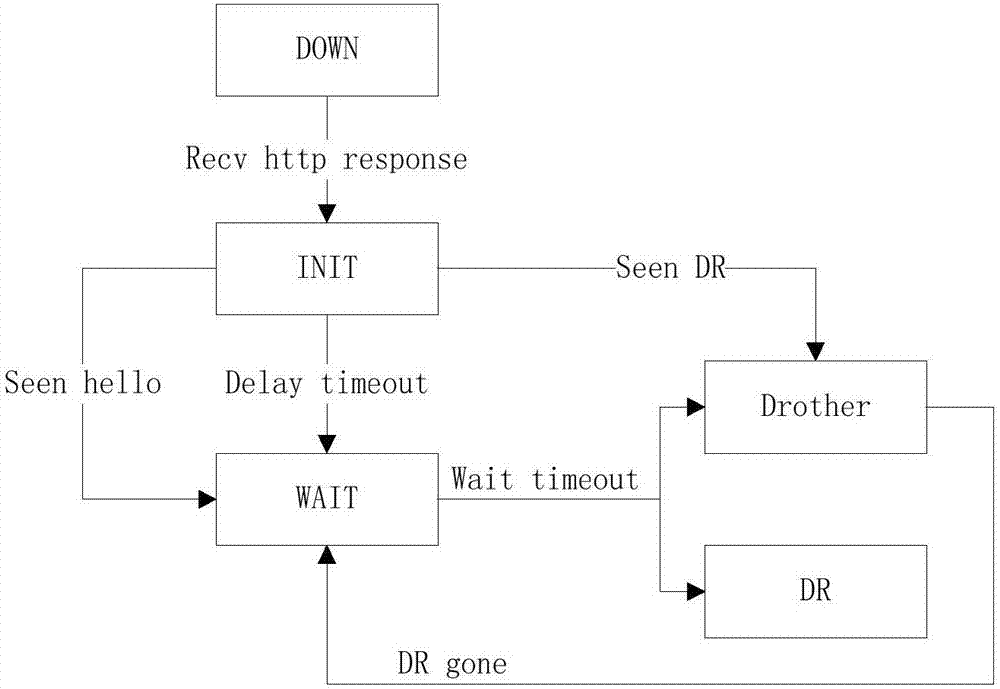
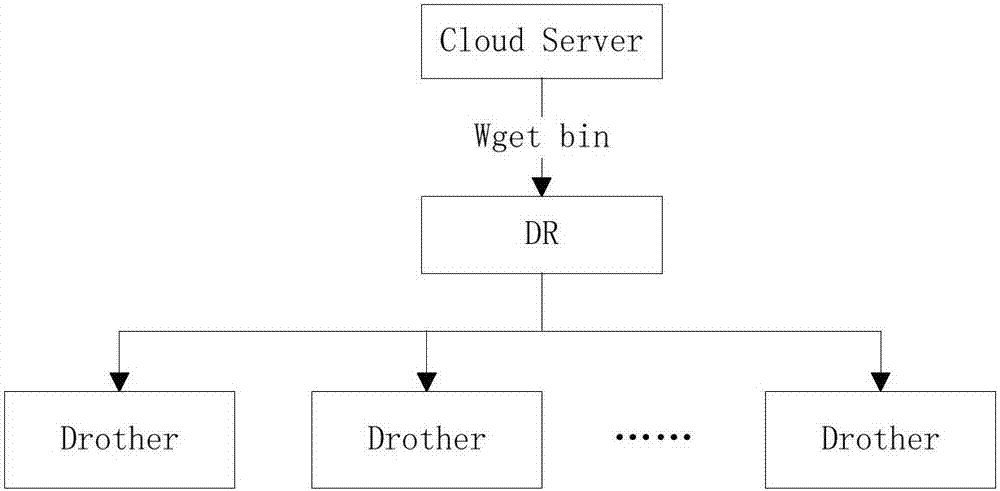
ActiveCN107483224AReduce bandwidth pressureNo downtimeData switching networksWireless routerCollision domain
The invention discloses a wireless router version upgrading method based on DR election. A DR generated by election downloads an update file in a collision domain, and the update file is propagated to other to-be-upgraded equipment in the collision domain. According to the scheme, batch upgrading on APs in a local area network in fixed time can be implemented, bandwidth resources of the local area network are effectively utilized, and a bandwidth pressure of a cloud server is reduced.
Owner:SHANGHAI BAUD DATA COMM
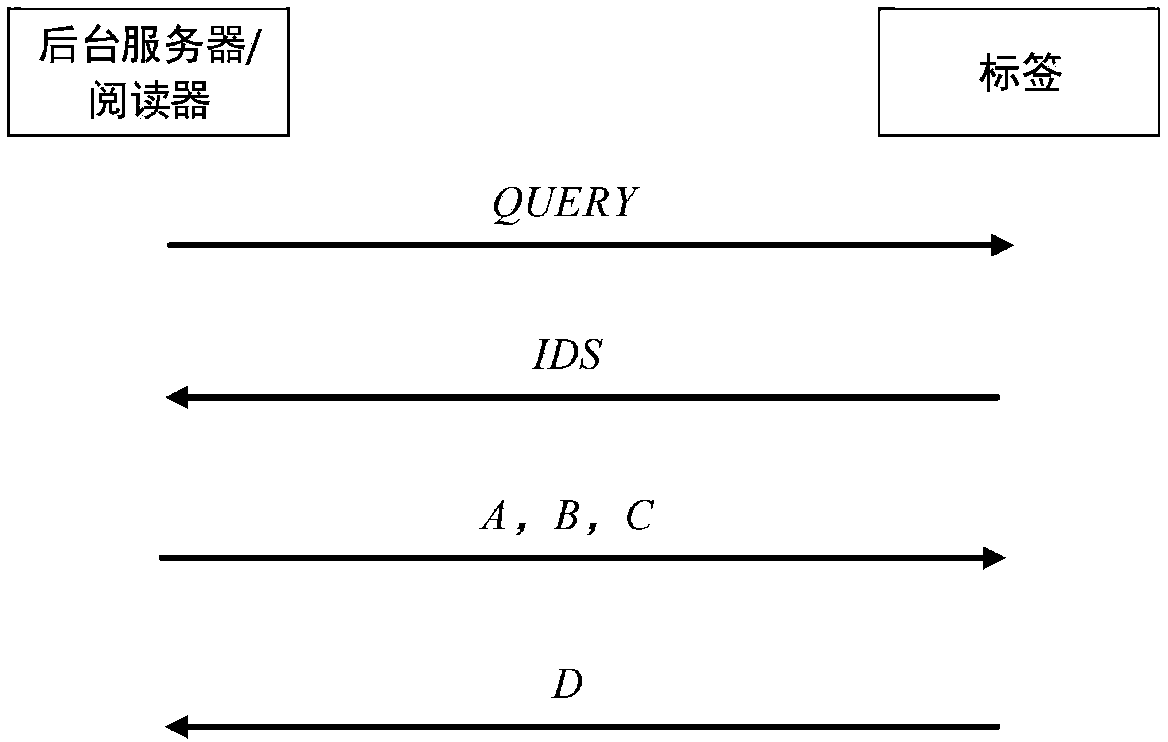
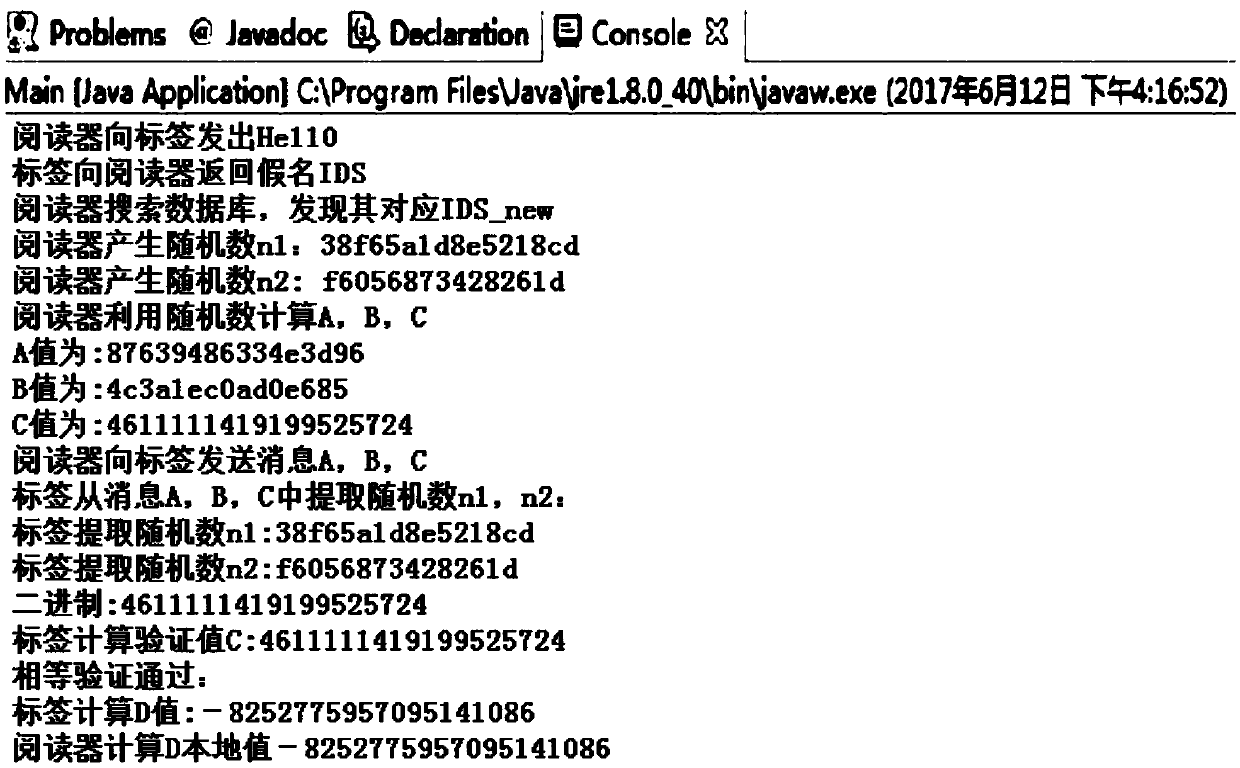
Method for enhancing ability of protocol to resist desynchronization attacks
InactiveCN107634828AEnsure consistencyGuaranteed confidentialityKey distribution for secure communicationSecurity arrangementCollision domainAuthentication
A method for enhancing an ability of a protocol to resist desynchronization attacks comprises the following steps: a reader sends an authentication request message to a label; the label calculates IDSnew and sends the IDSnew to the reader; the reader searches the IDSnew in a background database; if the IDSnew does not exist, the reader waits for the label to transmit IDSold and re-searches the database, and the phenomenon shows that a new key of one party of the label is not updated; if the IDSnew exists, the reader generates two random numbers n1 and n2, calculates A, B and C, and sends messages to the label; after receiving the messages A, B and C, the label extracts the random numbers n1 and n2, calculates local C', judges whether C is equal to C', calculates a D value, and sends the Dvalue to the reader; otherwise, the authentication fails, wherein D is equal to FORMULA (for the detailed formula, please refer to the abstract), and the keys and pseudonyms are finally updated; and after receiving the message D, the reader verifies whether the message D is equal to a local value D', and if yes, the corresponding keys and pseudonyms in the database are updated. According to the method, the correlation between the random numbers can be enhanced, the collision domain of unit values of the random numbers can be reduced, and thus the ability of the protocol to resist the desynchronization attacks can be enhanced, and the security of the protocol can be effectively improved.
Owner:XUZHOU MEDICAL UNIV
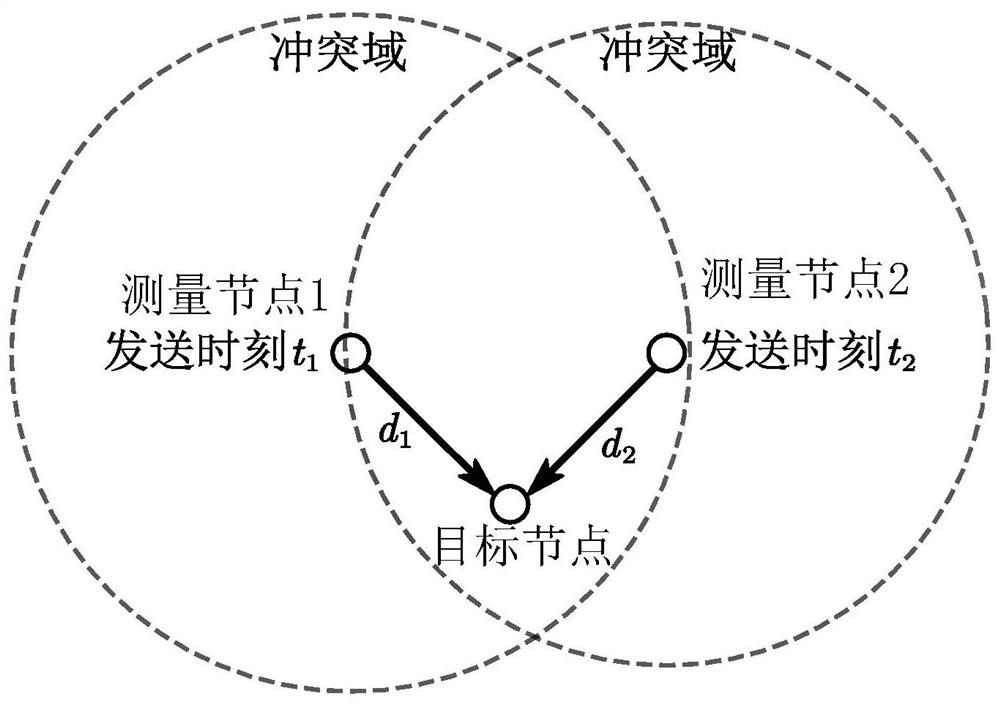
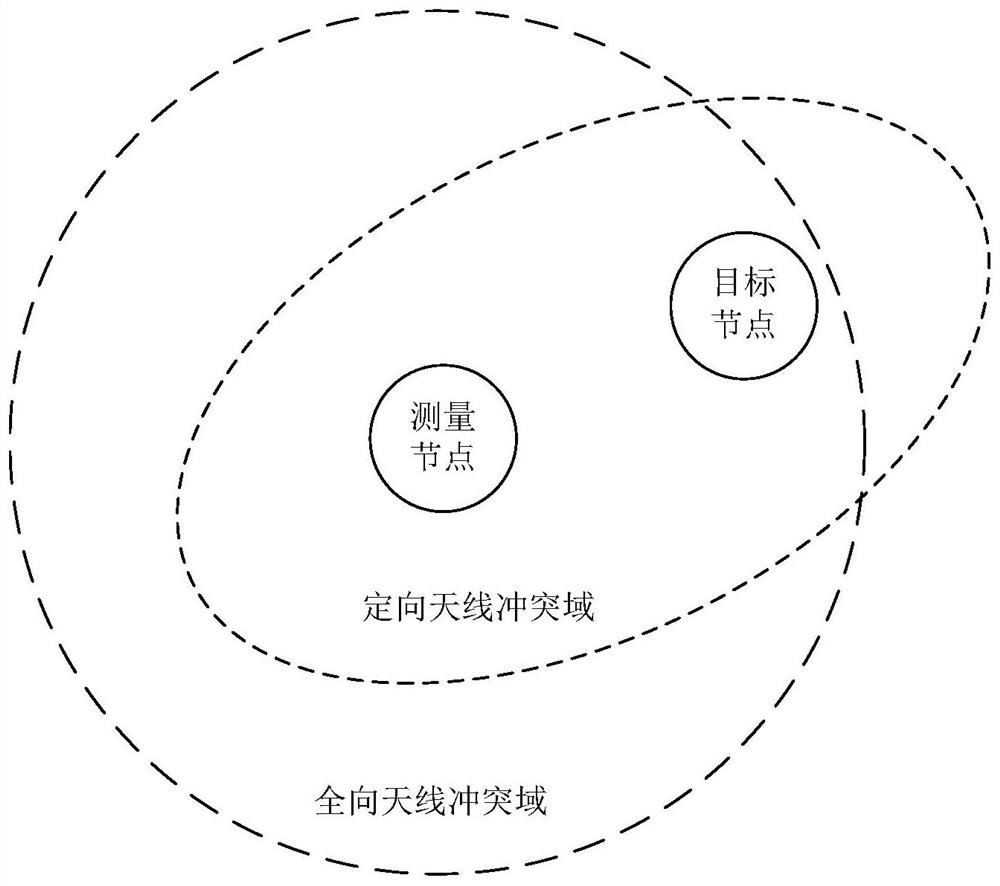
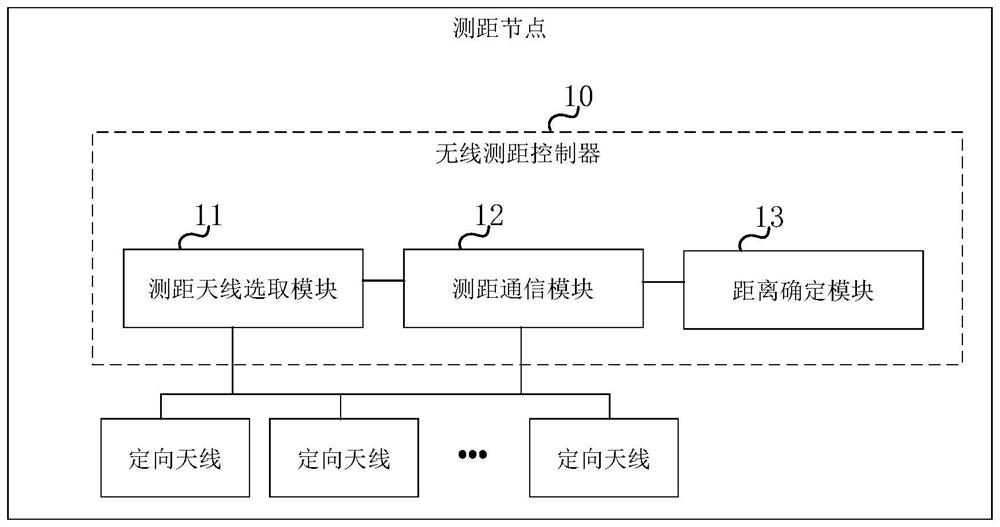
Wireless ranging, direction finding and positioning method and related equipment
PendingCN112394319AReduced collision domain sizeThe scope of the collision domain is reducedRadio wave direction/deviation determination systemsPosition fixationDirectional antennaCollision domain
The embodiment of the invention provides a wireless ranging, direction finding and positioning method and related equipment, and the method comprises the steps: selecting one of a plurality of directional antennas disposed at a range finding node as a target antenna corresponding to a target node in a current range finding period, the orientations corresponding to the directional antennas being different; only controlling data communication between the target antenna and the target node by using a carrier-free communication technology; and acquiring distance information of the ranging node relative to the target node based on a result of the data communication. According to the invention, the conflict domain range of wireless signals in the measurement process can be effectively reduced, and the measurement capacity of the target node can be effectively improved.
Owner:TSINGOAL BEIJING TECH CO LTD
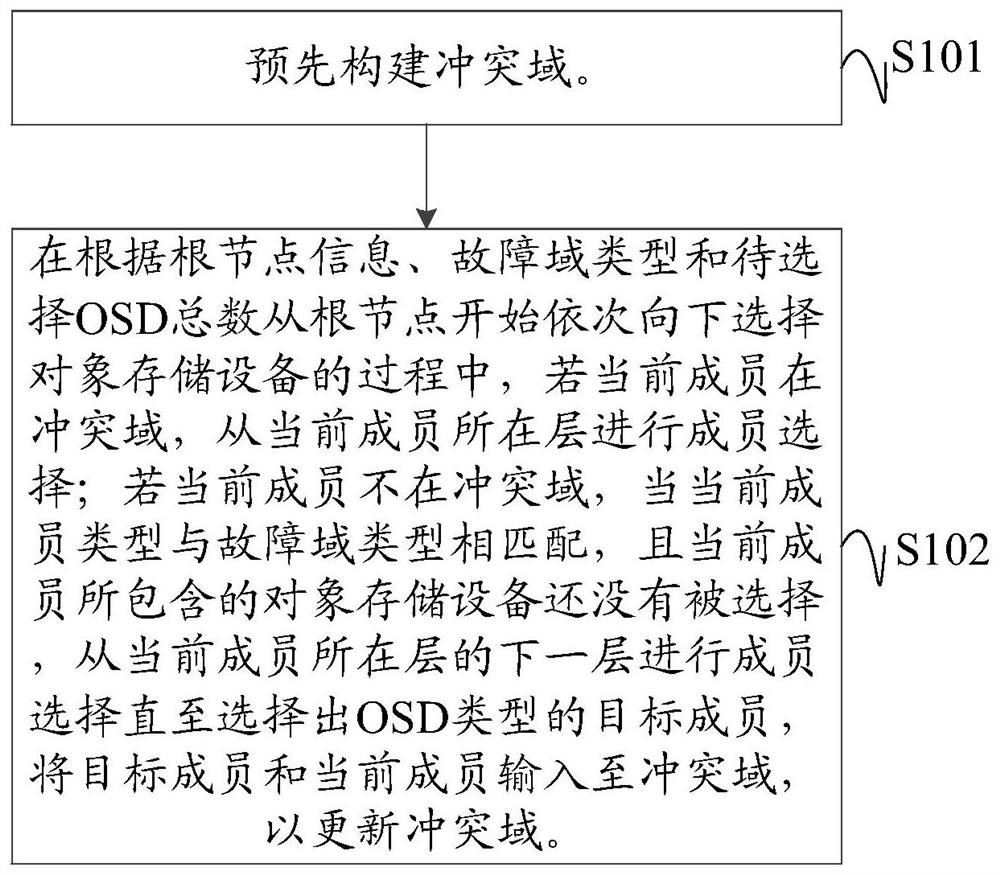
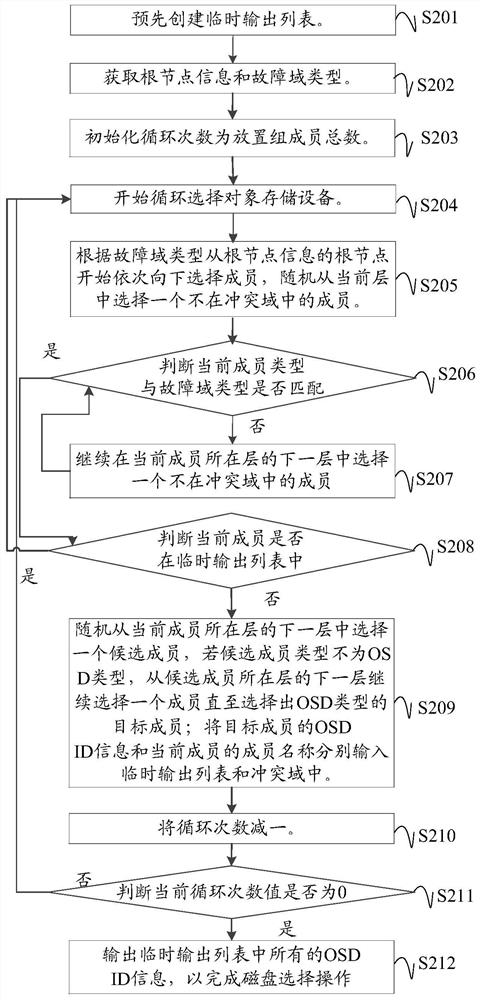
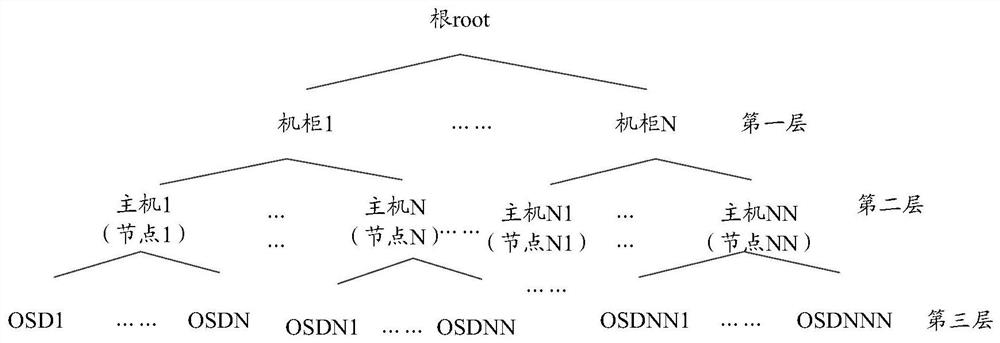
Disk selection method and device for distributed storage cluster and readable storage medium
ActiveCN113126931AImprove efficiencyImprove selection efficiencyInput/output to record carriersComputer hardwareEngineering
The invention discloses a disk selection method and device for a distributed storage cluster and a computer readable storage medium. The method comprises the steps that a conflict domain used for storing selected object storage equipment and related information of a fault domain where the selected object storage equipment is located is constructed. In the process of sequentially selecting the OSDs downwards from the root node according to the root node information, the fault domain type and the total number of the OSDs to be selected, if the current member is in the conflict domain, selecting other members from the layer where the current member is located; if the current member is not in the conflict domain, the type of the current member is matched with the type of the fault domain, and the object storage device contained in the current member is not selected, member selection is carried out from the next layer of the layer where the current member is located until a target member of the OSD type is selected; and the target member information and the current member information are input into the conflict domain to update the conflict domain, thereby effectively reducing the frequency of invalid disk selection by a data distribution algorithm, improving the disk selection efficiency, and reducing the occupation of CPU resources and the consumption of time.
Owner:SHANDONG YINGXIN COMP TECH CO LTD
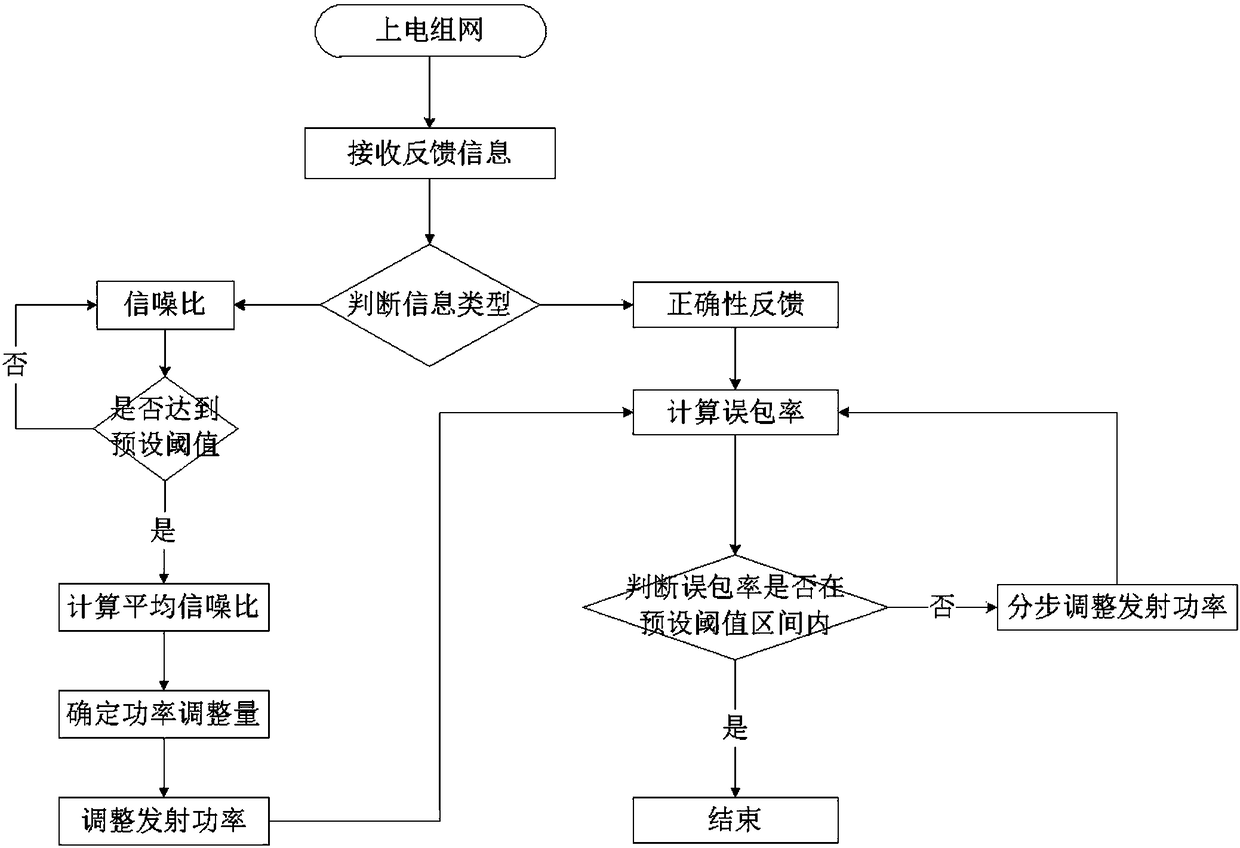
Self-adaptive method for controlling collision domain in power line carrier communication
InactiveCN108521288ATransmit power controlRealize dynamic adjustmentPower distribution line transmissionCross-talk reductionTransmitted powerCarrier signal
The invention discloses a self-adaptive method for controlling a collision domain in power line carrier communication, and relates to the technical field of power line carrier communication. The self-adaptive method comprises: a networking step in which a slave node is powered up and networked with a preset transmitting power; an adjustment amount determining step in which the slave node receivesfeedback information of a relay node after networking, and when a variable in the feedback information reaches a preset threshold value, the slave node determines an adjustment amount according to thevariable; and a dynamic adjustment step in which the slave node dynamically adjusts the transmitting power according to the adjustment amount. The self-adaptive method of the invention solves the problem of high collision rate of carrier monitoring between nodes caused by fixed transmitting power, and is mainly used for controlling the collision domain in the power line carrier communication.
Owner:WU QI TECH INC +1
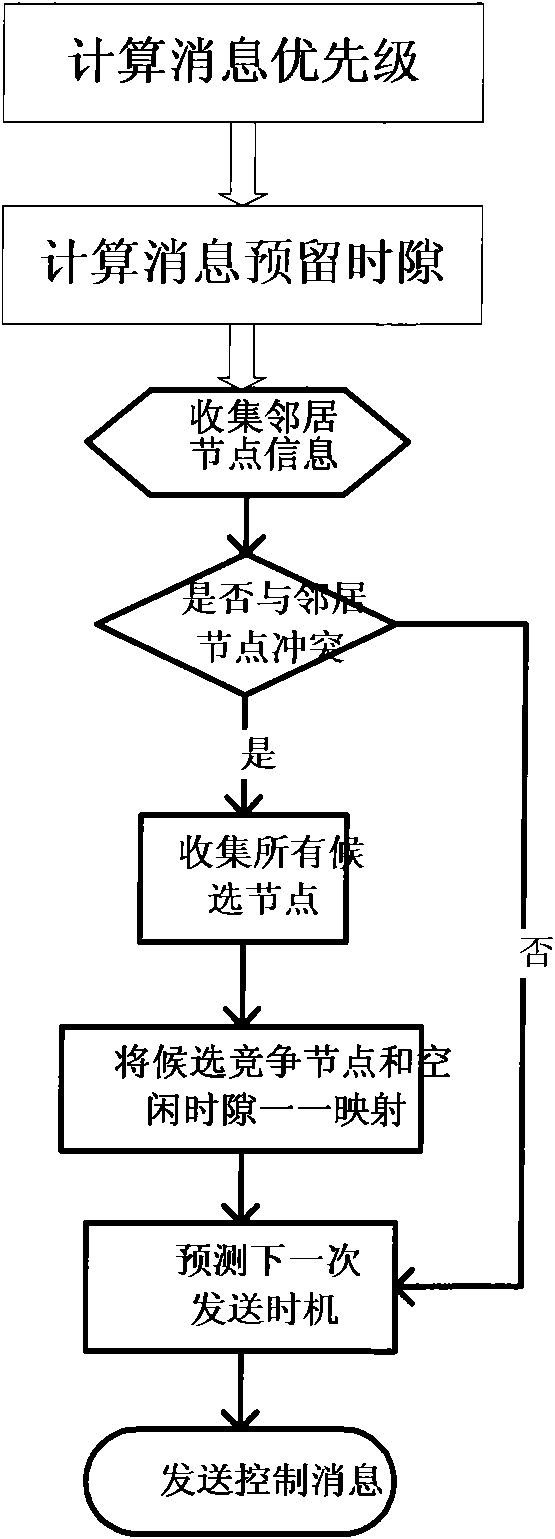
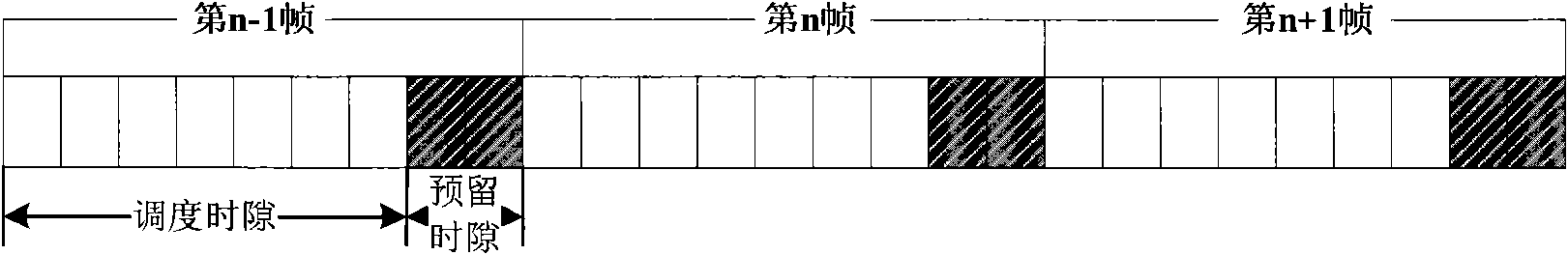
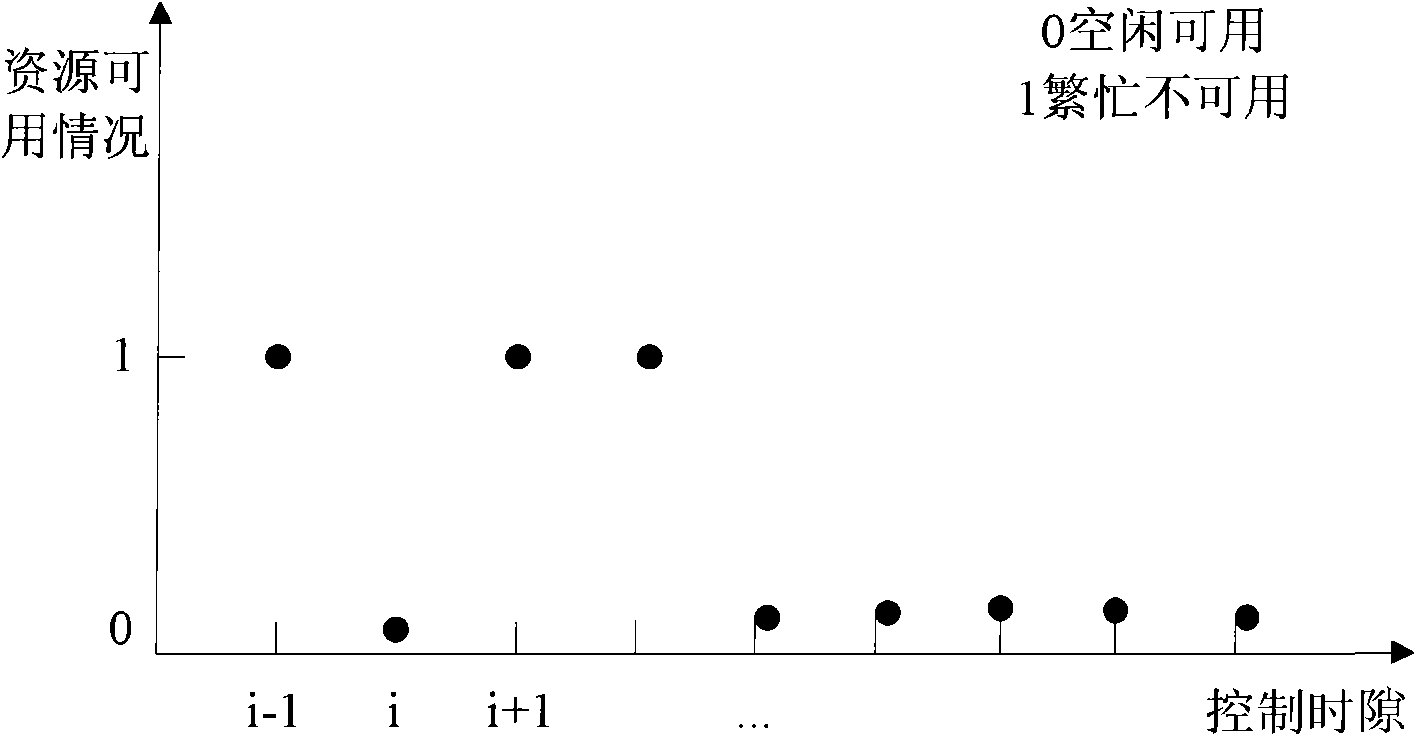
Conflict avoidance-based dispatching method for wireless MESH network
ActiveCN101848032AAvoid confictRadio transmission for post communicationData switching networksWireless mesh networkCollision domain
The invention provides a conflict avoidance-based dispatching method for a wireless MESH network, which comprises the following steps of: determining the reserved time slot of an MSH-DSCH message and calculating the priority level of the MSH-DSCH message; collecting the transmission moment number of the next transmission of two-hop neighboring nodes in a collision domain range by a node, updating the transmission moment into an unusable resource on a binary bitmap saved by the node and counting the numbers of all neighboring nodes in a two-hop range by the node; determining whether the transmission moment of the node collides with the next transmission moment of the neighboring nodes in the two-hop range or not; and if collision occurs, arranging candidate competition node sets according to node numbers before the transmission moment of the node, searching the binary bitmap, forming free time slot sets, arranging the free time slot sets according to the transmission moment number, mapping the candidate competition node sets and the free time slot sets and selecting to transmit in the reserved time slot or competing the same reserved time slot, wherein in the transmission moment of the node, a control message which comprises the next transmission moment of the node is sent.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method for blocking worm propagation and device for implementing the same
InactiveCN101197809AStop transmissionAvoid spreadingData switching networksBroadcast packetNetwork data
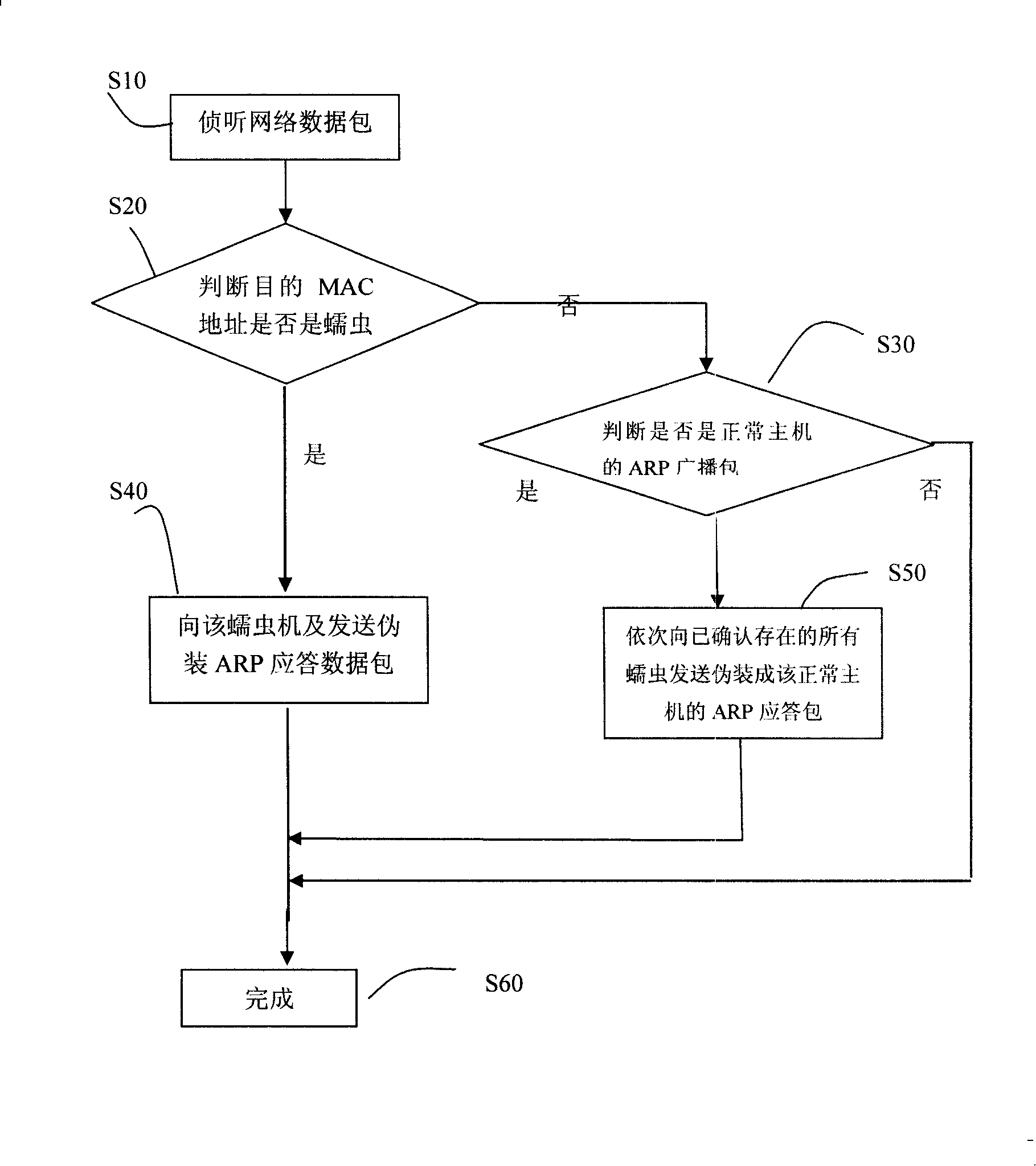
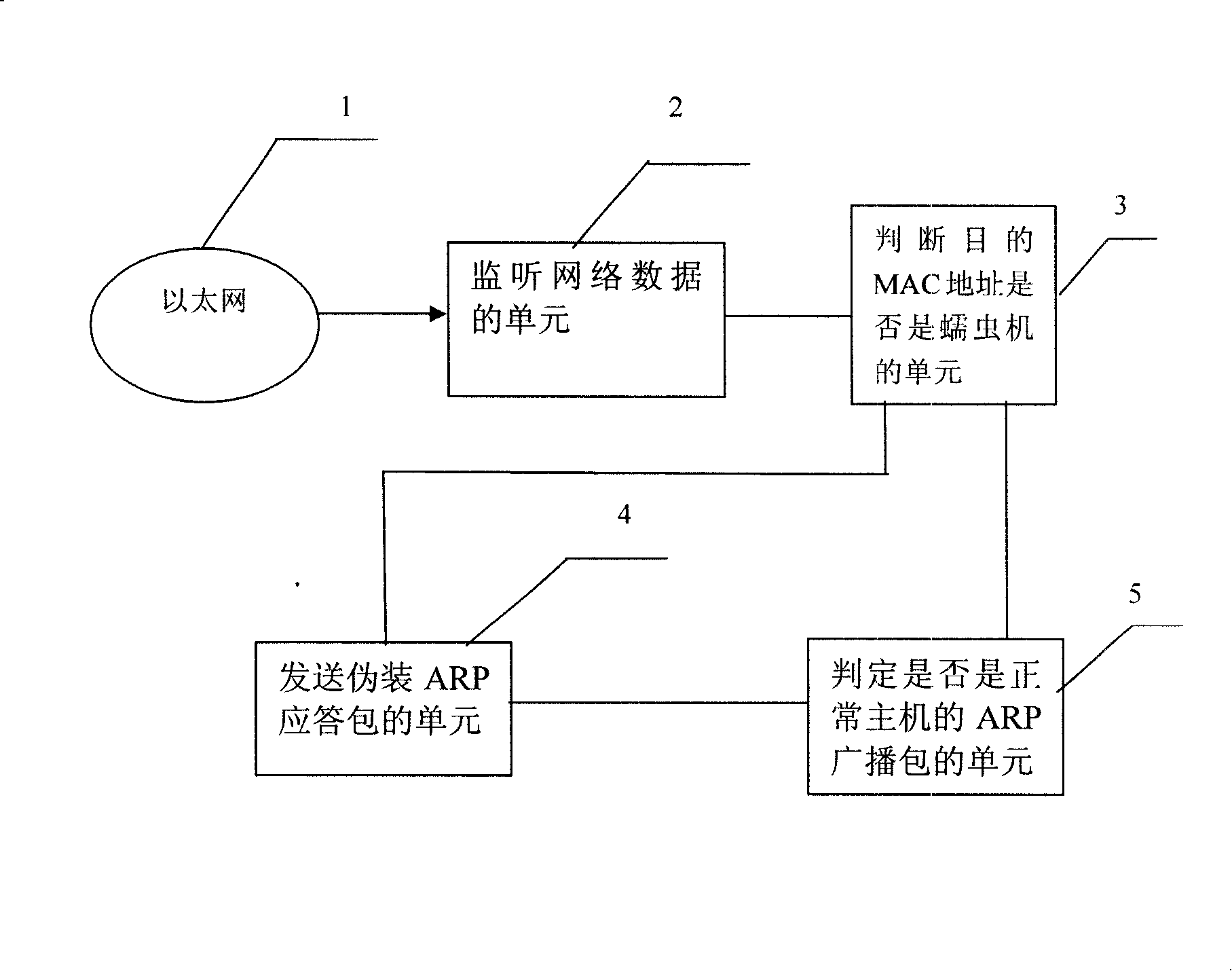
The invention provides a method for blocking the spreading of worm virus, which comprises that: a step of monitoring network data, all data packets in a two-layer network collision domain are monitored in the step; a step of judging a target MAC address to be a worm machine or not, the target MAC address of the monitored data packet is judged to be a host which is identified as a worm machine or not in the step; a step of judging to be an ARP broadcast packet of a normal host or not, if a non-worm machine is determined in the step of judging the target MAC address to be the worm machine or not, the data packet is judged further to be the ARP broadcast packet or not; a step of sending a masquerade ARP reply packet to the worm machine, if a worm machine is determined in the step of judging the target MAC address to be the worm machine or not, the masquerade ARP reply packet is sent to the worm machine, if a ARP broadcast packet is determined in the step of judging to be the ARP broadcast packet of a normal host or not, ARP reply packets disguised to be the normal host are sent to all worm machines determined to be existed in turn.
Owner:PEKING UNIV
Domain name matching method based on tree automaton
ActiveCN105824927AHigh matching operation efficiencySave storage spaceWeb data indexingSpecial data processing applicationsNODALDomain name
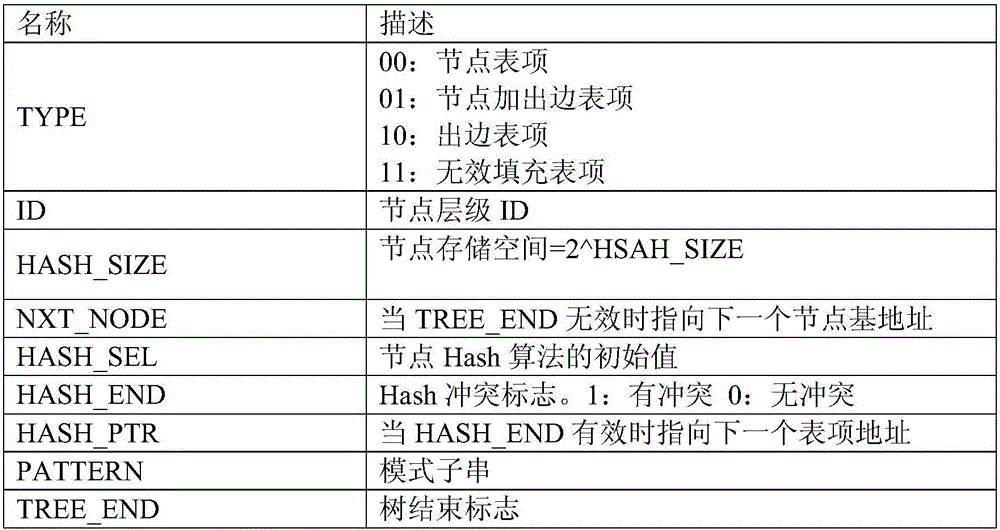
The invention relates to a domain name matching method based on a tree automaton. The method comprises the following steps: filling a domain name to be matched and each fragment of a model substring to integer multiples of n bytes, wherein n is equal to L divided by 8 and L is a minimum operation bit width of a computer system; then constructing the tree automaton by taking the n bytes of the model substring as units; then, sequentially executing the tree automaton of the domain name to be matched until a domain name matching is finished from a root node. By taking the n bytes as the matching units when a matching operation is carried out, the matching operation efficiency of the method is much higher than that of an existing character string matching method; the tree automaton takes a hash value as a table item storage address, and a storage space occupied by table items can be reduced; a hash collision domain is limited in a local-grade node. The domain name matching method based on the tree automaton is applicable to fixed prefix matching or fixed postfix matching of the domain name, and the matching operation of other character strings with same stratification characteristics.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com