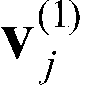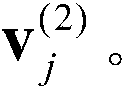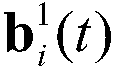Patents
Literature
37results about How to "Avoid huge workload" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
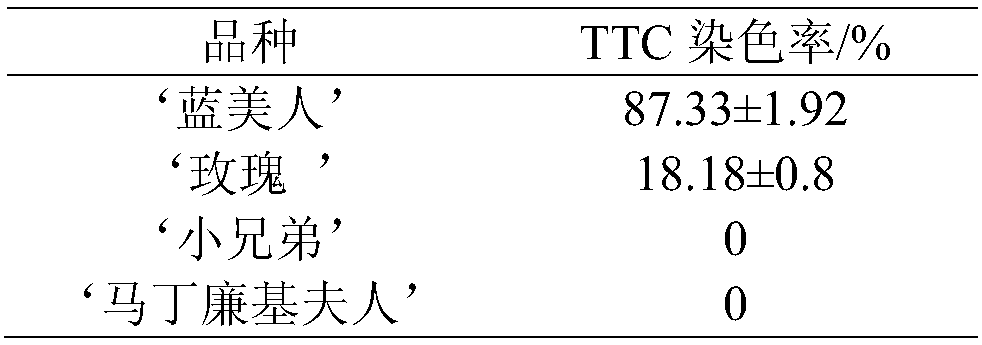
Static analysis method and system of smart phone application program
ActiveCN104715196AFast scanningImprove detection accuracyPlatform integrity maintainanceAnalysis methodAutomatic testing
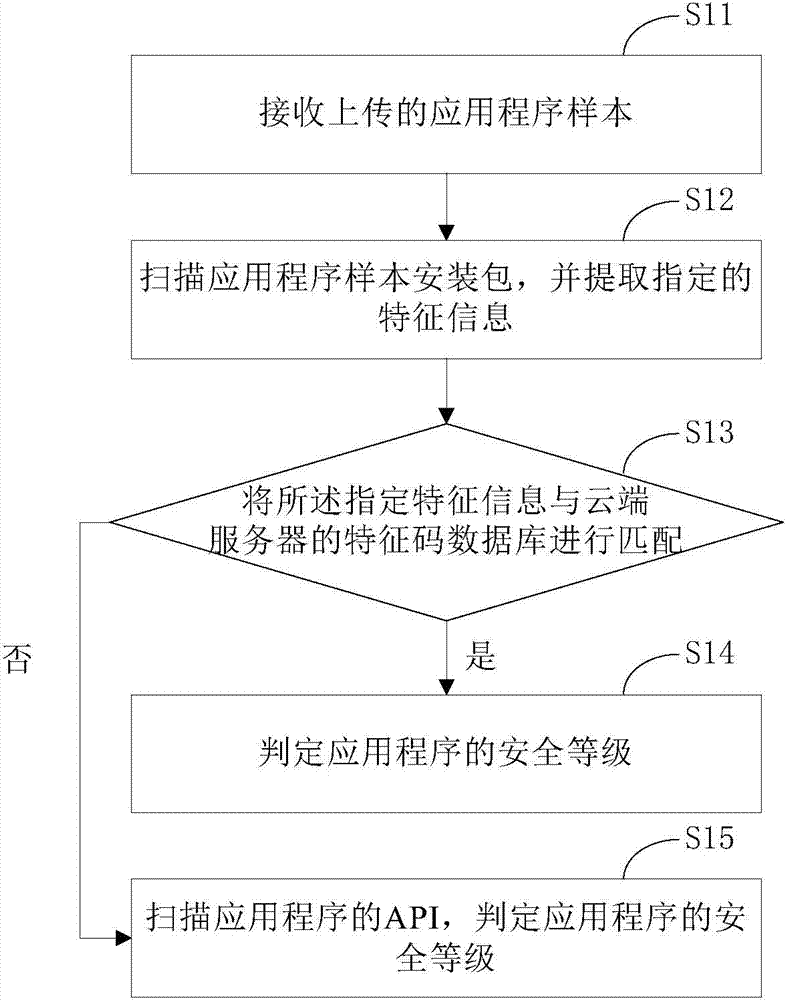
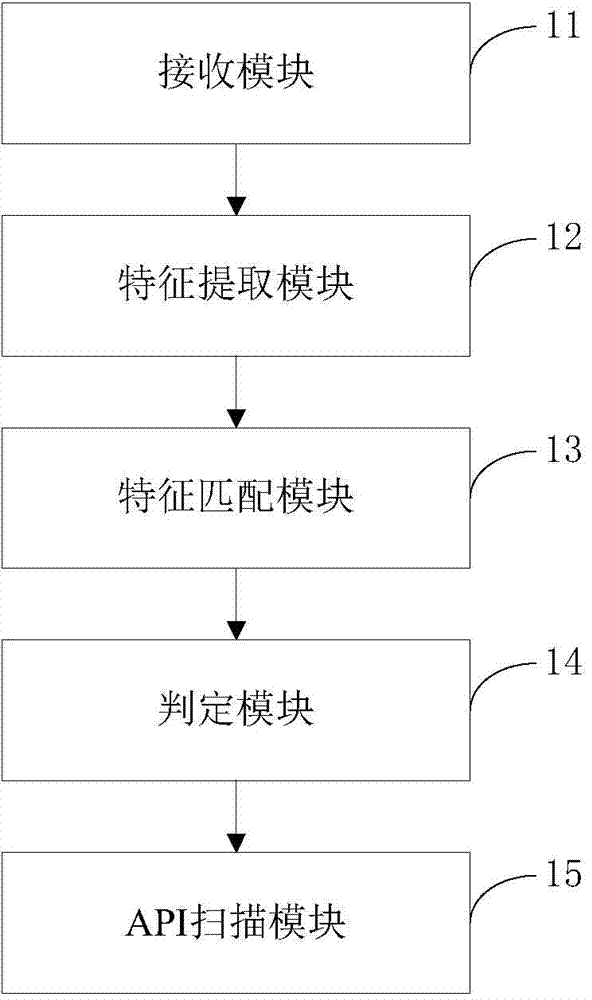
The invention provides a static analysis method of a smart phone application program. The static analysis method comprises the steps of receiving an uploaded application program sample; scanning an installation package of the application program sample and extracting specified feature information; matching the specified feature information with a feature code database of a cloud server; judging the safety level of the application program if matching is successful; scanning an API of the application program and judging the safety level of the application program if matching is unsuccessful. In addition, the invention further provides a static analysis system of the smart phone application program. According to the static analysis method and system, automatic detecting of the safety level of the application programs of an Android system and an IOS system can be achieved, the detection efficiency is high, and the accurate rate is high.
Owner:BEIJING QIHOO TECH CO LTD
Fiber vibration sensing system two-order signal feature extraction and determining method
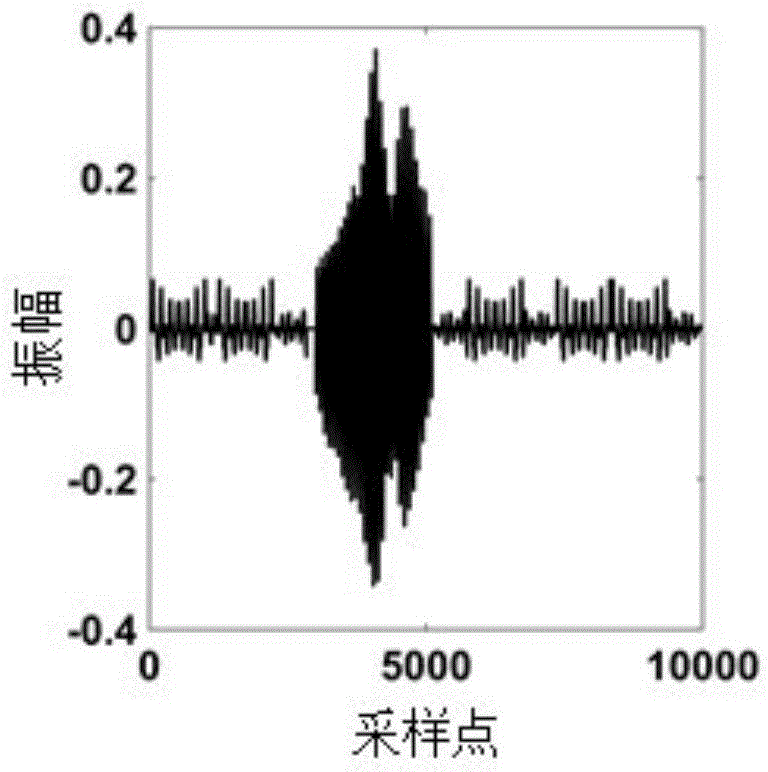
InactiveCN105606198AReduce workloadAvoid huge workloadSubsonic/sonic/ultrasonic wave measurementUsing wave/particle radiation meansFiberFeature extraction
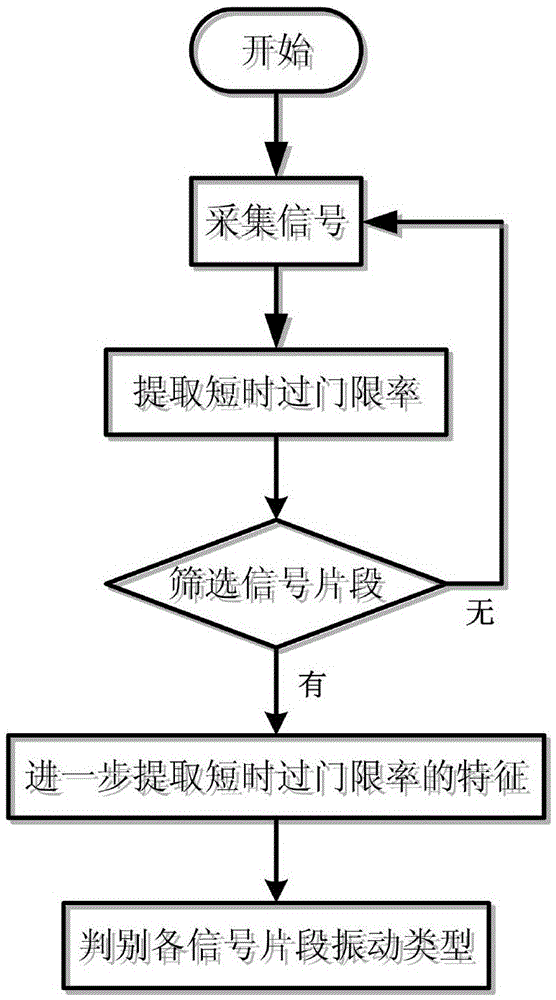
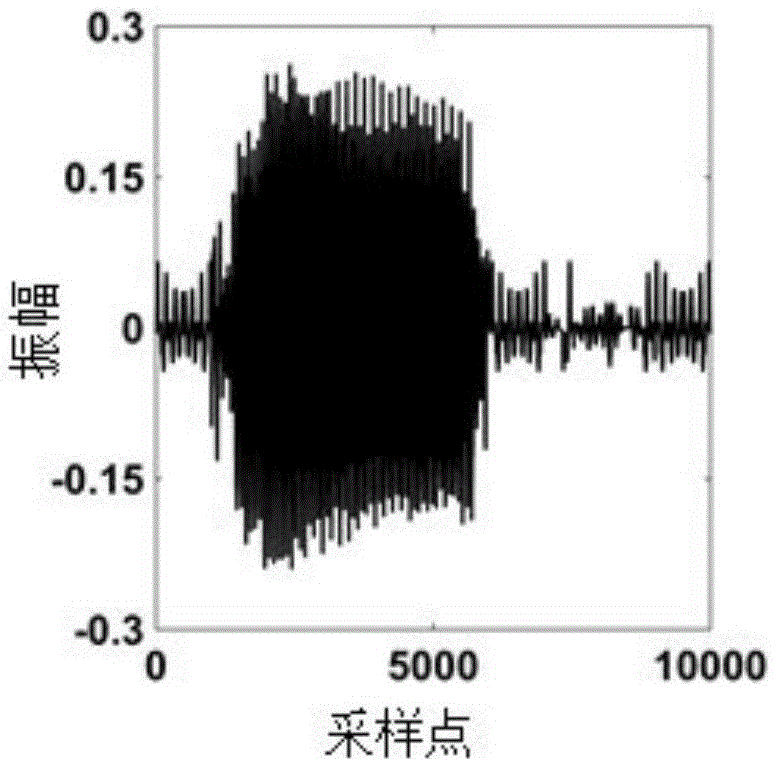
The invention discloses a fiber vibration sensing system two-order signal feature extraction and determining method, and belongs to the technical field of fiber sensing signal determining, for solving the problems of incapability of accurately determining external vibration signal types under ambient noise interference and quite low efficiency of a conventional signal type discriminating method in the prior art. The method is characterized in that first of all, a short-time over-threshold rate of external vibration signals is extracted; secondary, an average algebraic sum of the extracted short-time over-threshold rate is calculated, and signal fragments comprising external vibration information are screened; thirdly, feature extraction is further performed on the short-time over-threshold rate of the signal fragments; and finally, a vibration type of each signal fragment is determined. The method provided by the invention, as a signal type determining algorithm, though signals come from a noisy background, various external vibration signal types can be accurately and efficiently determined, there are fewer false alarms, and false alarm rate is low.
Owner:JILIN UNIV
Unmanned aerial vehicle UAV control law parameter adjusting method
InactiveCN110032797AAvoid huge workloadImprove dynamic responsivenessDesign optimisation/simulationSpecial data processing applicationsJet aeroplaneAcquired characteristic
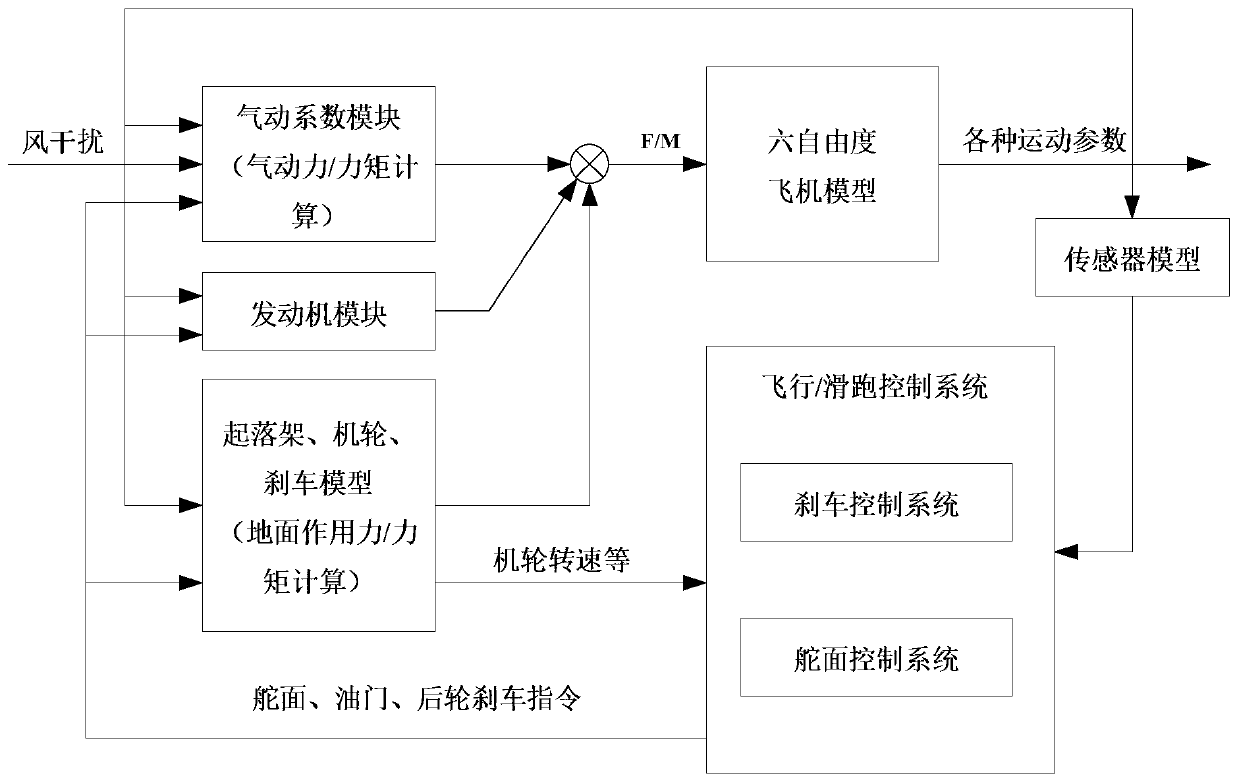
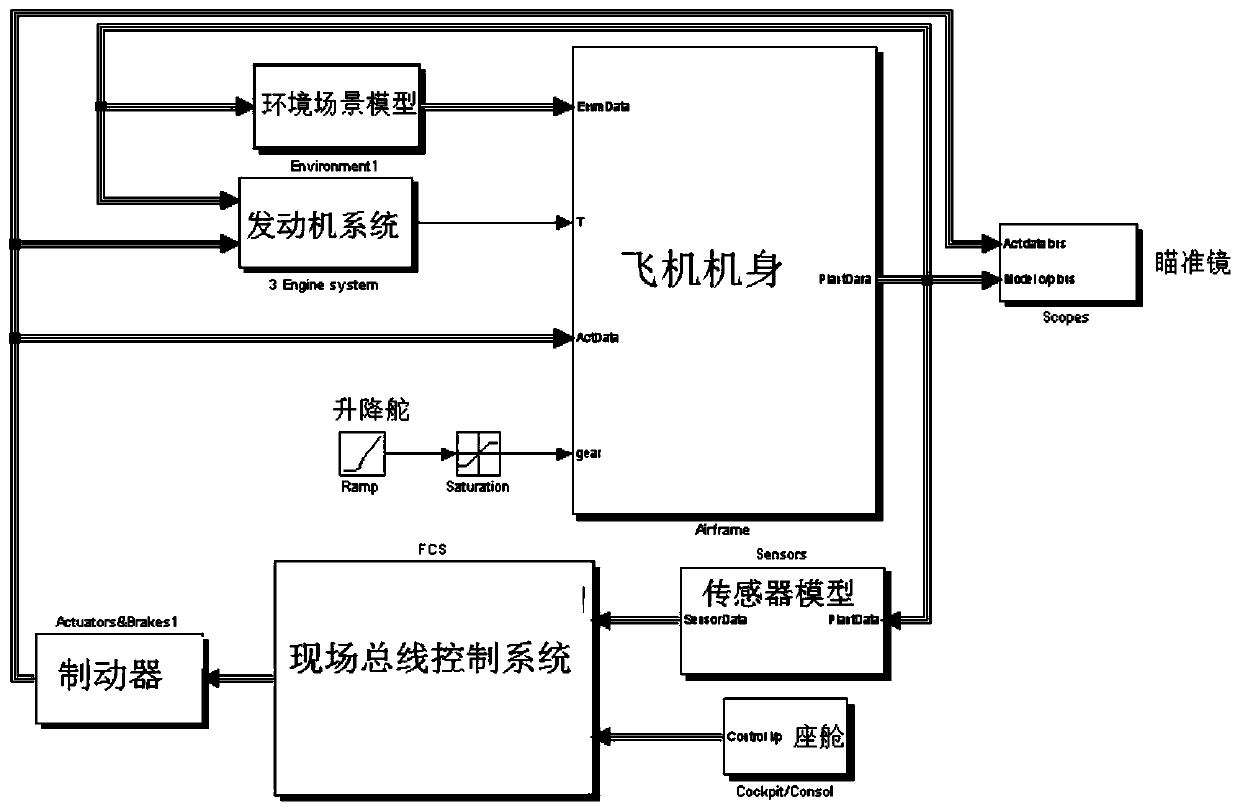
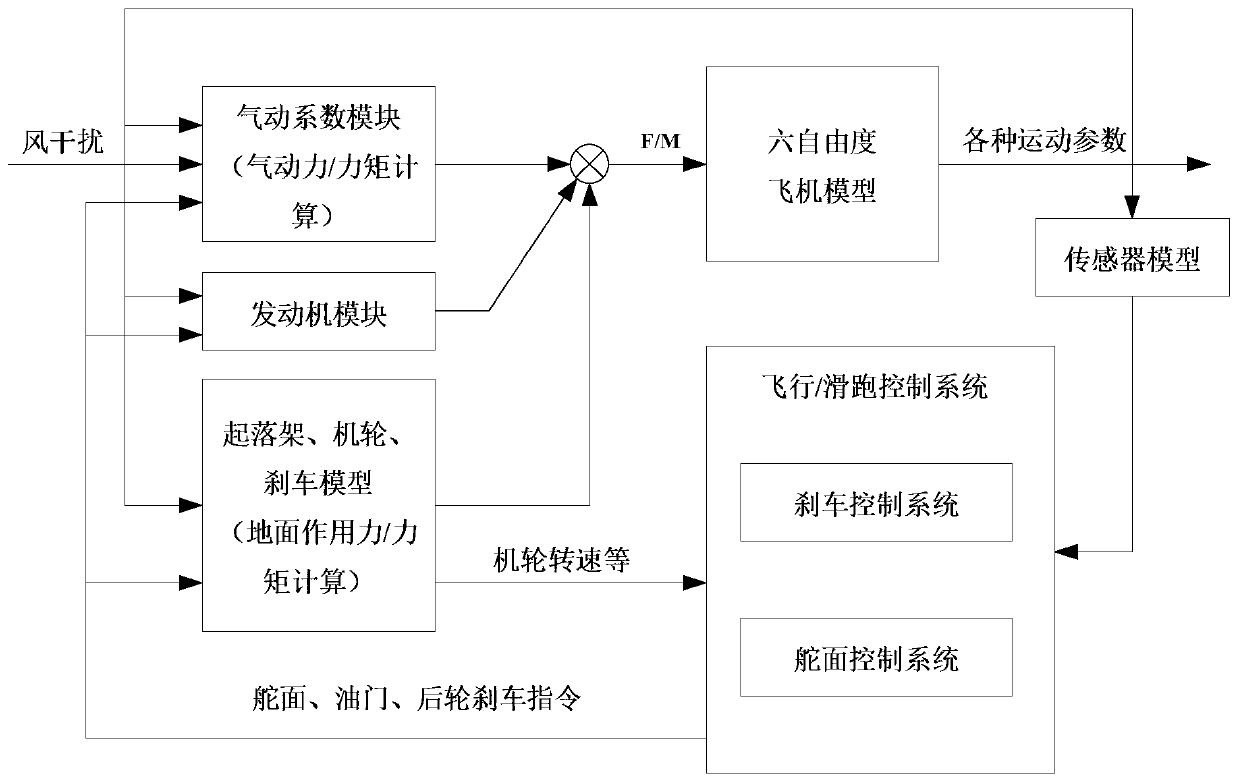
The invention discloses an unmanned aerial vehicle UAV control law parameter adjusting method, and aims at providing a parameter adjusting method which is large in parameter adjusting freedom degree,capable of effectively improving system design efficiency and capable of saving cost. According to the technical scheme, the method comprises the steps that a Matlab is used as a tool, and a general control console, a pneumatic coefficient module, an engine module, an undercarriage, airplane wheels, a brake model, a pitch angle local controller at the balance point of the unmanned aerial vehicle,a six-degree-of-freedom airplane model and a general module library of a sensor model for building the control law of the unmanned aerial vehicle are generated; a field bus control system FCS selectsa set control mode to calculate a control law, an accelerator position instruction and a rudder deviation instruction according to a control instruction given by the general console, ,,sends the flight state parameters of the unmanned aerial vehicle, and directly fits the obtained controller parameters at the characteristic points to obtain a function of the controller parameters about the heightH and the Mach number M and a parameter adjustment control law of a continuous change law of the controller parameters along with the parameter variables in the whole situation.
Owner:CHENGDU AIRCRAFT INDUSTRY GROUP
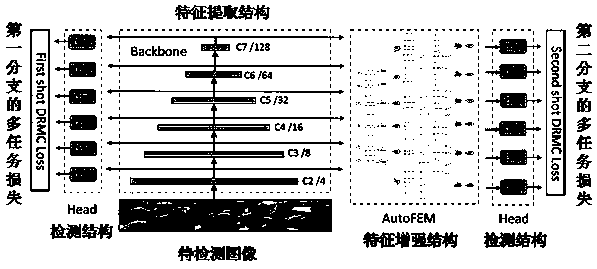
Face detection and image detection neural network training method, device and equipment
ActiveCN111291739AImprove accuracyAvoid huge workloadCharacter and pattern recognitionNeural learning methodsFace detectionFeature extraction
The invention relates to a face detection and image detection neural network training method, device and equipment. The face detection method comprises the steps of obtaining a to-be-detected image; calling a face detection network to process the to-be-detected image to obtain an original feature map extracted by a feature extraction structure in the face detection network; wherein there are morethan one original feature map and the resolutions are different; processing the original feature maps through a feature enhancement structure of the face detection network to obtain enhanced feature maps corresponding to the original feature maps; wherein based on the detection purpose of the face detection network and the processing object of the feature enhancement structure, a search space usedfor searching the feature enhancement structure is determined; wherein the feature enhancement structure is searched from a search space; and obtaining a face detection result of the to-be-detected image according to the enhanced feature map through a detection structure of the face detection network. According to the scheme provided by the invention, the face detection precision can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
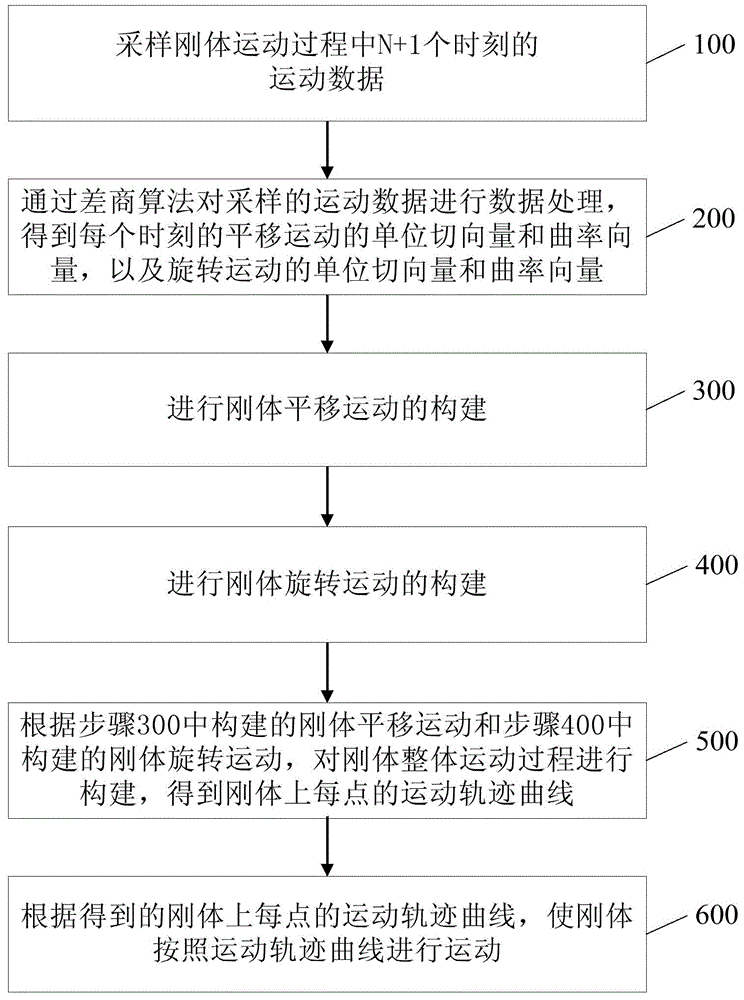
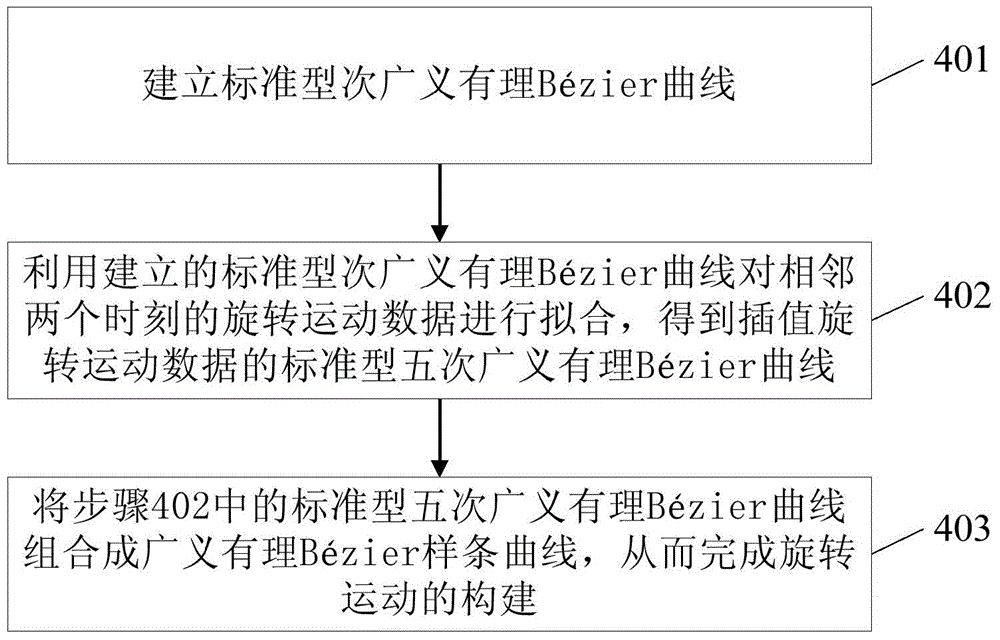
Rigid body motion realization method
InactiveCN104867172AAvoid huge workloadAvoiding Geometric DistortionsAnimationObject motionAnimation
The invention relates to the field of three-dimensional animation design, and provides a rigid body motion realization method comprising the steps that step 100, motion data of N+1 moments in the rigid body motion process are acquired; step 200, data processing is performed on the sampled motion data via a difference quotient algorithm so that a unit tangent vector and a curvature vector of translational motion of each moment are obtained and the unit tangent vector and the curvature vector of rotary motion are also obtained; step 300, construction of rigid body translational motion is performed; step 400, construction of rigid body rotary motion is performed; step 500, the whole motion process of a rigid body is constructed according to the rigid body translational motion constructed in the step 300 and the rigid body rotary motion constructed in the step 400 so that a motion track curve of each point on the rigid body is obtained; and step 600, the rigid body is enabled to move according to the motion track curve according to the obtained motion tract curve of each point on the rigid body. The rigid body motion is closer to the real object motion scene in real life so that interactivity of the design is enhanced.
Owner:DALIAN UNIV OF TECH
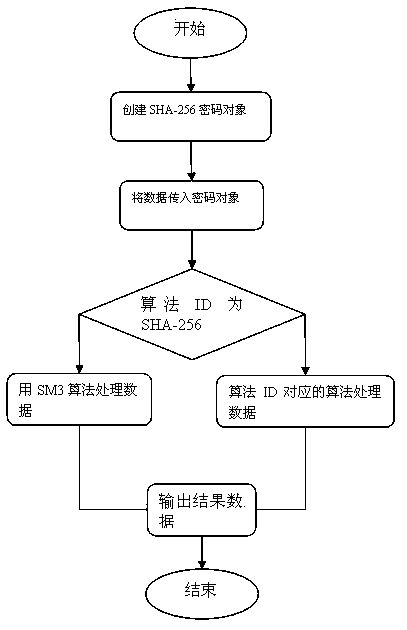
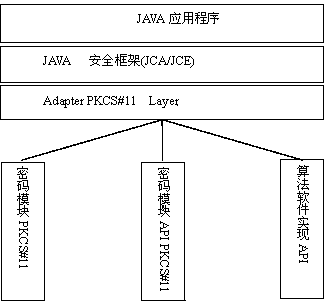
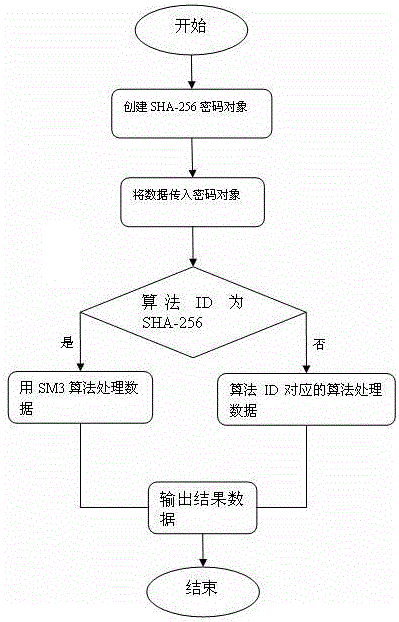
Implementation method and system for SM3 algorithm in JAVA environment
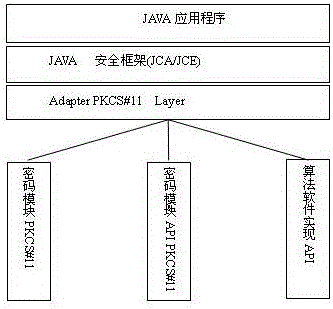
ActiveCN103425939AAvoid huge workloadAvoid red tapeUser identity/authority verificationDigital data protectionApplication programming interfaceCryptogram
The invention relates to the technical field of cryptogram and information safety, and discloses an implementation method and system for an SM3 algorithm in a JAVA environment. The implementation method specifically comprises the following steps that an adaptation layer for achieving algorithm replacement is developed based on a PKCS#11 standard; in the JAVA environment, when an application program calls a secure hash algorithm (SHA()-256 algorithm) in JAVA cryptography extension (JCE) through a programming interface of an encryption framework JCA standard, the adaptation layer directly calls the SM3 algorithm to achieve an application programming interface (API), operations and processing are carried out on data on which a hash algorithm needing to be carried out in a sublayer based on the SM3 algorithm, and thus the operation that the SHA-256 algorithm is replaced by the SM3 algorithm is achieved. The invention further discloses an implementation system for the SM3 algorithm in the JAVA environment. The algorithm ID of the SHA-256 algorithm is used for achieving the SM3 algorithm in the encryption framework JCA, the problem that a new algorithm cannot be added in the implementation of ready-made JCE is solved, and meanwhile the huge amount of workload for achieving new JCE and complex procedures for applying JCE authorized signatures are avoided.
Owner:中电科网络安全科技股份有限公司
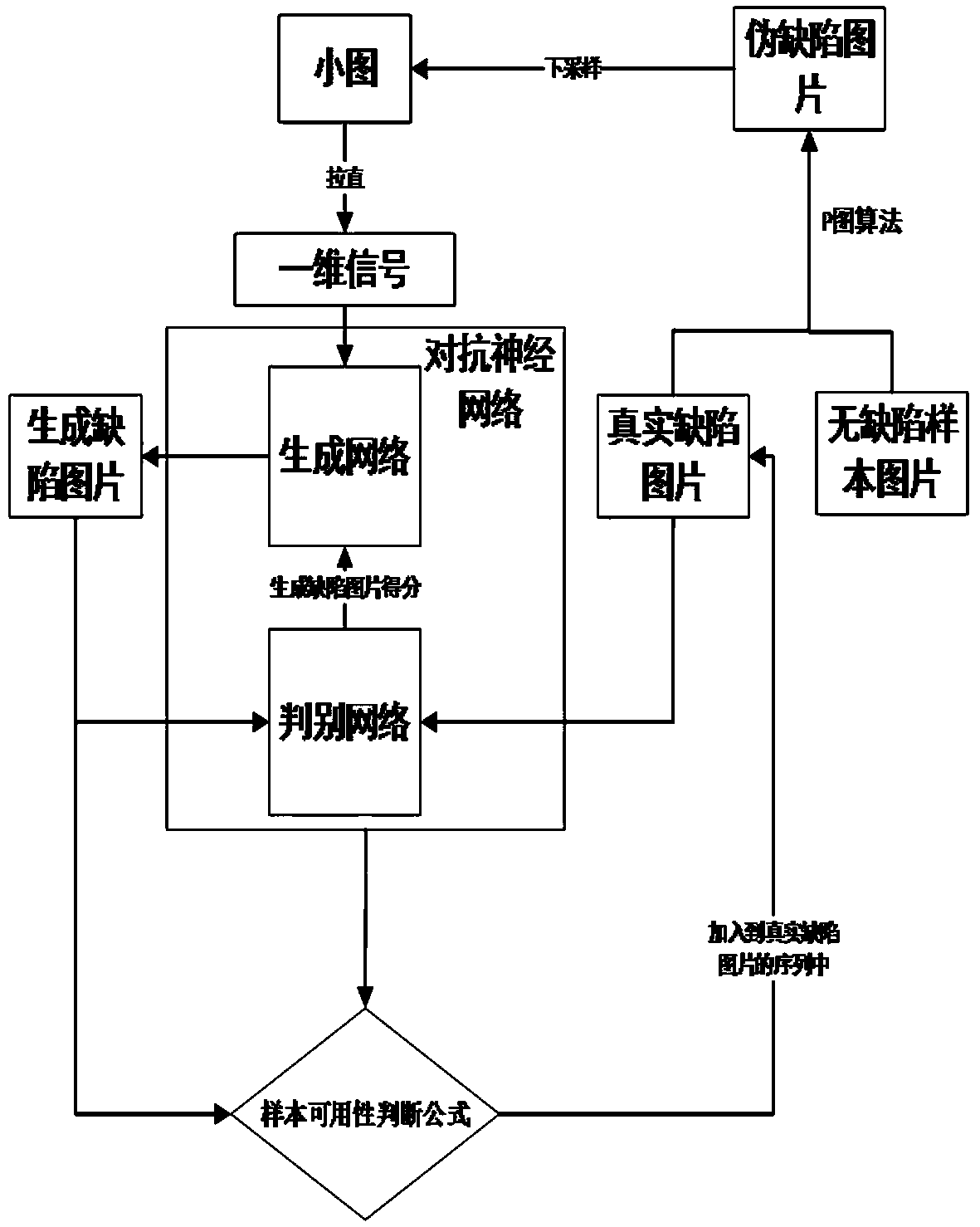
Deep learning-based sample generation method in industrial vision detection
ActiveCN110853035ALow similarityAvoid huge workloadImage enhancementImage analysisAlgorithmEngineering
The invention relates to a deep learning-based sample generation method in industrial vision detection, which aims to solve the problems of few existing vision detection samples, long sample trainingtime and high similarity among the samples, and comprises the following steps of: a) extracting defects in a real defect picture; b) fusing the extracted defect with a defect-free picture so as to generate a pseudo defect picture; c) processing the pseudo defect picture and sending the processed pseudo defect picture to a generation network in the adversarial neural network to generate a defect picture; d) continuing to generate a pseudo defect picture according to the step b), and then iteratively training the network repeatedly according to the step c); and e) when the training in the step d) meets the requirements, adding the generated defect pictures into the sequence of the real defect pictures, and continuing iterative training. Finite samples can be utilized to generate a large number of samples meeting the requirements, the training time is shortened, and meanwhile, the similarity among the samples is low.
Owner:BEIJING FOCUSIGHT TECH
Artificial crossing breeding method of water lilies
The invention discloses an artificial crossing breeding method of water lilies. The artificial crossing breeding method of the water lilies, provided by the invention, comprises the following steps: (1) collecting pollen; (2) collecting stigma mucus; (3) germinating the pollen in the stigma mucus; (4) selecting crossing parents; (5) artificially pollinating. According to the artificial crossing breeding method of the water lilies, provided by the invention, the characteristics that the amount of the stigma mucus is great and the stigma mucus can be separated are utilized, and suitable parentsare screened through the culture of the pollen in the stigma mucus at the early period so that the huge amount of work for blindly crossing and pollinating can be avoided; the flowering phase of the water lilies is long and a phenomenon that the flowering phases of male and female parents do not meet is avoided; the male parents are bagged in the field and the pollen is collected on site in a crossing process, so that the problem that the vitality of the pollen is reduced, caused by pollen storage, is avoided. The artificial crossing breeding method of the water lilies, provided by the invention, has important meanings of alleviating the labor intensity of breeding, improving the working efficiency of breeding and accelerating a water lily new variety breeding progress.
Owner:QINGDAO AGRI UNIV
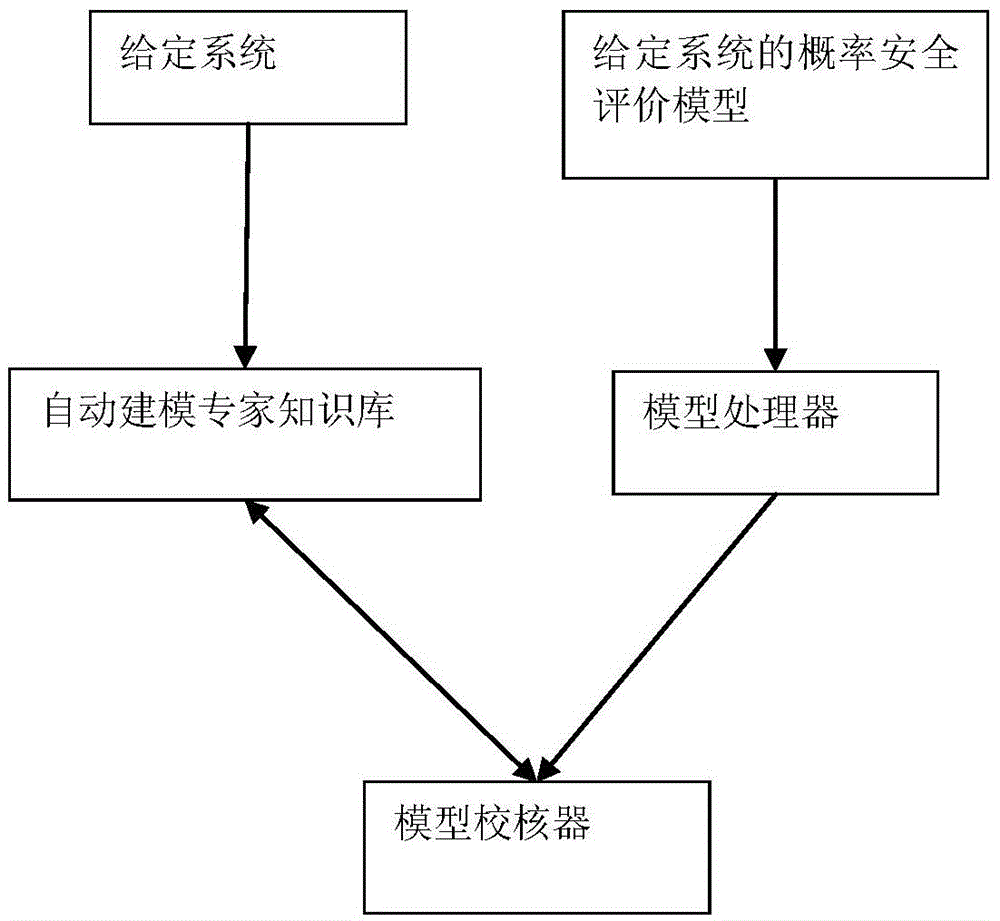
Universal probabilistic safety assessment model conversion system
InactiveCN105678055AAutomatic and efficient identificationAutomatic and efficient processingInformaticsSpecial data processing applicationsDecompositionComputer science
The invention discloses a universal probabilistic safety assessment model conversion system. With respect to the universal probabilistic safety assessment model conversion system, general probabilistic safety assessment automatic modeling methods and rules are combined with decomposition processing of a rich text probabilistic safety assessment model, computer-assisted modeling of the probabilistic safety assessment model can be carried out to a system including common cause failures. The universal probabilistic safety assessment model conversion system mainly comprises three modules: a model processor analyzes and processes the probabilistic safety assessment mode of a given system, model information of the given system is converted and decomposed into a standard model unit; an automatic modeling expert knowledge base stores construction rules of a universal system probabilistic safety assessment model, design and flow information of the given system, and specific probabilistic safety assessment model check rules of the given system and input by the user; and a model checking device analyzes, checks and arranges the standard model unit, changes the error of the standard model unit, and supplements missing probabilistic safety assessment model information, and a perfect system probabilistic safety assessment model is obtained.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
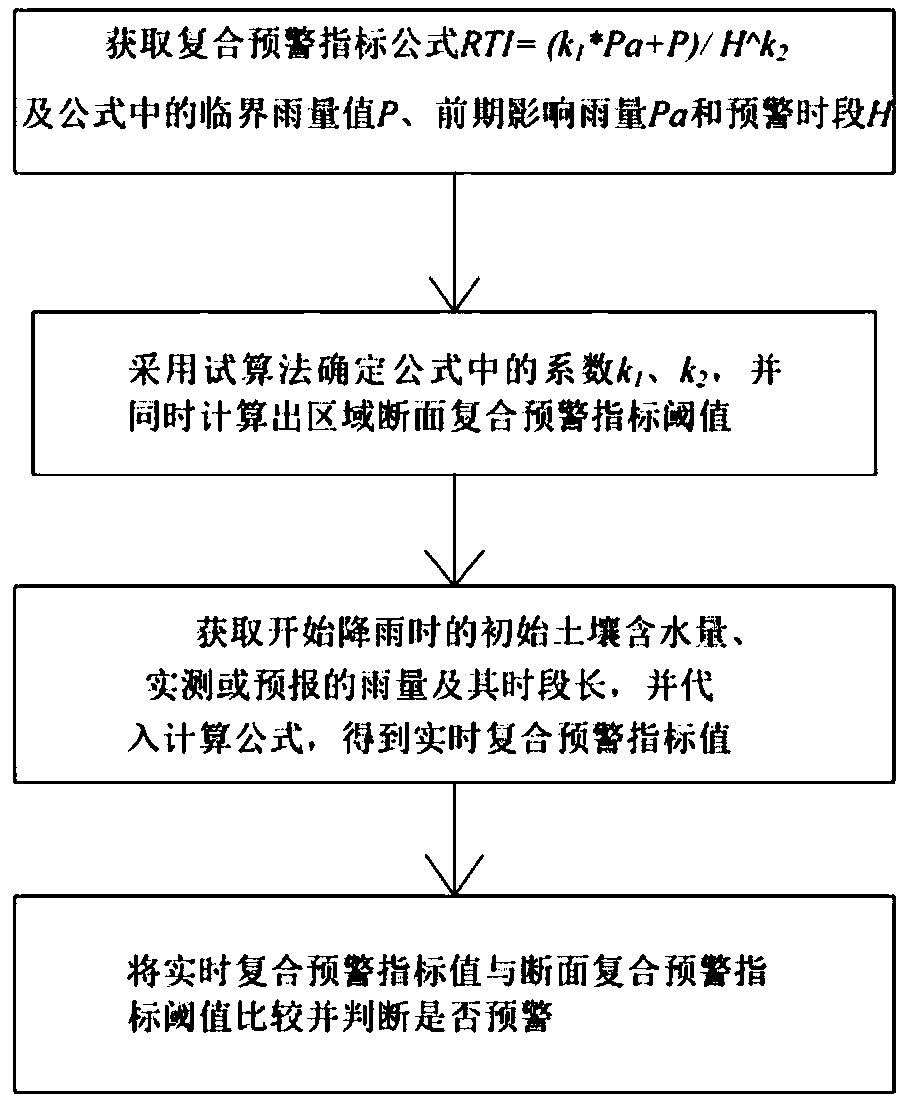
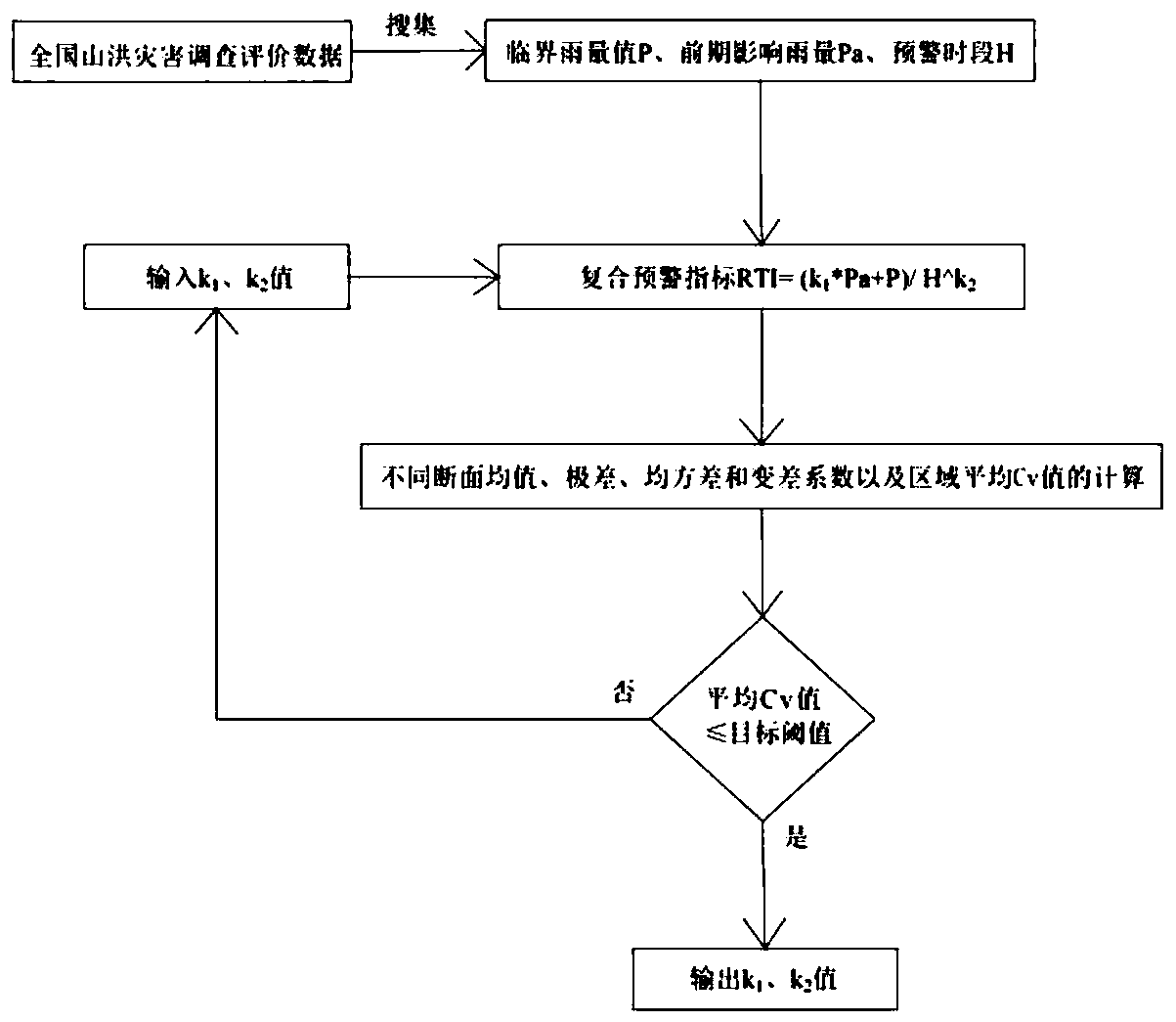
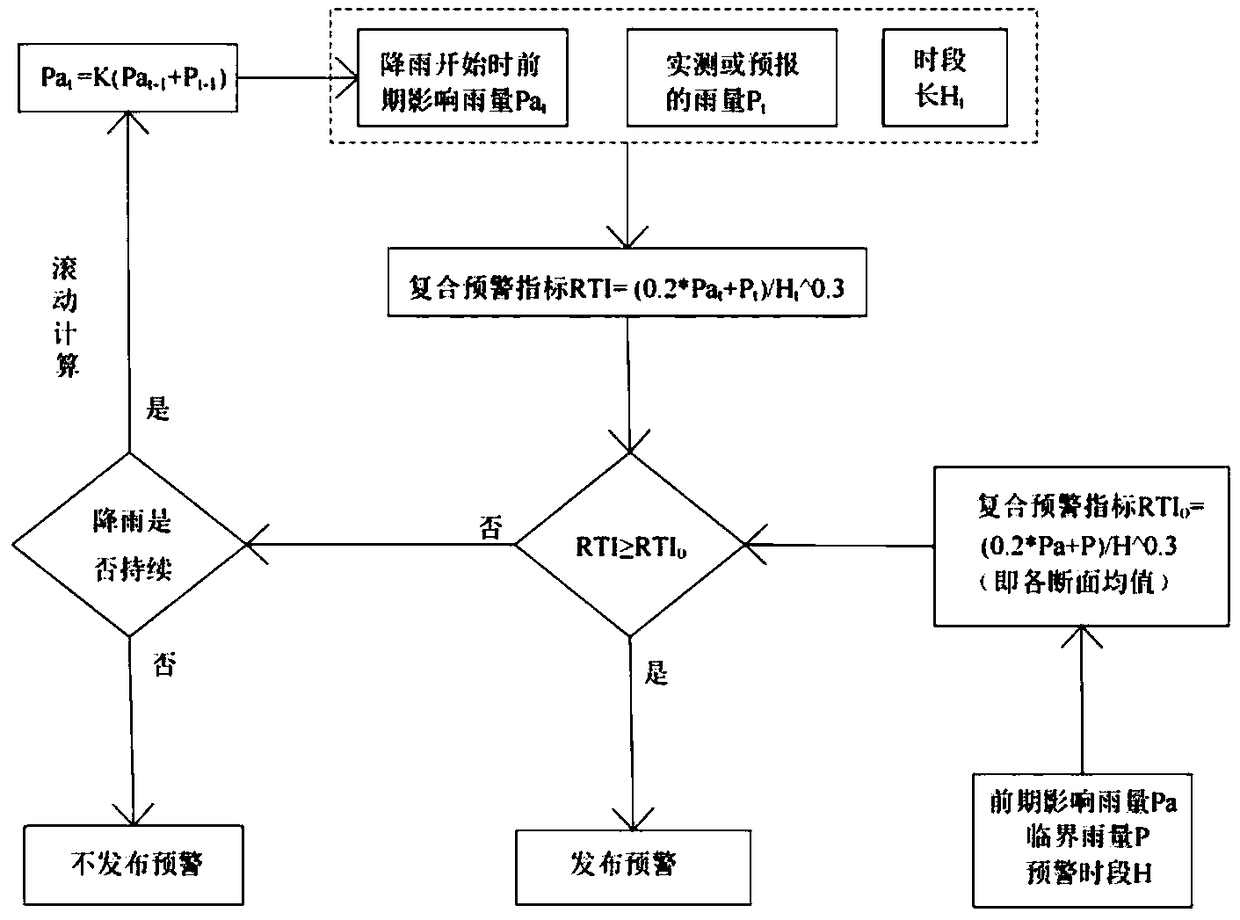
Method and device for calculating composite early warning index based on critical rainfall and early warning method
The invention discloses a method an device for calculating a composite early warning index based on critical rainfall and an early warning method. A calculation formula RTI=(K1*Pa+P) / H^K2 of the composite early warning index RTI is obtained, K1 and K2 represent coefficients respectively, Pa represents the early-stage influence rainfall, H represents an early warning period, and P represents a critical rainfall in the situation of combination between early-stage influence rainfall and the early warning period; values of the coefficients K1 and K2 are obtained; the initial soil water content during start of rain, actually measured or forecast rainfall and time length of the rainfall are obtained and substituted into the above calculation formula RTI=(K1*Pa+P) / H^K2, and a real-time compositeearly warning index value is obtained; and the real-time composite early warning index value is compared with a sectional composite early warning index threshold, and corresponding operation is carried out according to the comparison result. Existing information before is used fully, the early warning value in a random period can be calculated easily, and a new effective method is provided for early warning against a mountain torrent disaster.
Owner:HOHAI UNIV
Automobile bumper full-aspect paint spraying workbench
InactiveCN108940661AAvoid the problem of uneven sprayingAvoid huge workloadSpraying apparatusEngineeringNozzle
The invention relates to an automobile bumper full-aspect paint spraying workbench, and belongs to the technical field of nozzle configuration or installation. The workbench comprises a working table,wherein a transmission mechanism and a paint spraying device are arranged on the working table; the transmission mechanism comprises a first conveying belt, a first conveying chain, a second conveying belt, a second conveying chain and a third conveying belt, wherein the first conveying belt, the second conveying belt and the third conveying belt are horizontally placed, the first conveying chainand the second conveying chain are vertically placed, the first conveying chain is arranged between the first conveying belt and the second conveying belt, and the second conveying chain is arrangedbetween the second conveying belt and the third conveying belt; and the paint spraying device comprises a first spray gun, a second spray gun, a third spray gun, a fourth spray gun, and the first spray gun, the second spray gun, the third spray gun and the fourth spray gun are arranged right above the first conveying belt, the first conveying chain, the second conveying belt and the second conveying chain respectively. According to the technical scheme, the problem that automobile bumpers cannot be painted in batches in the prior art is solved, and the practicability is high.
Owner:宁波高新区意川汽车零部件有限公司
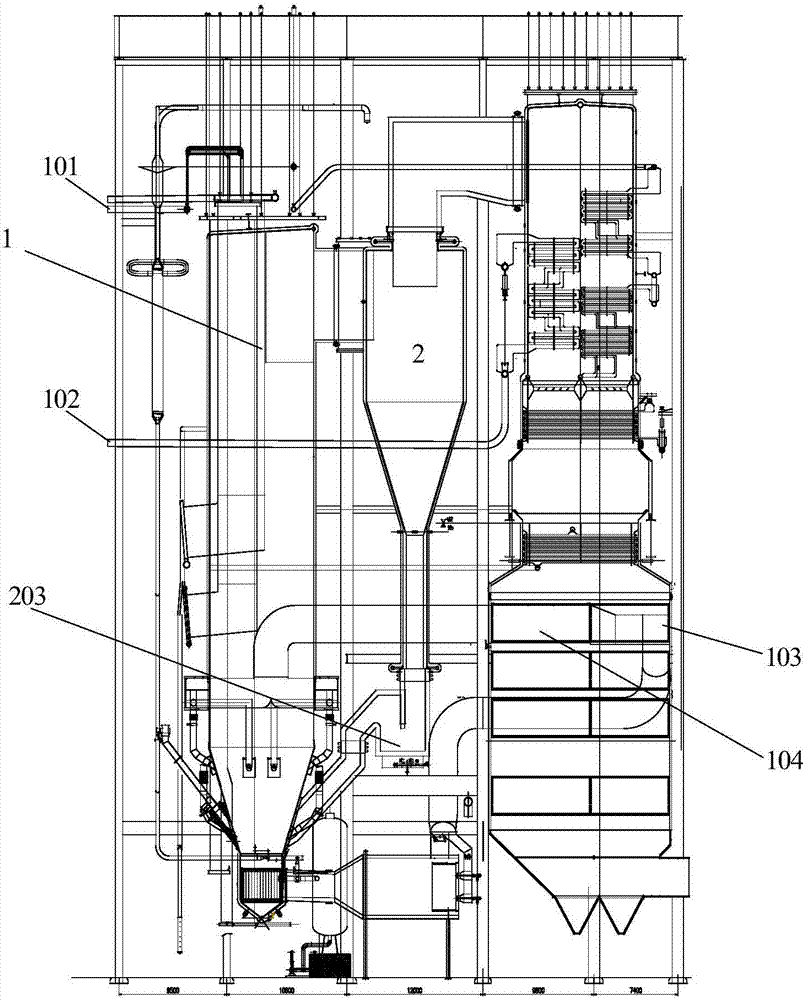
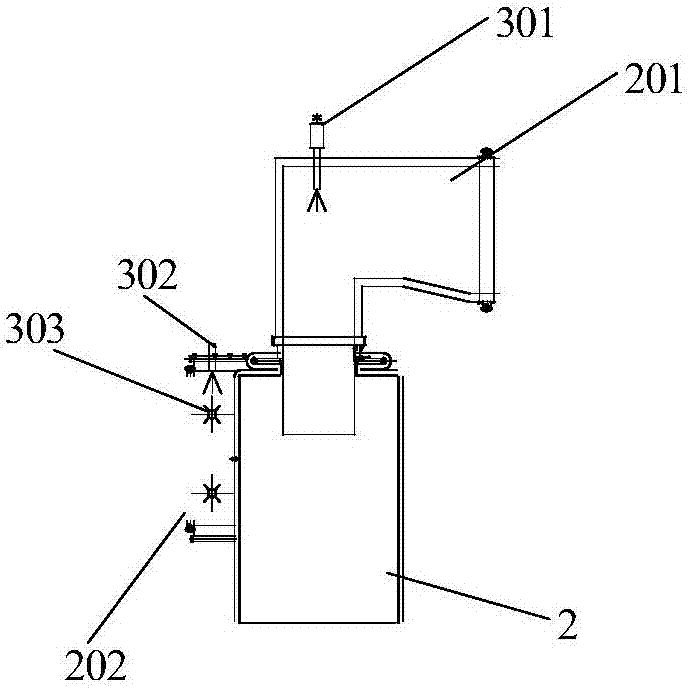
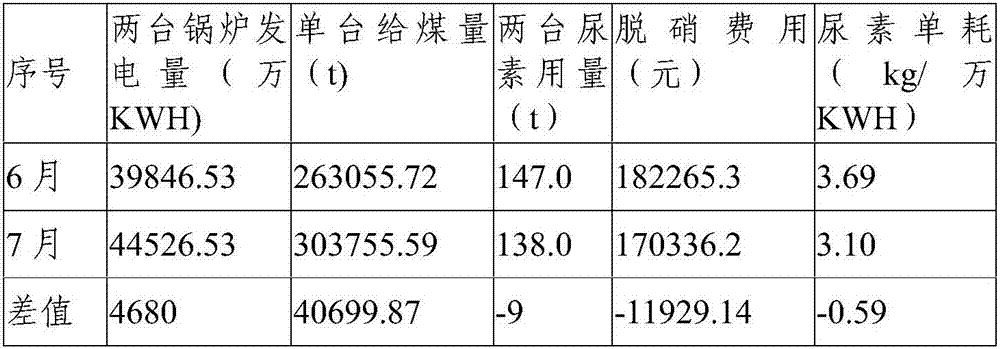
Fluidized bed boiler denitration device and method based on cyclone separators
PendingCN107166376AIncrease profitBest Response PortfolioFluidized bed combustionGas treatmentCycloneFlue gas
The invention provides a fluidized bed boiler denitration device based on cyclone separators. The cyclone separators are connected to a hearth outlet flue of a fluidized bed boiler. Ammonia guns are arranged on outlet flues of the cyclone separators, and jet orifices of the ammonia guns of the outlet flues are downward. The invention further provides a fluidized bed boiler denitration method. According to the fluidized bed boiler denitration device provided by the invention, the flue gas temperature at the outlet flues of the cyclone separators is located between the optimum temperatures of denitration agent and NOx reaction; denitration reaction can be better conducted; the utilization rate of denitration agents is increased; a shut-off valve is installed on each newly-added pipeline to be matched with an original pipeline; and operation of the ammonia guns in the different positions can be switched at any moment under the different working conditions of the boiler, so that the optimum reaction combination is sought.
Owner:ORDOS JUNZHENG ENERGY CHEM
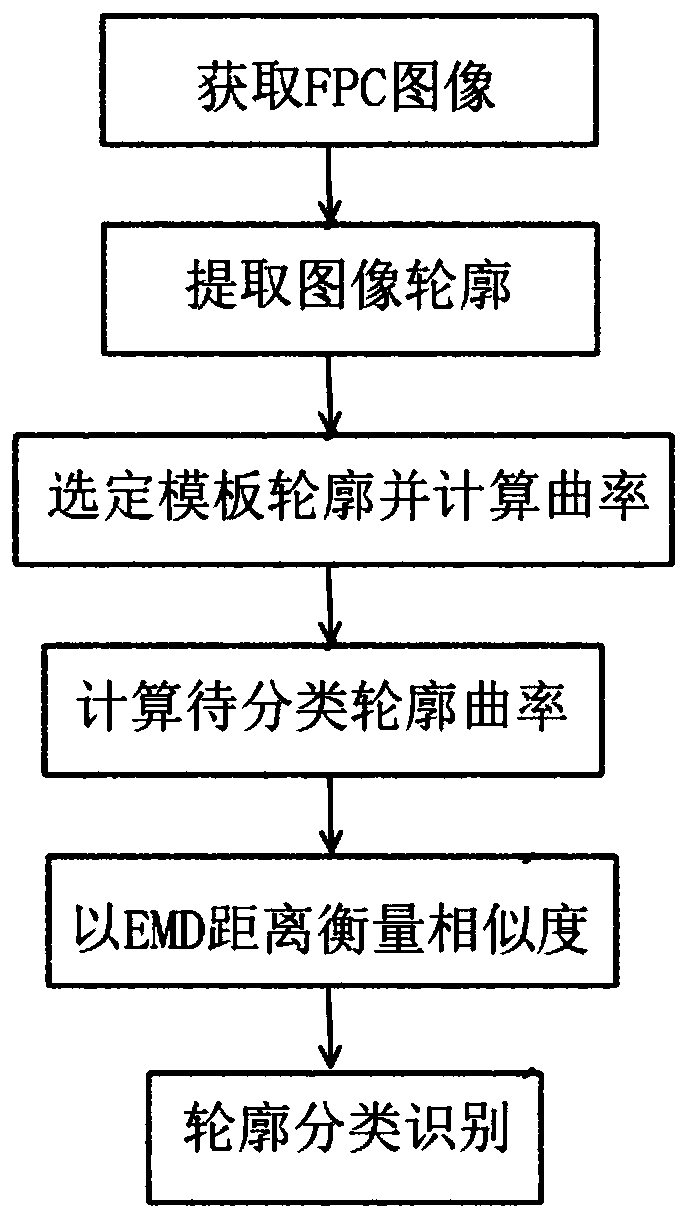
Flexible circuit board image area identification method based on differential geometry
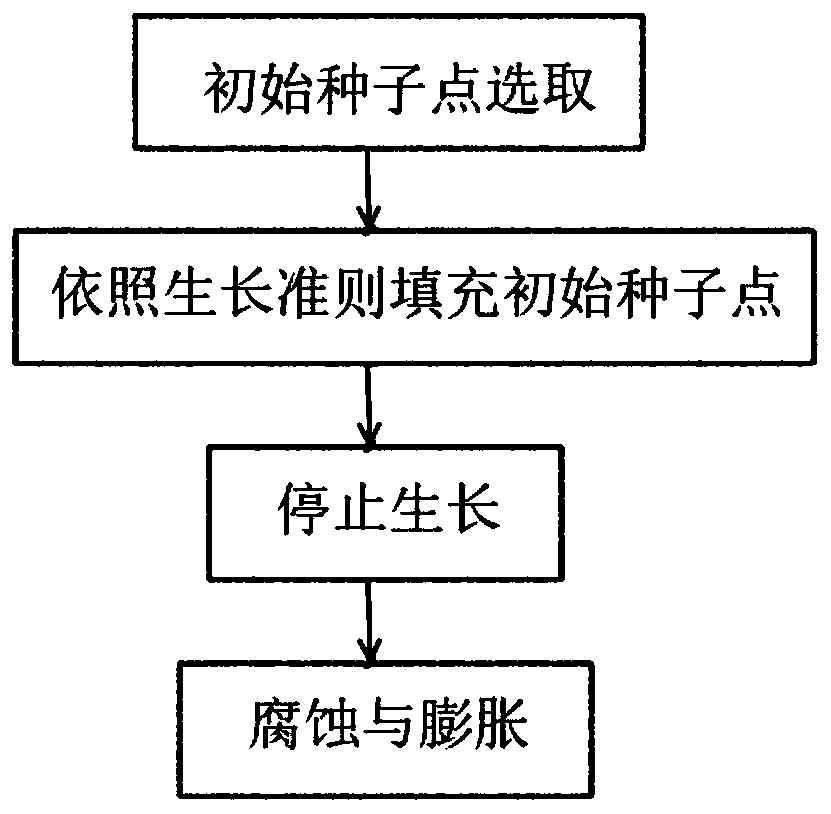
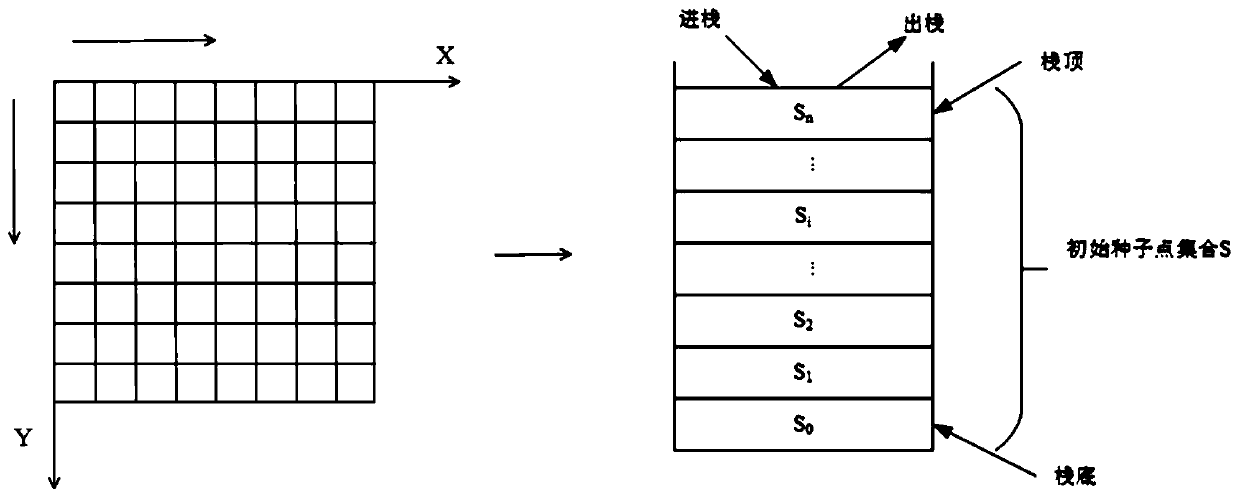
ActiveCN110544235APure profileEasy to operateImage enhancementImage analysisEngineeringRegion growing
The invention discloses a flexible circuit board image area identification method based on differential geometry. The flexible circuit board image area identification method comprises the following steps: S1, collecting an FPC surface image as a to-be-classified image; S2, extracting the contour of the to-be-classified image based on a region growing method of adaptively selecting an initial seedpoint; S3, selecting a standard template contour, calculating the curvature of the standard template contour, and converting the curvature into a histogram; S4, calculating the discrete curvature of the contour of the to-be-classified image, and converting the discrete curvature into a histogram with the same group distance as the contour of the standard template; S5, evaluating the similarity between the contour of the to-be-classified image and the contour of the standard template by adopting an EMD distance; and S6 identification profile. According to the invention, the requirement of defect detection on a single FPC component in actual detection is met.
Owner:SOUTH CHINA UNIV OF TECH
Glass covered wire insulating layer stripping device and method
ActiveCN105790170AAvoid huge workloadAddress health impactsApparatus for removing/armouring cablesGlass coverEngineering
The invention discloses a glass covered wire insulating layer stripping device and a glass covered wire insulating layer stripping method. The device comprises a dust containing device, wherein first through holes penetrating through two end faces of the dust containing device are formed in the dust containing device; one end of the dust containing device is internally connected with a transmission mechanism and the other end of the dust containing device is externally connected with an annular middle fixed part; the annular middle fixed part is provided with a groove penetrating through a first surface of the annular middle fixed part, and a second through hole penetrating through a second surface of the annular middle fixed part; the groove and the second through hole are coaxially arranged; the second through hole is overlapped with the first through holes; the groove is internally and fixedly provided with a tooth milling tool; the tooth milling tool is provided with three third through holes which penetrate through two relative surfaces of the tooth milling tool and are communicated with one another; and a crescent tool edge is arranged at the engaged part of the two third through holes, and the third through holes are communicated with the second through holes. With the adoption of the glass covered wire insulating layer stripping device, automatic stripping of glass covered wire insulating layers can be carried out by manually controlling the transmission mechanism so that the working efficiency is improved, and the problem that the health of human bodies is influenced by splashed dust is solved.
Owner:WUHAN NARI LIABILITY OF STATE GRID ELECTRIC POWER RES INST
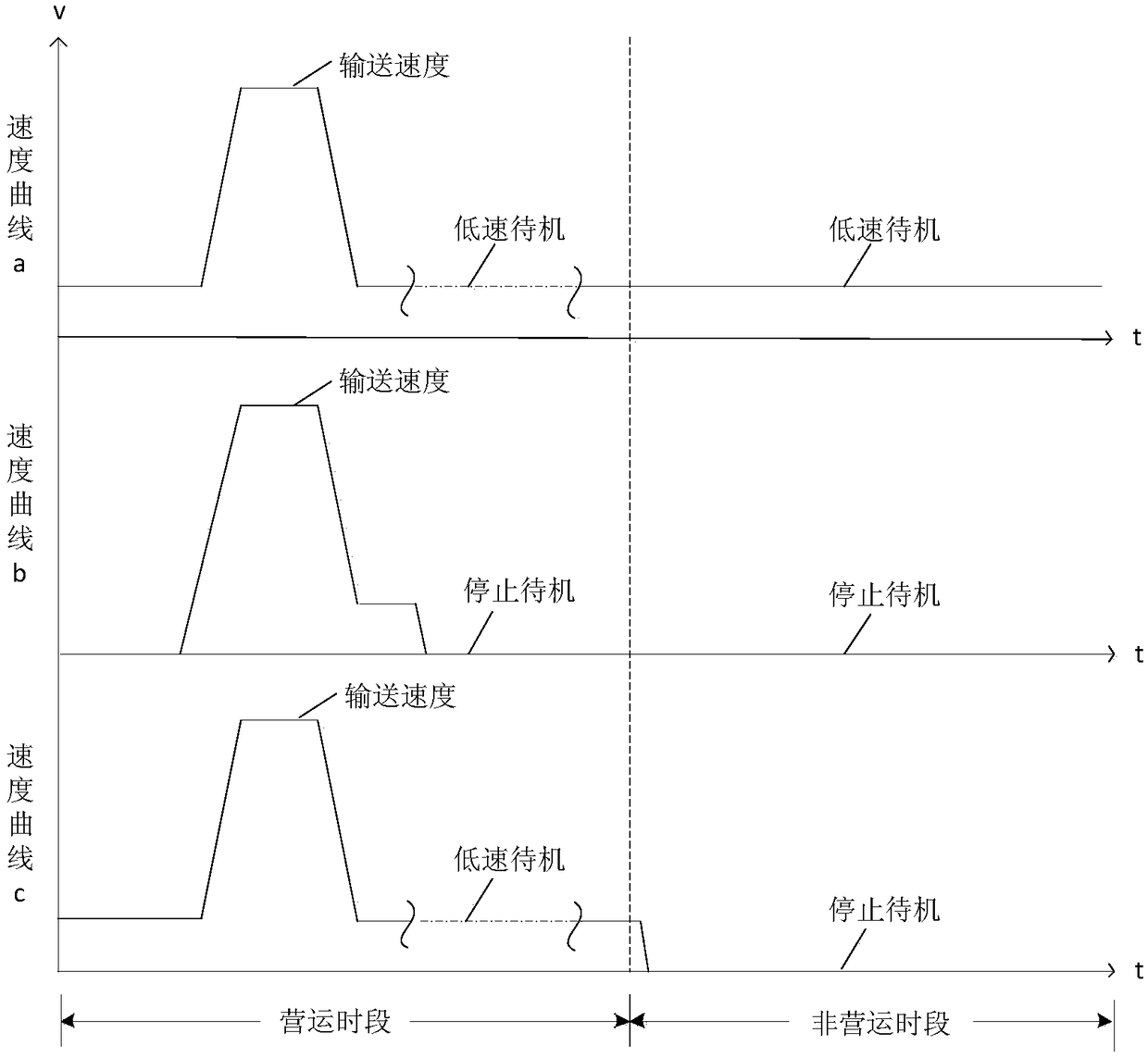
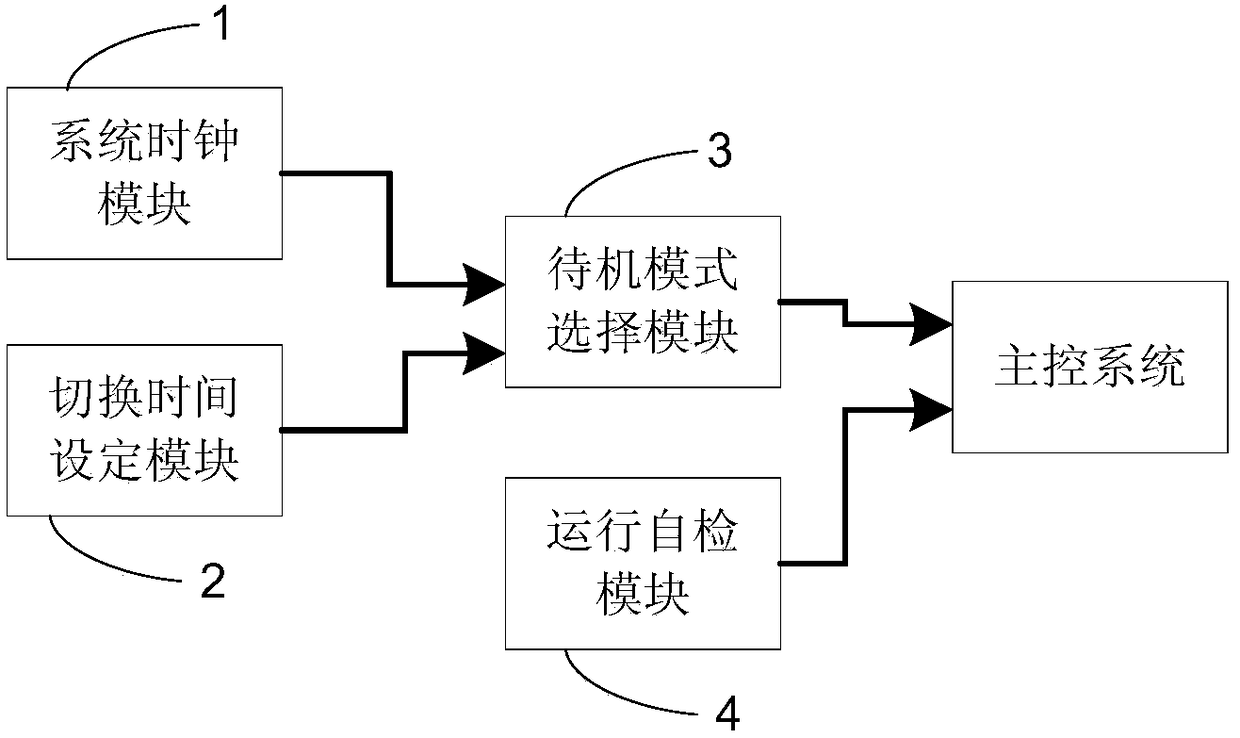
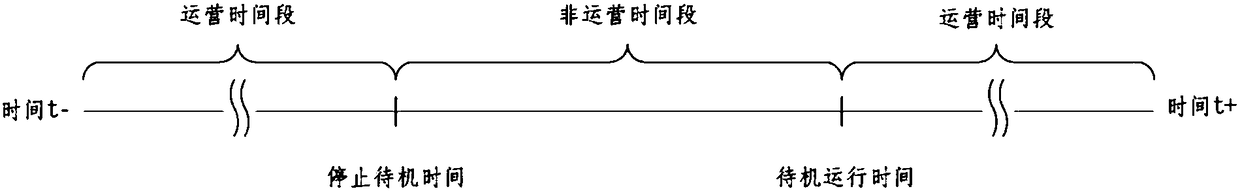
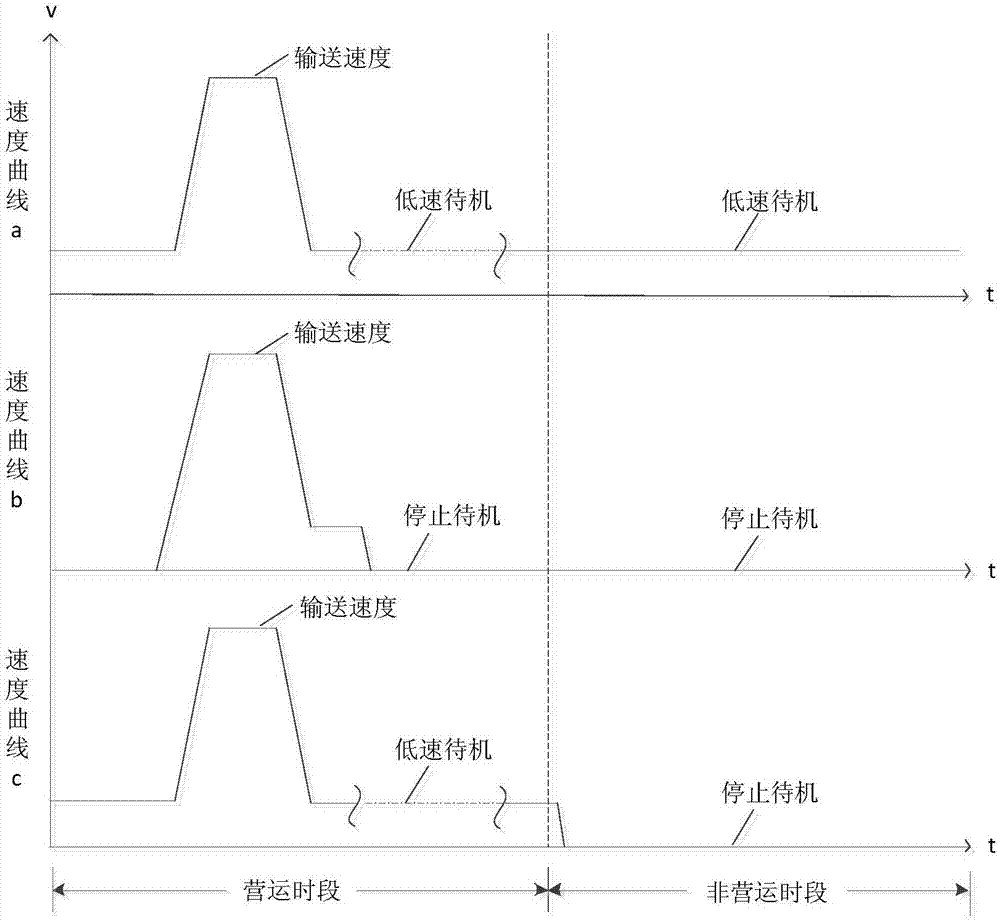
Passenger delivery system standby mode control device
ActiveCN108147266AImprove service qualityGood energy saving effectSustainable buildingsEscalatorsQuality of serviceMode control
Owner:SHANGHAI MITSUBISHI ELEVATOR CO LTD
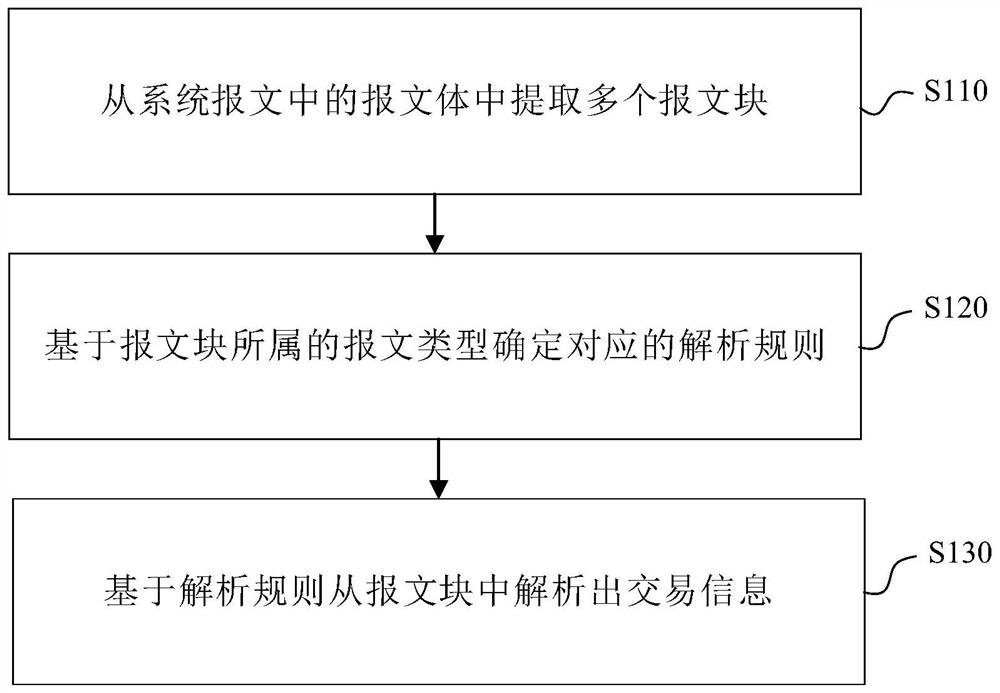
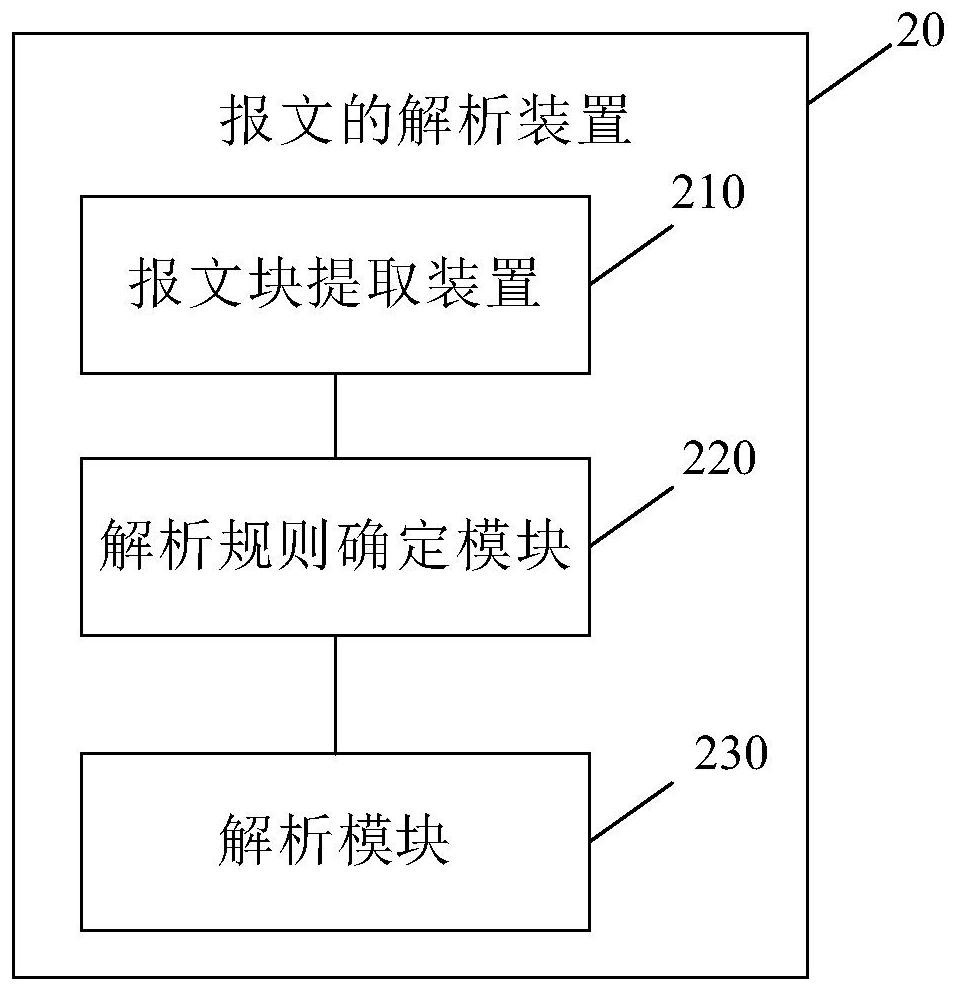
Message analysis method and device, electronic equipment and computer readable storage medium
The embodiment of the invention provides a message analysis method and device, electronic equipment and a computer readable storage medium. The method comprises the following steps: extracting a plurality of message blocks from a message body in a system message; determining a corresponding analysis rule based on the message type to which the message block belongs; and analyzing the transaction information from the message block based on the analysis rule. Based on the scheme, message analysis of different application systems can be realized, the application range is wide, and huge workload caused by writing an analysis program can be avoided.
Owner:CCB FINTECH CO LTD
A digital detection method and system for surface assembly quality of aircraft fuselage
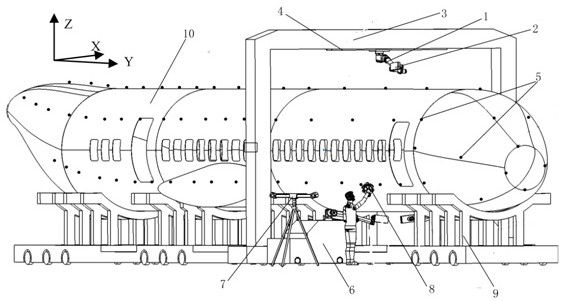
ActiveCN113335557BGuaranteed assembly qualityReduce workloadAircraft assemblyAircraft components testingEngineeringManipulator
The invention belongs to the technical field of aircraft assembly measurement, and in particular relates to a method and a system for digital detection of the surface assembly quality of an aircraft fuselage. This technical solution is based on digital inspection tools such as surface quality detector I, tracking three-dimensional scanning unit, etc., combined with motion positioning equipment such as measuring manipulator I, to realize digital inspection of the surface assembly quality of the aircraft fuselage, including the amount of concave and convex of the nail head of the connector, the thickness of the The skin to seam step gap has high measurement accuracy and good measurement accessibility, and can project the detection results to the corresponding detection area, ensuring the traceability of the aircraft surface assembly quality.
Owner:CHENGDU AIRCRAFT INDUSTRY GROUP
A method for collecting and preserving dormant eggs of black pearl killifish
ActiveCN108522372BAddress adverse effects of preservationAvoid huge workloadClimate change adaptationPisciculture and aquariaCynolebiasKillifish
The invention relates to a collection and storage method for fish eggs, and discloses a collection and storage method for dormant eggs of cynolebias nigripinnis. The method comprises the following steps: (1) egg collection; (2) washing; (3) previewing; (4) soaking; (5) packaging; (6) storage of dormant eggs. By preparing a special egg-laying medium, the invention designs a corresponding filter screen, consequently, great workload caused by the work of egg selection in the traditional reproduction method is solved, and manpower is saved by 90 percent or more; moreover, an egg-carrying materialis utilized to solve the adverse influence caused by peat soil storage in the traditional reproduction method, and thereby technical support is provided for the large-scale reproduction of the aquarium fish.
Owner:ZHEJIANG NORMAL UNIVERSITY
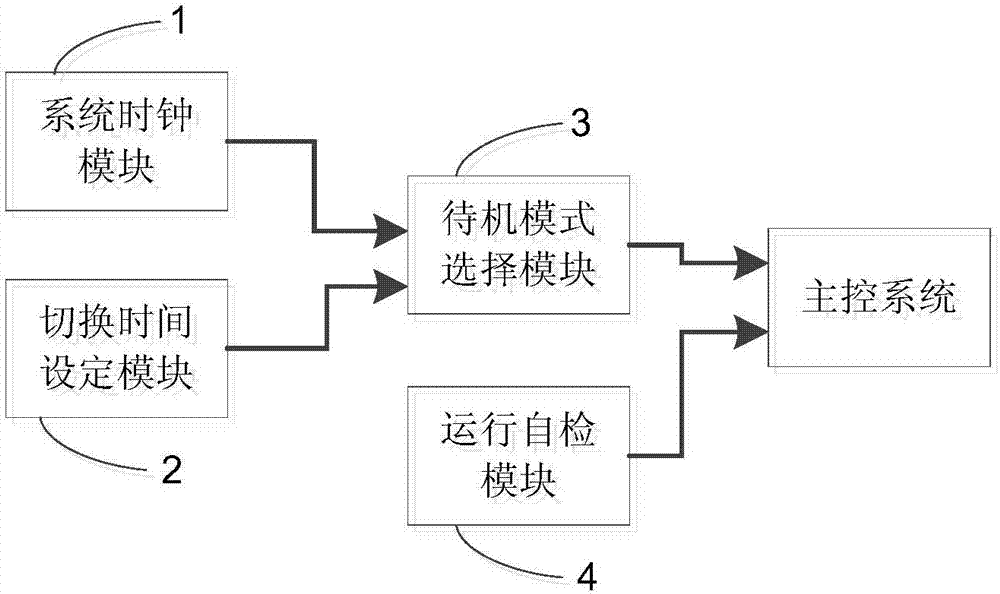
Standby mode control device for passenger transporting system
InactiveCN107285178AImprove service qualityGood energy saving effectSustainable buildingsEscalatorsQuality of serviceLow speed
The invention discloses a standby mode control device for a passenger transporting system. A system clock module is used for carrying out timing on time of a current system; a switching time setting module is used for setting low-speed standby switching time and stopping standby switching time; a standby mode selection module is used for switching a standby mode of the passenger transporting system to a stopping standby mode if the time of the current system reaches the stopping standby switching time, and switching the standby mode of the passenger transporting system to a low-speed standby mode if the time of the current system reaches the low-speed standby switching time. The standby mode control device for the passenger transporting system, disclosed by the invention, has the effects of saving energy within a non-operation time period and improving the passenger service quality within an operation time period; and the working amount can be reduced and the high equipment cost is reduced.
Owner:SHANGHAI MITSUBISHI ELEVATOR CO LTD
A method and system for realizing sm3 algorithm in java environment
ActiveCN103425939BAvoid huge workloadAvoid red tapeUser identity/authority verificationDigital data protectionApplication programming interfaceWorkload
The invention relates to the technical field of cryptogram and information safety, and discloses an implementation method and system for an SM3 algorithm in a JAVA environment. The implementation method specifically comprises the following steps that an adaptation layer for achieving algorithm replacement is developed based on a PKCS#11 standard; in the JAVA environment, when an application program calls a secure hash algorithm (SHA()-256 algorithm) in JAVA cryptography extension (JCE) through a programming interface of an encryption framework JCA standard, the adaptation layer directly calls the SM3 algorithm to achieve an application programming interface (API), operations and processing are carried out on data on which a hash algorithm needing to be carried out in a sublayer based on the SM3 algorithm, and thus the operation that the SHA-256 algorithm is replaced by the SM3 algorithm is achieved. The invention further discloses an implementation system for the SM3 algorithm in the JAVA environment. The algorithm ID of the SHA-256 algorithm is used for achieving the SM3 algorithm in the encryption framework JCA, the problem that a new algorithm cannot be added in the implementation of ready-made JCE is solved, and meanwhile the huge amount of workload for achieving new JCE and complex procedures for applying JCE authorized signatures are avoided.
Owner:中电科网络安全科技股份有限公司
A kind of image semantic retrieval method and system
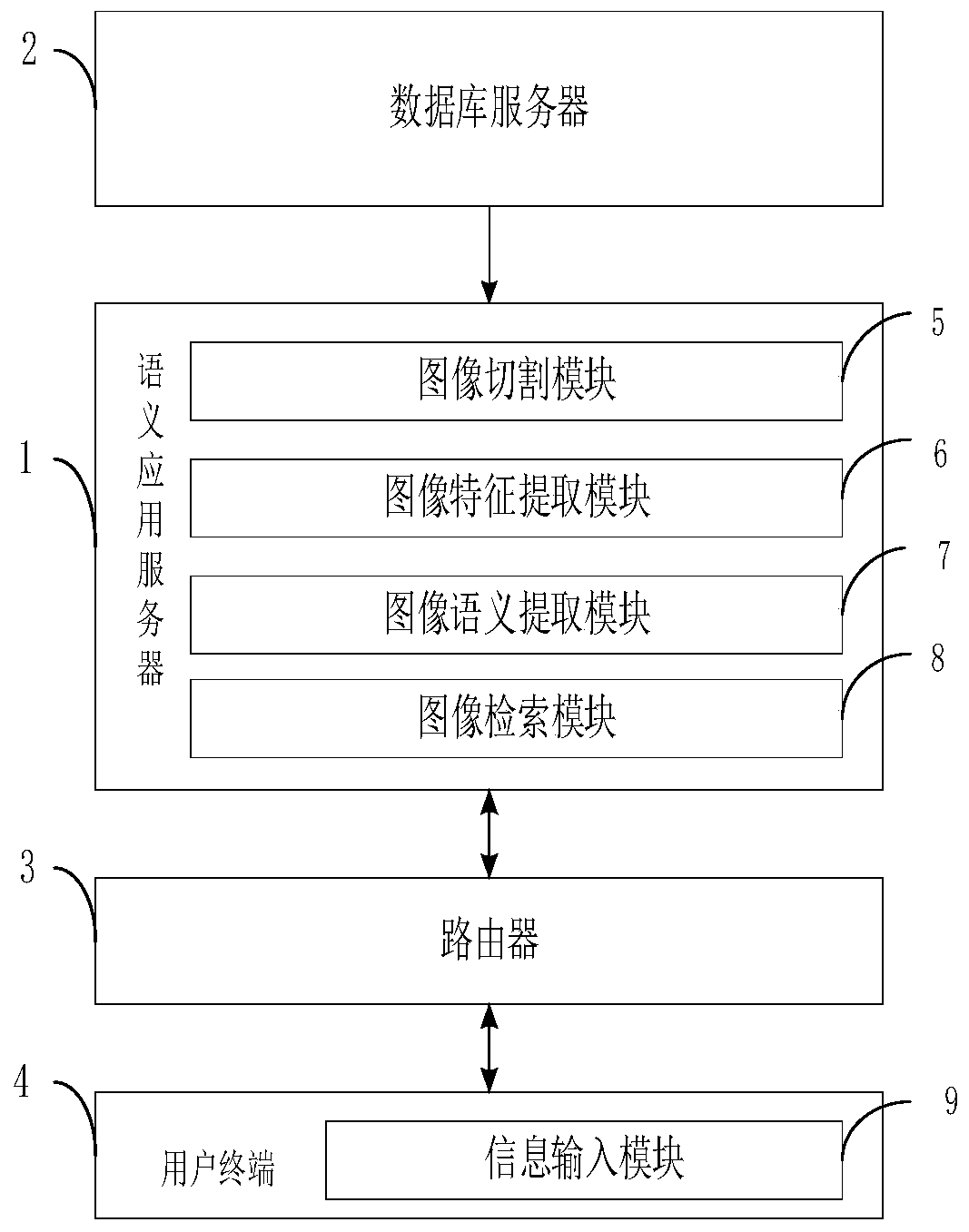
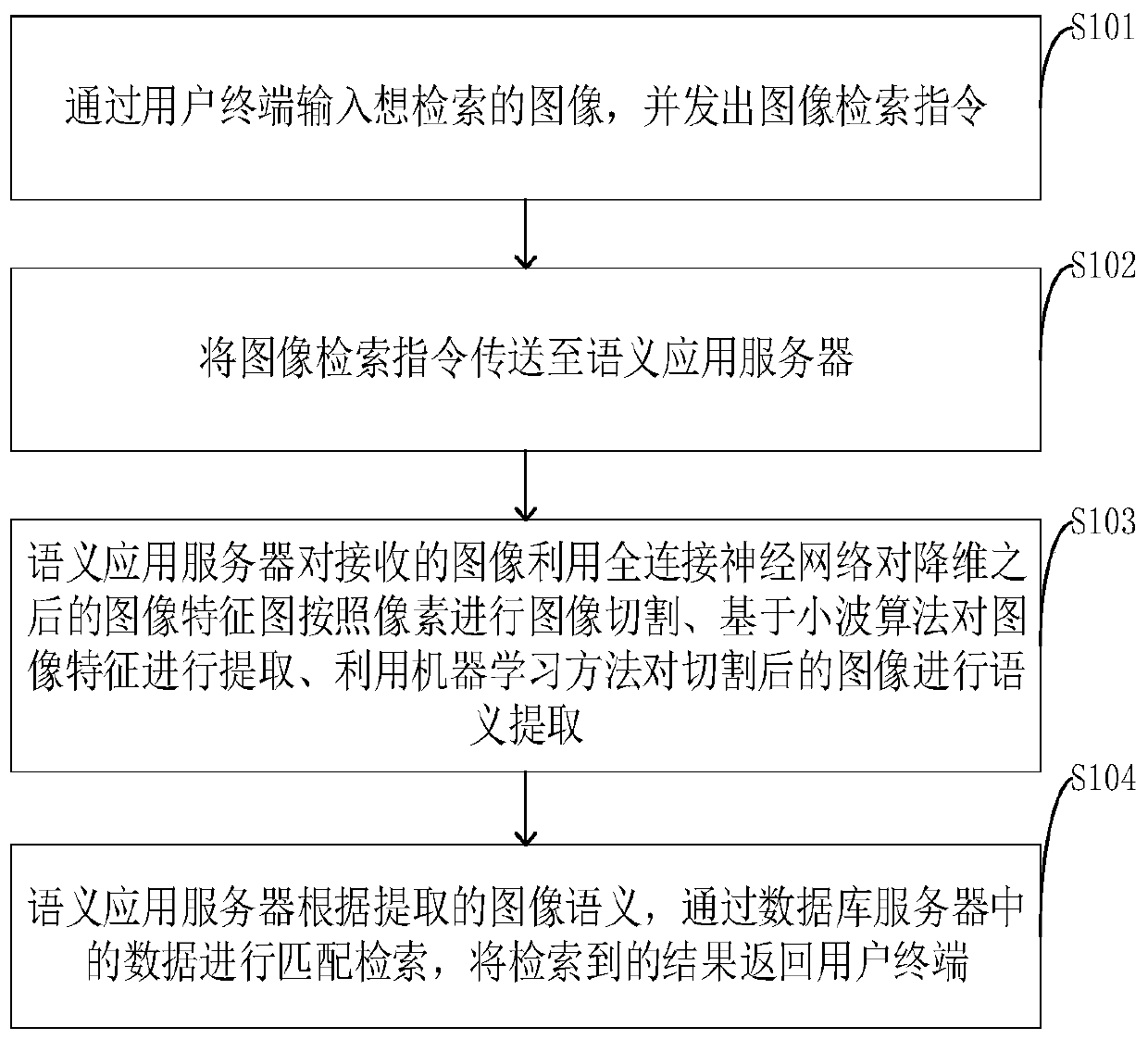
InactiveCN109783670BQuick searchExact searchImage enhancementImage analysisApplication serverDocument model
The invention belongs to the field of image retrieval, and discloses an image semantic retrieval method and system, which redefines the DEF item and expands the DEF item into the union of the basic sememe contained in the word and the relational sememe in the word; the sentence is established as a unit The document model before the concept is acquired; enter the sentence scanning to establish the vector space model; scan the words in the sentence one by one to find out whether there is a corresponding DEF item and a word with the same meaning as the DEF item. In the present invention, the router logs in the database server, queries through the information input module, the database server is connected to the semantic application server, and after the user sends a retrieval command, the semantic application server converts the query through the query conversion submodule Instructions, through the decision-making implementation module to call the database server to complete image semantic retrieval, through the dynamic generation and release sub-module of the scheme to return data to the user terminal.
Owner:BAOJI UNIV OF ARTS & SCI
Determination method for optimal thickness of protection layer reserved for retaining piles in deep foundation pit blasting construction
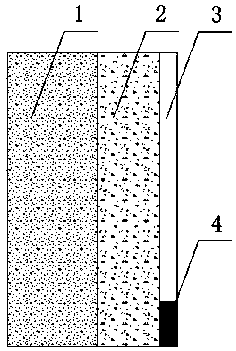
InactiveCN106592604BEnsure safetyAccurately guide the constructionFoundation testingExcavationsElement modelPeak value
The invention discloses a determining method for the optimum thickness of a guard post reserved protection layer in deep foundation pit blasting construction. The number of to-be-optimized thicknesses of the optimum thickness delta of the reserved protection layer (2) is set to be n+1 within the optimal range of the optimum thickness delta of the reserved protection layer (2); then according to a blasthole (3), explosive (4), the n+1 to-be-optimized thicknesses of the optimum thickness delta of the reserved protection layer (2) and a finite element model of a guard post (1), the pressure peak Fci and the tension peak Fti applied to the guard post (1) under the action of the blast load are obtained sequentially; and then the pressure peak Fci is compared with the compression bearing capacity [Fc] of the guard post (1), the tension peak Fti is compared with the tension capacity [Ft] of the guard post (1), and the corresponding i to-be-optimized thickness delta i which first meets the requirements that the pressure peak Fci is smaller than the compression bearing capacity [Fc] and the tension peak Fti is smaller than the tension capacity [Ft] is the optimum thickness delta of the reserved protection layer (2). The determining method can meet the actual bearing requirement and can also ensure the excavation safety of a deep foundation pit, high efficiency and maximum benefit.
Owner:WUHAN UNIV OF SCI & TECH
A process scheduling method and device
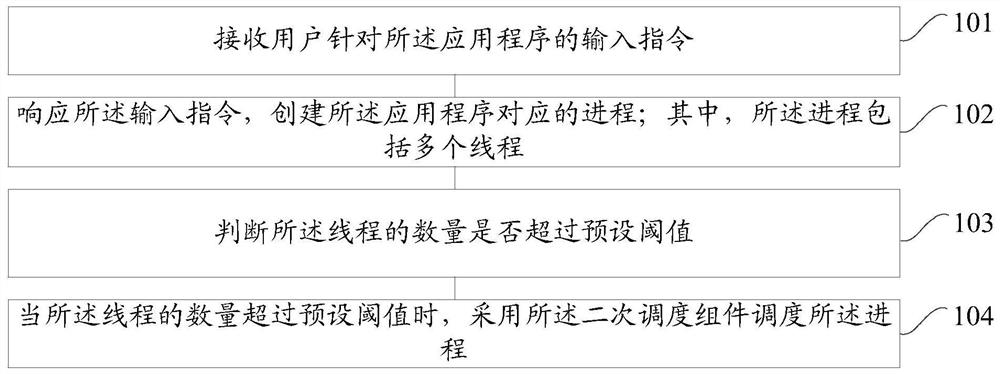
ActiveCN109426556BAvoid huge workloadReduce task switching overheadProgram initiation/switchingResource allocationParallel computingApplication procedure
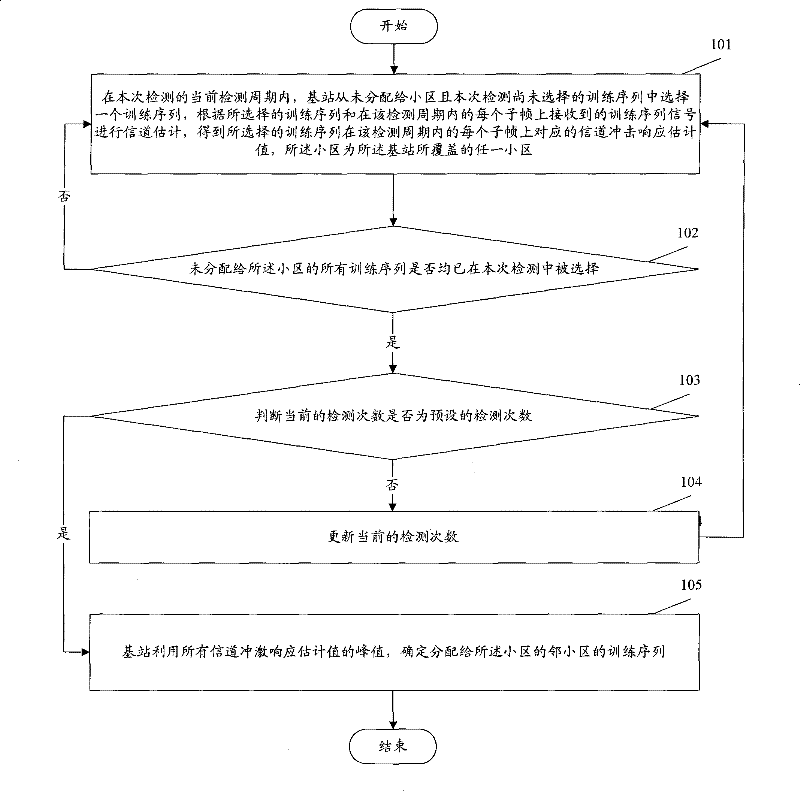
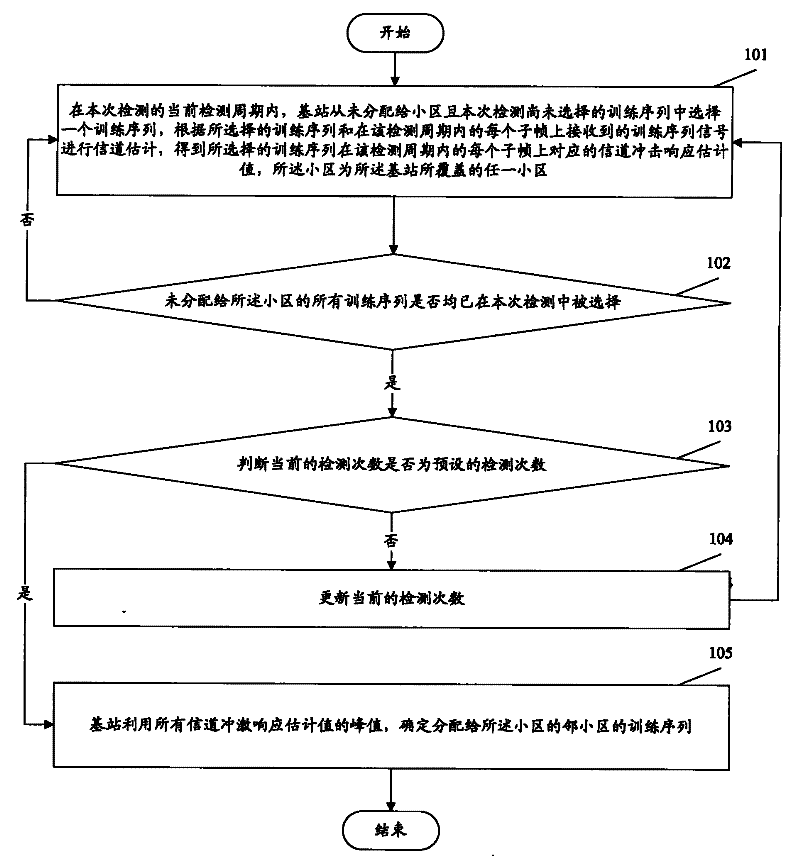
Embodiments of the present invention provide a method and device for process scheduling, which are applied to a Linux system. The Linux system includes a secondary scheduling component, and an application program is installed on the Linux system. The method includes: An input instruction of a program; in response to the input instruction, create a process corresponding to the application program; wherein, the process includes a plurality of threads; judge whether the number of the threads exceeds a preset threshold; when the number of the threads exceeds a preset threshold When the threshold is set, the secondary scheduling component is used to schedule the process; one or more exclusive CPUs are set for the secondary scheduling component to ensure that the secondary scheduling component monopolizes one or more CPUs, reducing task switching overhead, thereby maximizing Maximize the improvement of system performance and avoid the huge workload of developing a new operating system. The simple and efficient system including secondary scheduling components has excellent performance and can maximize system efficiency.
Owner:DATANG MOBILE COMM EQUIP CO LTD
cdm cluster website management system
ActiveCN107147531BAvoid huge workloadAvoid useless workData switching networksWeb siteInformation sharing
Owner:贵州华宁科技股份有限公司
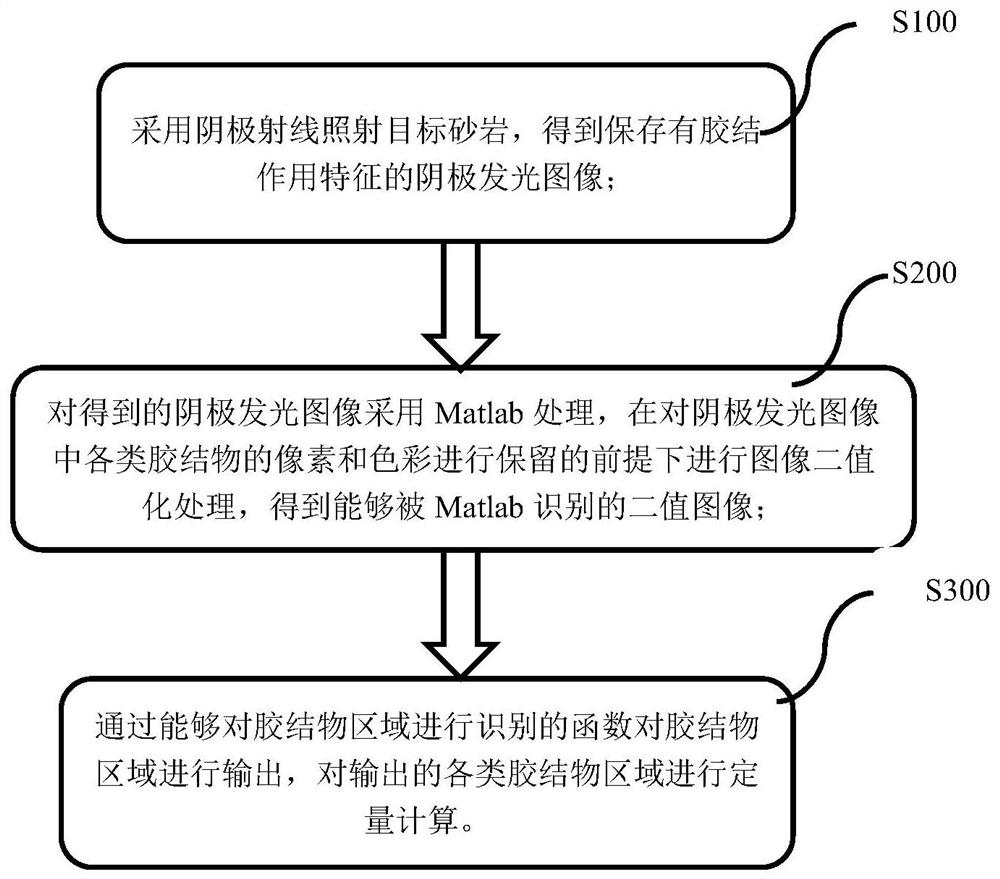
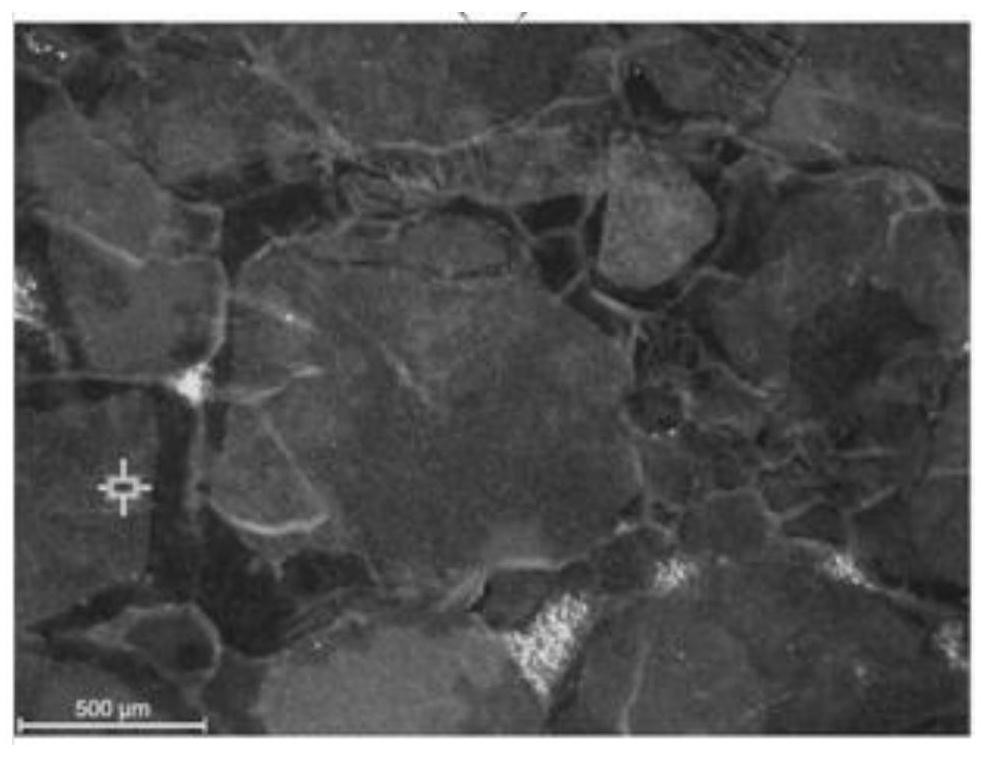
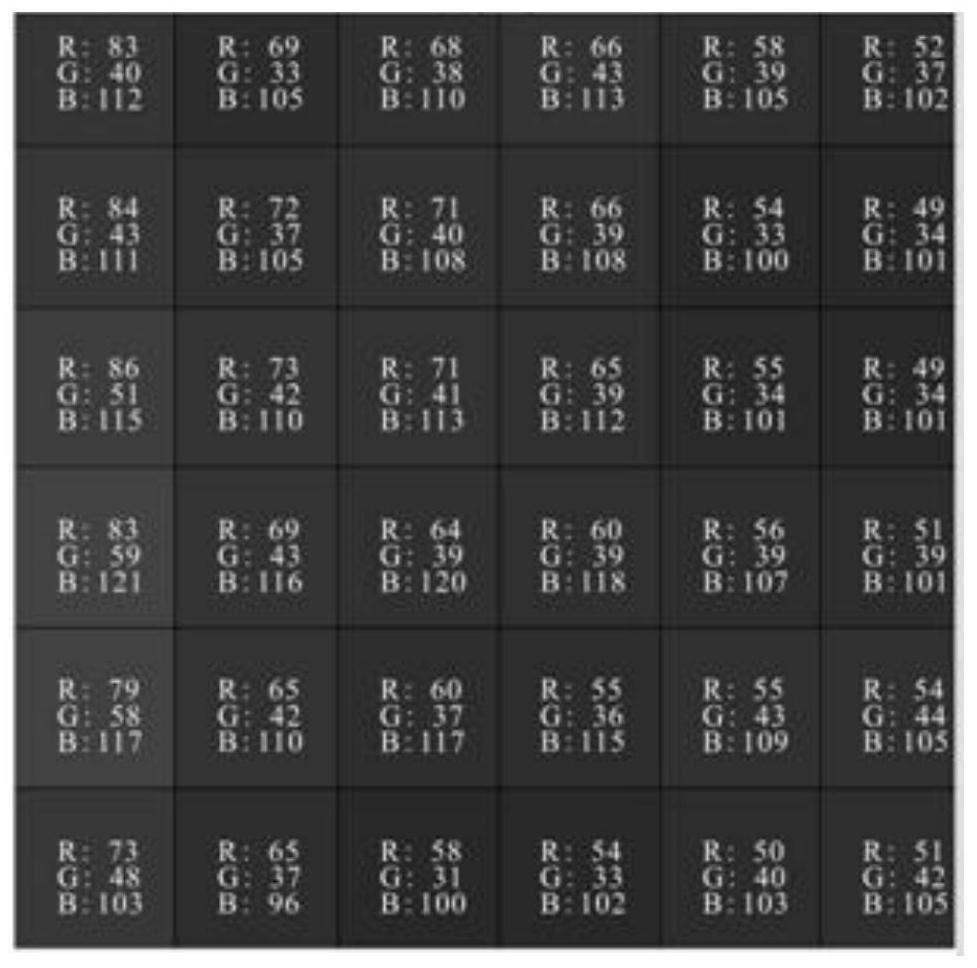
A Quantitative Calculation Method for Secondary Oversizing of Silicate Based on Cathodoluminescence Technology
ActiveCN111487274BAvoid huge workloadImprove recognition accuracyImage analysisMaterial analysis using wave/particle radiationEngineeringCathode ray
The embodiment of the present invention discloses a quantitative calculation method for siliceous secondary enlargement based on cathodoluminescence technology, including: S100, using cathode rays to irradiate the target sandstone, to obtain a cathodoluminescence image with cementation characteristics preserved; S200, for The obtained cathodoluminescence image is processed by Matlab, and image binarization is performed under the premise of retaining the pixels and colors of various cements in the cathodoluminescence image to obtain a binary image that can be recognized by Matlab; S300, through being able to The function of identifying the cement area outputs the cement area, and quantitatively calculates the output cement areas. The present invention collects cathodoluminescent images of the target sandstone, outputs and quantitatively calculates the identified cement region after binarization processing, so as to solve the problem of large deviations and huge workload in manual stacking distance measurement.
Owner:CHINA UNIV OF GEOSCIENCES (BEIJING)
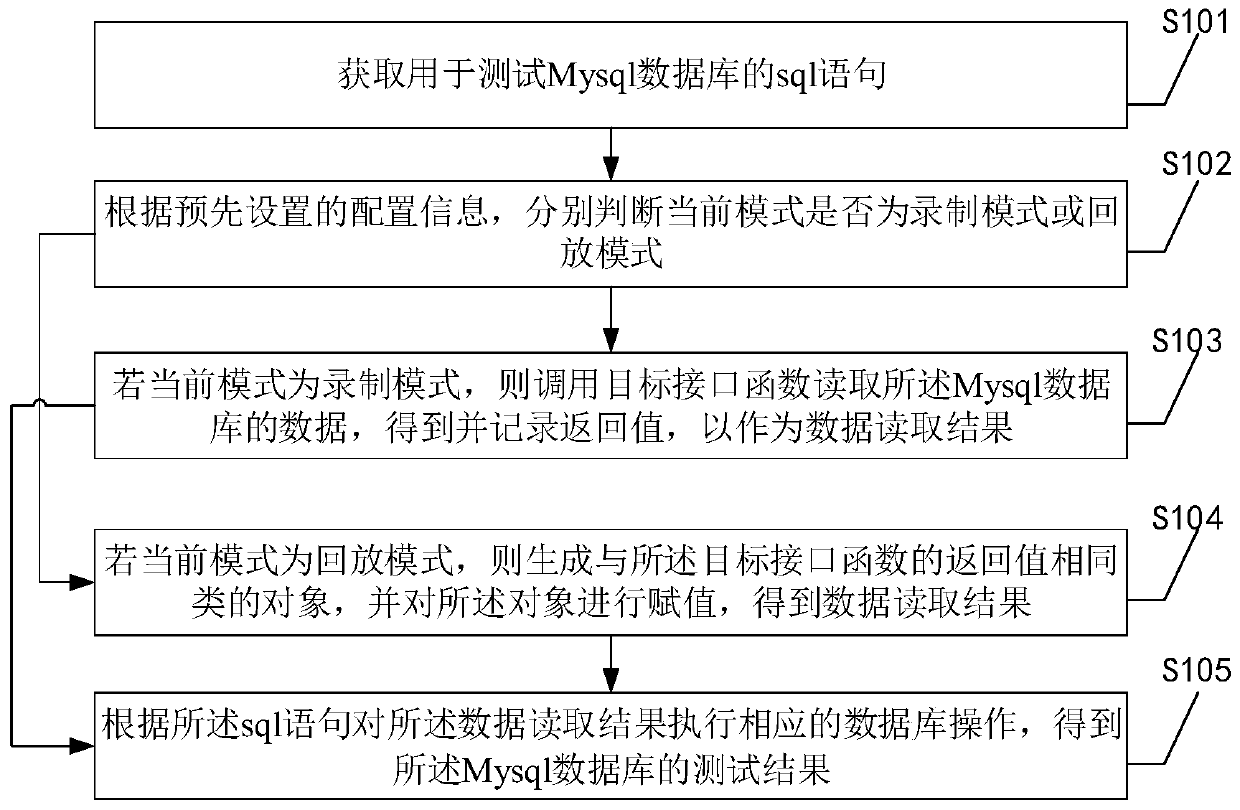
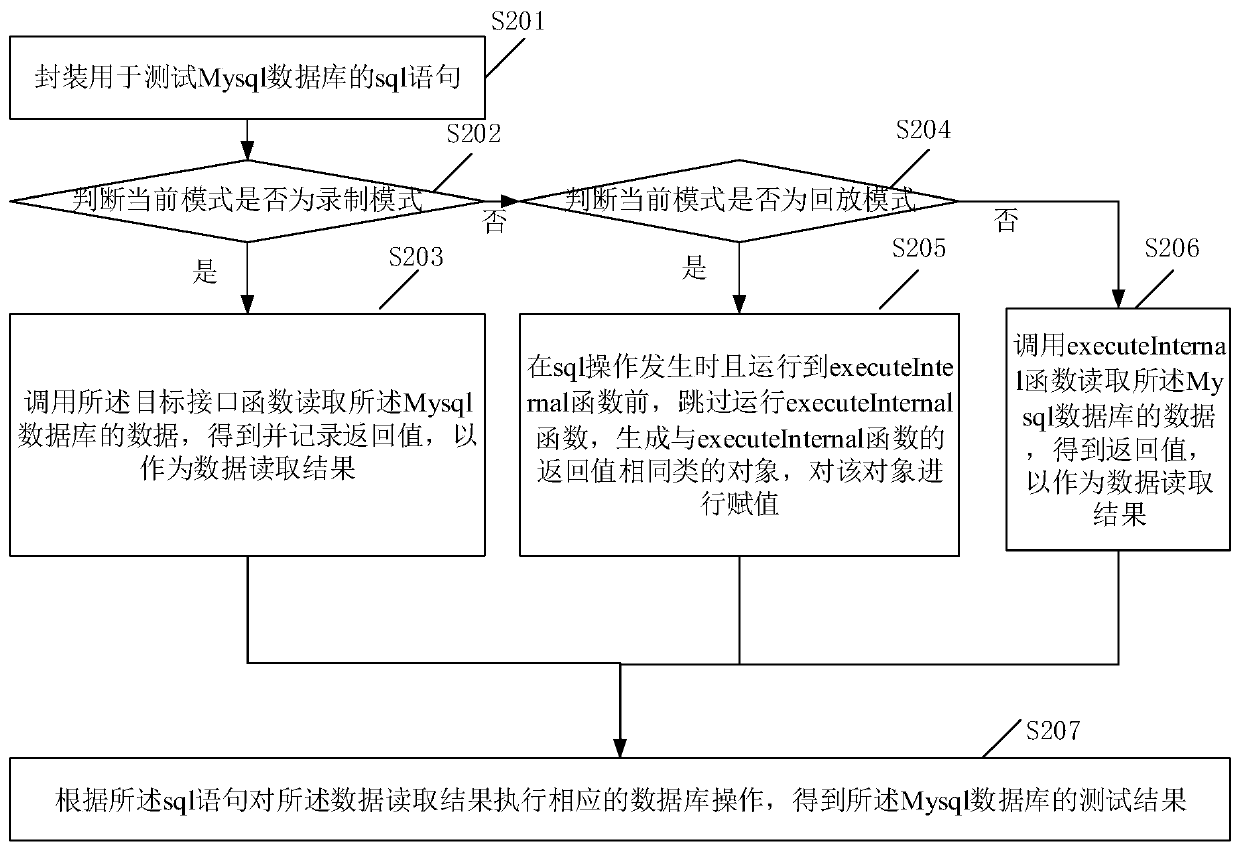
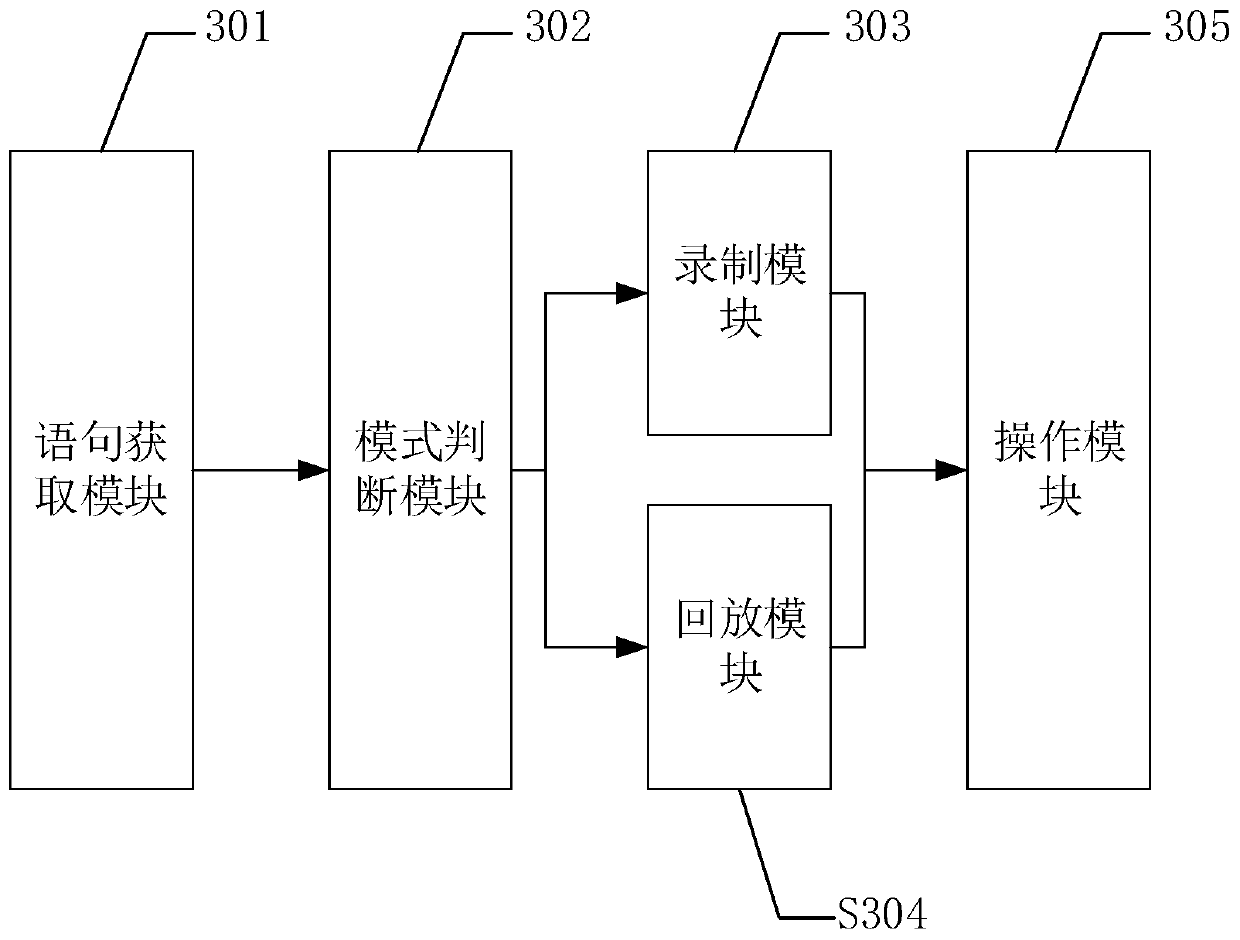
Simulation return method, device and equipment of Mysql
ActiveCN110597725AImprove test efficiencyAvoid interferenceDatabase management systemsSoftware testing/debuggingTest efficiencyData preparation
The invention discloses a simulation return method of Mysql. According to the scheme, when the database operation is carried out for the first time, the database data preparation process is recorded,and when the database operation is carried out subsequently, the database data is not prepared again, and the database data is determined according to the recording result, so that the original database data is always consistent in each database operation. On one hand, the interference of data change on a test result is avoided, on the other hand, the huge workload of repeatedly initializing the database is avoided, and finally, the database test efficiency is improved. In addition, the invention further provides a simulation return device and equipment of Mysql and a readable storage medium,and the technical effects of the Mysql simulation return device and equipment correspond to the technical effects of the method.
Owner:浙江诺诺网络科技有限公司
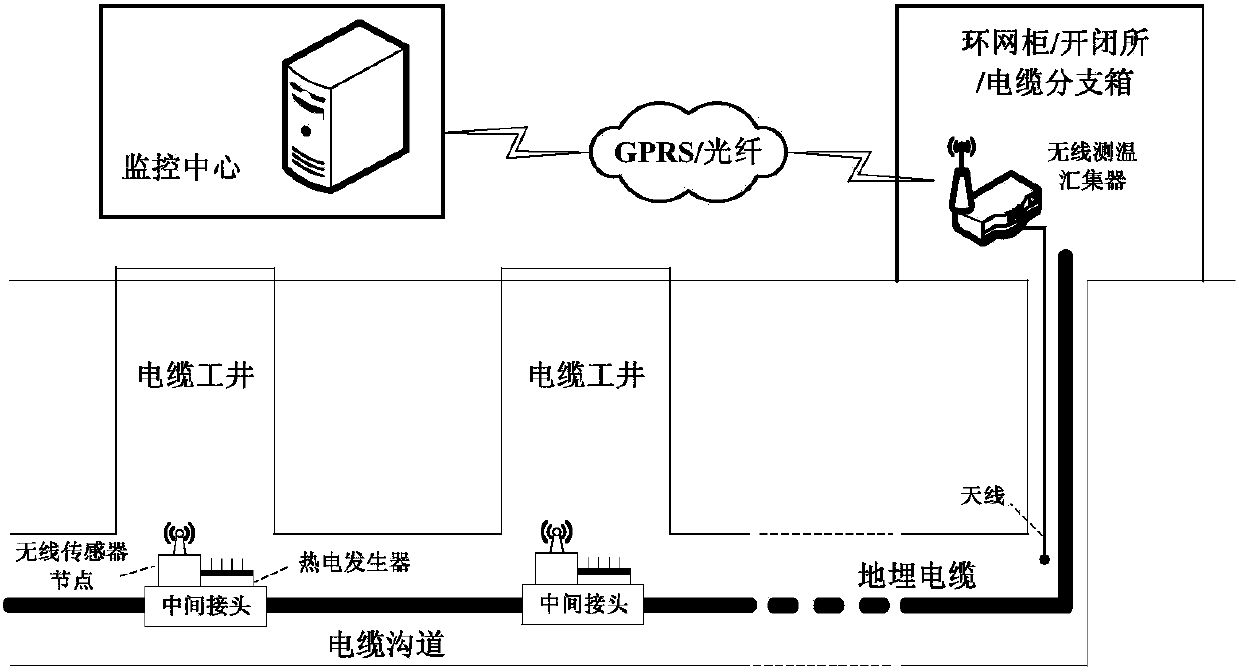
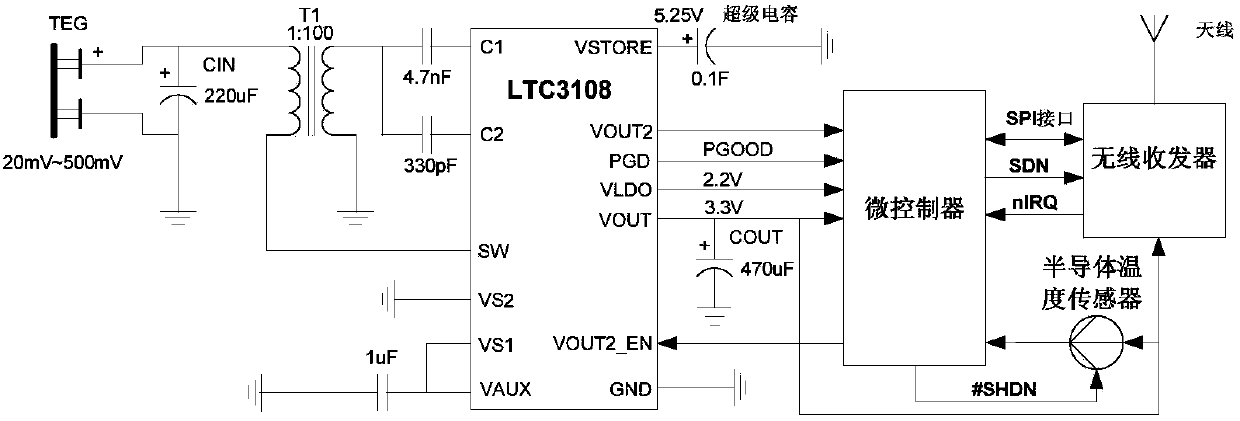
An on-line monitoring system and monitoring method for the temperature of the intermediate joint of buried cables
ActiveCN103575415BAvoid huge workloadNo maintenanceTransmission systemsThermometers using electric/magnetic elementsEnergy harvesterEngineering
The invention relates to an on-line temperature monitoring system and method for power cables, in particular to an on-line temperature monitoring system and method for intermediate joints of a buried cable. The monitoring system is composed of wireless sensor nodes, TEGs, a wireless temperature measurement concentrator and a monitor center, wherein the intermediate joints of the buried cable are located below cable work wells; the wireless sensor nodes and the TEGs are installed on the outer surfaces of the intermediate joints of the buried cable; the wireless temperature measurement concentrator is installed in a switching station or a ring main unit or a cable branch box at a cable terminal or a branch joint; an antenna of the wireless temperature measurement concentrator extends into a cable channel to collect monitor data of the wireless sensor nodes and send the monitor data to the monitor center through a GPRS or an optical fiber. According to the on-line temperature monitoring system and method for the intermediate joints of the buried cable, the TEGs and an energy collector are adopted to convert temperature difference into electric energy to be supplied for a wireless sensor, and at the same time, the monitor data are collected in a wireless mode; the wireless sensor nodes work in a low-power dissipation mode, and therefore the power dissipation of the whole monitoring system is reduced.
Owner:STATE GRID CORP OF CHINA +2
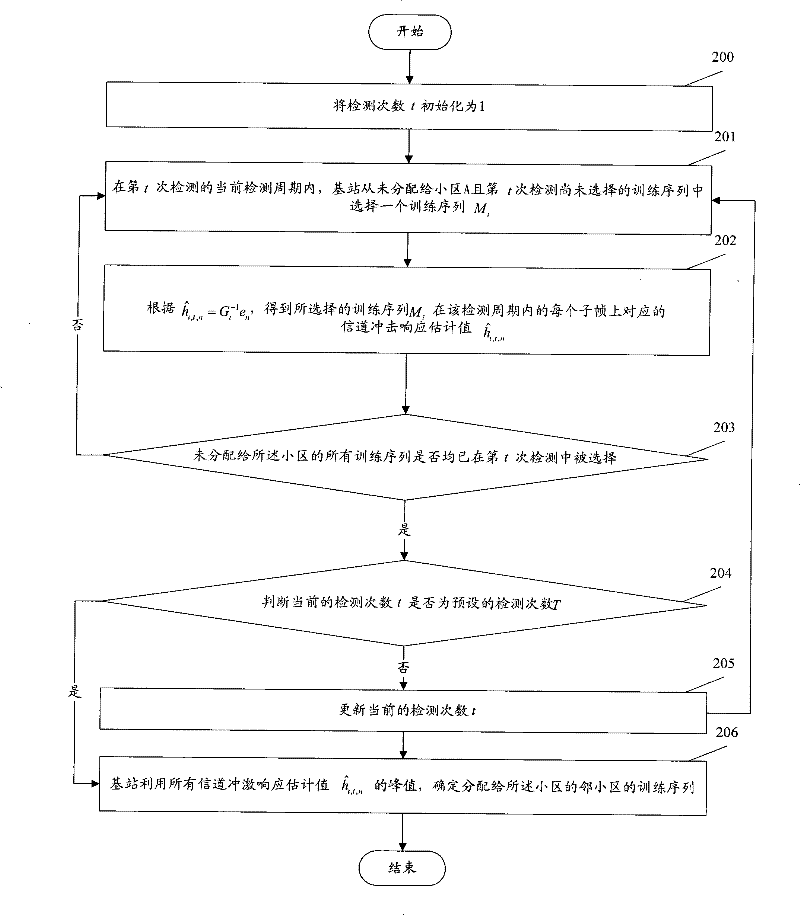
Method for detecting adjacent cell information
InactiveCN101635579BImplement automatic detectionAvoid huge workloadBaseband system detailsMulti-frequency code systemsSequence signalChannel impulse response
Owner:TD TECH COMM TECH LTD
A method of realizing rigid body motion
InactiveCN104867172BAvoid huge workloadAvoiding Geometric DistortionsAnimationObject motionInteractive design
The present invention relates to the field of three-dimensional animation design, and provides a method for realizing rigid body motion, including: step 100, sampling motion data at N+1 moments in the rigid body motion process; step 200, performing data processing on the sampled motion data through a difference quotient algorithm, Obtain the unit tangent vector and curvature vector of the translation motion at each moment, and the unit tangent vector and curvature vector of the rotation motion; step 300, carry out the construction of rigid body translation motion; step 400, carry out the construction of rigid body rotation motion; step 500, according to The rigid body translational motion constructed in step 300 and the rigid body rotational motion constructed in step 400 construct the overall motion process of the rigid body to obtain the motion trajectory curve of each point on the rigid body; step 600, according to the obtained motion trajectory curve of each point on the rigid body , so that the rigid body moves according to the trajectory curve. The invention is closer to the real object motion scene in real life, and enhances the interactivity of the design.
Owner:DALIAN UNIV OF TECH
Pre-embedded fixing device and embedding method for single-hole multi-point pore water piezometer
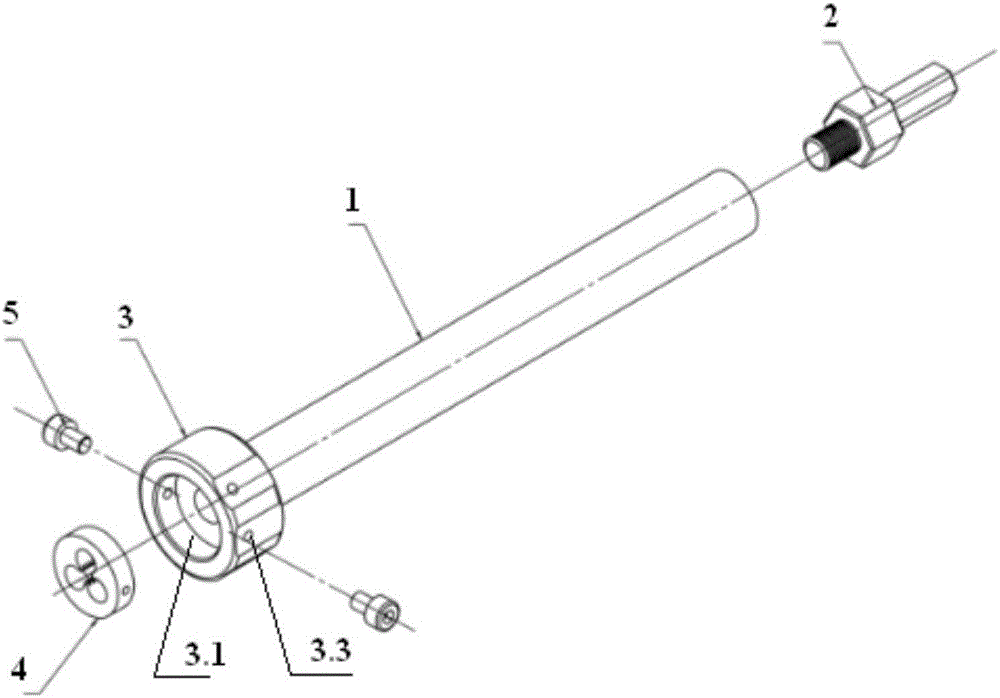
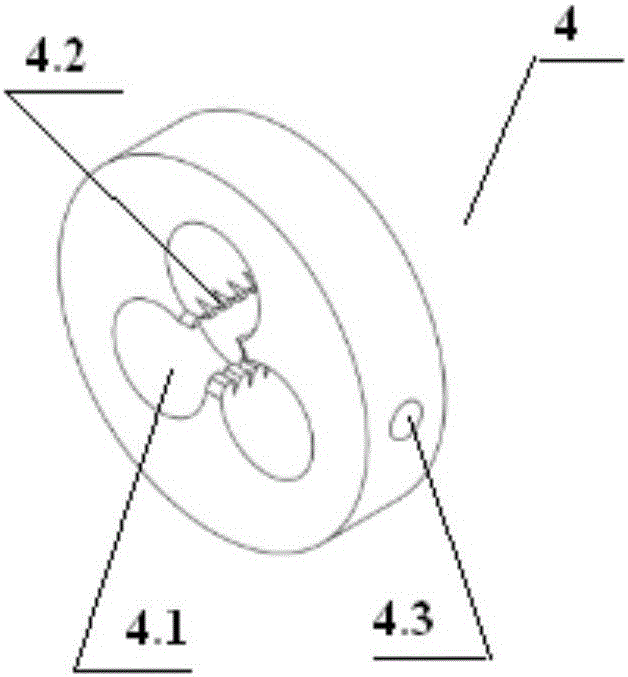
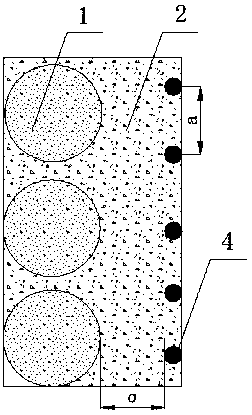
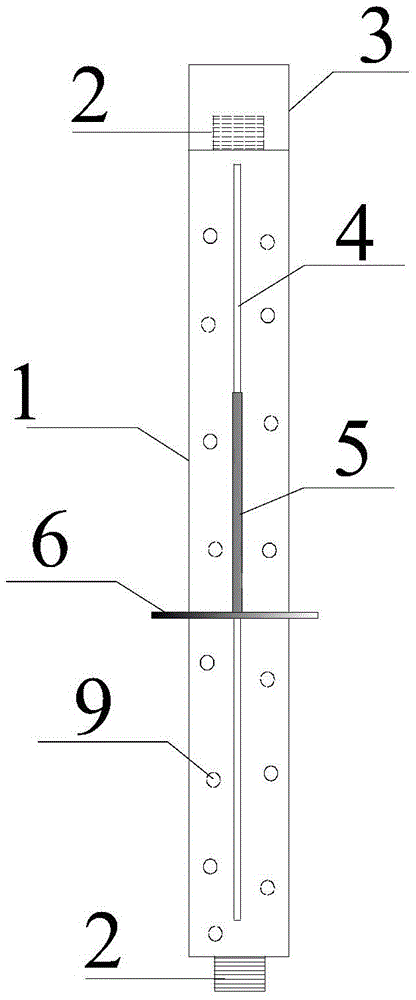
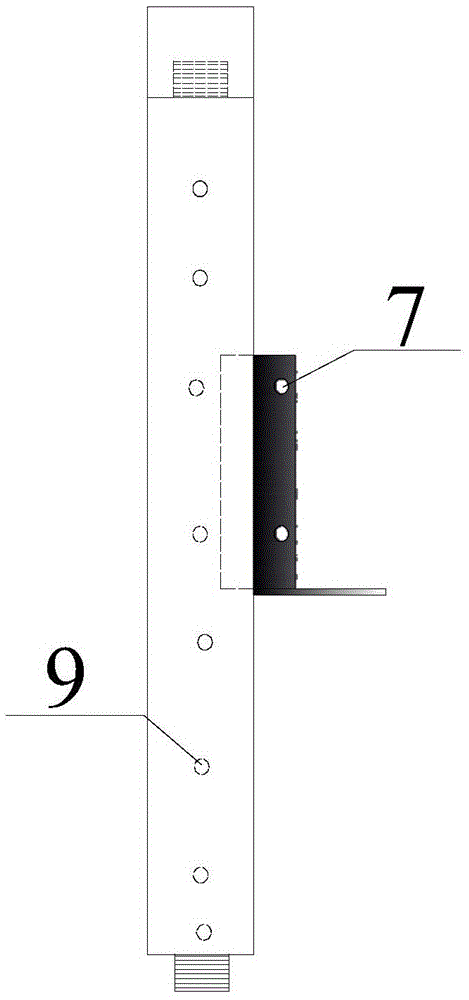
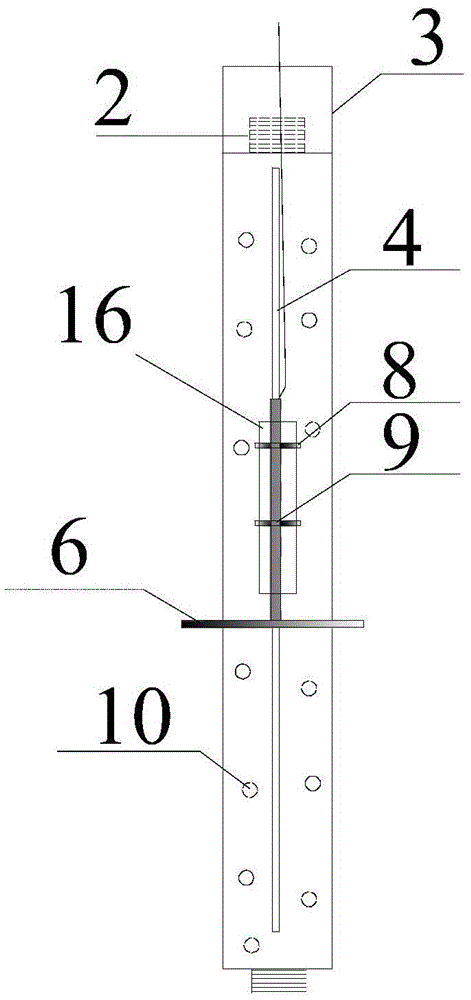
ActiveCN104805822BSimplify the construction processRealize simultaneous embeddingIn situ soil foundationPore water pressureEngineering
A single-pore multi-point pore water pressure meter embedding fixing device and an embedding method thereof are disclosed. The device comprises a fixing component, a connecting component and a container, wherein the fixing component consists of a plurality of hanging rods; each hanging rod is provided with a vent hole; two ends of each hanging rod are provided with a screw thread and a sleeve; and one side of each hanging rod is provided with a guidance sliding chute. The connecting component consists of a connecting plate and a supporting plate. The supporting plate is provided with a vent hole. One side of the connecting plate is inserted into the guidance sliding chute; the other side is fixed with an annular hoop. A pore water pressure meter is installed inside the annular hoop. The container for containing water to dip the pore water pressure meter is arranged on the supporting plate. A lead wire hole is arranged on the top of the container for containing water. A pulling wire is arranged on the lead wire of the pore water pressure meter. A signal cable of each pore water pressure meter is led outside a monitoring hole upwardly. The single-pore multi-point pore water pressure meter embedding fixing device solves the problem that the pore water pressure meter in the single-hole multi-point manner is easy to deflect; accordingly, with the application range being enlarged, the single-pore multi-point pore water pressure meter embedding fixing device has the advantages of short device embedding time, low construction cost, low construction difficulty, high monitoring precision, reliable long-term monitoring data, or the like.
Owner:NANJING HYDRAULIC RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com