Patents
Literature
30results about How to "Safety level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method, system and apparatus for selecting encryption levels based on policy profiling
InactiveUS7010681B1Easily maintainable methodSelective encryptionSecuring communicationClient-sideSecurity level
The present invention depicts a method, system and program product for controlling levels of security and levels of encryption based on a predefined policy profile. This enables administrators and those who control the network to easily respond to changes in the requirements of the security levels for specific applications. It also allows for response to changes in personnel (such as someone being removed from a position that had topsecret security access) and accommodates variations in access by client devices.
Owner:IBM CORP
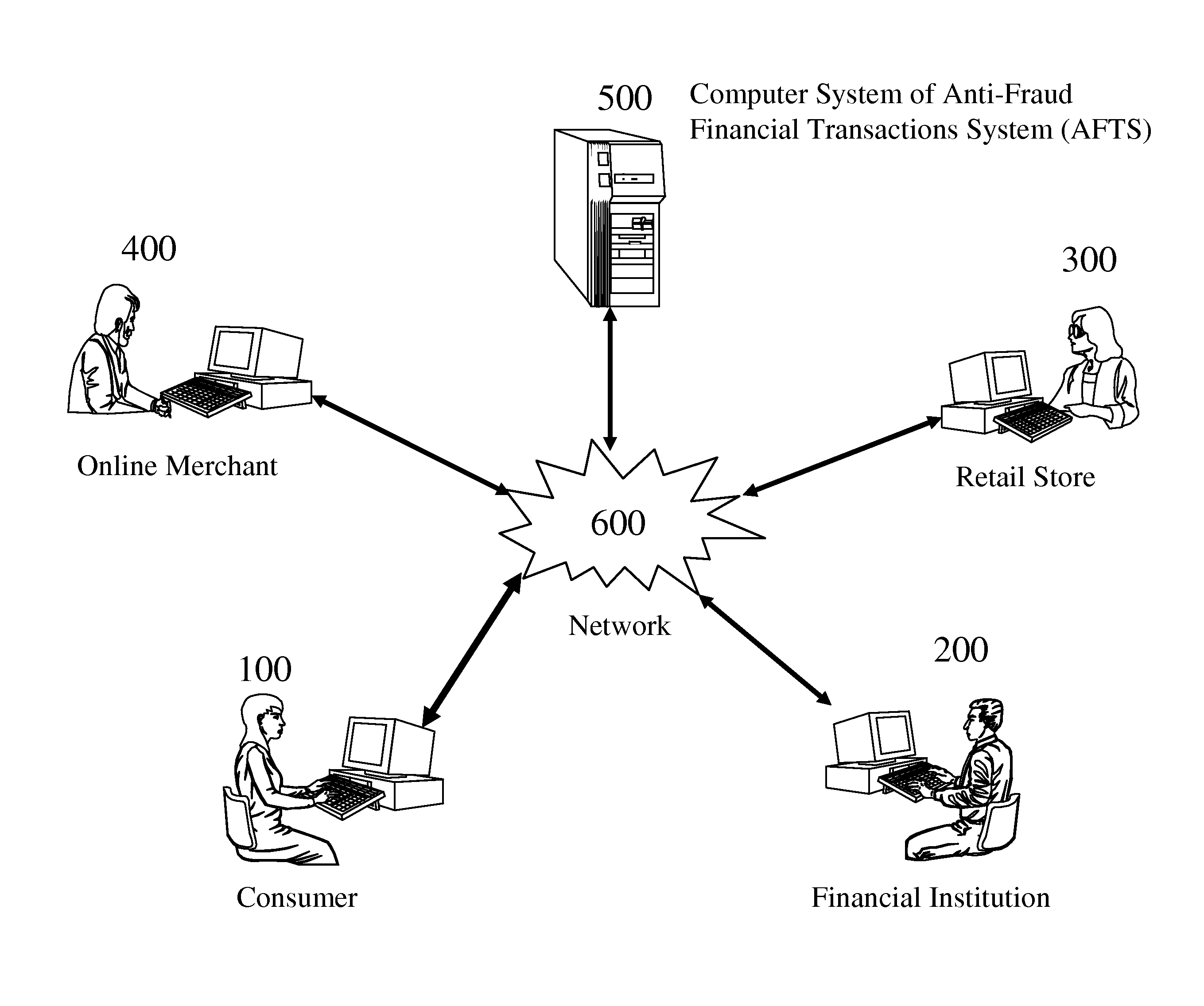
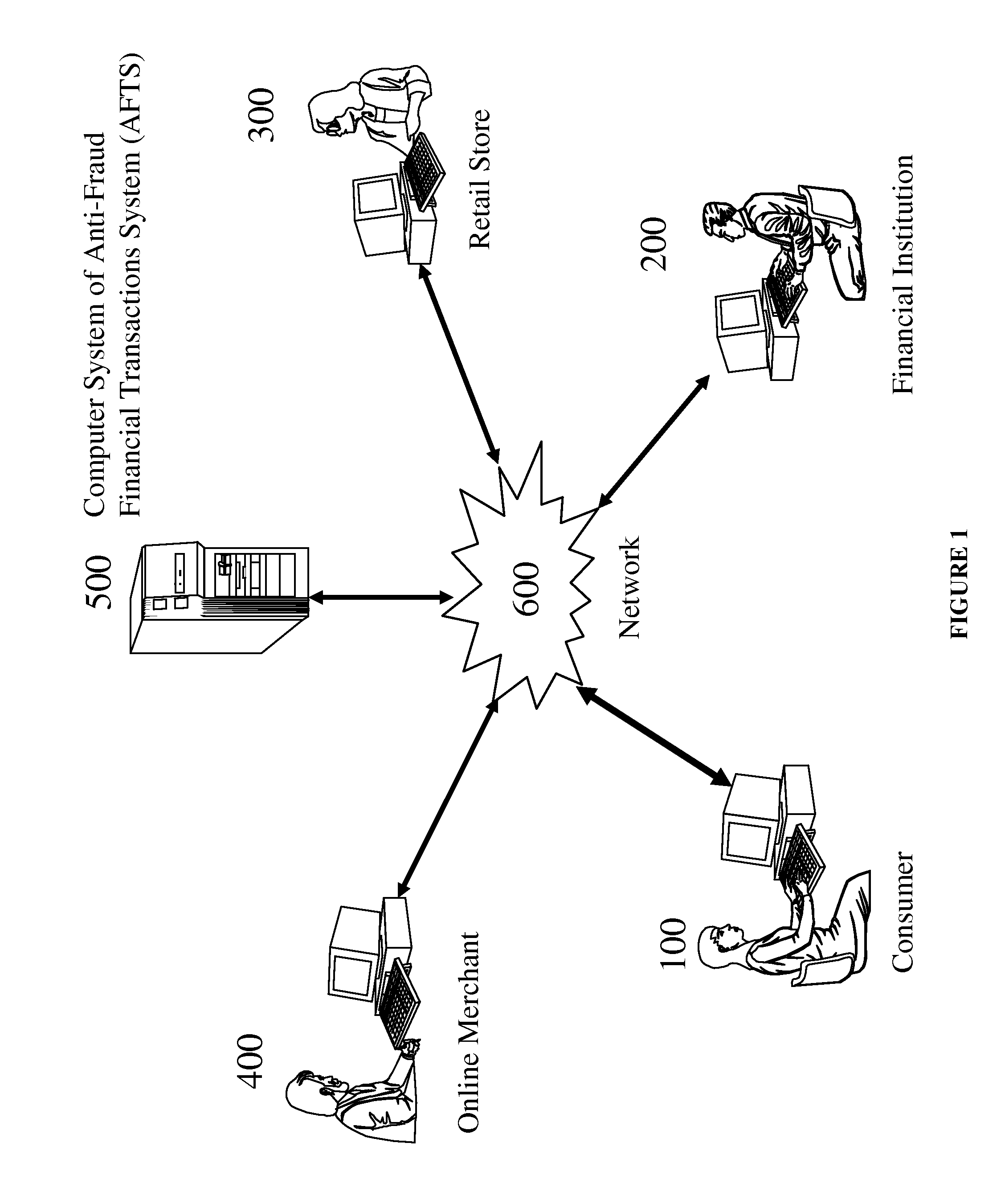
Anti-fraud financial transactions system
ActiveUS20130103482A1Easily fabricatedEasy to be stolenMarketingInternet privacyFinancial transaction
Users can conduct financial transactions in a secure manner without the need to use any traditional financial instrument, such as credit card, debit card, ATM card, gift card, stored value card, prepaid card, cash, check, coupon, token, ticket, voucher, certificate, note, security, etc. In addition, users' identities are kept confidential in the transactions without violating the Anti-Money Laundering and Anti-Terrorist Financing requirements.
Owner:SONG ALEXANDER +2
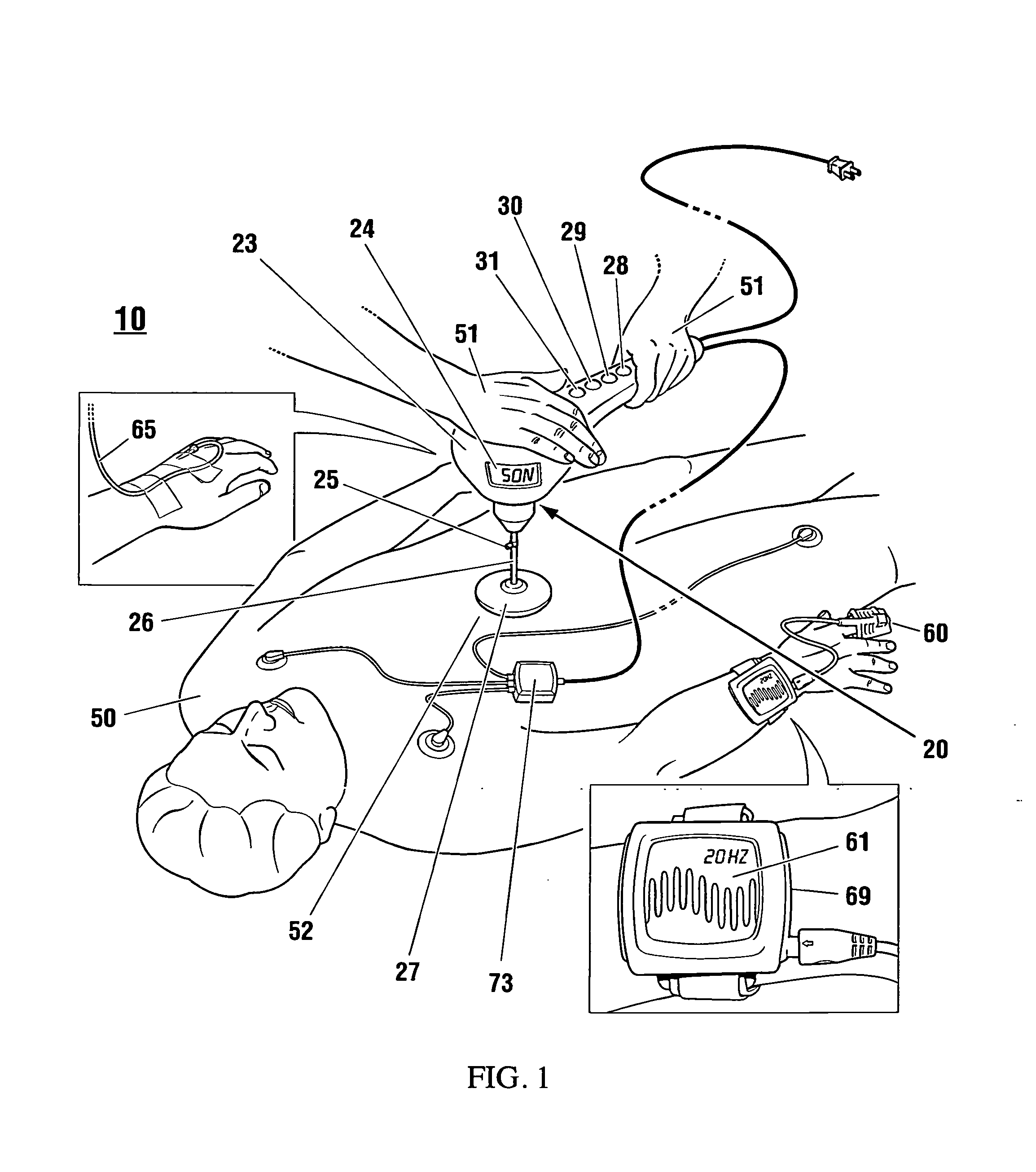
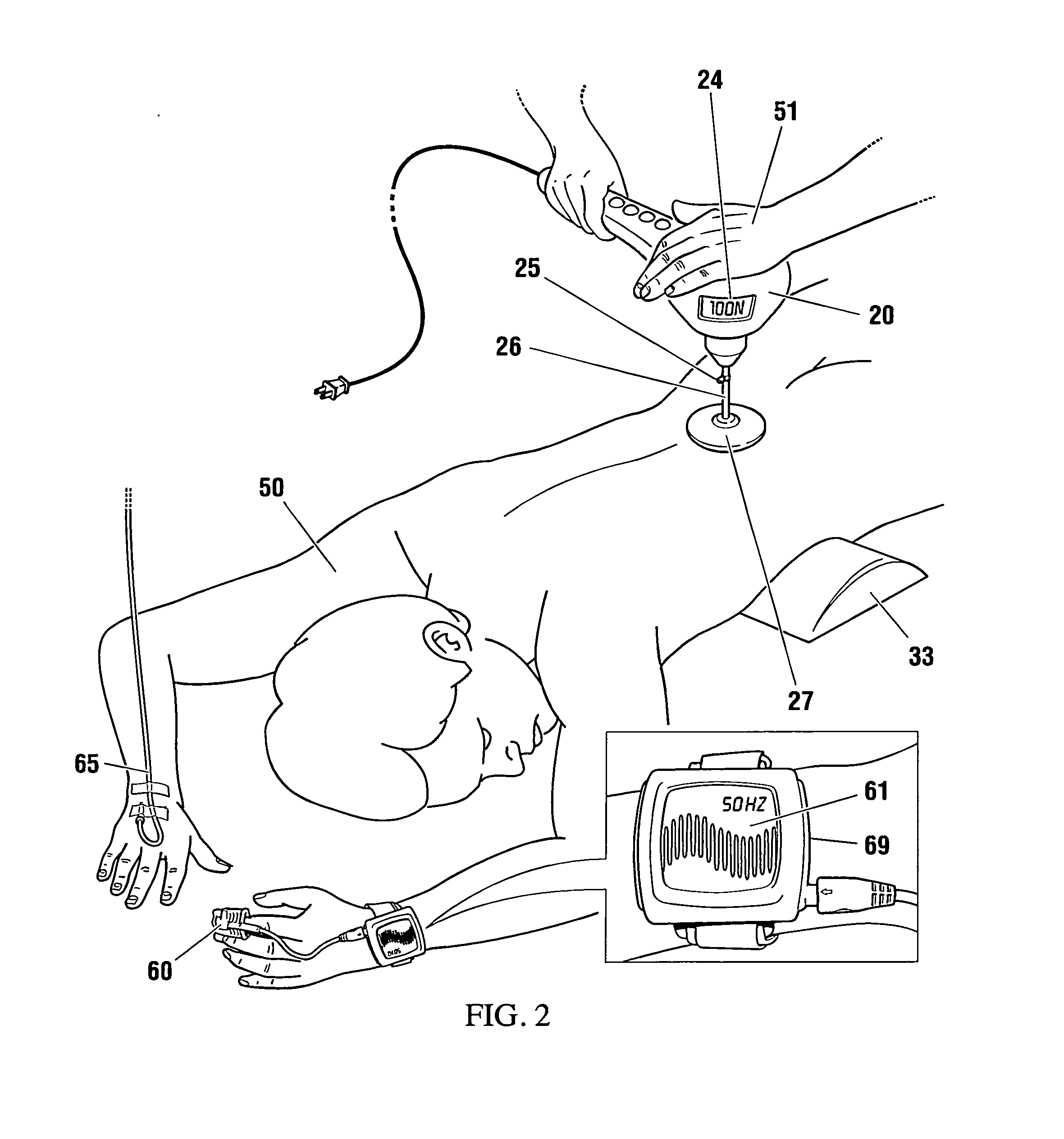
Non-invasive reperfusion system by deformation of remote, superficial arteries at a frequency much greater than the pulse rate
InactiveUS20130281897A1Effective researchEffective clinical toolUltrasound therapyOrgan movement/changes detectionPULMONARY EMBOLUSThrombus
Preferred systems for assisting clearance of an acutely thrombosed artery substantially surrounded by boney external body surfaces which are resistant to deformative displacement relative to the thrombosed artery by the application of external percussive force are described. The method consists of applying targeted, localized, non-invasive, high infrasonic to low sonic frequency vibratory percussion with a serial impact frequency much greater than the pulse rate of a patient being treated, the percussion directed towards a remote, preferably superficial “target vessel” residing palpably close to the skin surface. Marked vessel deformations with resultant blood pressure and flow fluctuations are thereby induced by the percussion within the target vessel which propagate to the acutely thrombosed artery to provide localized agitation and turbulence to assist thrombolytic and / or IV microbubble delivery and effectiveness in facilitating reperfusion. Preferred apparatus for treatment of ST elevation myocardial infarction, acute ischemic stroke and acute pulmonary embolus are presented.
Owner:AHOF BIOPHYSICAL SYST
Respiratory Mask for Use in Endoscopy Procedures
InactiveUS20080053449A1Safe and effectiveMaintain Seal IntegrityBronchoscopesLaryngoscopesOropharyngeal suctionOxygen
A patient respiratory mask having a shell and a patient cushion for supplying oxygen during an endoscopic or bronchoscopic procedure. The mask has a first port for accepting an endoscope, a second port for accepting oropharyngeal suction, and an optional third port for carbon dioxide monitoring. The first and second ports are covered by preferably flexible, perforated diaphragms for maintaining the seal integrity during oxygen therapy.
Owner:ENDOMASK
Aquatic farming systems
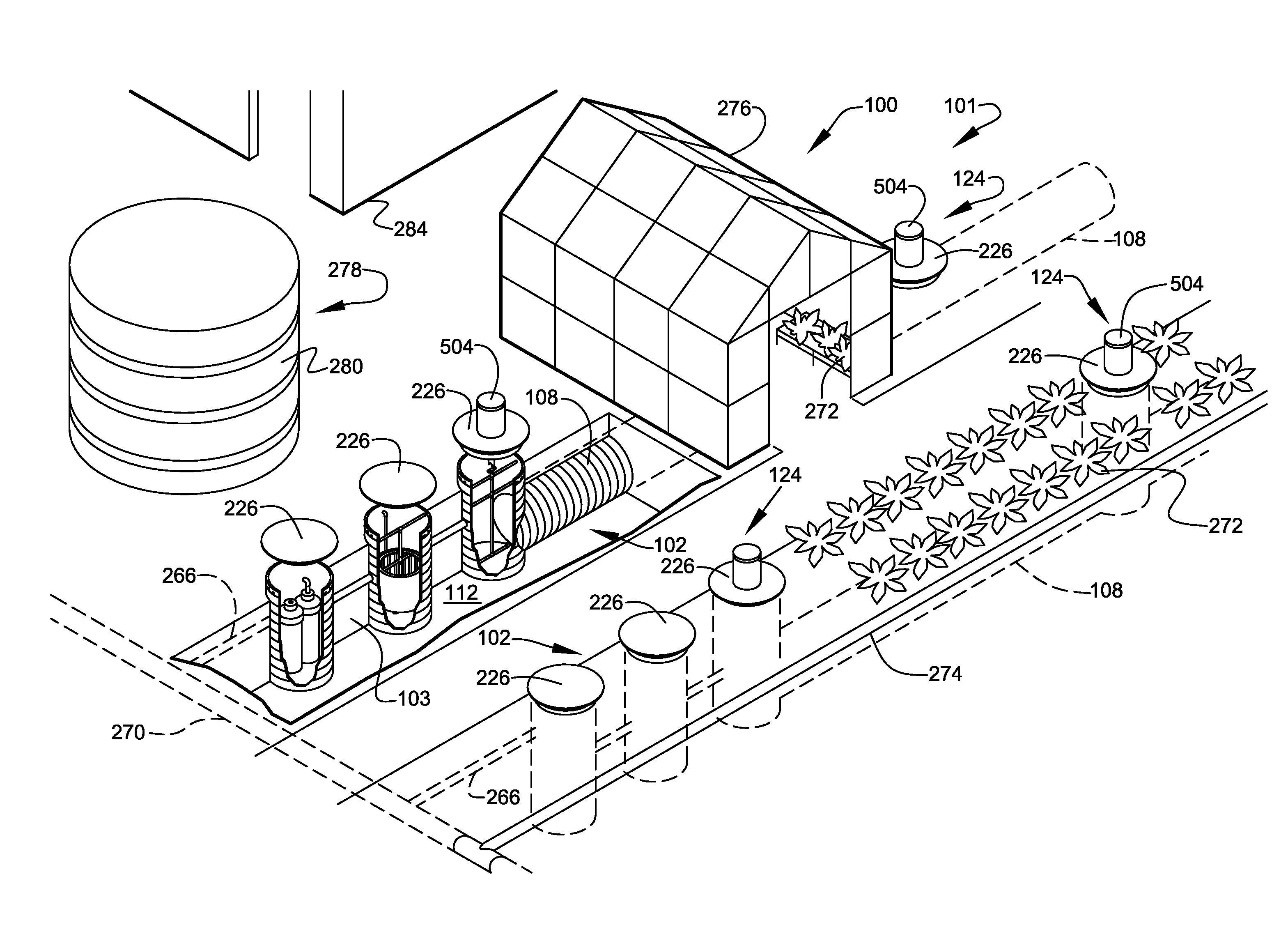
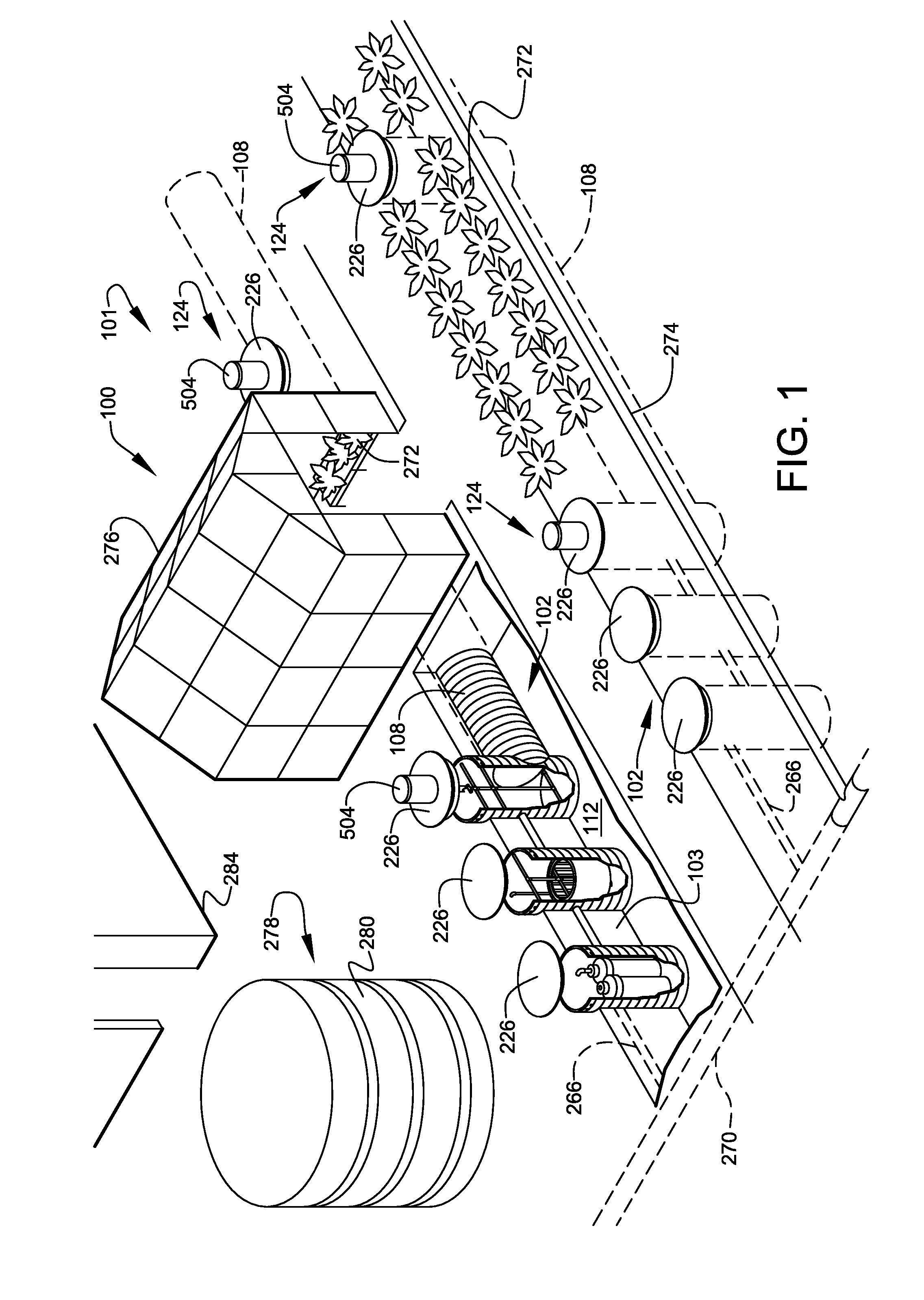
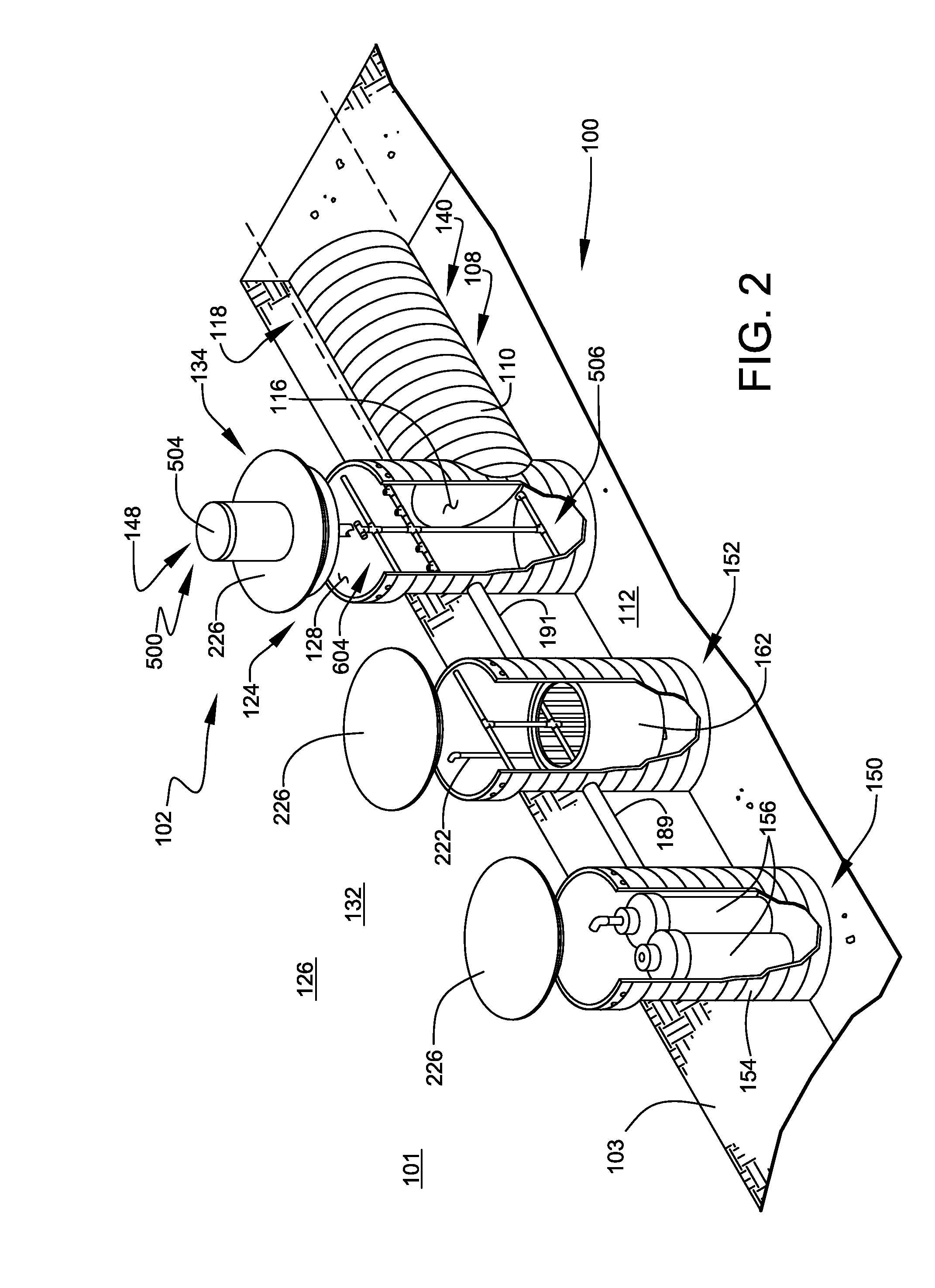
InactiveUS8117992B2Safety levelGrowth inhibitionData processing applicationsClimate change adaptationFarming environmentAgricultural science
A system related to inland farming of seafood products within an environmentally-controlled seafood-farming environment. The seafood-farming environment is preferably established within at least one substantially buried space. The associated apparatus preferably comprises at least one nutrient supplier to supply adequate nutrients to at least one aqueous medium supporting the farming of the seafood, and at least one waste remover to remove unwanted waste from the aqueous medium. Surface crops are grown above and around the seafood-farming environment to maximize production within the farming site. A kit and methods of implementation are also discussed.
Owner:DRP LAP ENTERPRISES LLC +1
Process for remediation of hydrocarbons
InactiveUS20040229342A1Increase oxygen contentPromote bioremediationContaminated soil reclamationFermentationFertilizerPollutant
A process for the remediation and conditioning of soil containing a contaminant. The process comprises (a) mixing the soil with solid material comprising a source of microbial nourishment, (b) inoculating the mixed soil with a diverse microbe population capable of digesting the contaminant, and (c) maintaining the moisture content of the inoculated soil at a level sufficient to support microbial growth. The process can include the additional steps of applying a suspension fertilizer to the mixed soil and / or applying an oxygen-releasing compound to the mixed soil. Step (b) can be repeated to sufficiently reduce the level of contamination.
Owner:BIO CHEM TECH
Capacity load type probe, and test jig using the same
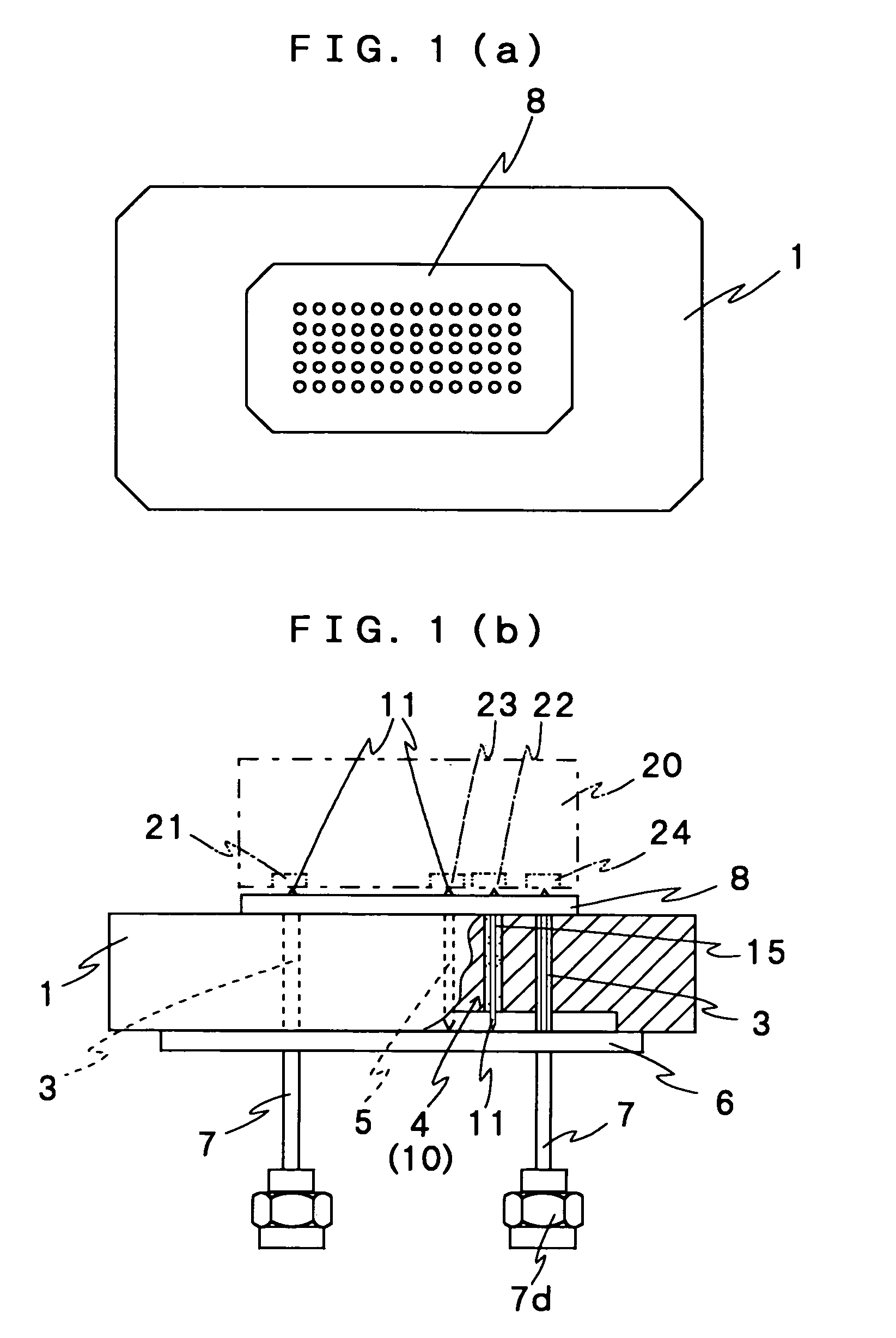
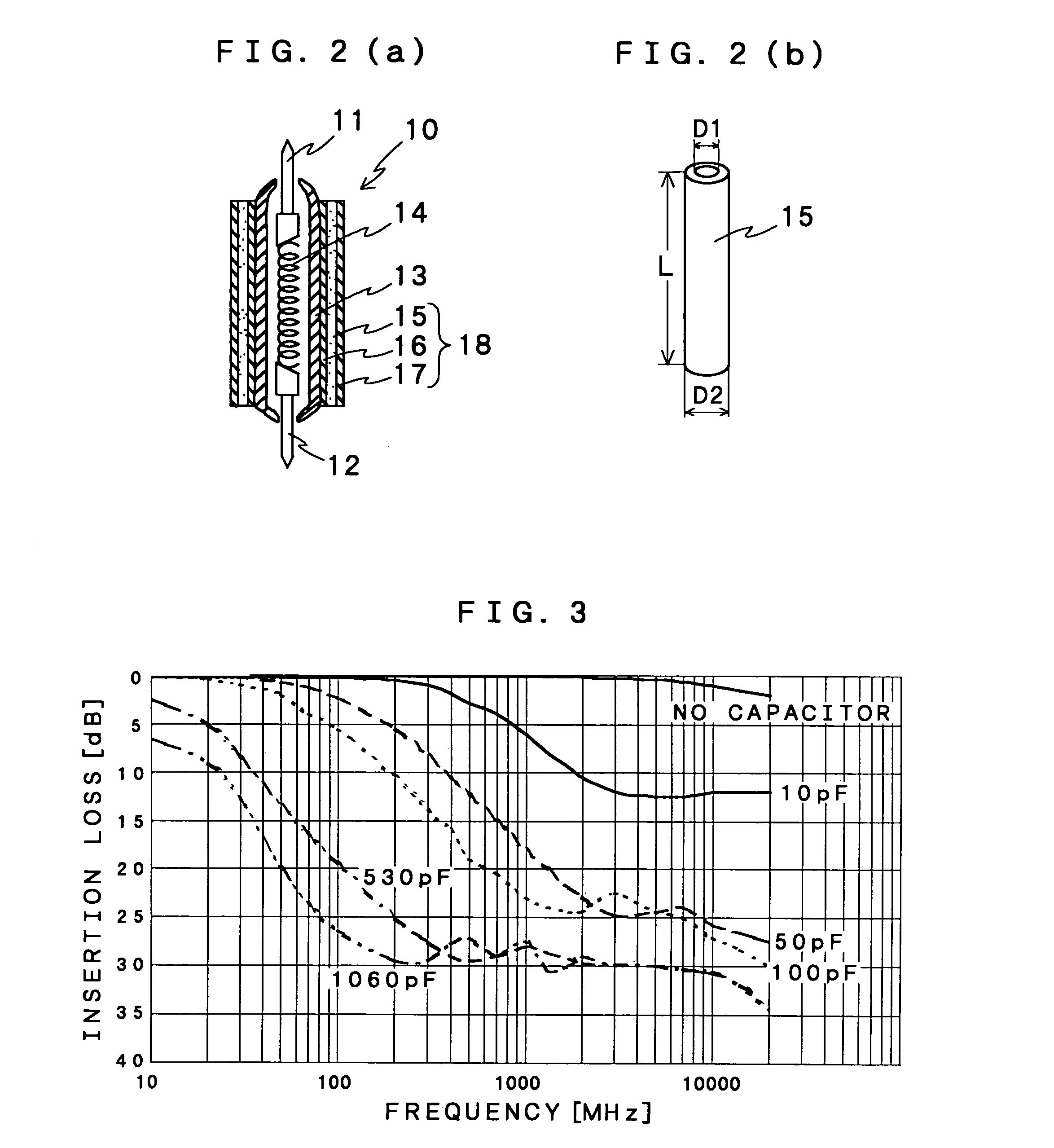
InactiveUS7233156B2Reduce voltage dropVoltage drop at the power supply terminal can be avoidedElectrical measurement instrument detailsElectrical testingVoltage dropDielectric layer
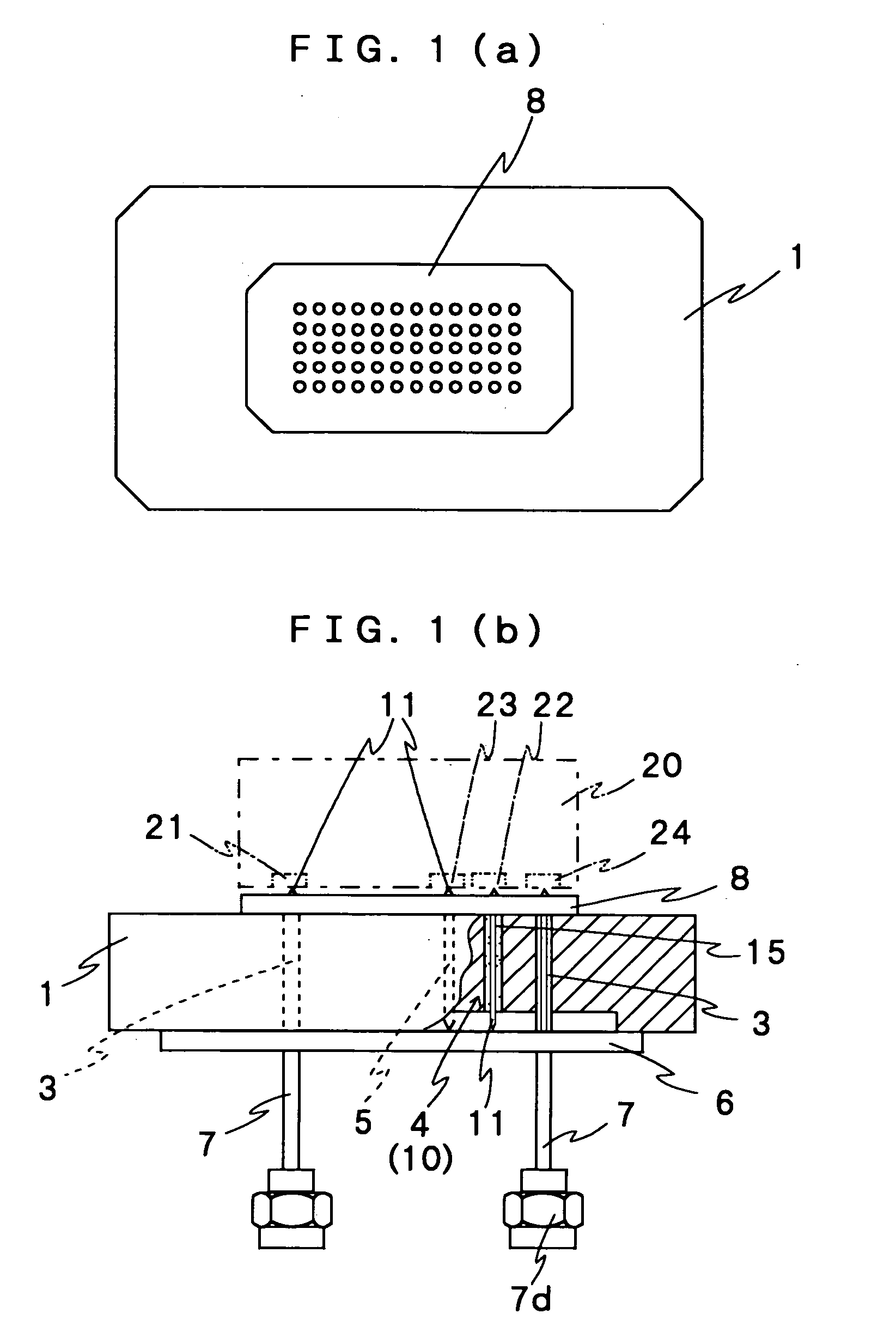
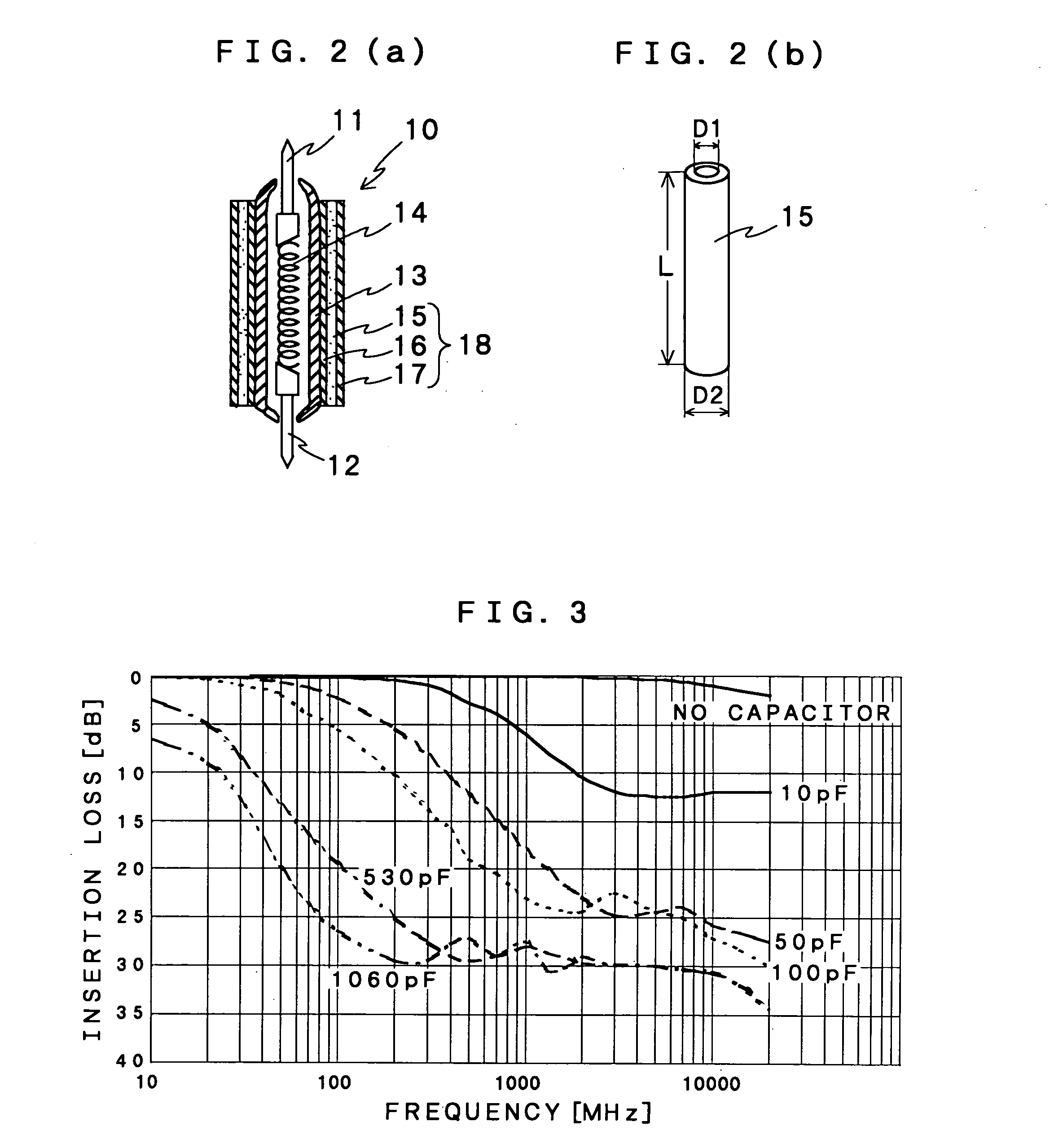
A plurality of probes such as a signal probe (3) and a power supply probe (4) are provided into a metal block (1) so as to penetrate. Each of the probes has a movable pin (11). A tip of the movable pin is projecting from one surface of the metal block (1). And a projection length of the tip is variable. A DUT 20 is pressed onto the surface of the metal block (1) to contact between electrode terminals (21 to 24) and tips of the probes to test characteristics of the DUT. At least one of the probes is capacity loaded probe having a capacitor by providing a dielectric layer and a metal film to peripheral of the probe. As a result, noise can be removed reliably. Additionally, when the capacity loaded probe is used as the power supply probe, a voltage drop is reduced at the power supply terminal in a case of change of the output.
Owner:YOKOWO CO LTD
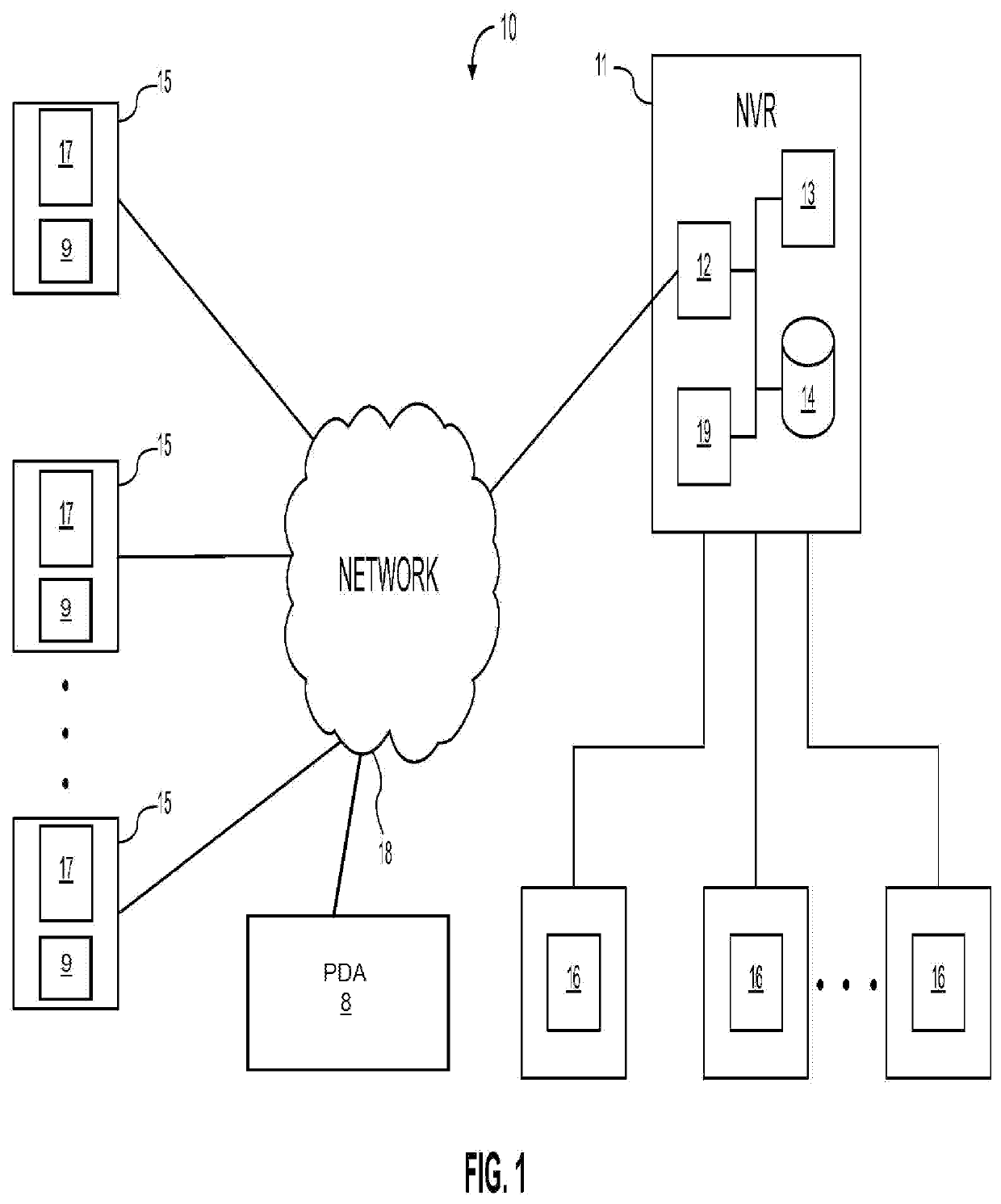
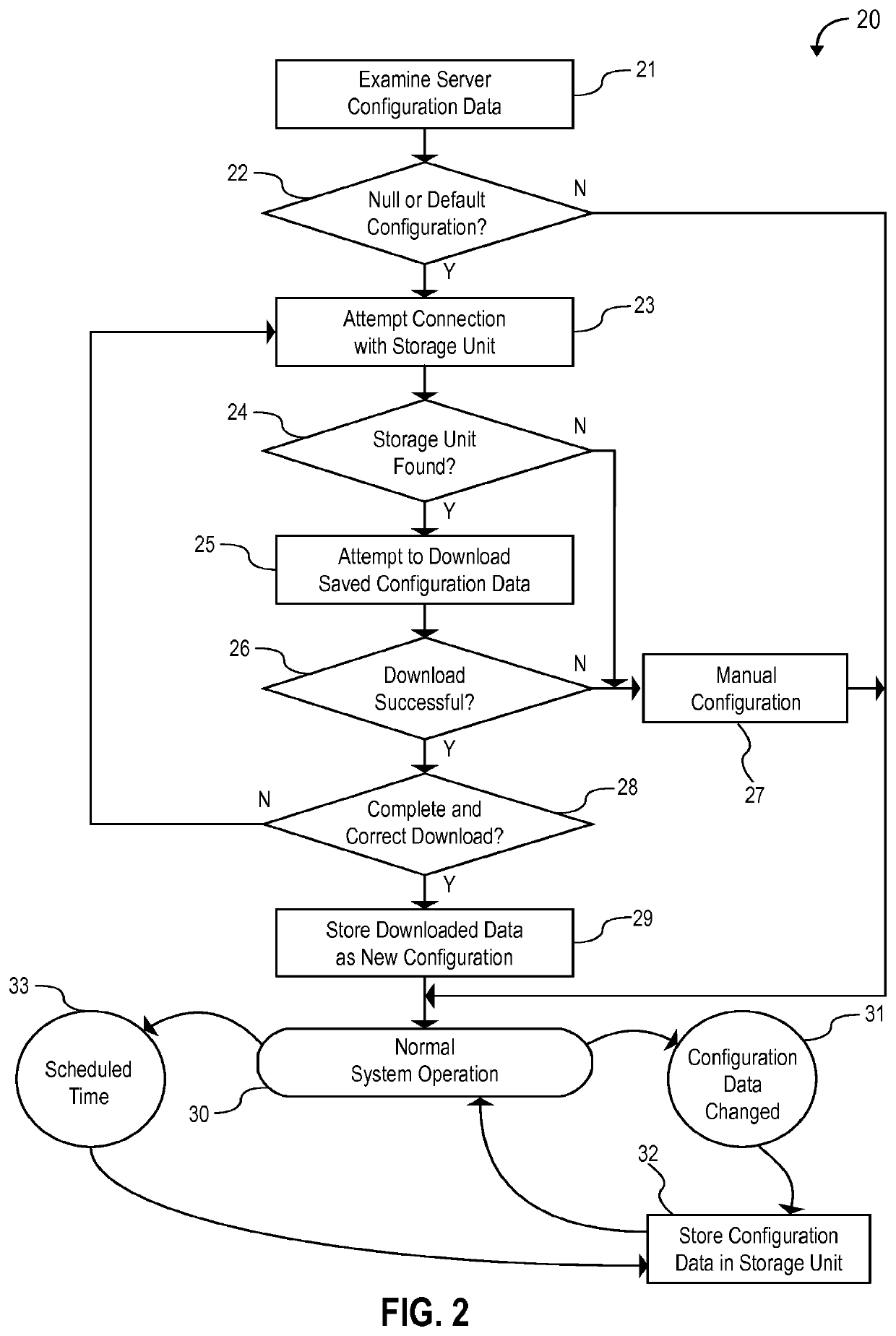
Self-healing video surveillance system
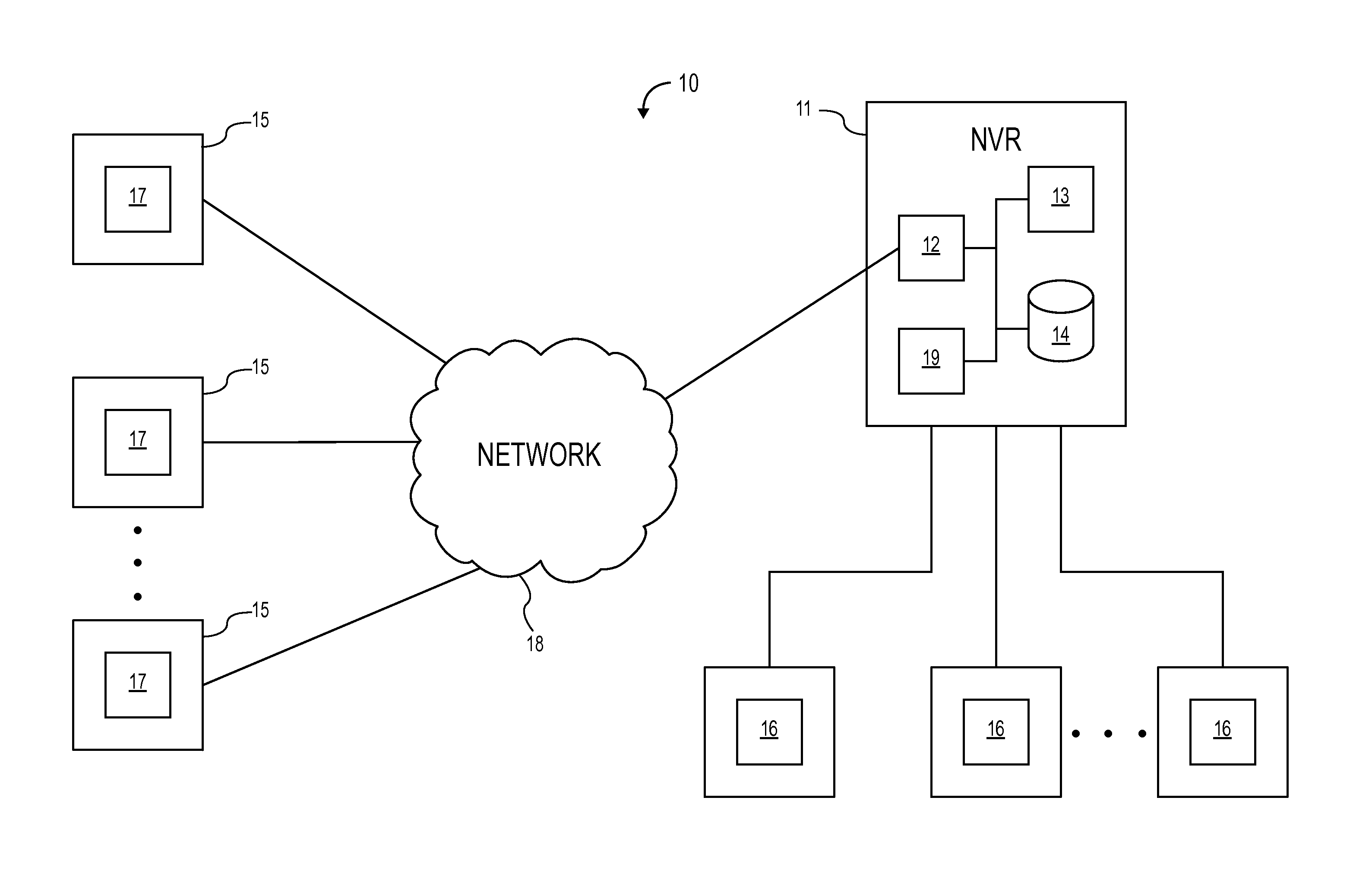
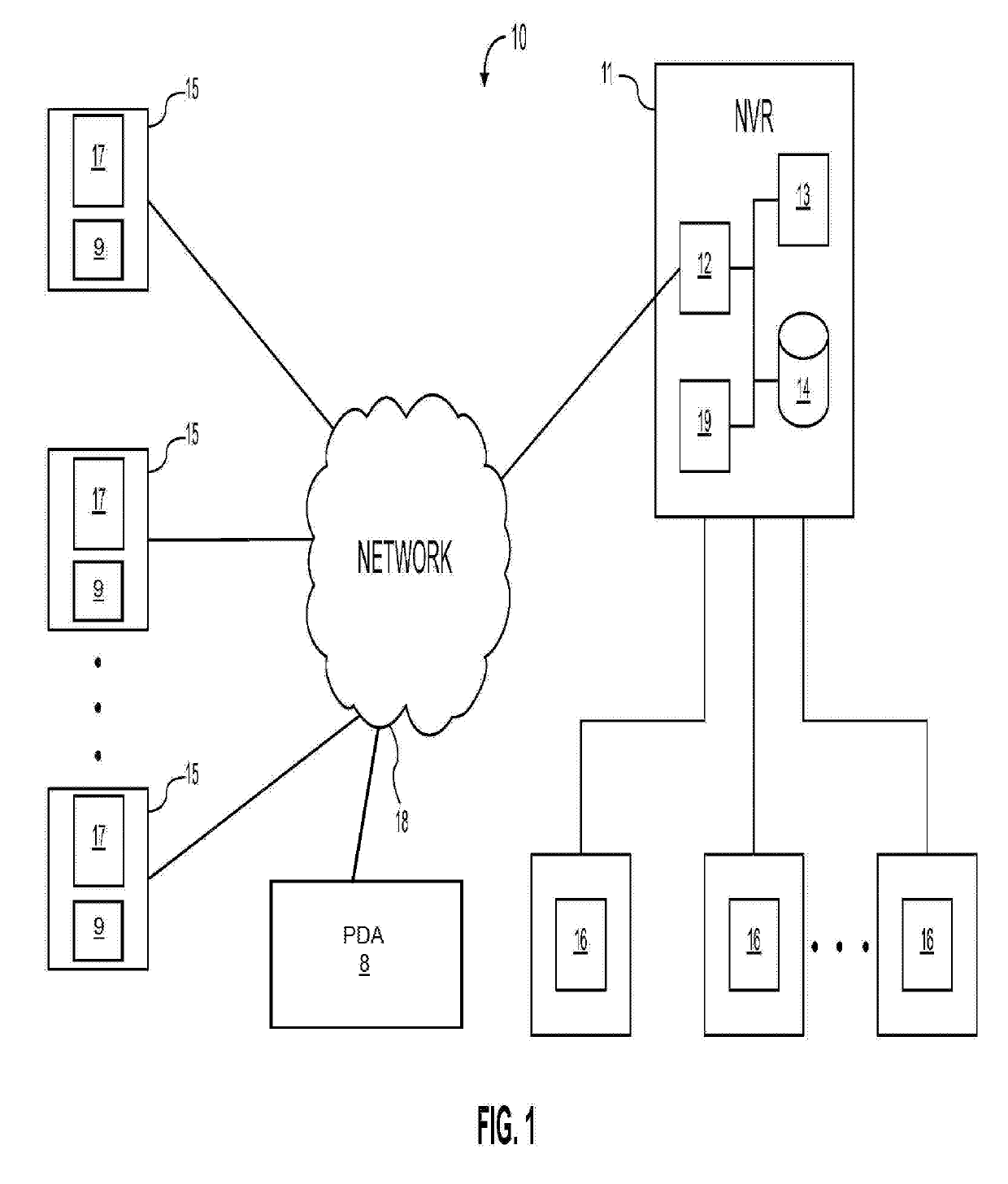
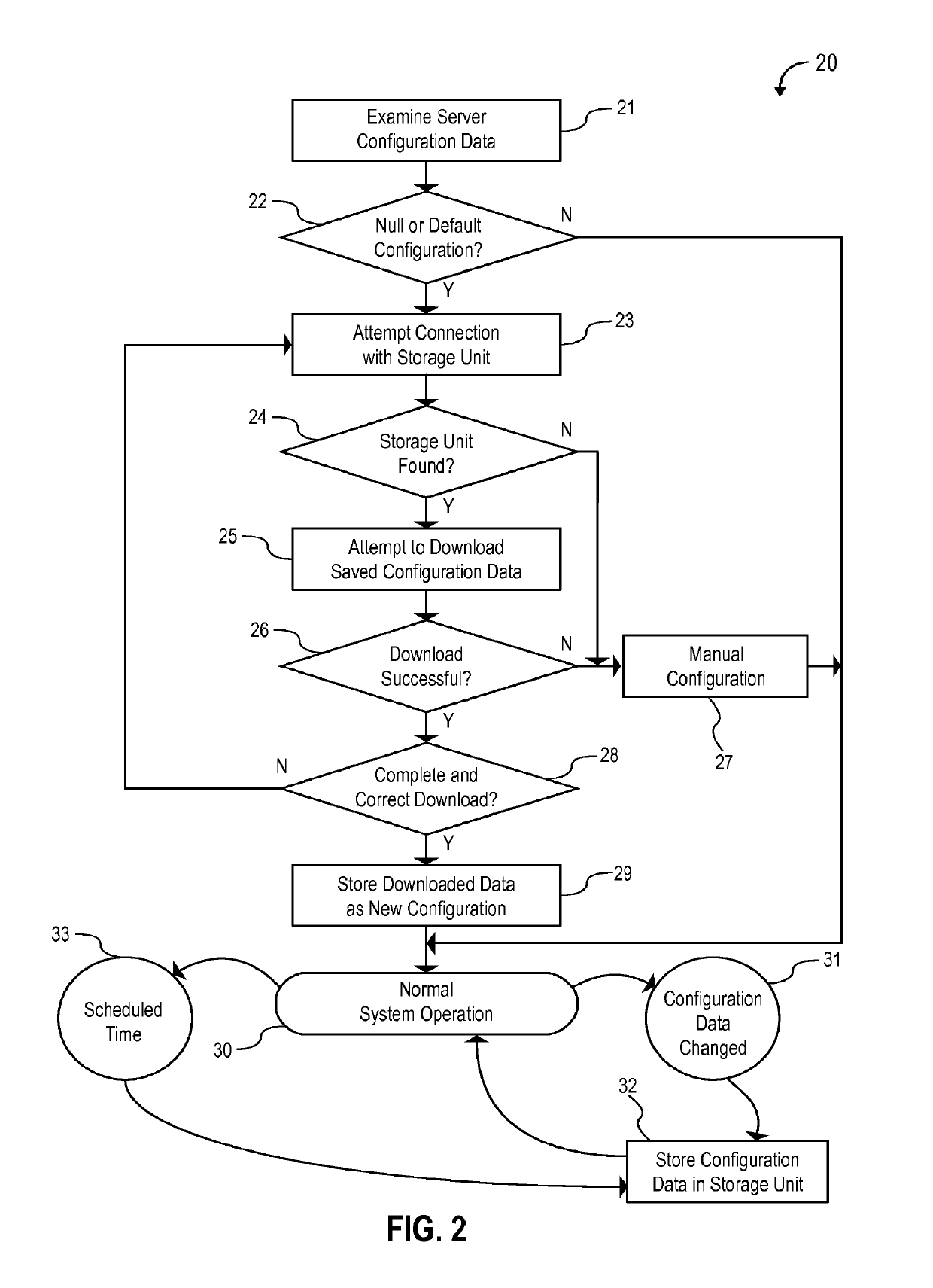
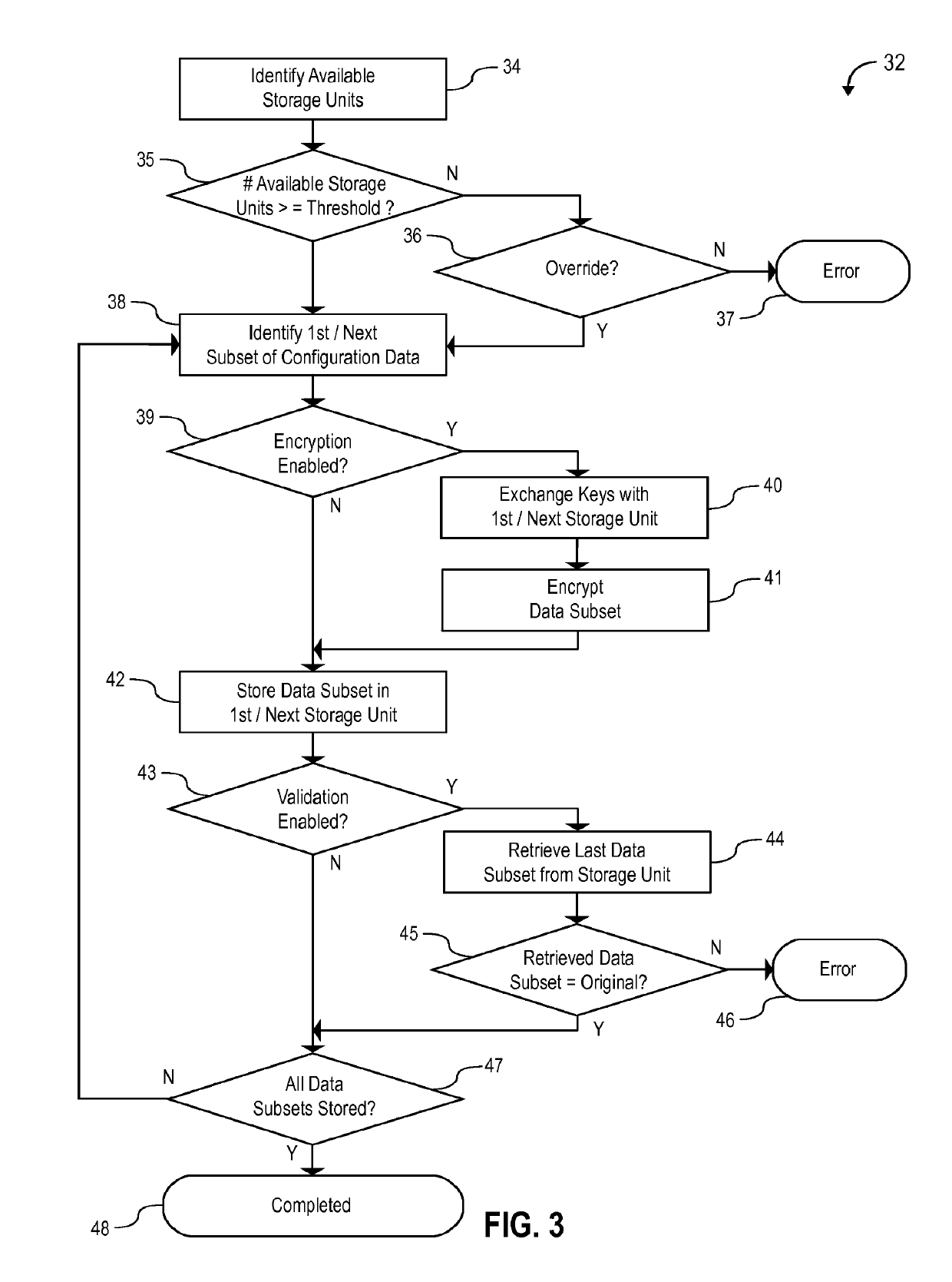
ActiveUS20140270682A1Less effortQuick changeTelevision system detailsColor television detailsVideo monitoringHuman interaction
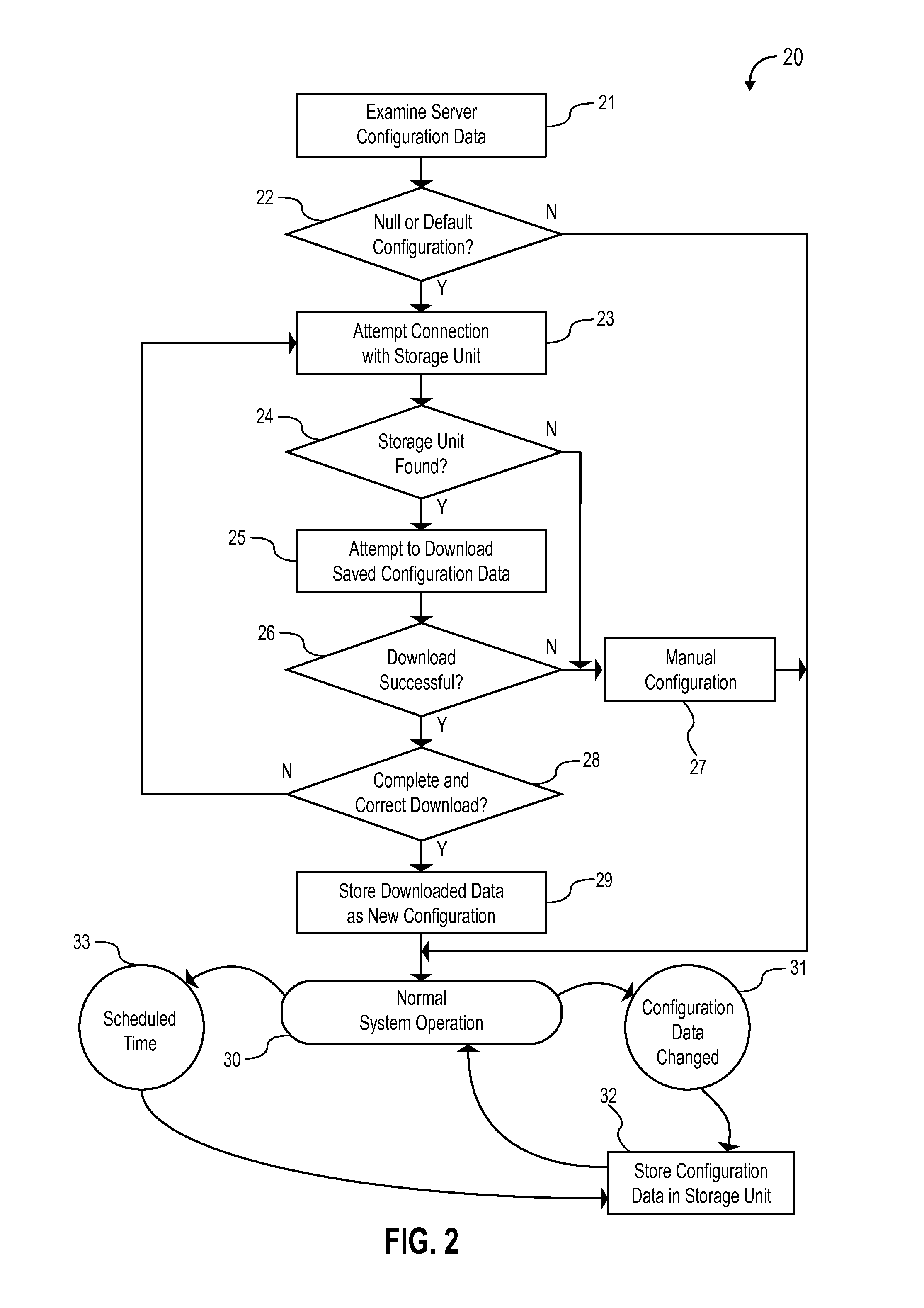
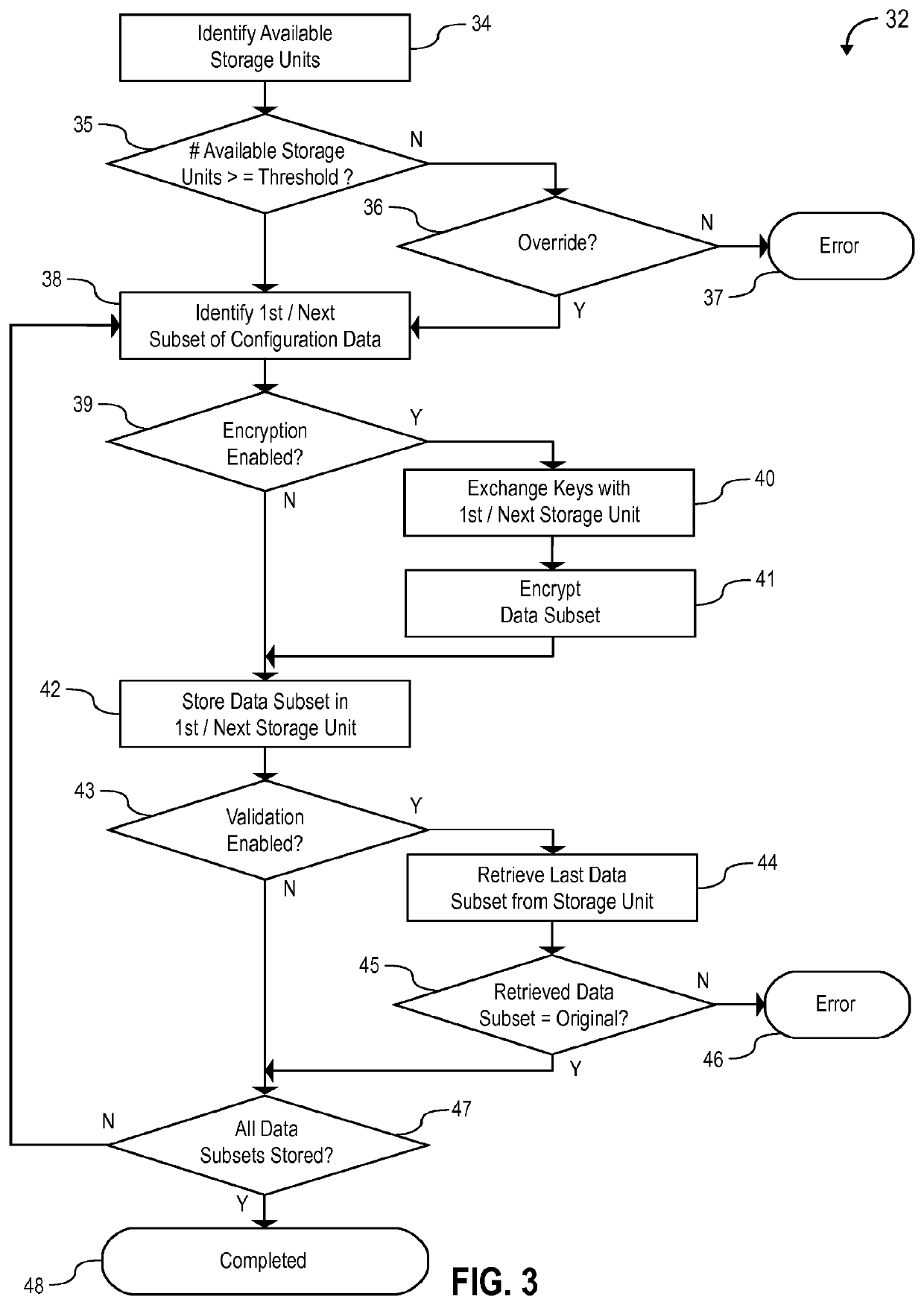
A self-healing video surveillance system is described. The self-healing video surveillance system includes one or more surveillance cameras that are configured to store configuration data of a network video recorder in operable communication with the surveillance cameras. The network video recorder includes configuration data, and a module configured to store the configuration data on the surveillance cameras and / or retrieve configuration data stored on the surveillance cameras. A new network video recorder introduced into the network retrieves the stored configuration data to self-configure with minimal or no human interaction. In embodiments, configuration data is distributed among a plurality of surveillance cameras, and may be stored in encrypted format.
Owner:CAREY JAMES
Capacity load type probe, and test jig using the same
InactiveUS20050088189A1Avoid noiseRemove RF noiseElectrical measurement instrument detailsElectrical testingCapacitanceEquipment under test
A plurality of probes such as a signal probe (3) and a power supply probe (4) are provided into a metal block (1) so as to penetrate. Each of the probes has a movable pin (11). A tip of the movable pin is projecting from one surface of the metal block (1). And a projection length of the tip is variable. A DUT 20 is pressed onto the surface of the metal block (1) to contact between electrode terminals (21 to 24) and tips of the probes to test characteristics of the DUT. At least one of the probes is capacity loaded probe having a capacitor by providing a dielectric layer and a metal film to peripheral of the probe. As a result, noise can be removed reliably. Additionally, when the capacity loaded probe is used as the power supply probe, a voltage drop is reduced at the power supply terminal in a case of change of the output.
Owner:YOKOWO CO LTD
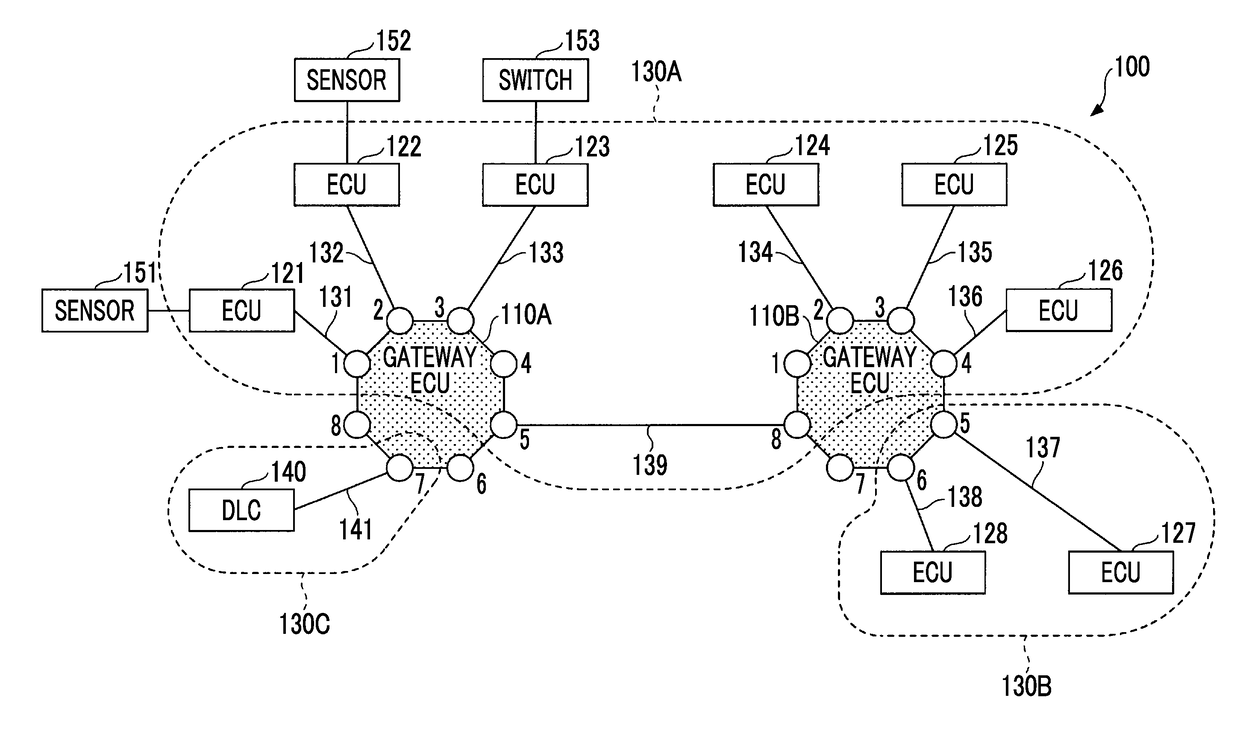
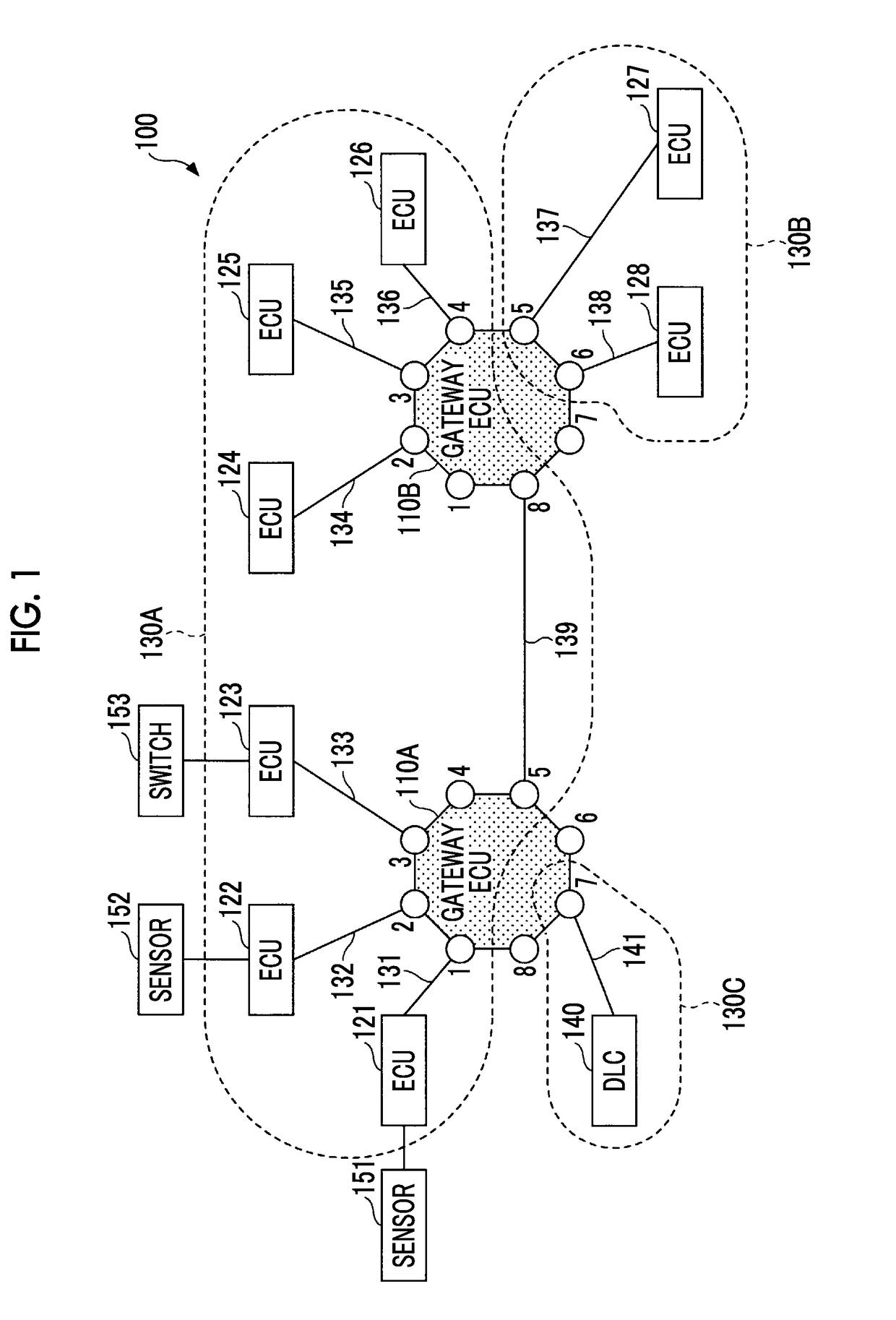
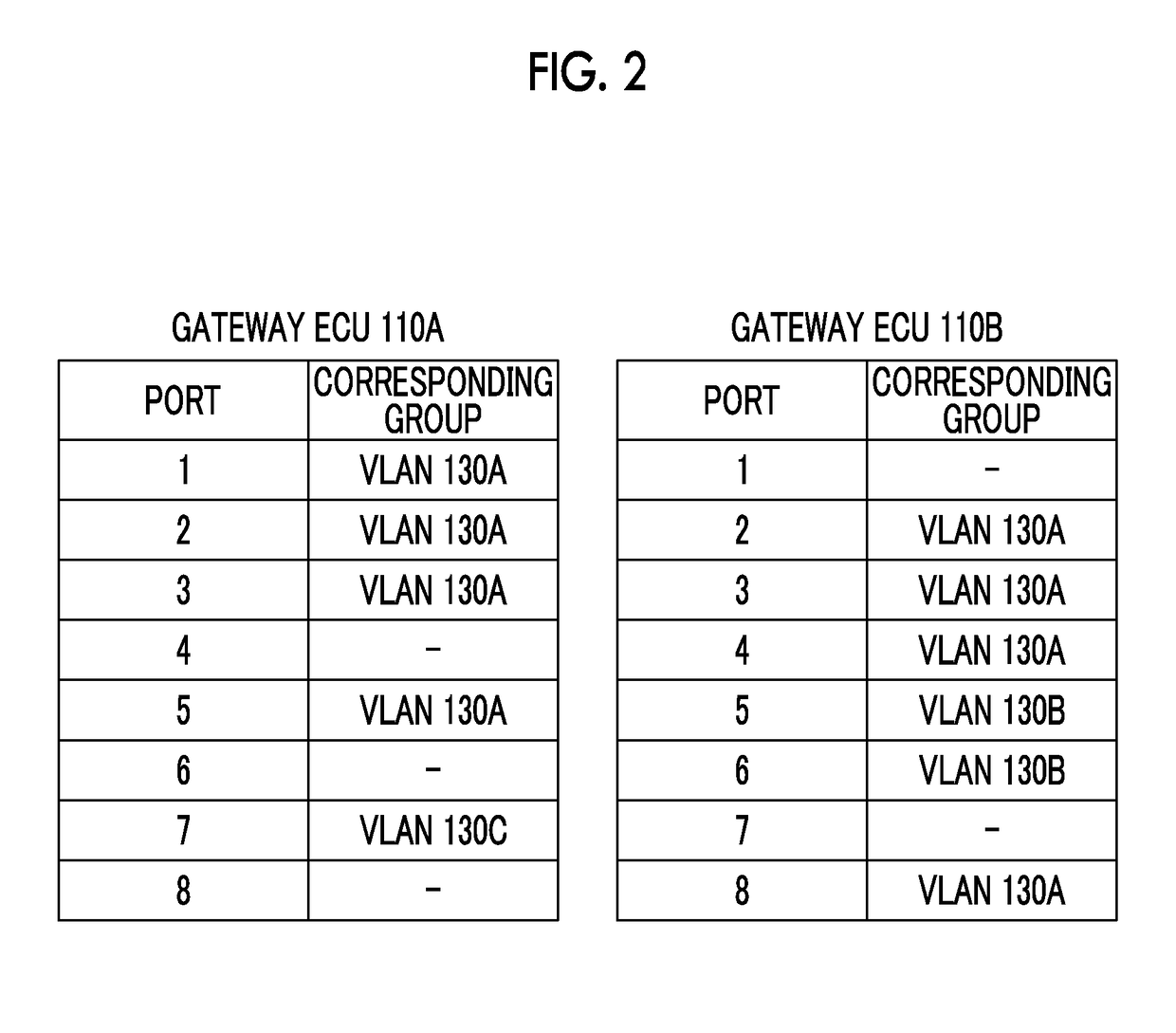
In-vehicle network system
ActiveUS20180131700A1Decrease in communication speedSafety levelNetwork connectionsElectric/fluid circuitIn vehiclePeripheral
An in-vehicle network system includes a plurality of first controllers; a plurality of first communication lines, the first communication lines being respectively connected to the first controllers; a connector that connects an external device or a wireless communication device; a connection communication line that is connected to the connector; and a first relay device that relays between the first communication lines and the connection communication line. The first relay device is configured to determine whether a security level in data communication between the first controllers is increased according to a type of the external device or a communication state of the wireless communication device in a state in which the external device or the wireless communication device is connected to the connector, and the first relay device is configured to increase the security level when the first relay device determines that the security level is increased.
Owner:TOYOTA JIDOSHA KK
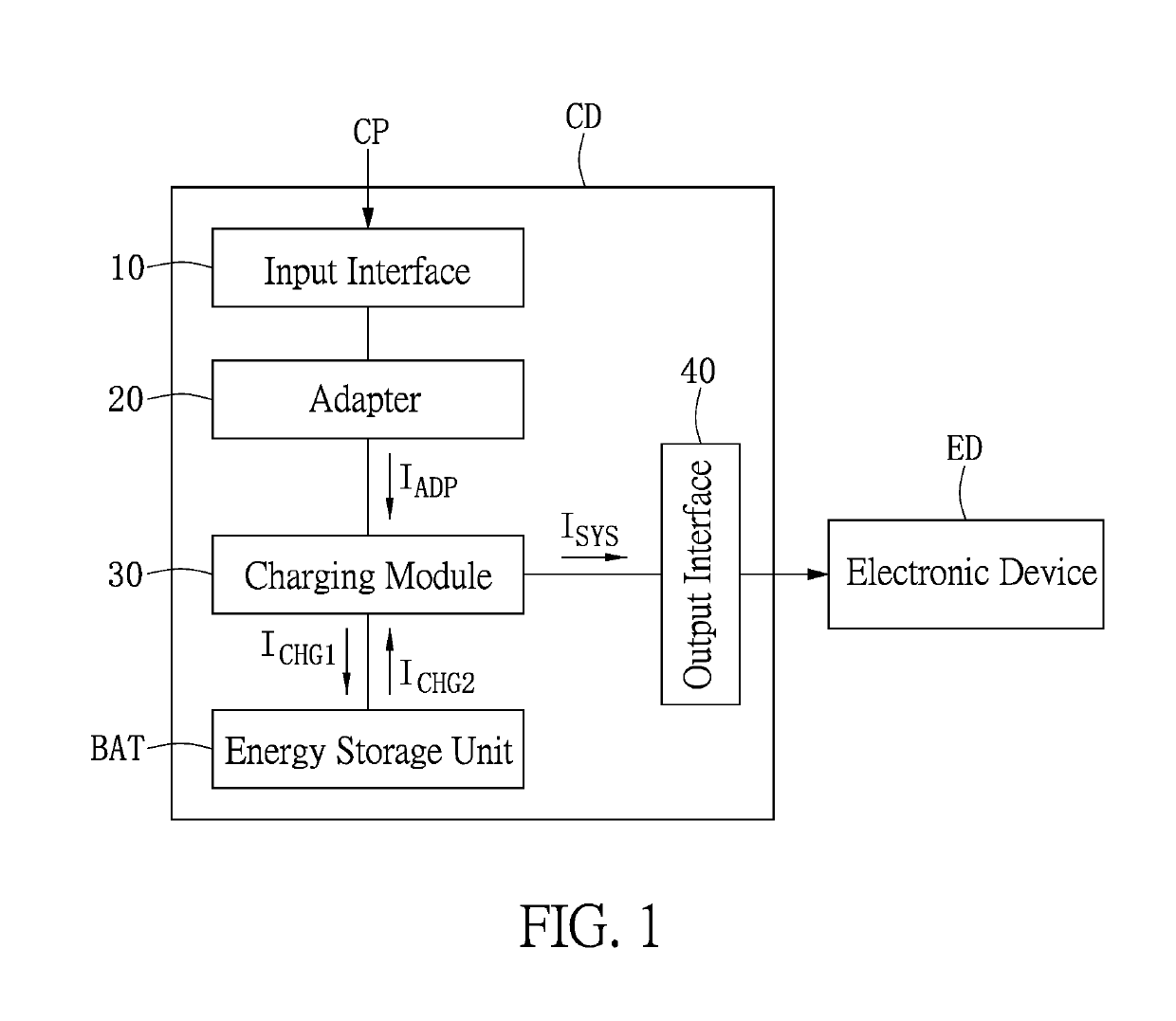
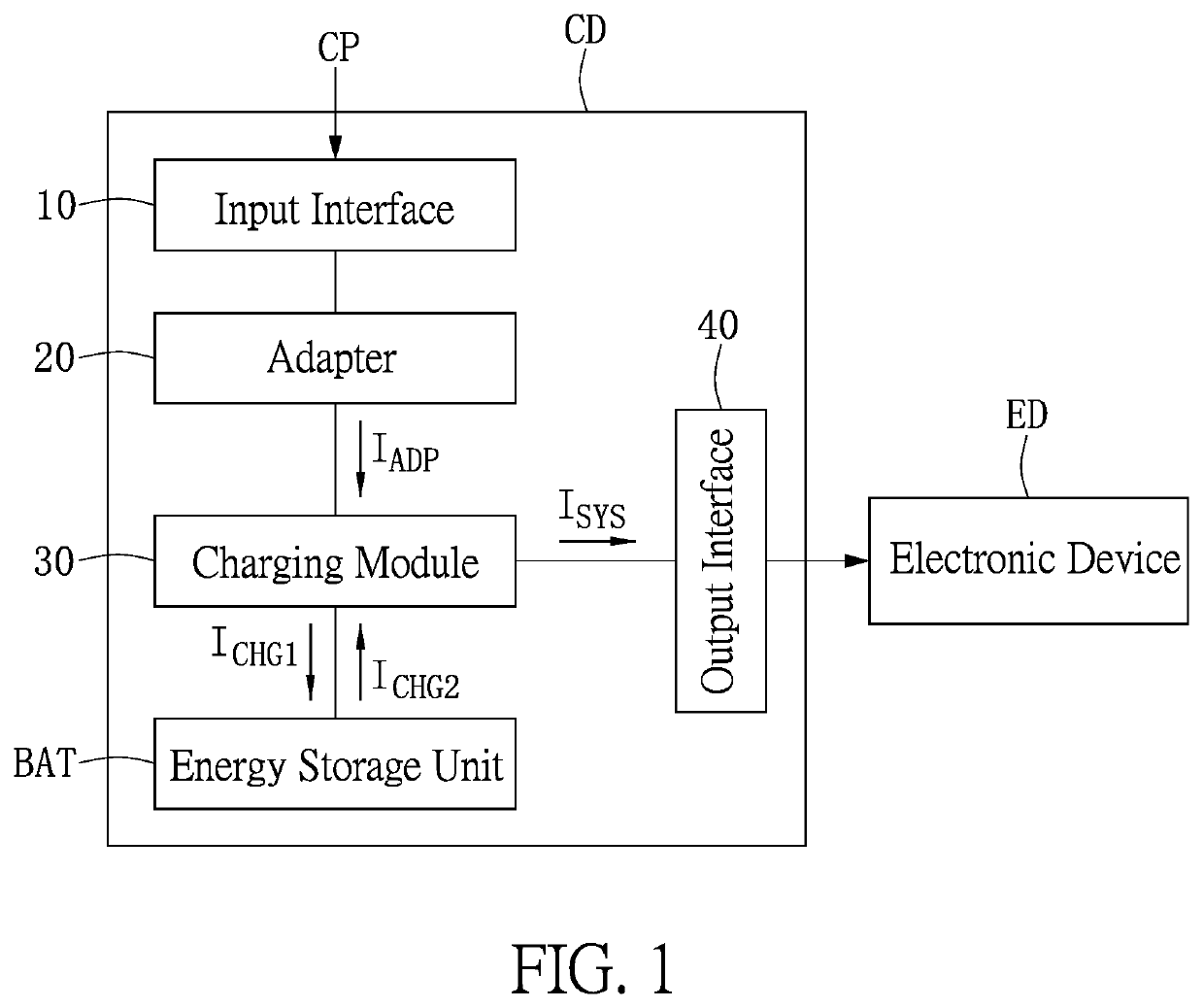
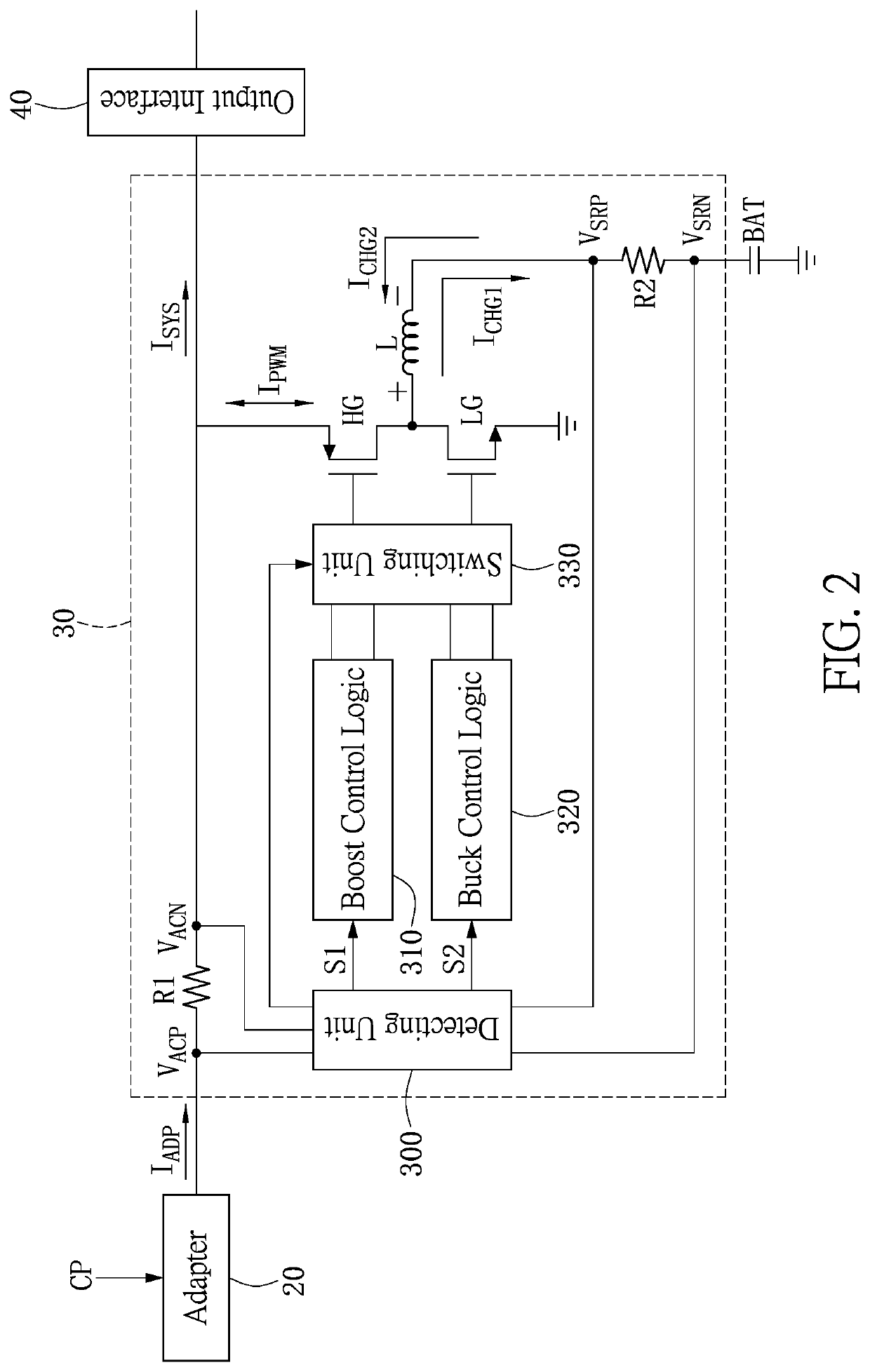
Charging device and control method thereof
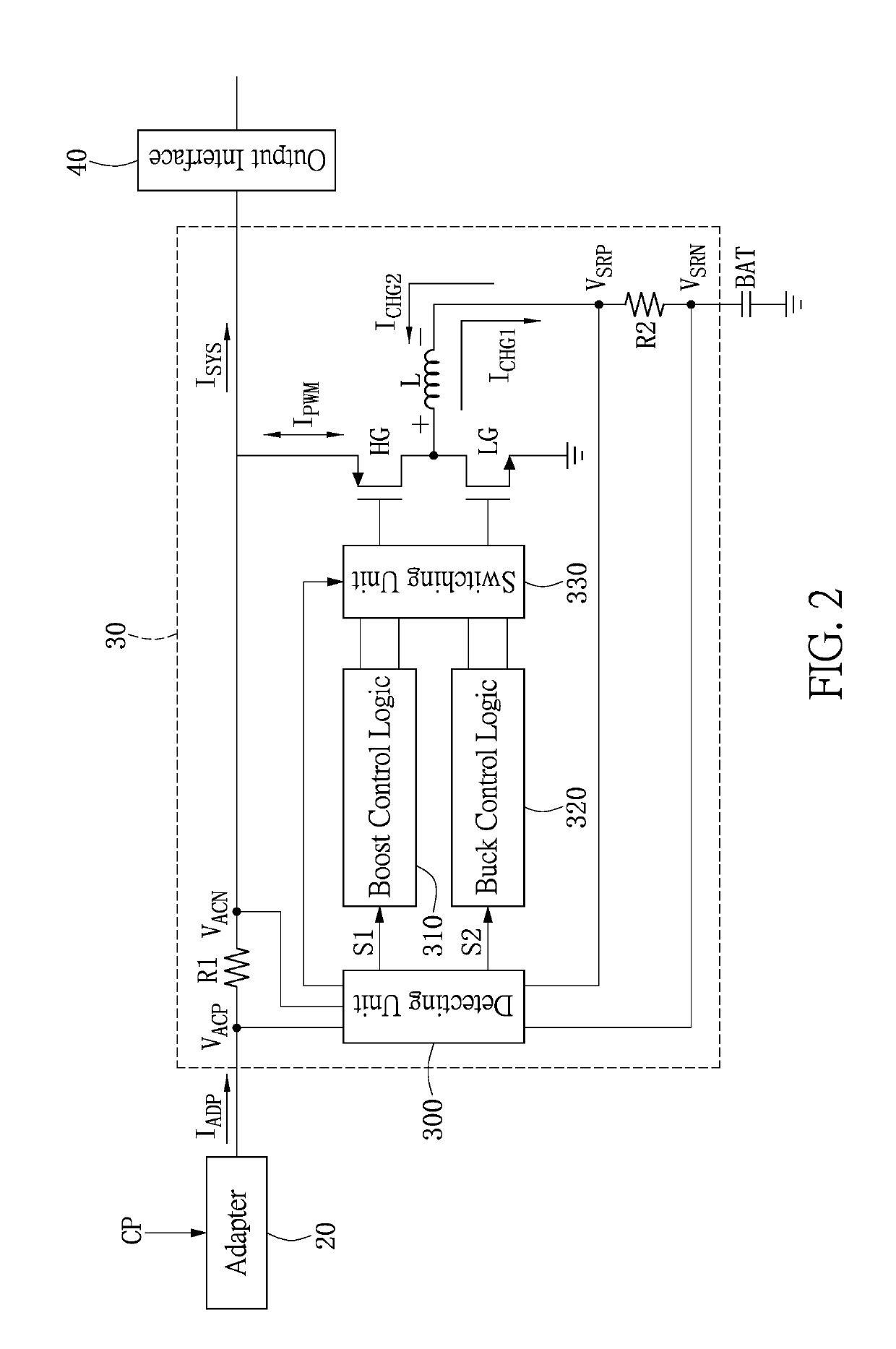
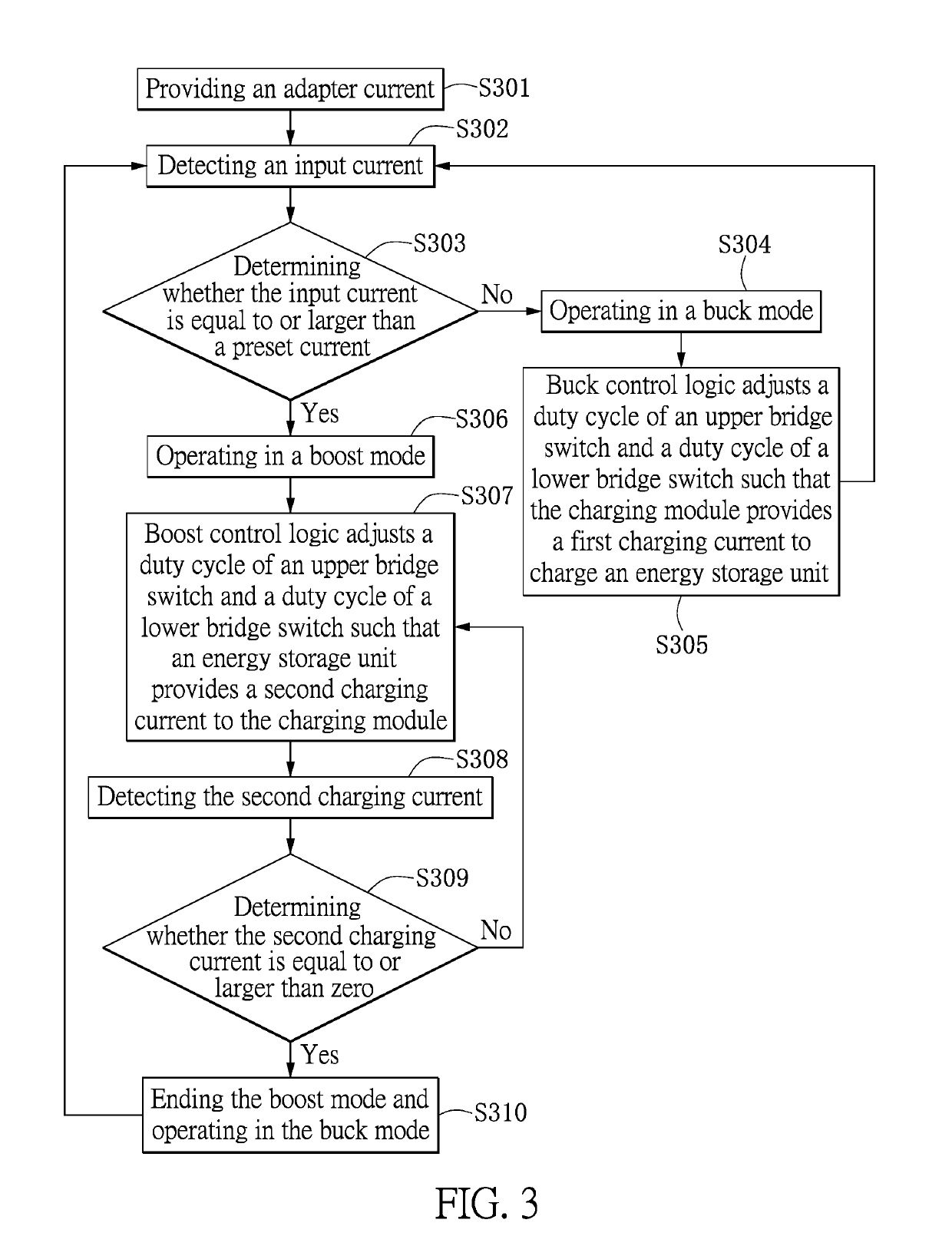
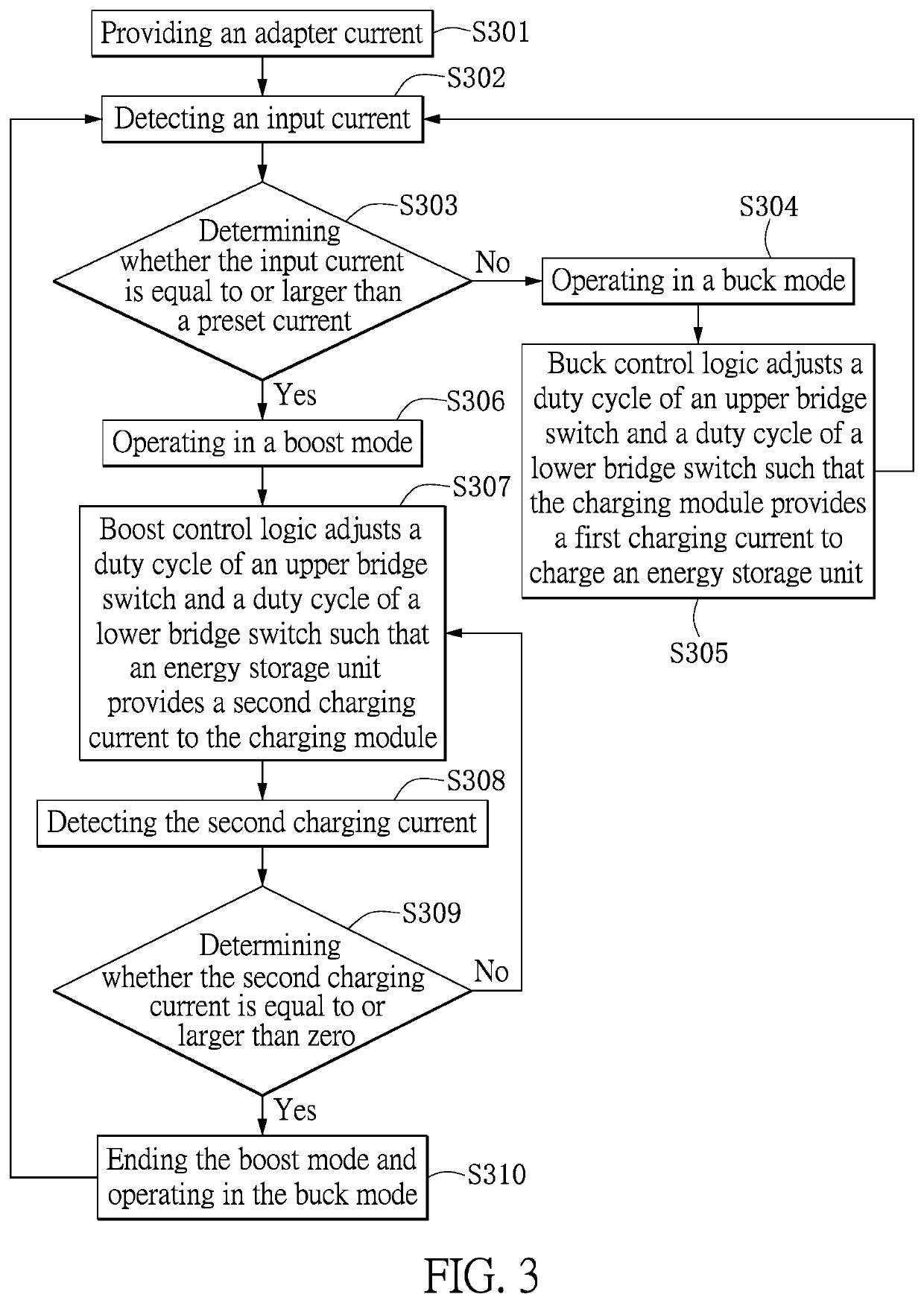
A charging device and a control method thereof are provided. The charging device includes an adapter, an energy storage unit and a charging module. The adapter provides an adapter current. The charging module receives the adapter current and provides a first charging current to charge the energy storage unit, or an output current to charge an electronic device. When the input current is larger than a first preset current and the first charging current is equal to or less than a third preset current, the charging module operates in a boost mode, such that the energy storage unit provides a second charging current to the charging module. When the second charging current is larger than the third preset current, the charging module enters a buck mode such that the energy storage unit is charged by the first charging current.
Owner:ANPEC ELECTRONICS CORPORATION
Method for assisting a single-engine rotorcraft during an engine failure
ActiveUS20200277072A1Limited impact speedEarly detectionSynchronous motors startersAircraft health monitoring devicesFlight vehicleElectrical energy storage
An assistance method for assisting a pilot of a single-engined rotary-wing aircraft during a flight phase in autorotation, the aircraft including a hybrid power plant provided with a main engine, with an electric machine, with a main gearbox, and with an electrical energy storage device. The aircraft also includes a main rotor driven by the hybrid power plant. In the method, during a flight, operation of the main engine is monitored in order to detect a failure, in particular by means of a drop in power on the main rotor, then, when a failure of the main engine is detected, the electric machine is controlled to deliver auxiliary power We to the main rotor, making it possible to assist a pilot of the aircraft in performing the flight phase in autorotation following the failure.
Owner:EUROCOPTER
Detection device to identify markers dissolved in a liquid by means of a measurement of resistivity variation, detection method and use of marker and detection device
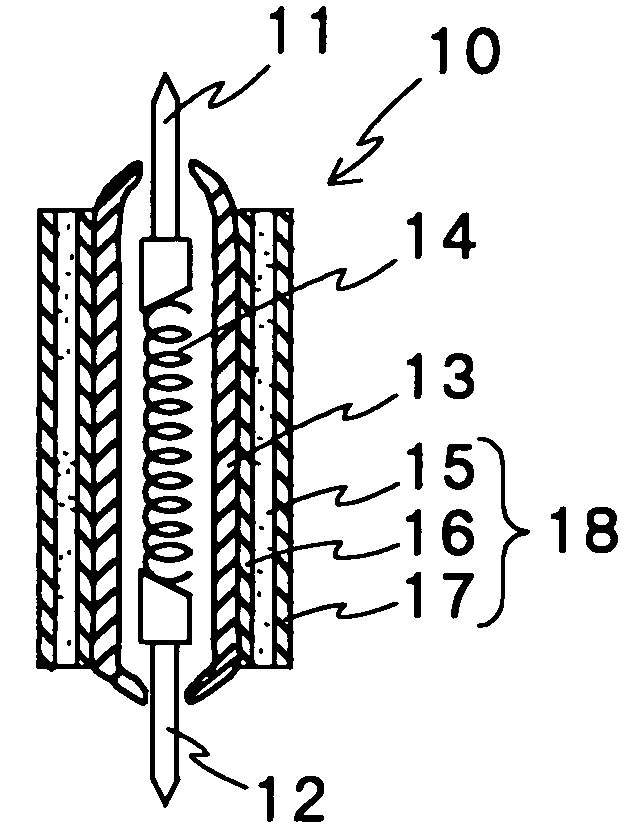
ActiveUS10175221B2Improve solubilityEasy to identifyHeating or cooling apparatusResistance/reactance/impedenceChemical reactionMeasurement device
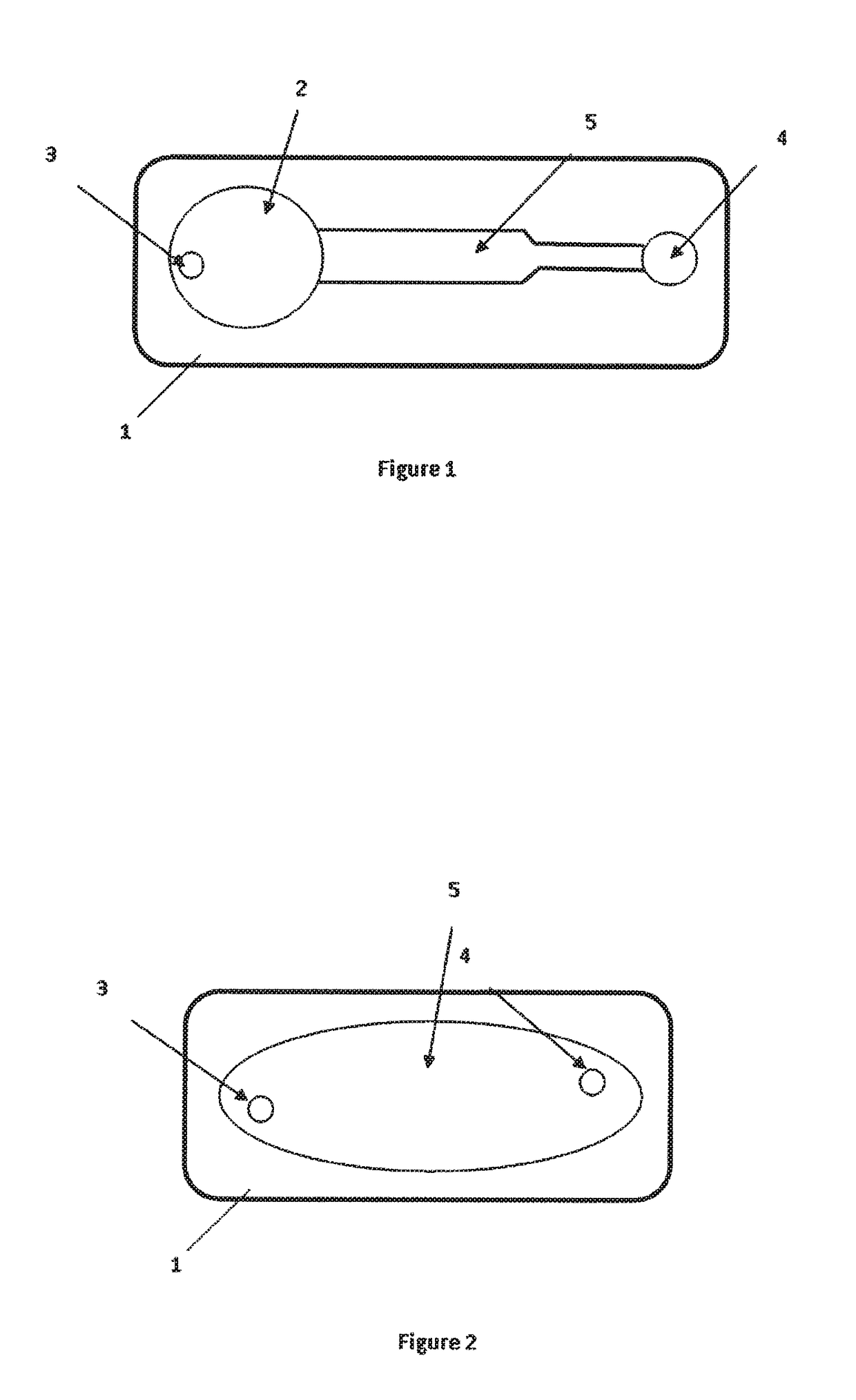
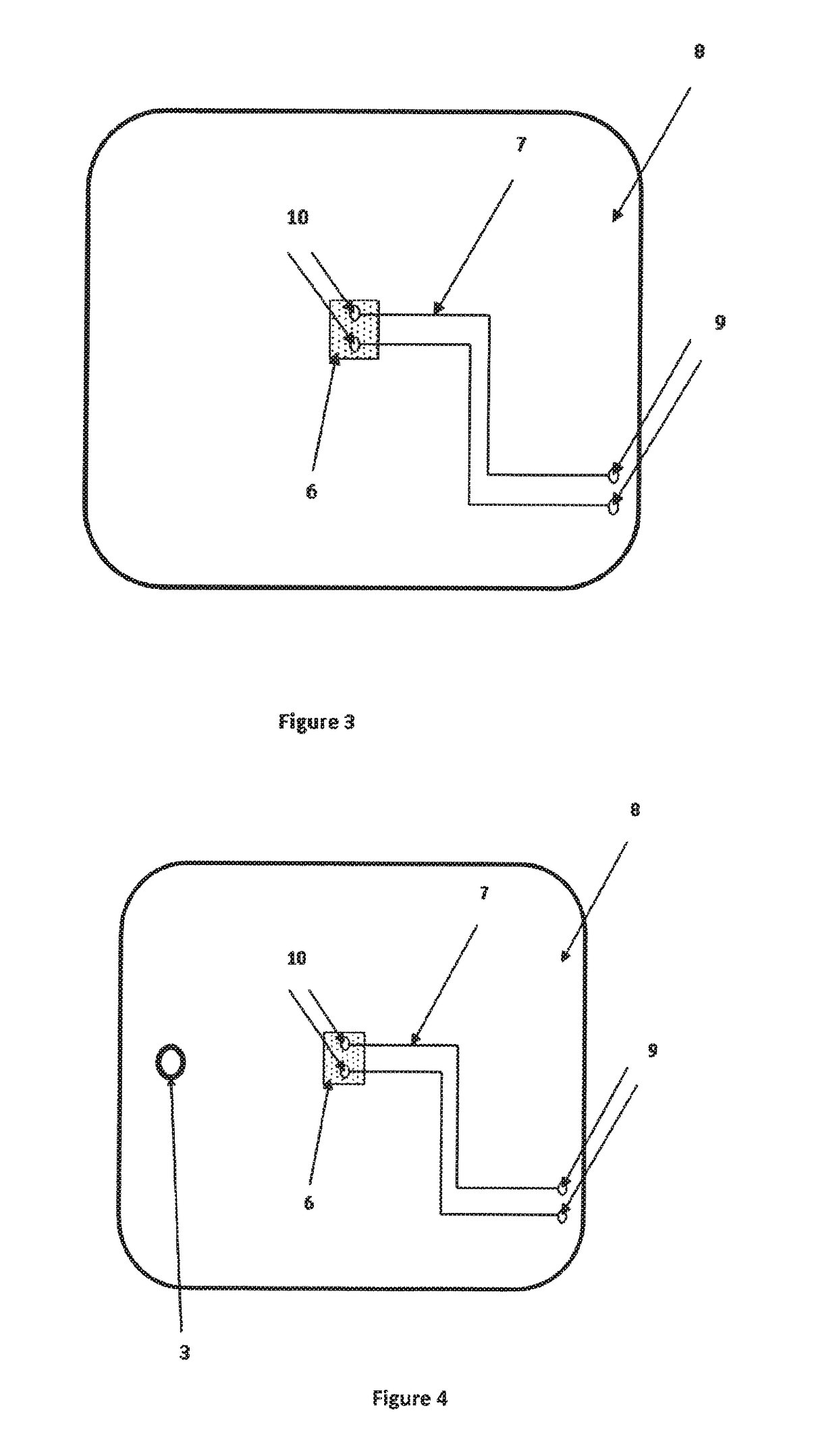
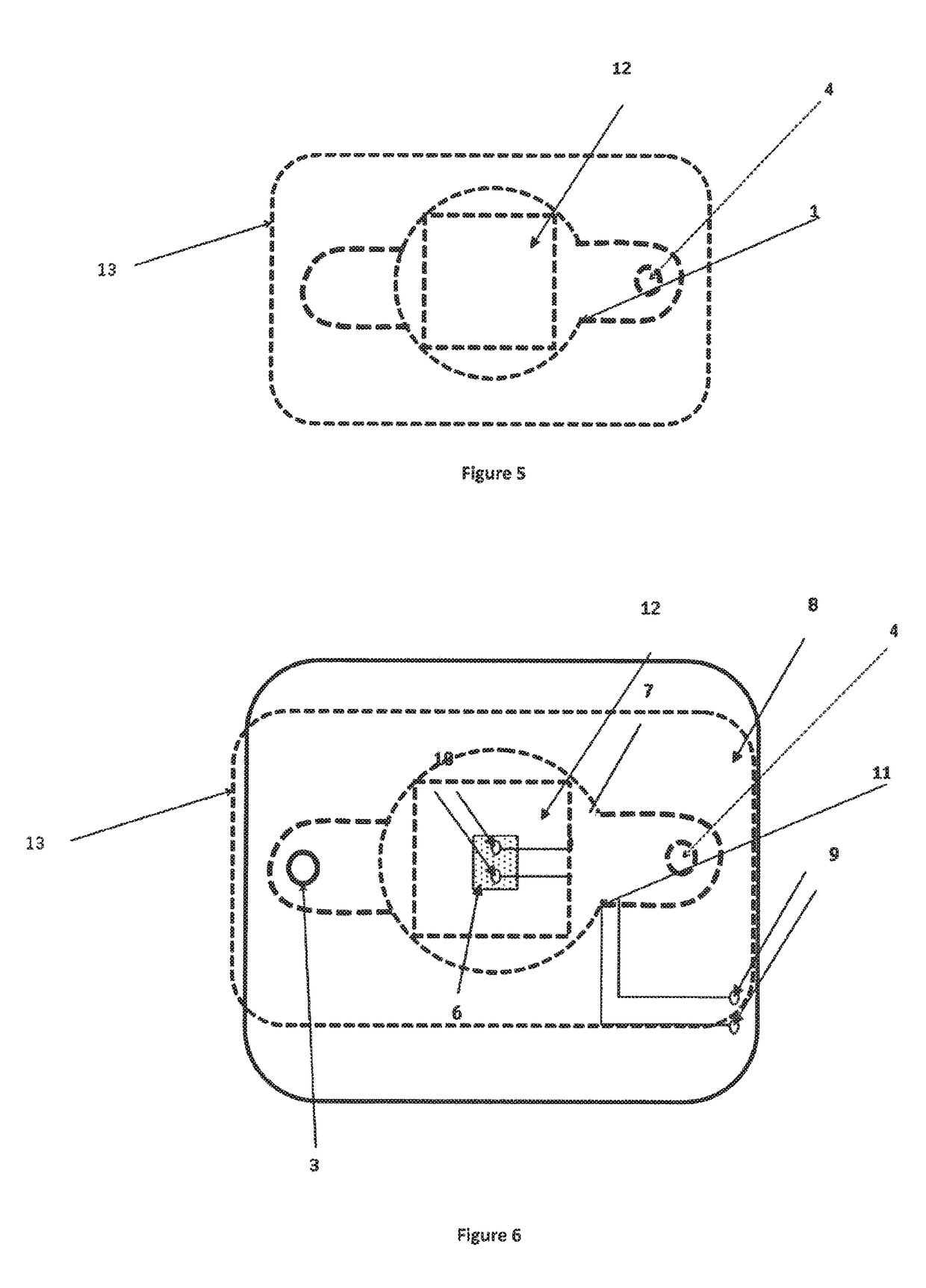
A detection device for detecting a marker in a liquid, preferably a fuel, comprising:a reaction chamber 5, provided with a de-dopable conductive polymer 6 building a path between two conductive pads 10 connected to a resistivity measurement device,wherein the de-dopable conductive polymer 6 is able to be de-doped by a chemical reaction with the marker, changing its resistivity.
Owner:SICPA HLDG SA
Self-healing video surveillance system
ActiveUS9571800B2Rapidly and conveniently self-configure and “ self-heal ”Quick changeTelevision system detailsColor television detailsHuman interactionSelf-healing
A self-healing video surveillance system is described. The self-healing video surveillance system includes one or more surveillance cameras that are configured to store configuration data of a network video recorder in operable communication with the surveillance cameras. The network video recorder includes configuration data, and a module configured to store the configuration data on the surveillance cameras and / or retrieve configuration data stored on the surveillance cameras. A new network video recorder introduced into the network retrieves the stored configuration data to self-configure with minimal or no human interaction. In embodiments, configuration data is distributed among a plurality of surveillance cameras, and may be stored in encrypted format.
Owner:CAREY JAMES
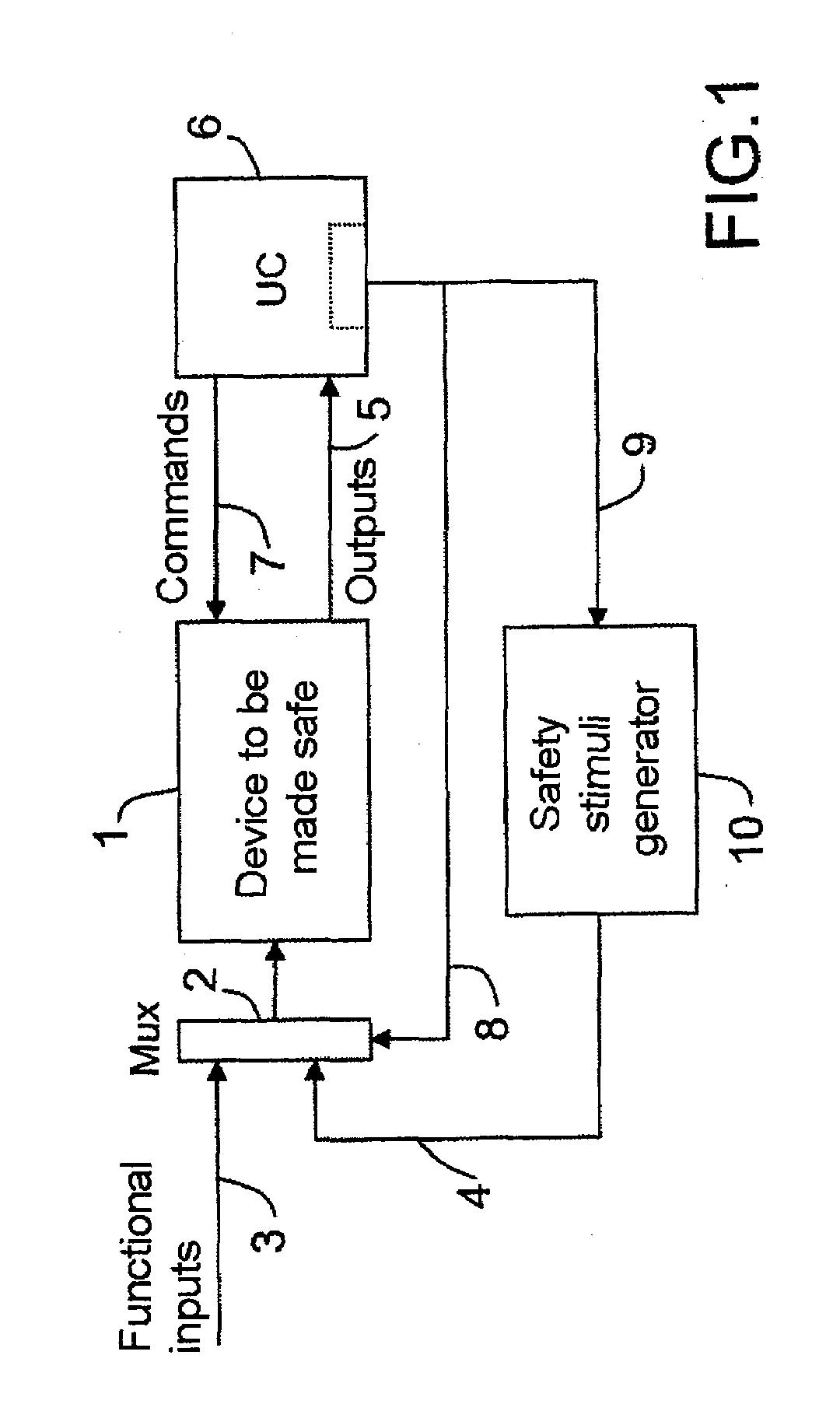
Method of improving the integrity and safety of an avionics system
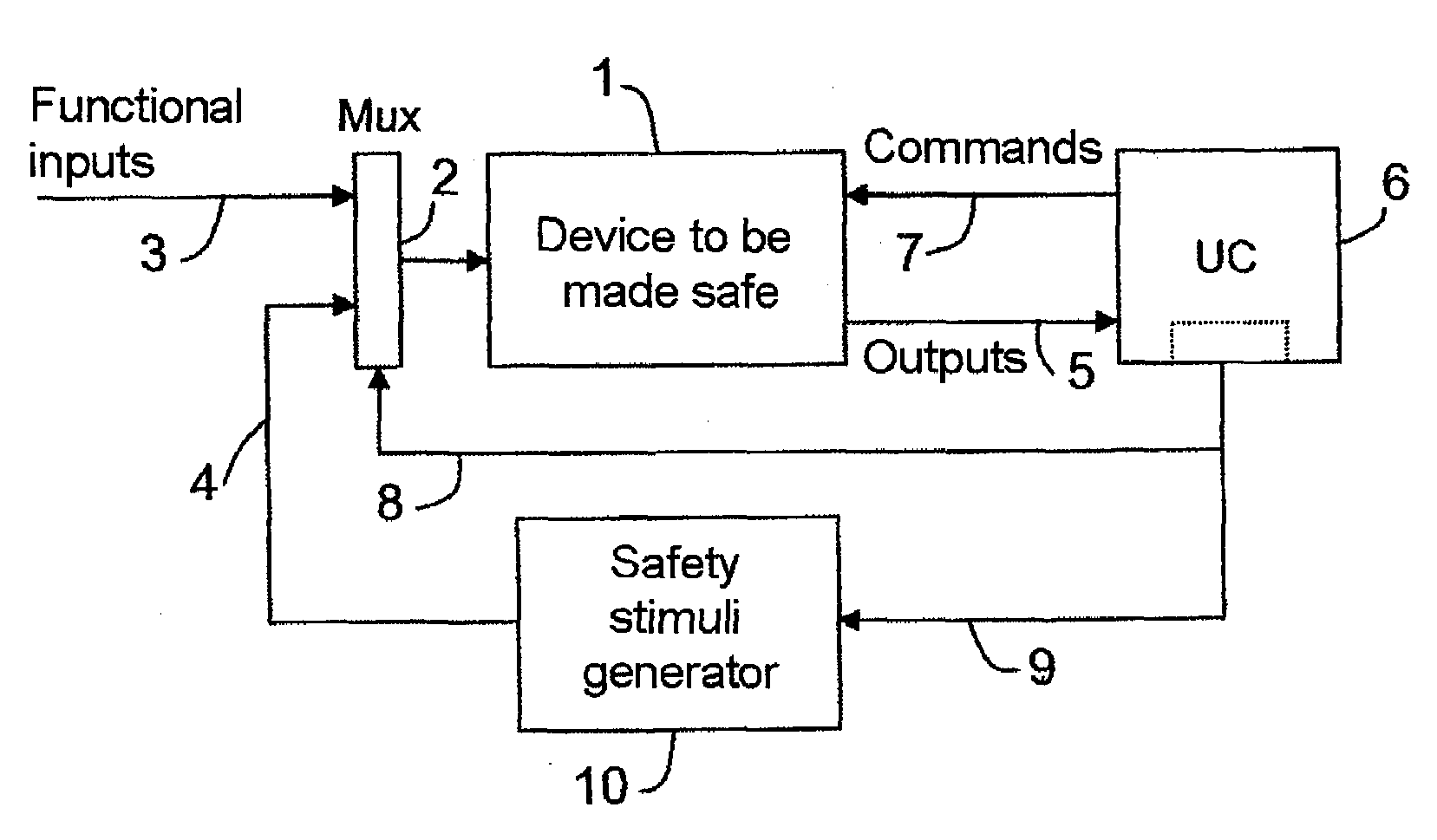
InactiveUS20090070635A1Improve integrityImprove securityError detection/correctionTesting/monitoring control systemsEngineeringReliability engineering
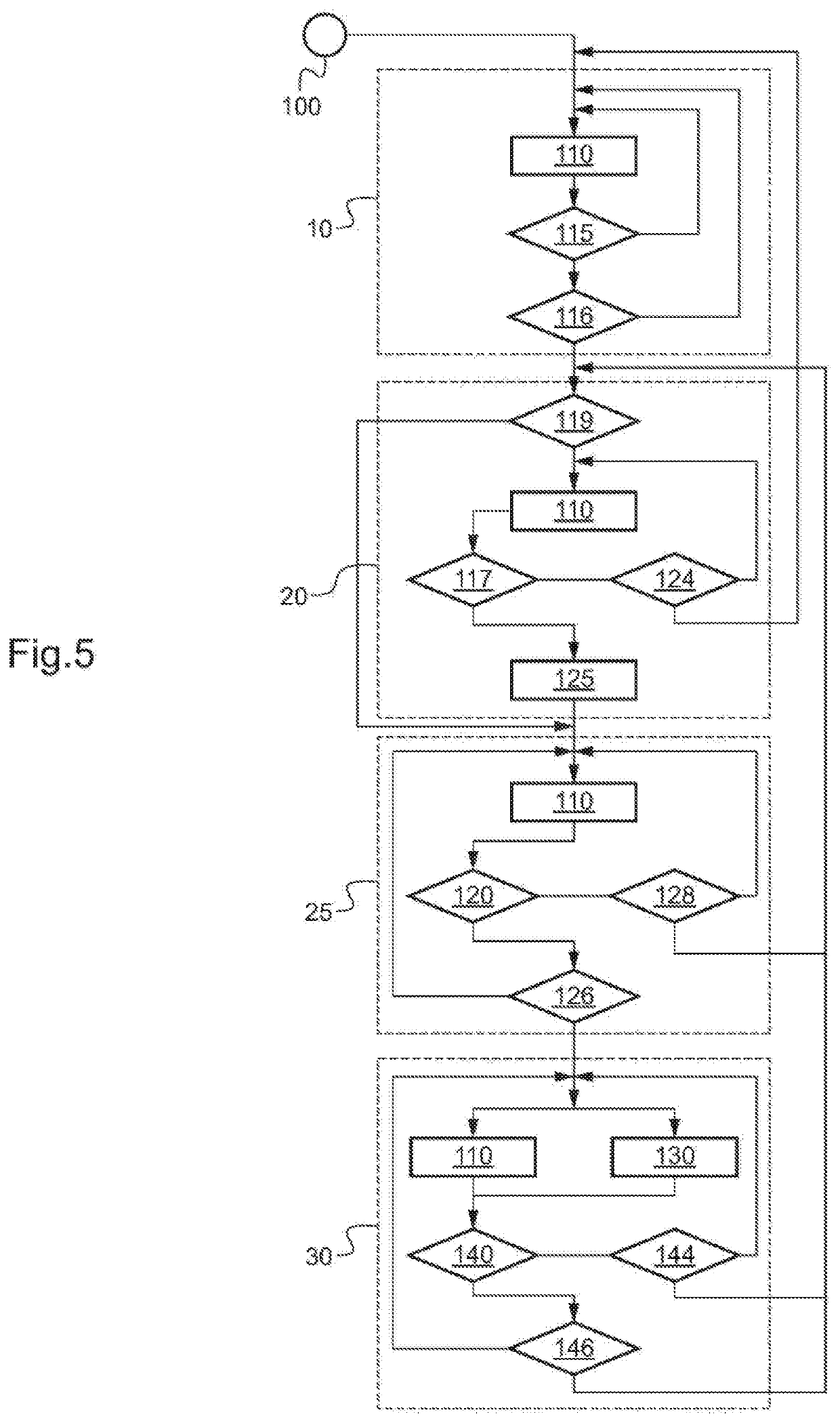
The present invention relates to a method of improving the integrity and safety of a system, this method making it possible, on the one hand, to detect and to locate an anomaly of a system, and on the other hand to estimate the impact of such an anomaly on the degradation of performance, with a view to attaining the safety level required and to making the data provided by this system safe, and this method is characterized in that it consists, in a system comprising sub-assemblies, in monitoring the proper operation of sub-assemblies by checking their respective transfer functions in the operational mode with the aid of stimuli dispatched to these sub-assemblies.
Owner:THALES SA
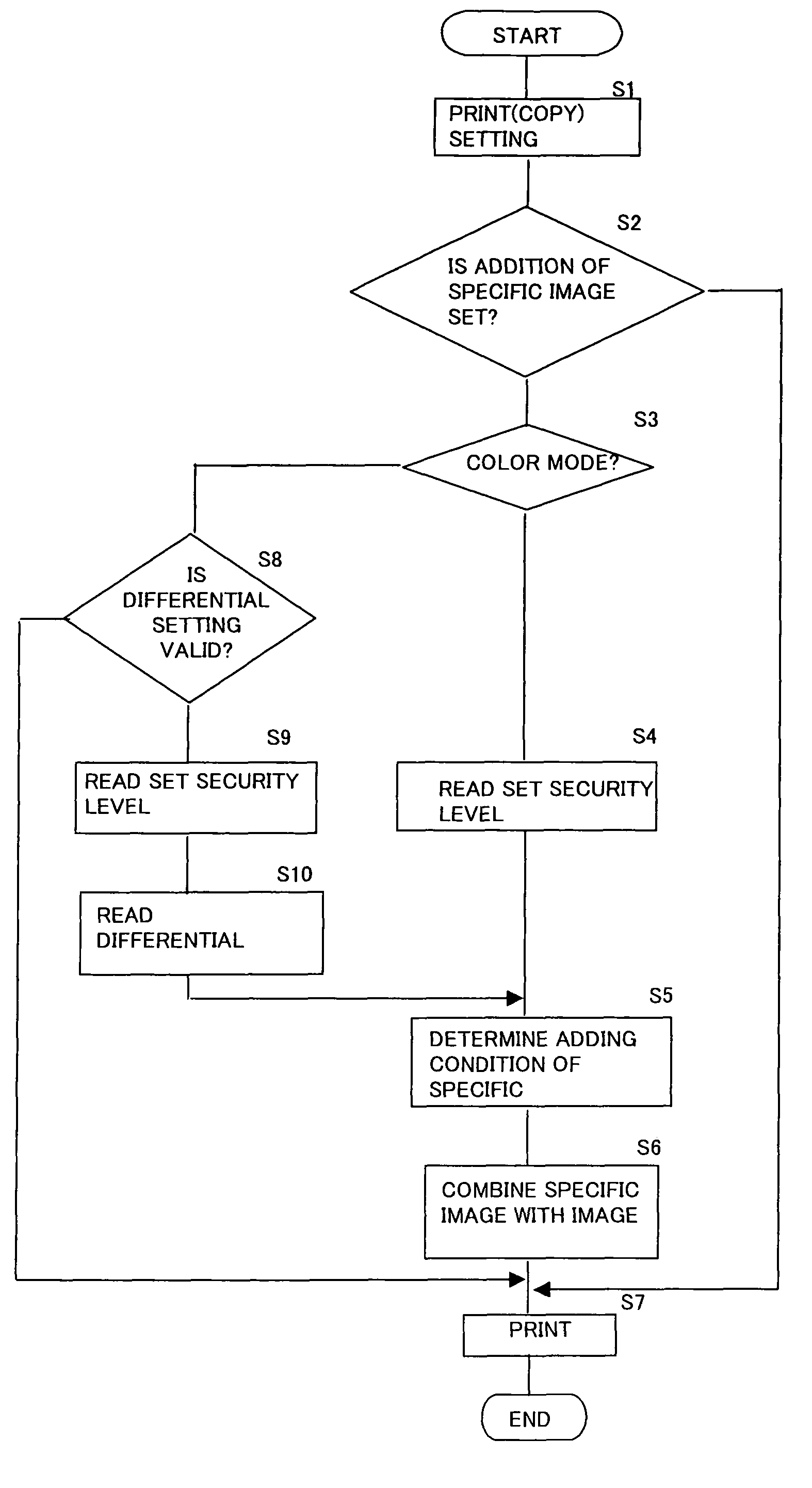
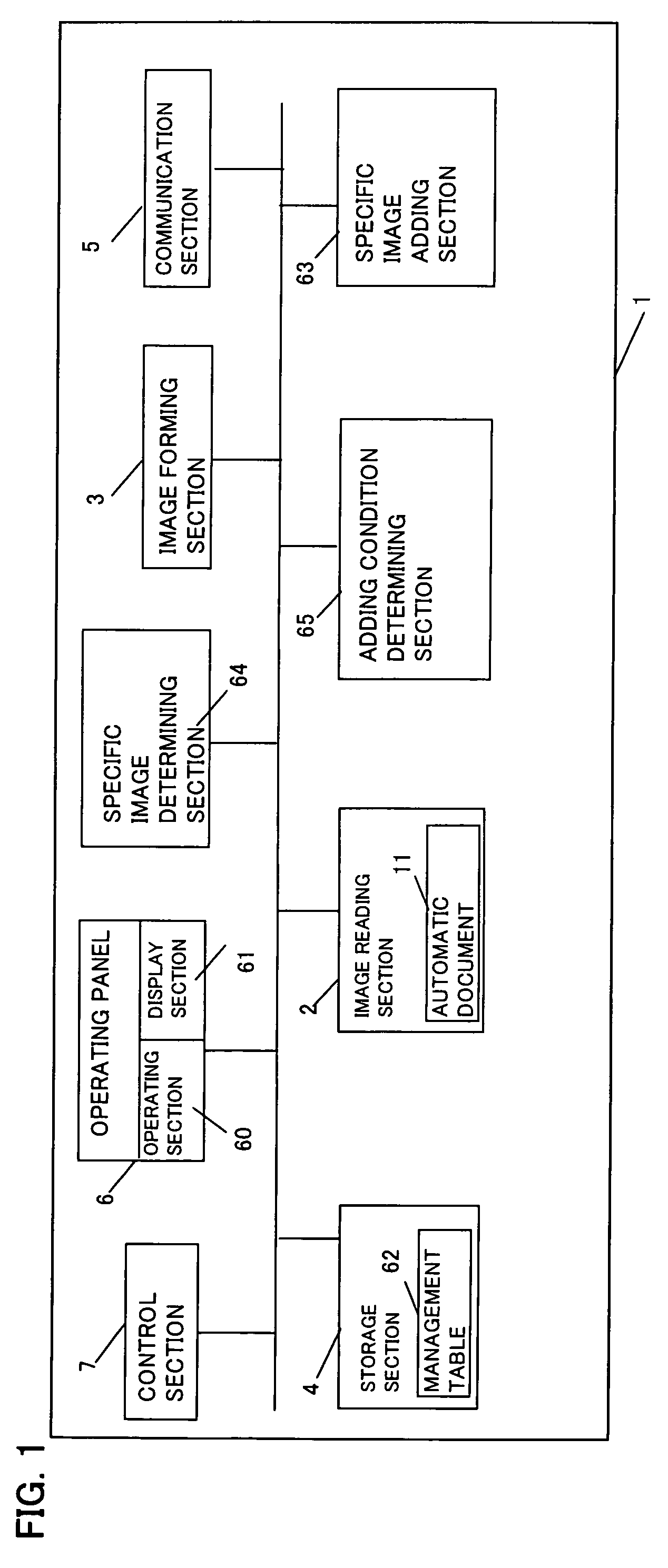
Image processing apparatus for adding different specific images to image data in color and black-and-white modes
ActiveUS7916320B2High densityLow densityDigitally marking record carriersDigital computer detailsImaging processingDocumentation
An image processing apparatus for preventing unauthorized uses of image data by allowing the addition of a specific image in a black-and-white mode even when it is set that a specific image is added in a color mode. When a document is copied, a control section determines whether the apparatus is in a color mode or a black-and-white mode. When in a black-and-white mode, an adding condition determining section reads a set security level and a differential value and determines a security level lower than the one in a color mode. Based on the security level in a black-and-white mode, an adding condition of a specific image is determined. The specific image adding section adds a specific image different from the one in a color mode based on the adding condition. A black-and-white image added with the specific image is printed.
Owner:SHARP KK
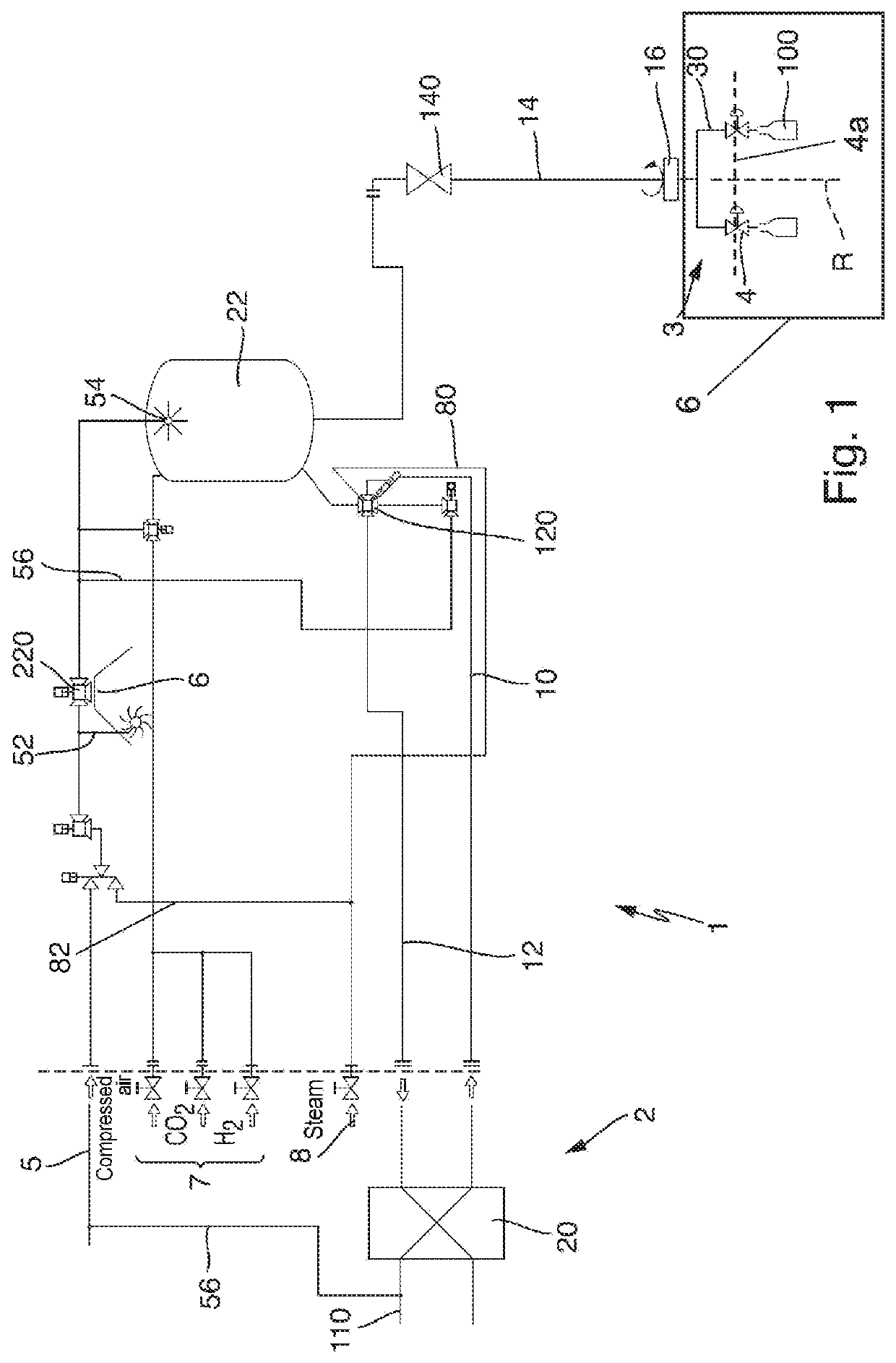
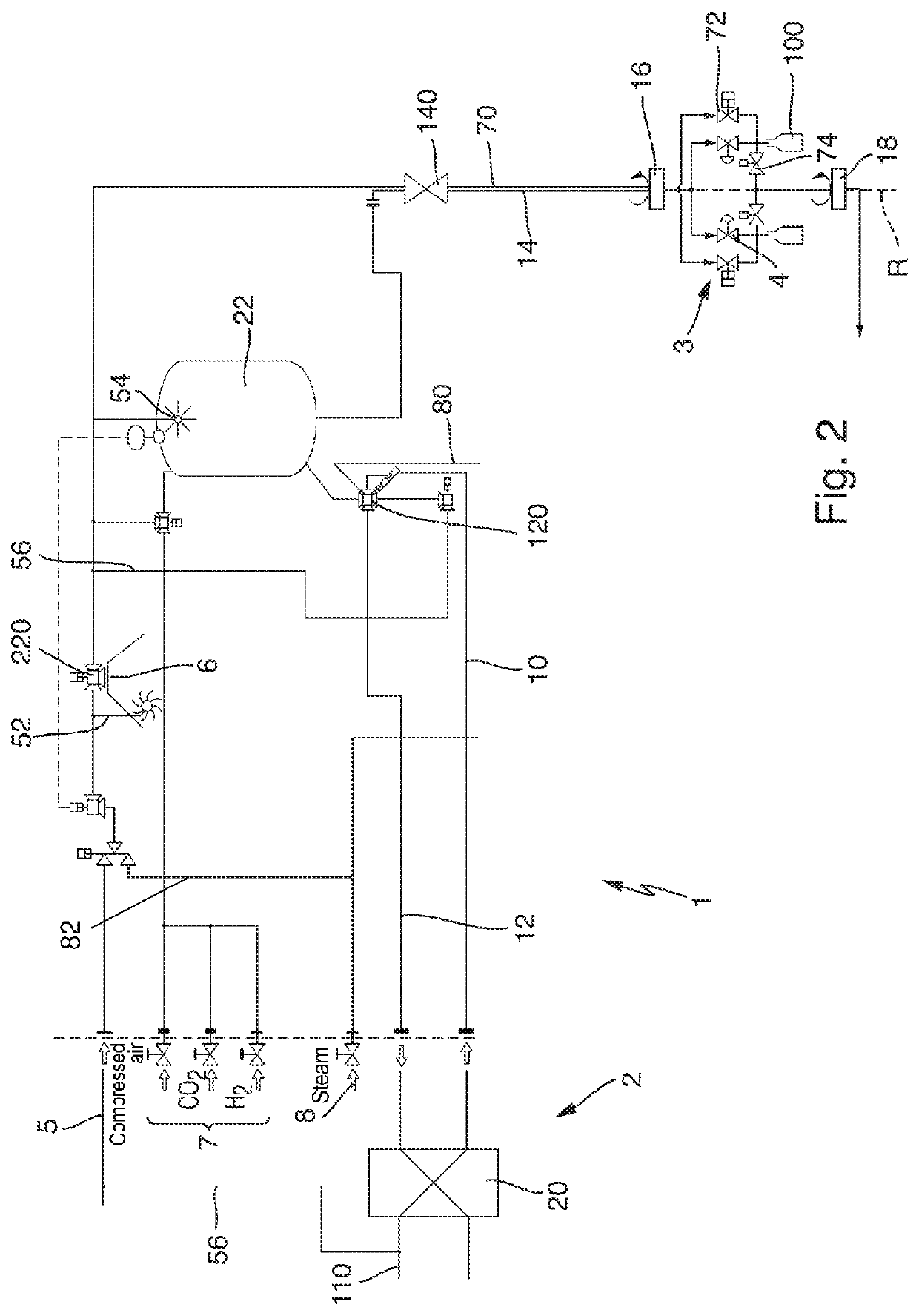
Device and method for filling a container with a sterilised filling product
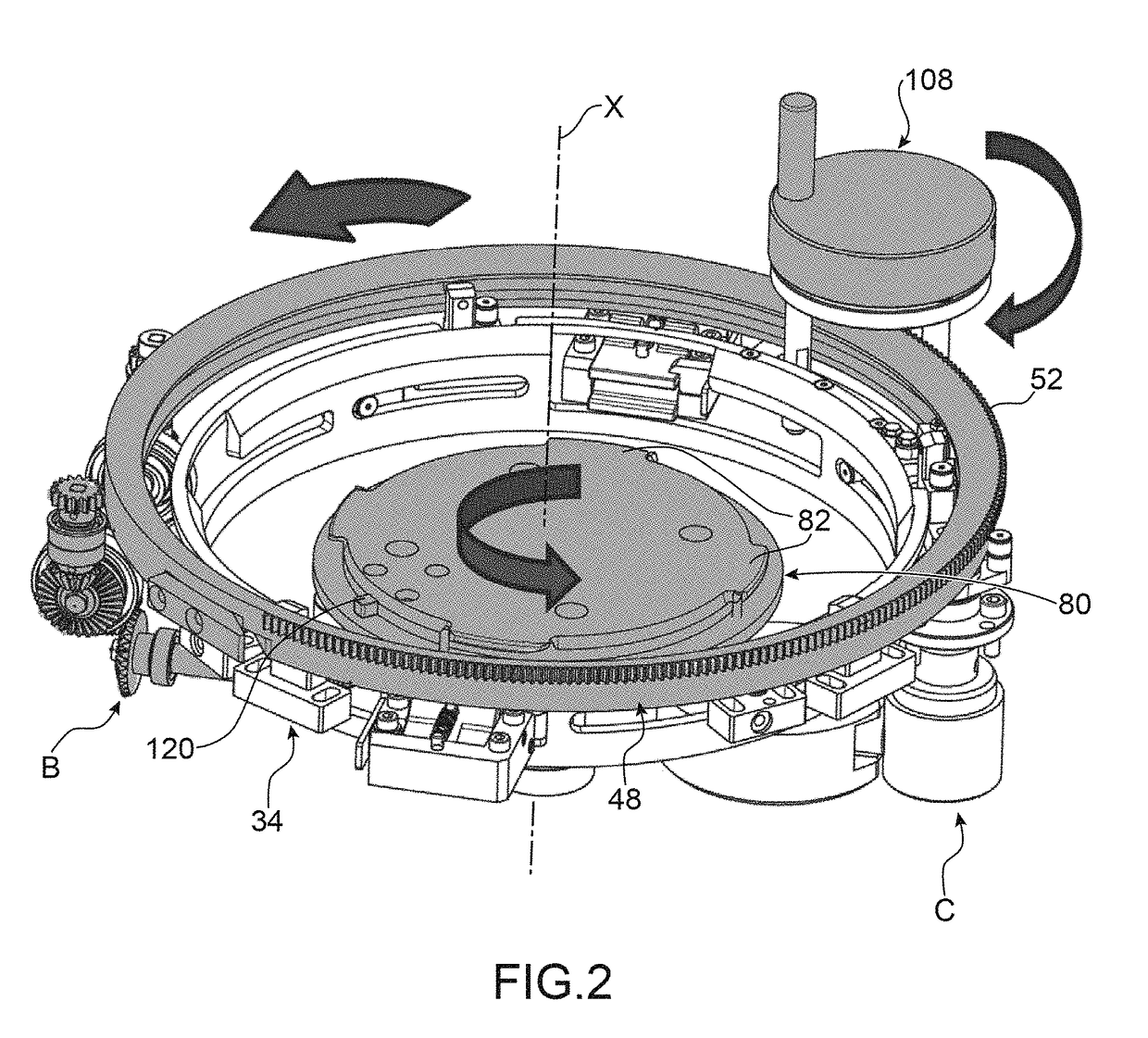
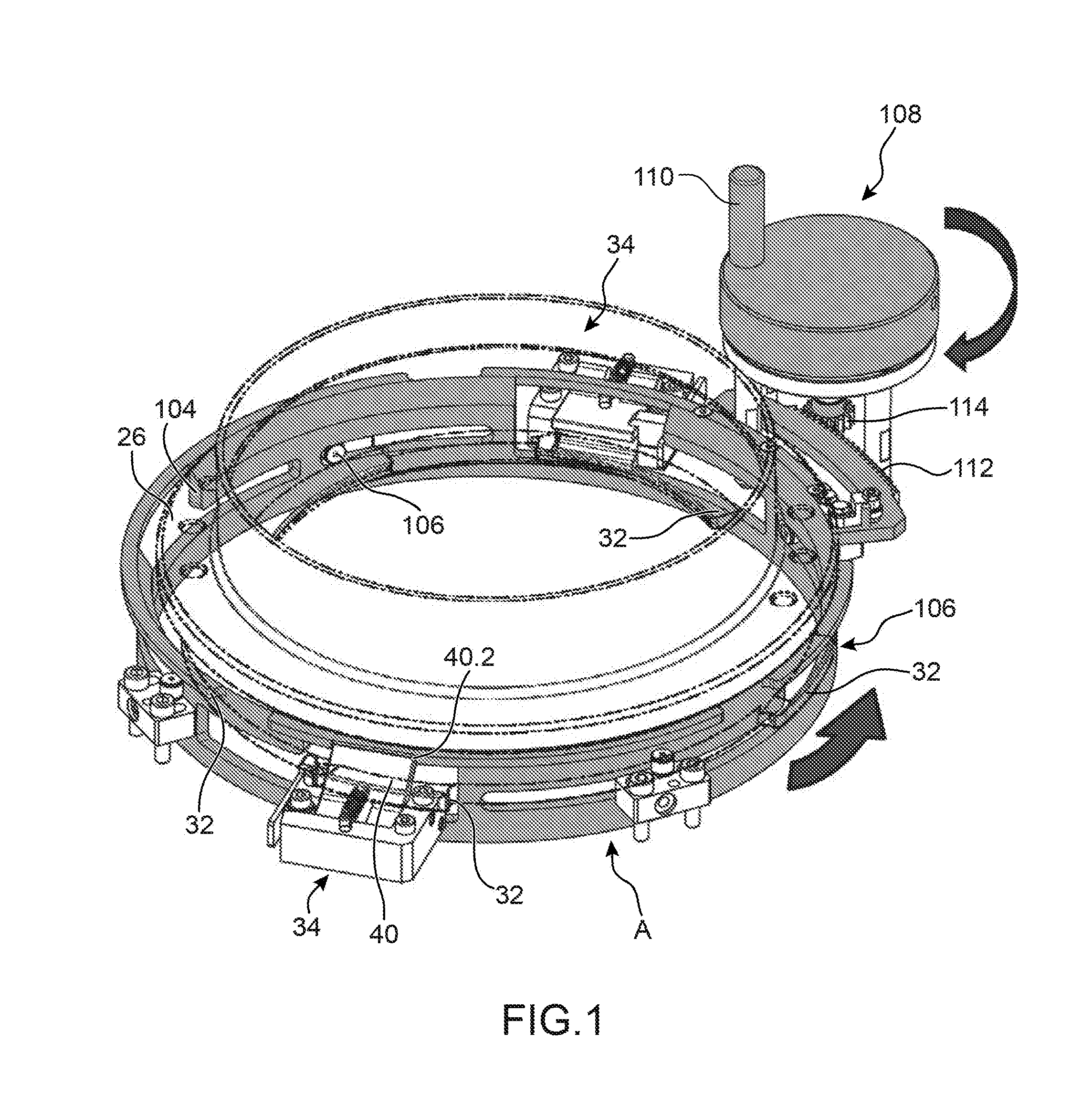
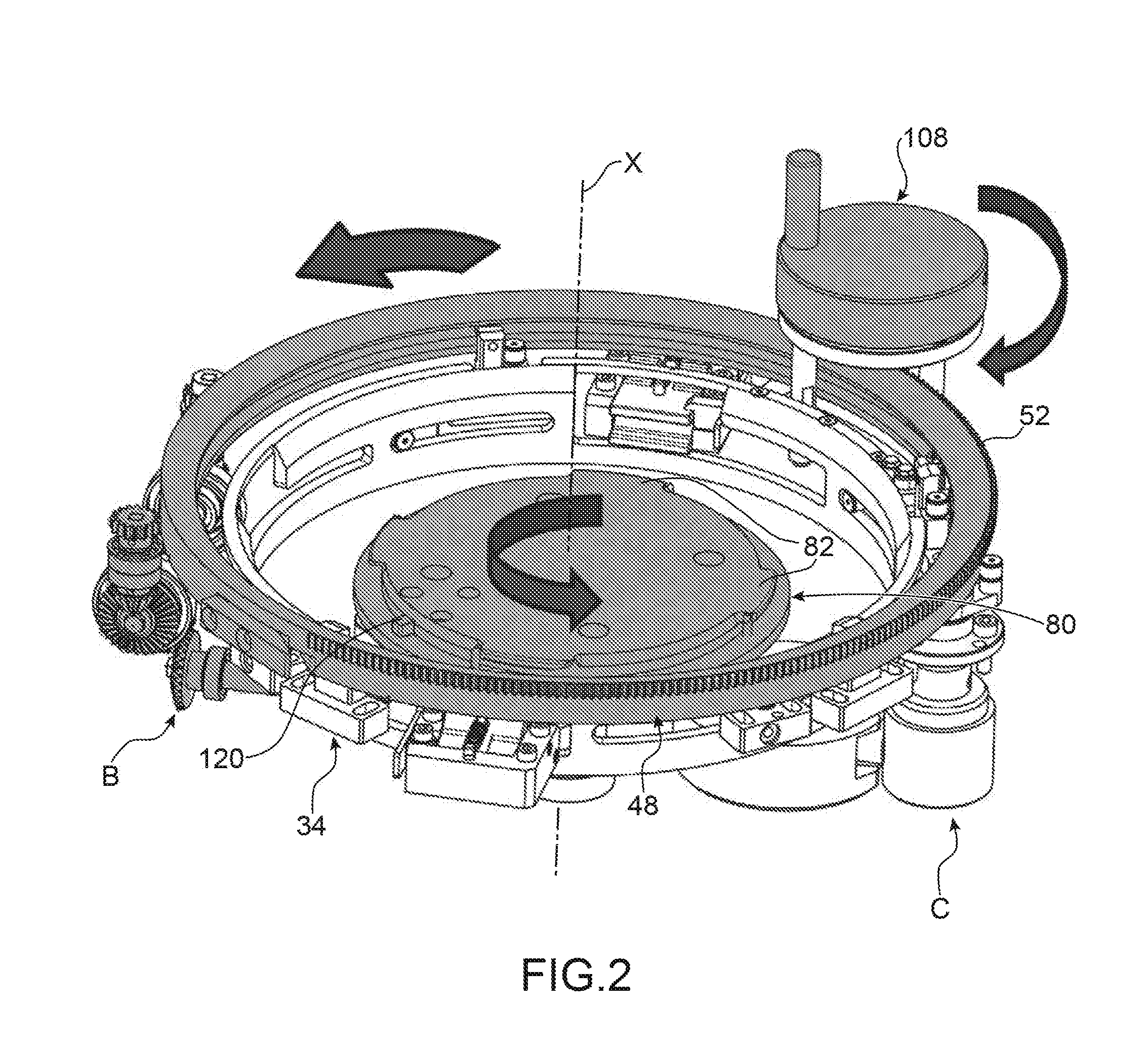
ActiveUS20200017344A1Shorten the lengthDegrading provisionLiquid fillingFilling device cleaningEngineeringMechanical engineering
A device for filling a container with a sterilized filling product, preferably for filling a beverage container with a sterilized beverage in a beverage bottling installation, comprising a sterilization device for sterilizing the filling product, a sterile tank for buffered receiving of the filling product sterilized in the sterilization device, and a filling device which has a filling valve for the filling of the container to be filled, wherein the filling valve is a proportional valve for controlling and / or regulating the filling-product flow of the filling product into the container to be filled, and the proportional valve is connected in a buffer-free manner to the sterile tank.
Owner:KRONES AG
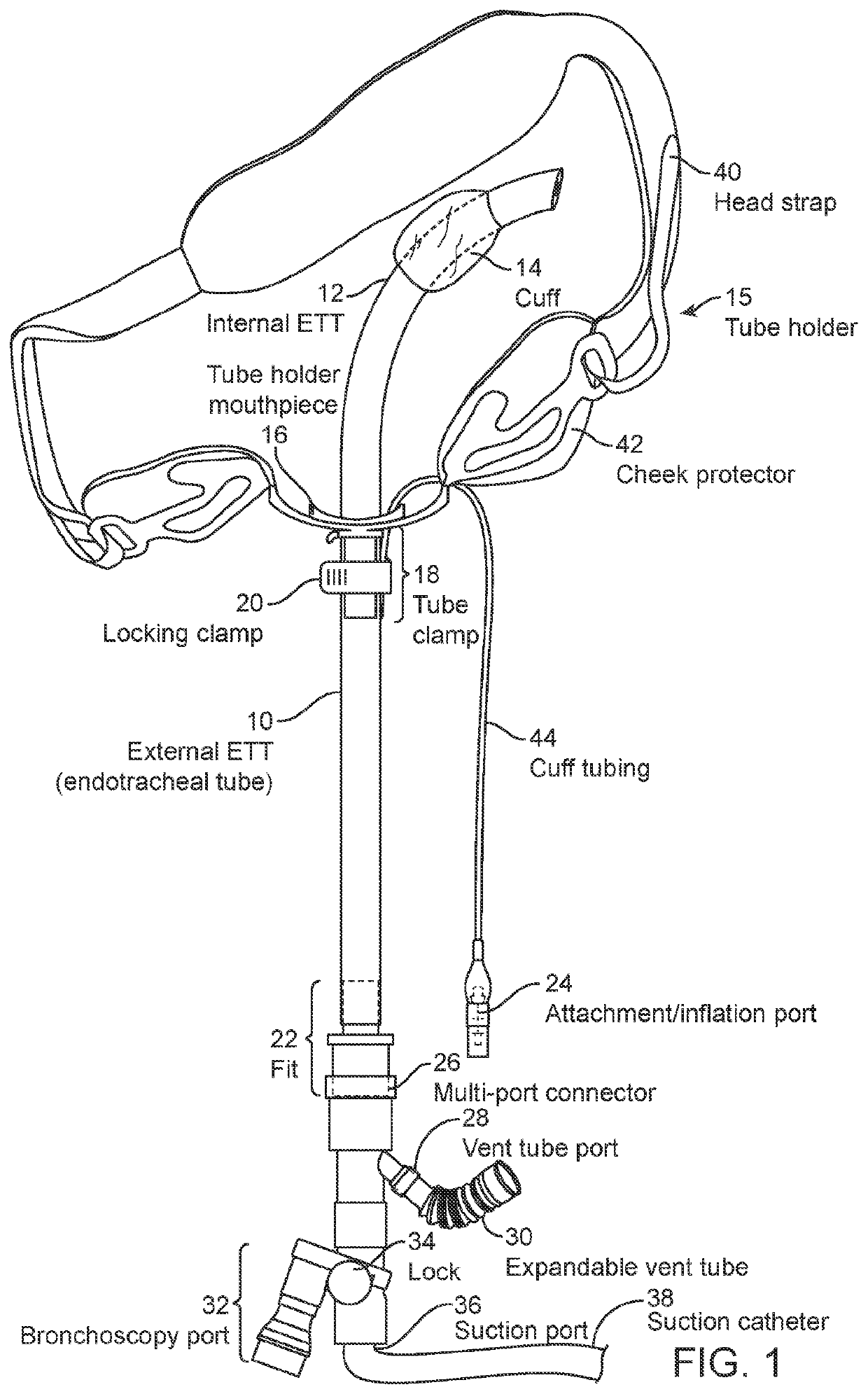
Endotracheal tube guard with optional holding system and optional sensor
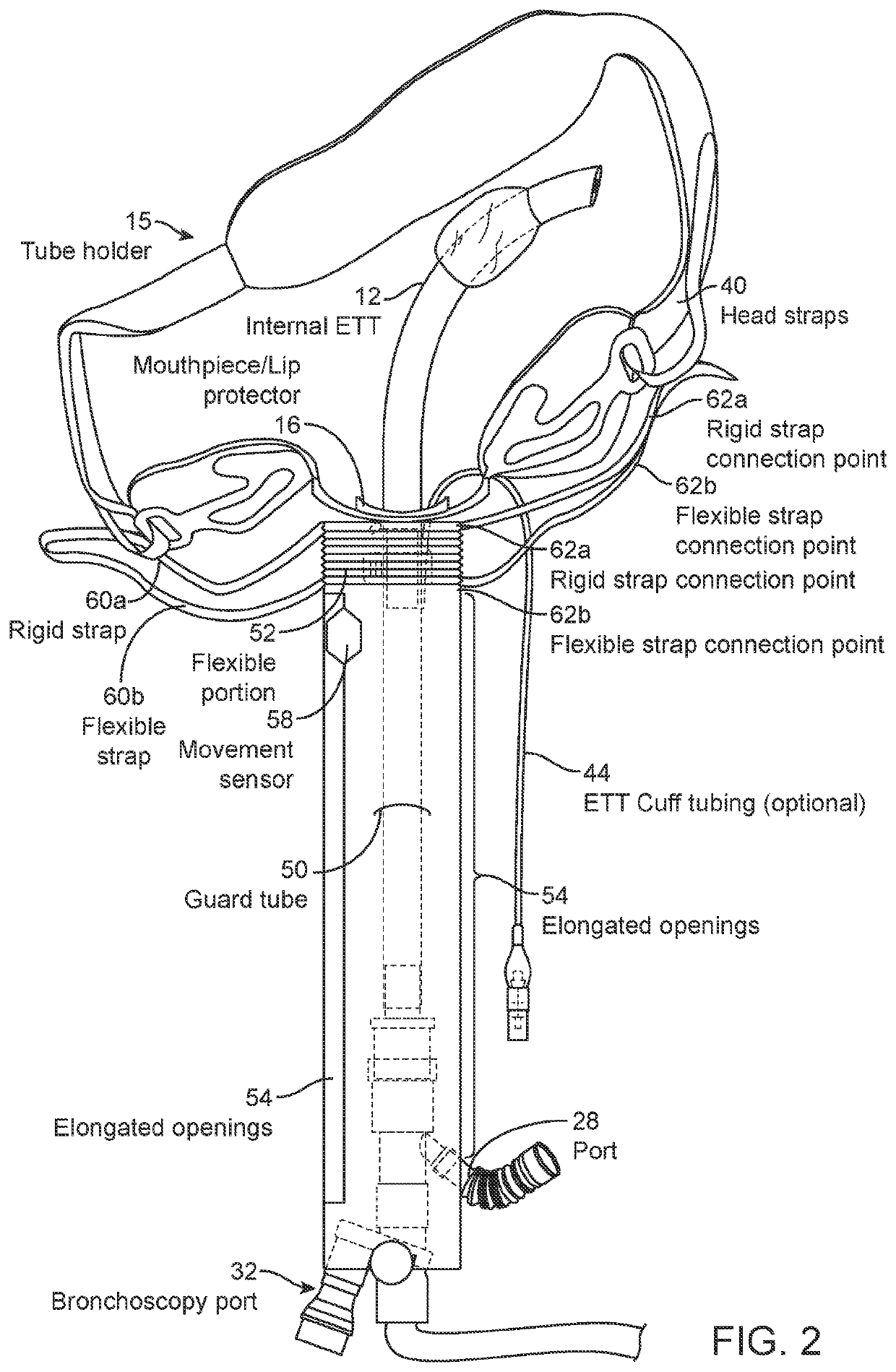
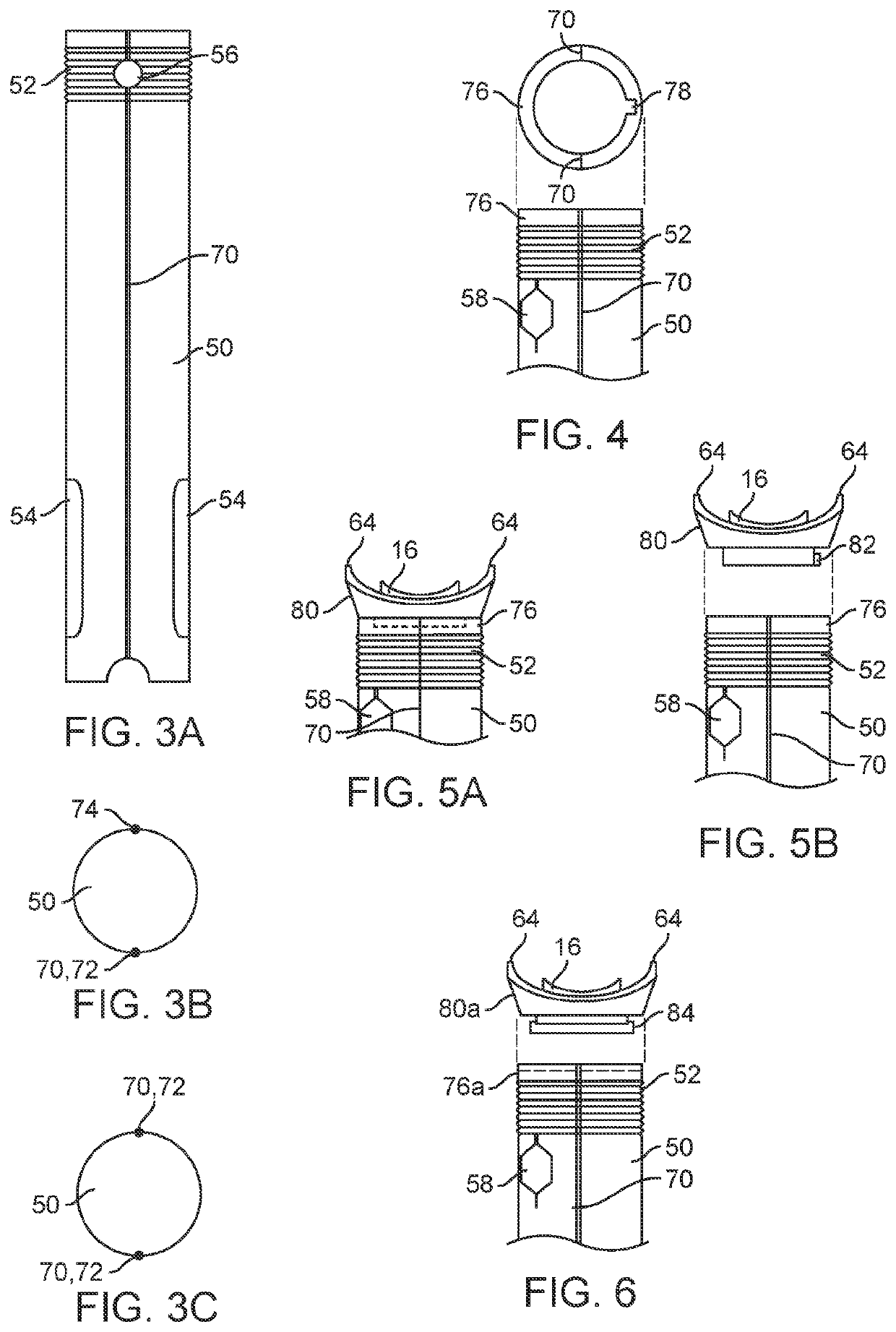
ActiveUS20210052841A1Safe levelPrevent self-extubationTracheal tubesMedical devicesMuscle strengthEmergency medicine
Disclosed embodiments of an endotracheal tube (ETT) guard system help to hinder self-extubation of the ETT of an awake patient who may reflexively attempt removal, but also allow early mobilization and exercise necessary for preservation of muscle strength. Embodiments may include an ETT holder, which may be generic ETT holders offered by various medical device companies, or a specially configured ETT holder as described herein. Embodiments also may include a sensor that alarms when the ETT guard is moved beyond pre-set motion thresholds.
Owner:PAVINI MARIE
Detection device to identify markers dissolved in a liquid by means of a measurement of resistivity variation, detection method and use of marker and detection device
ActiveUS20170219556A1Improve solubilityEasy to identifyHeating or cooling apparatusMaterial thermal conductivityMeasurement deviceChemical reaction
A detection device for detecting a marker in a liquid, preferably a fuel, comprising:a reaction chamber 5, provided with a de-dopable conductive polymer 6 building a path between two conductive pads 10 connected to a resistivity measurement device, wherein the de-dopable conductive polymer 6 is able to be de-doped by a chemical reaction with the marker, changing its resistivity.
Owner:SICPA HLDG SA
Card holder with tab
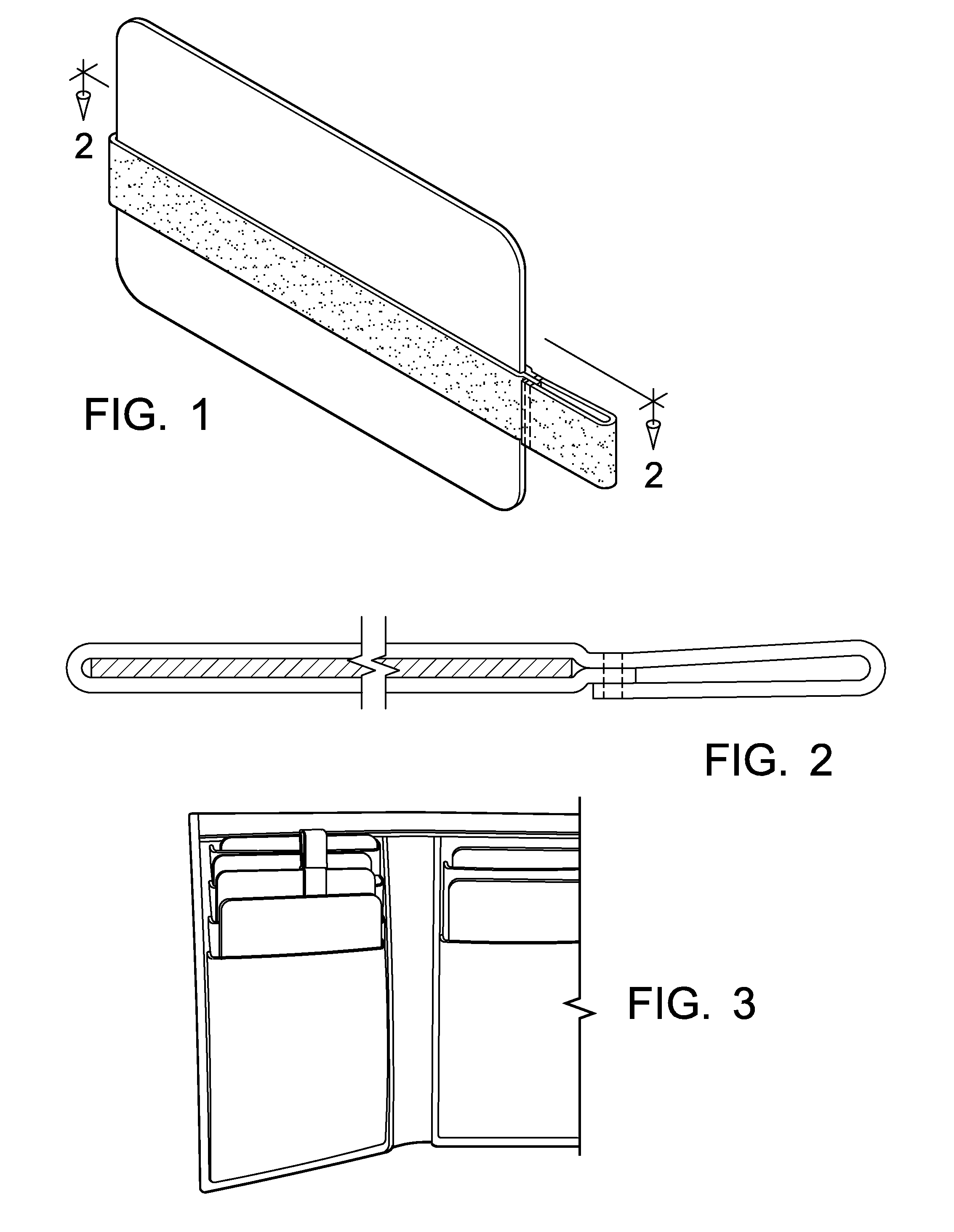
InactiveUS20160198839A1Level of securityEasy to identifyTravelling carriersPursesBusiness cardEngineering
This invention relates to an apparatus for quickly and easily locating and obtaining at least one credit card, ID card, driver's license, business card, and the like from a card carrying device. More particularly, an elastic circular band secured at one end with an elongated tab in such a way to enable quick and easy retrieval from the confined space is disclosed.
Owner:THUMBZEES LLC
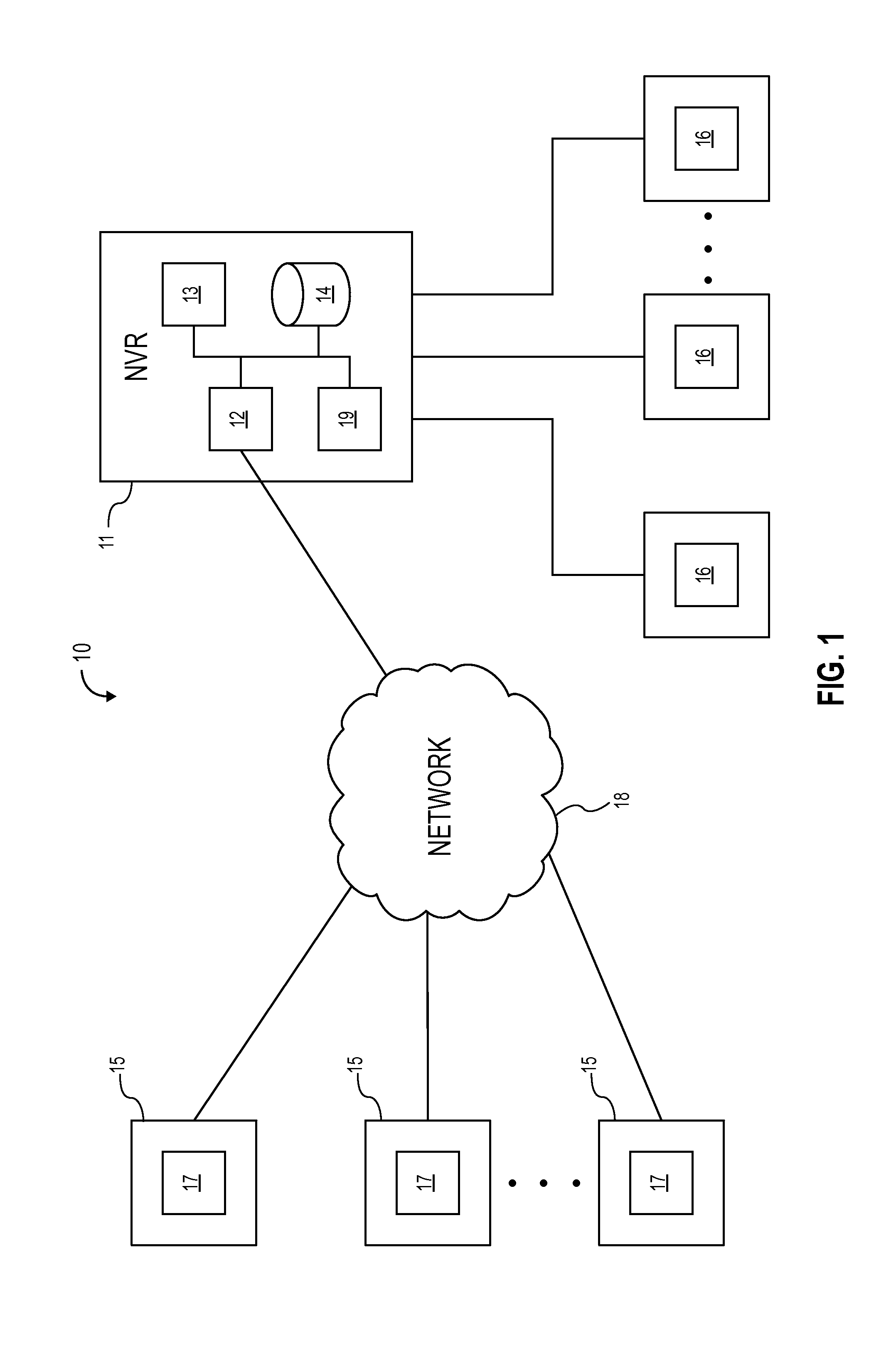
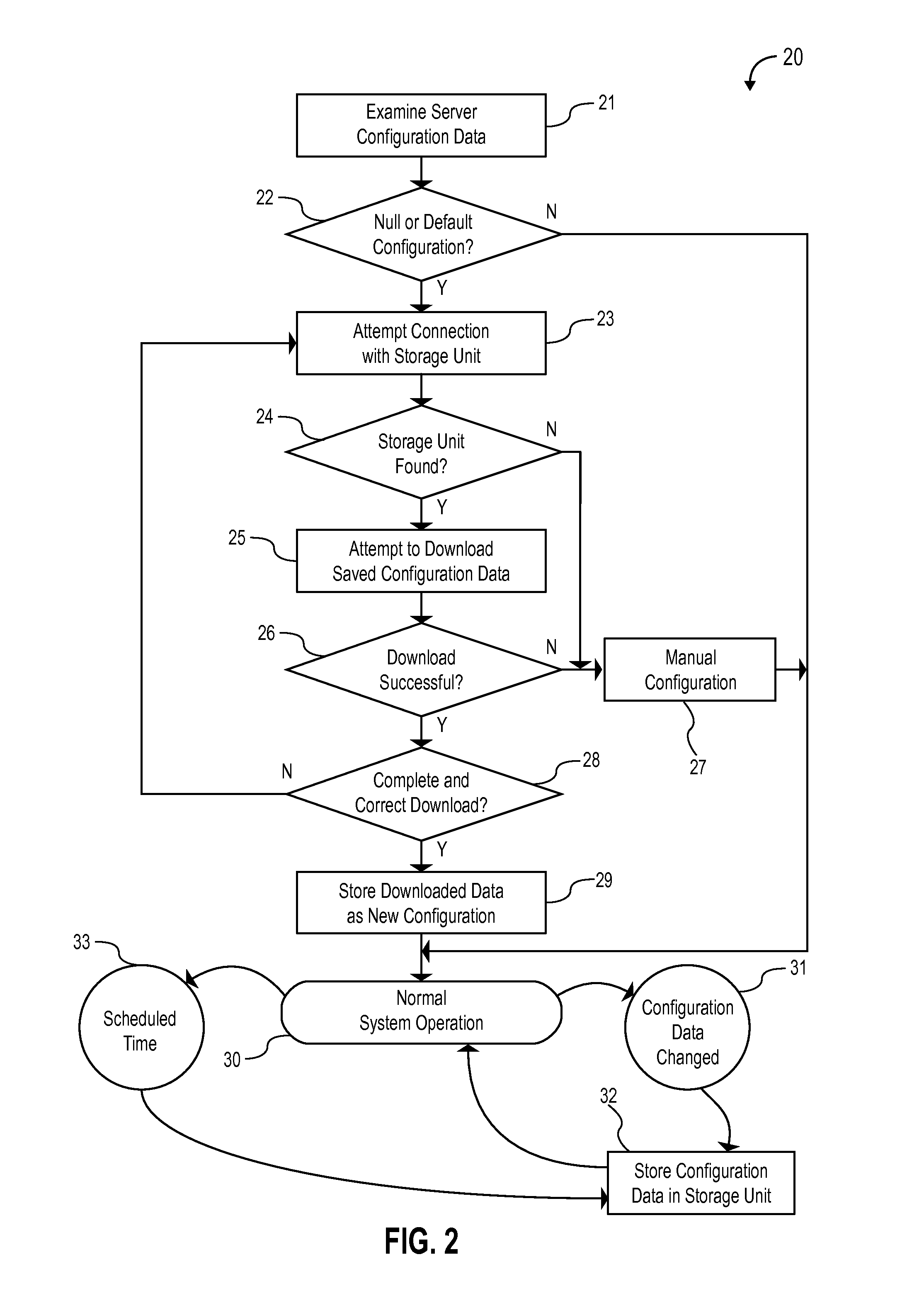
Self-healing video surveillance system
ActiveUS20190141293A1Rapidly and conveniently self-configureRapidly and conveniently and “ self-heal ”Television system detailsColor television detailsSelf-healingComputer science
A method for configuring a computing device in a network of at least one remote device is disclosed. The method includes: storing, in a remote device, a configuration data archive relating to an existing computing device, wherein the remote device is at least one of a traffic camera or an aerial drone camera; determining, by a computing device to be configured, whether the remote device has stored therein a configuration data archive; and transferring data from the configuration data archive to the computing device to be configured in response to a determination that the remote device has stored therein a configuration data archive.
Owner:CAREY JAMES
Charging device and control method thereof
ActiveUS10770912B2Safety levelProvide energyBatteries circuit arrangementsDc-dc conversionCharge currentComputational physics
A charging device and a control method thereof are provided. The charging device includes an adapter, an energy storage unit and a charging module. The adapter provides an adapter current. The charging module receives the adapter current and provides a first charging current to charge the energy storage unit, or an output current to charge an electronic device. When the input current is larger than a first preset current and the first charging current is equal to or less than a third preset current, the charging module operates in a boost mode, such that the energy storage unit provides a second charging current to the charging module. When the second charging current is larger than the third preset current, the charging module enters a buck mode such that the energy storage unit is charged by the first charging current.
Owner:ANPEC ELECTRONICS CORPORATION
Fail-Safe Speed Monitoring of a Drive
ActiveUS20190339098A1Overcome disadvantagesSafety levelElectric motor controlEmergency protective circuit arrangementsFrequency changerMagnetic flux
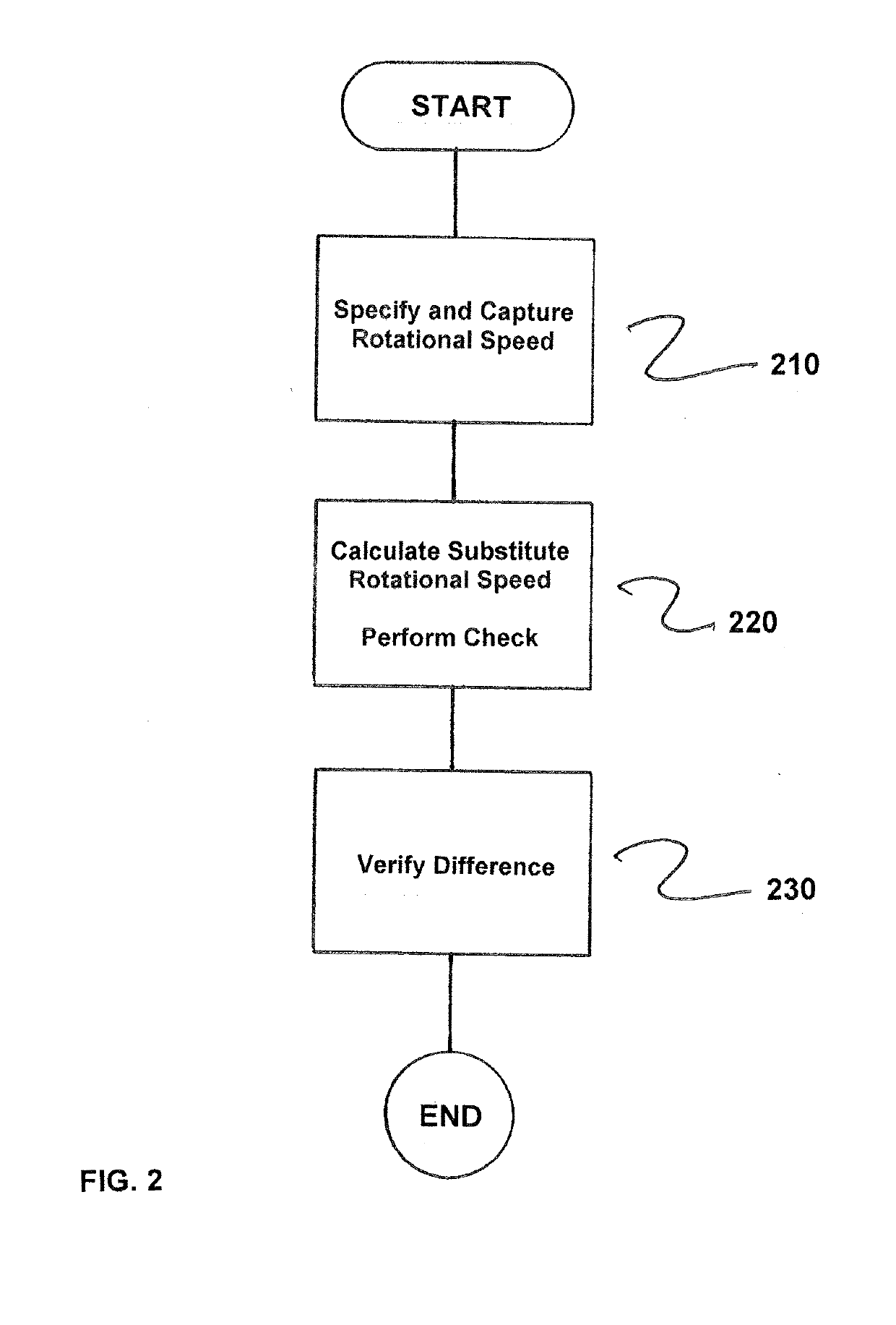
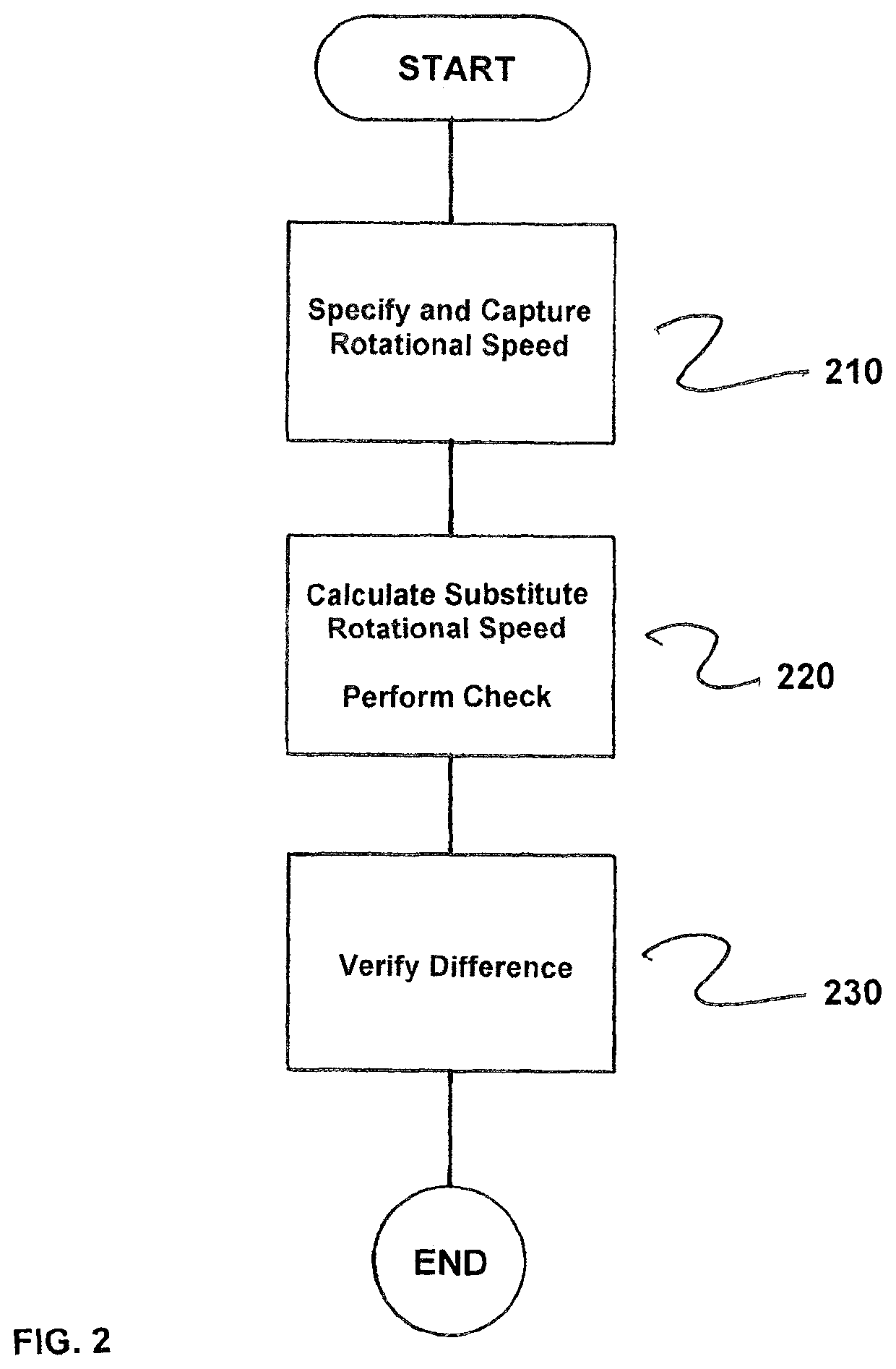
A method for fail-safe monitoring of the speed of a drive that includes at least a converter, a motor, and a rotational speed sensor, wherein a target rotational speed is specified to the drive and an actual rotational speed is sensed via the sensor, where a substitute rotational speed is calculated and three plausibility checks are performed in a safety program of a safety CPU, the substitute rotational speed being determinable, for example, from the initial frequency of a converter or from the quotient of EMF and magnetic flux, in each case two of the following three values being checked: target rotational speed, actual rotational speed and substitute rotational speed to achieve a high safety integrity level while avoiding disadvantages of conventional solutions, and because the calculated substitute rotational speed is independent of the sensor, even sensor errors that are difficult or impossible to detect via conventional solutions become detectable.
Owner:SIEMENS ENERGY GLOBAL GMBH & CO KG
Apparatus and method for a security-critical application
ActiveUS10394212B2Easily designedCompromising of safety can be excludedComputer controlError detection/correctionRuntime systemSafety critical application
An apparatus and a method for the parallel and independent operation of a normal program and a secure program on the basis of a runtime system structure have all components that are relevant to the control integrated on a hardware component with a specific hardware architecture and be isolated from one another by a runtime system structure for two dual runtime systems for making changes to non-security-relevant components without restriction. The isolation can be provided by prioritizing one of the runtime systems. Such a runtime system structure or hardware architecture eliminates the need for follow-up certification of user-programmable controllers and the certification of the security-critical component is valid even when changes to the non-security-relevant components are made.
Owner:INTER CONTROL HERMANN KOEHLER ELECTRIC GMBH & CO KG
Device providing fluidtight connection in two enclosed volumes comprising means of holding prior to connection
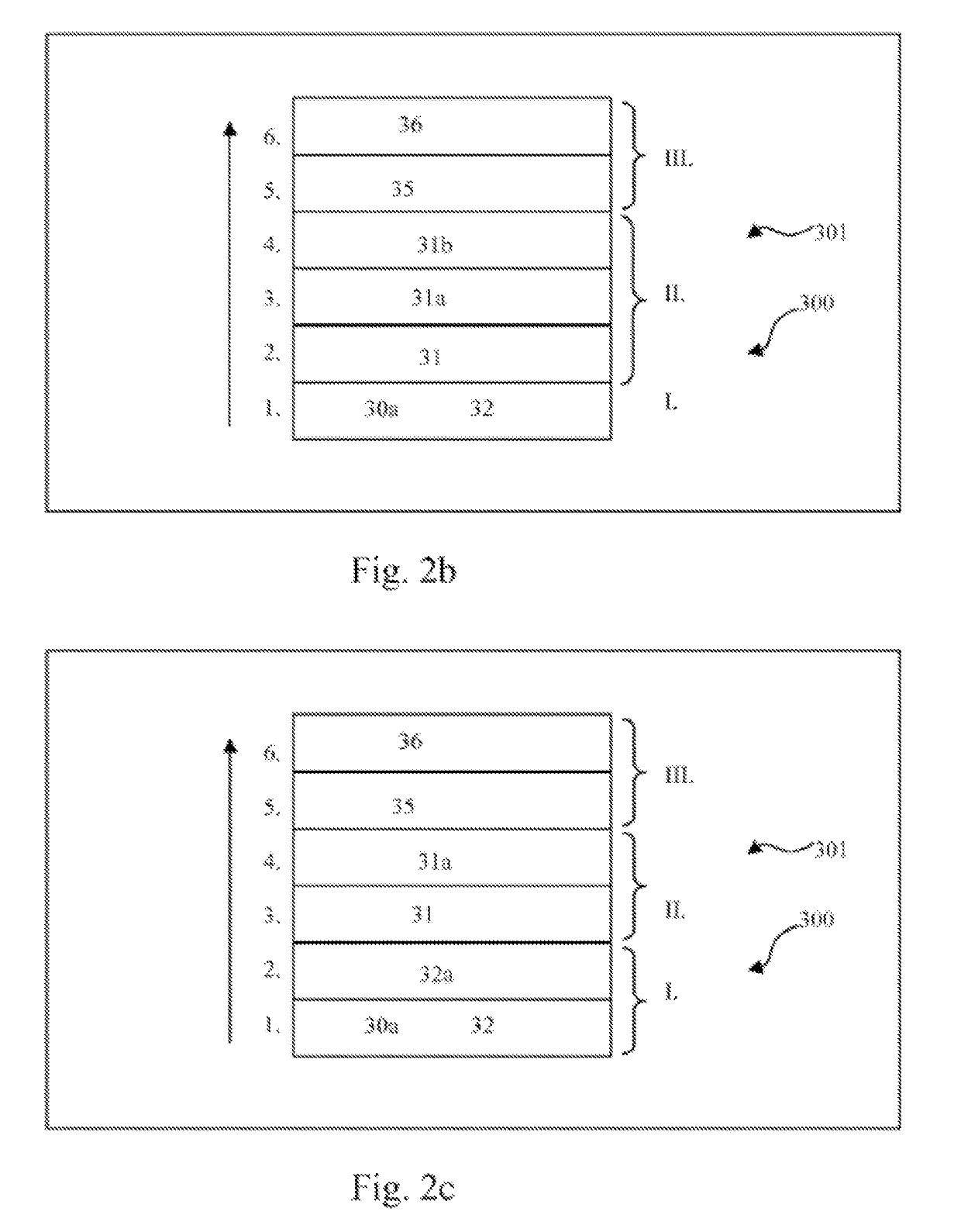
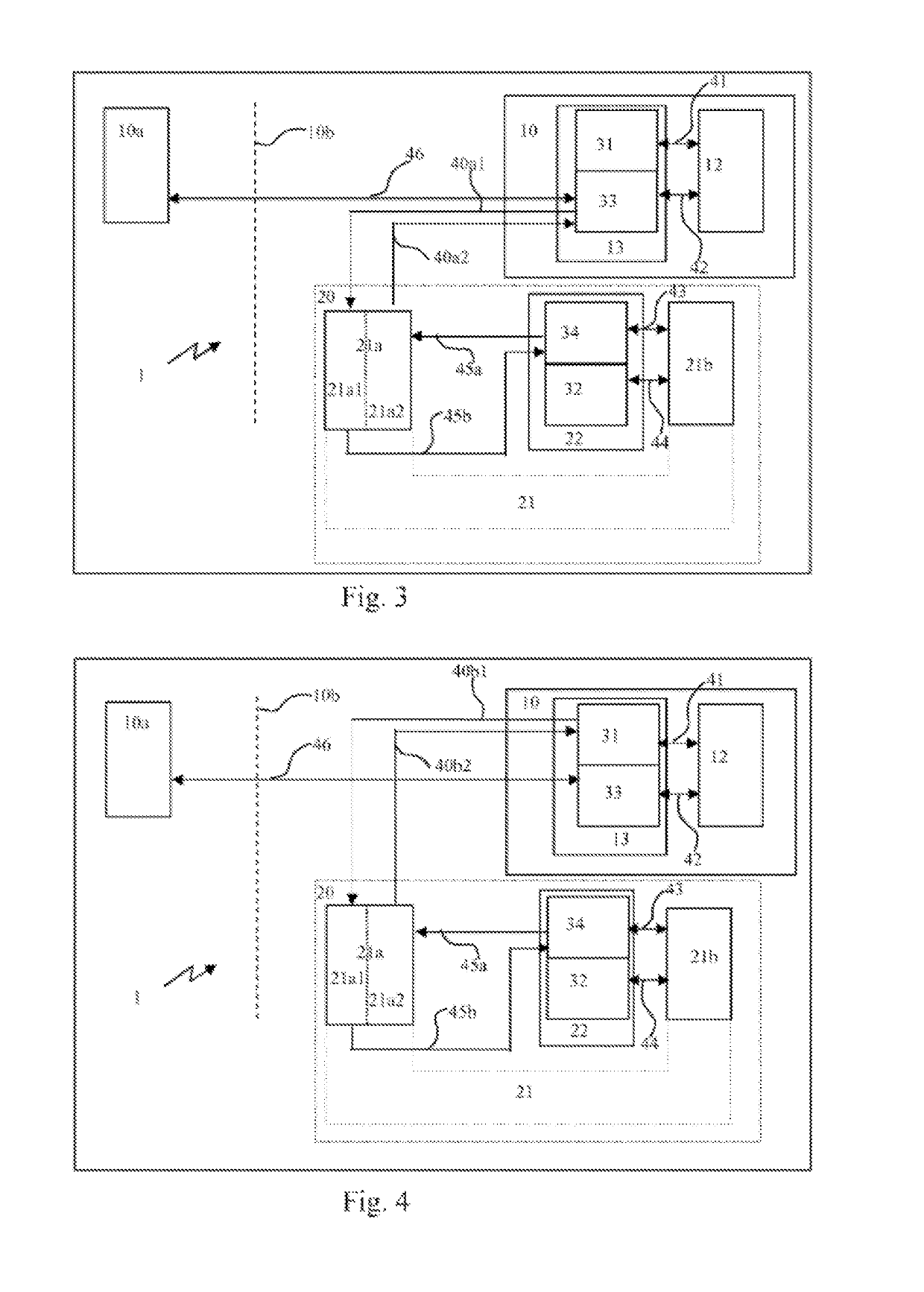
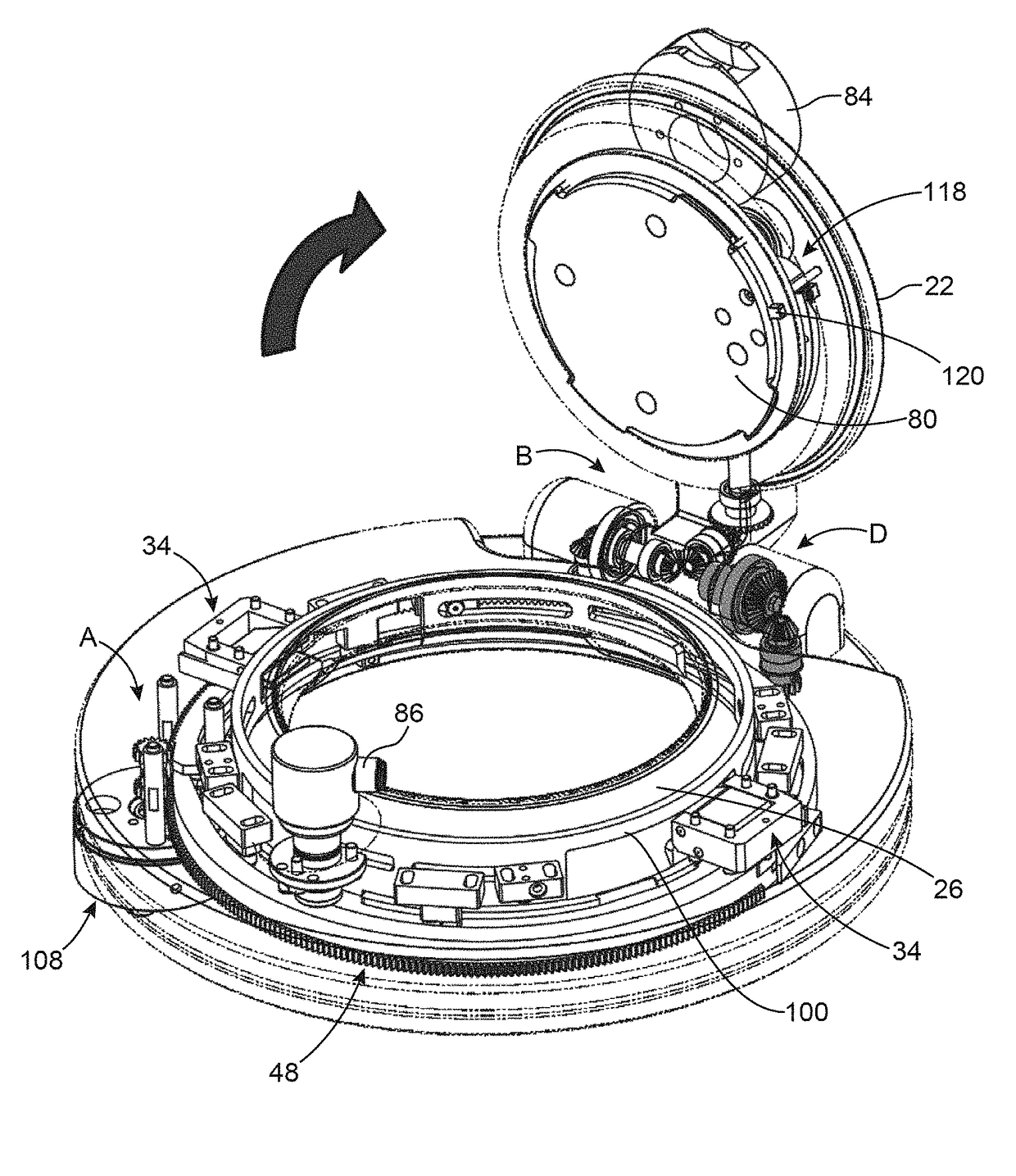
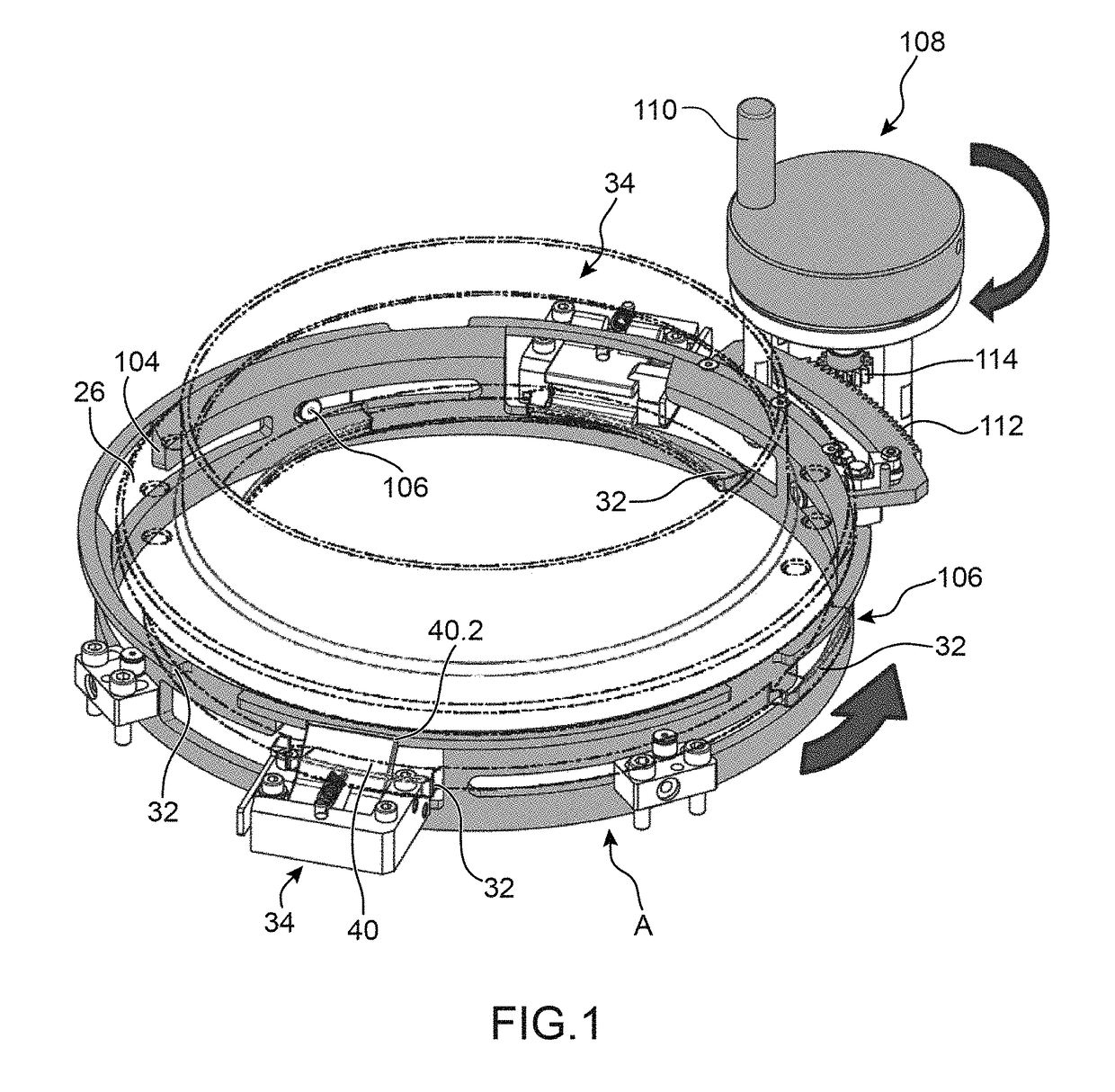
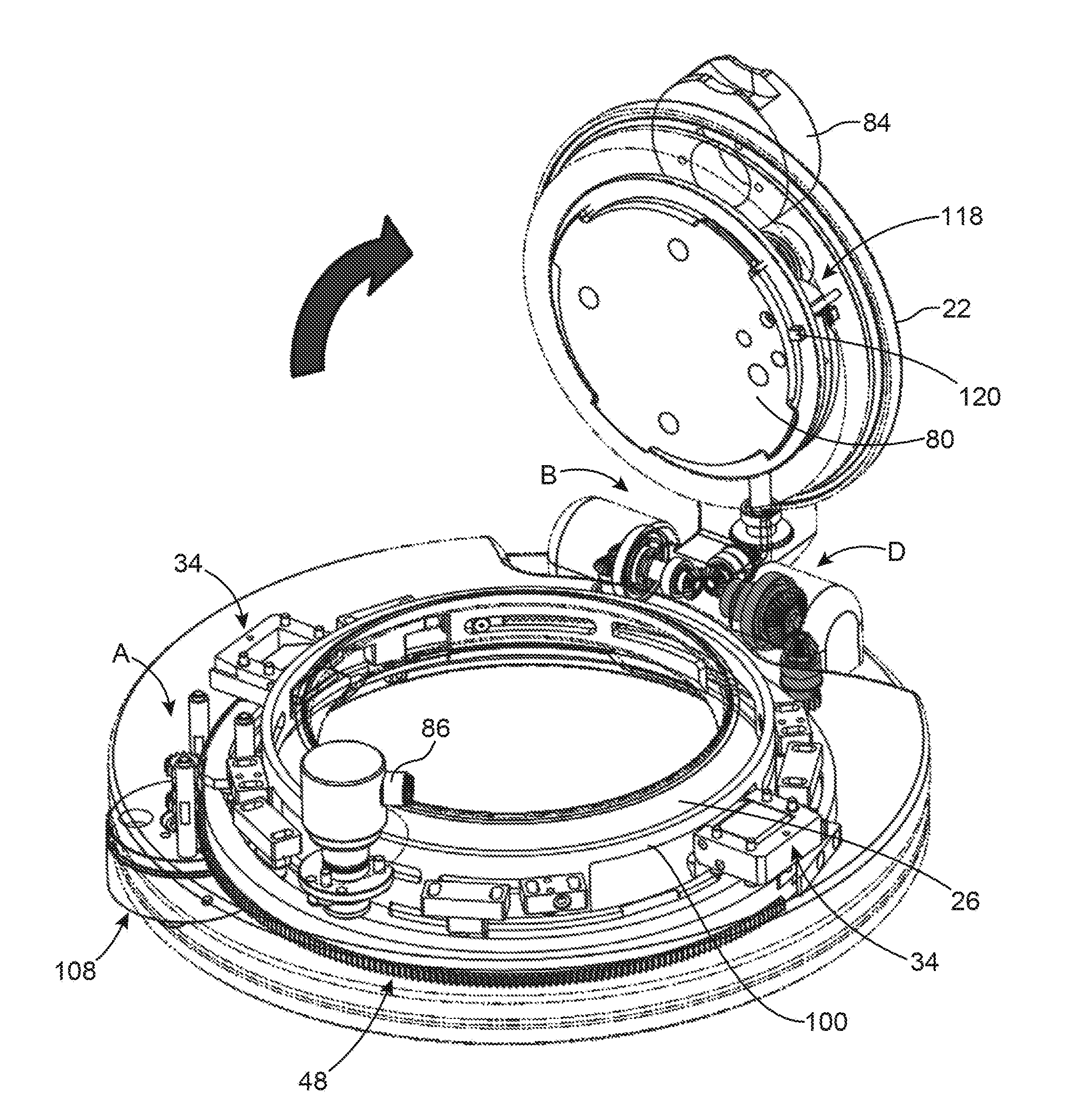
ActiveUS9704608B2Maintain securityImprove the level ofWing fastenersDoor/window applicationsEngineeringFlange
Owner:GETINGE LIFE SCI FRANCE
Device providing fluidtight connection in two enclosed volumes comprising means of holding prior to connection
ActiveUS20160208527A1Maintain securityImprove the level ofWing fastenersDoor/window applicationsFlangeElectrical and Electronics engineering
Sealed connection device between a first and a second closed space, closed off by doors, first part (A) for securing the first and second flanges to one another, second part for securing the second door and the first door in a sealed manner, part for detaching the second door from the second flange, third part for releasing the first door in relation to the first flange (18), fourth part for opening a passage between the first and the second closed space, and part for controlling the first, second, third and fourth parts allowing for the sealed connection without rotation of one of the closed spaces, the device also comprising a device for maintaining by snap fitting (34) for the second closed space in relation to the first closed space prior to the securing by the first part for securing.
Owner:GETINGE LIFE SCI FRANCE
Device and method for filling a container with a sterilised filling product
ActiveUS11014799B2Shorten the lengthDegrading provisionLiquid fillingFilling device cleaningMechanical engineeringMaterials science
A device for filling a container with a sterilized filling product, preferably for filling a beverage container with a sterilized beverage in a beverage bottling installation, comprising a sterilization device for sterilizing the filling product, a sterile tank for buffered receiving of the filling product sterilized in the sterilization device, and a filling device which has a filling valve for the filling of the container to be filled, wherein the filling valve is a proportional valve for controlling and / or regulating the filling-product flow of the filling product into the container to be filled, and the proportional valve is connected in a buffer-free manner to the sterile tank.
Owner:KRONES AG
Self-healing video surveillance system
ActiveUS20210297632A1Rapidly and conveniently self-configure and “ self-heal ”Quick changeTelevision system detailsColor television detailsComputer hardwareVideo monitoring
A method for configuring a computing device in a network of at least one remote device is disclosed. The method includes: storing, in a remote device, a configuration data archive relating to an existing computing device, wherein the remote device is at least one of a traffic camera or an aerial drone camera; determining, by a computing device to be configured, whether the remote device has stored therein a configuration data archive; and transferring data from the configuration data archive to the computing device to be configured in response to a determination that the remote device has stored therein a configuration data archive.
Owner:CAREY JAMES
Fail-safe speed monitoring of a drive
ActiveUS10883859B2Safety levelEnsure safetyElectric motor controlEmergency protective circuit arrangementsConvertersSafety Integrity Level
A method for fail-safe monitoring of the speed of a drive that includes at least a converter, a motor, and a rotational speed sensor, wherein a target rotational speed is specified to the drive and an actual rotational speed is sensed via the sensor, where a substitute rotational speed is calculated and three plausibility checks are performed in a safety program of a safety CPU, the substitute rotational speed being determinable, for example, from the initial frequency of a converter or from the quotient of EMF and magnetic flux, in each case two of the following three values being checked: target rotational speed, actual rotational speed and substitute rotational speed to achieve a high safety integrity level while avoiding disadvantages of conventional solutions, and because the calculated substitute rotational speed is independent of the sensor, even sensor errors that are difficult or impossible to detect via conventional solutions become detectable.
Owner:SIEMENS ENERGY GLOBAL GMBH & CO KG
Memristor-based circuit and method
ActiveUS20220329254A1Simple and efficientSafety levelElectric signal transmission systemsElectric analogue storesMemristorConverters
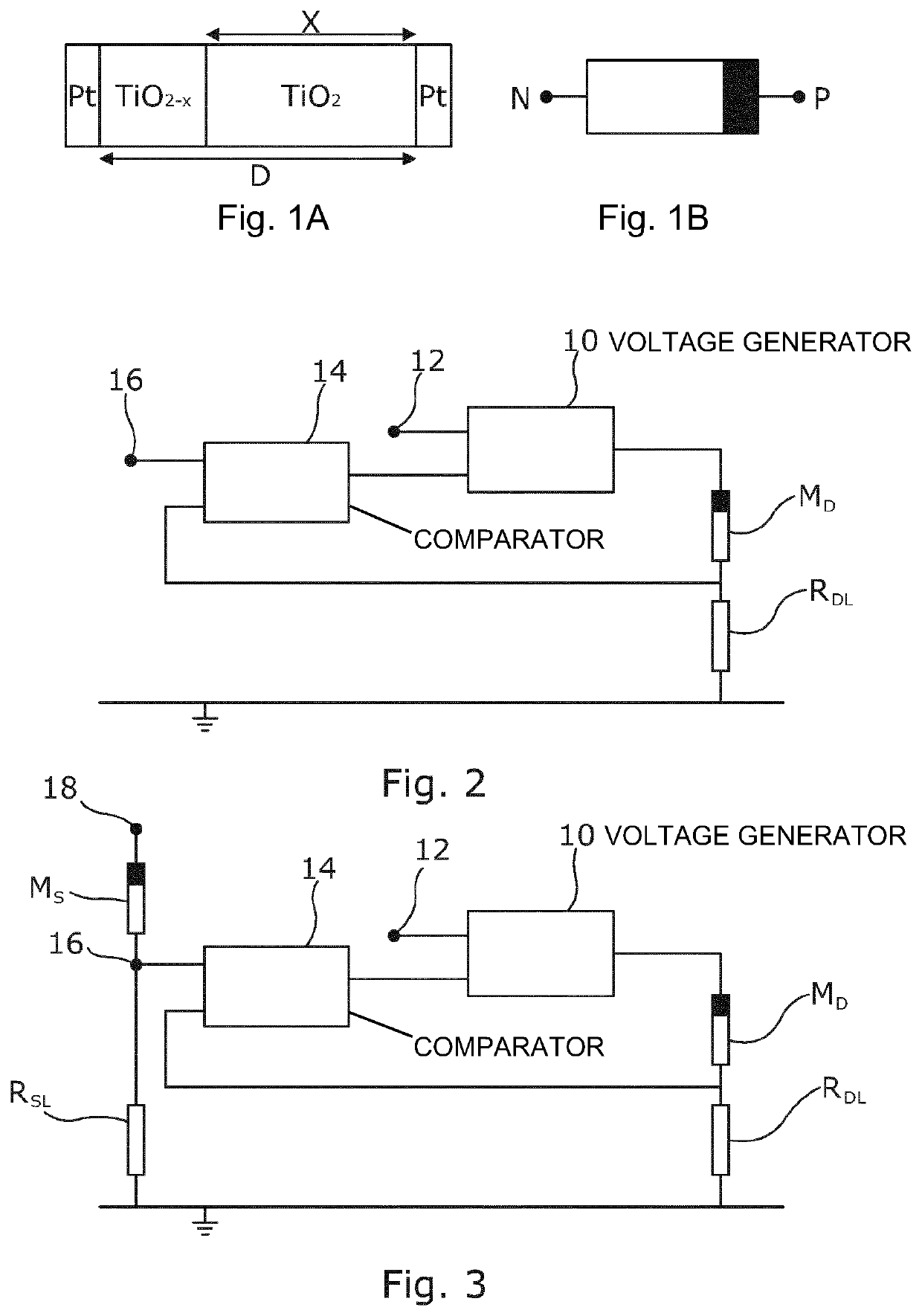
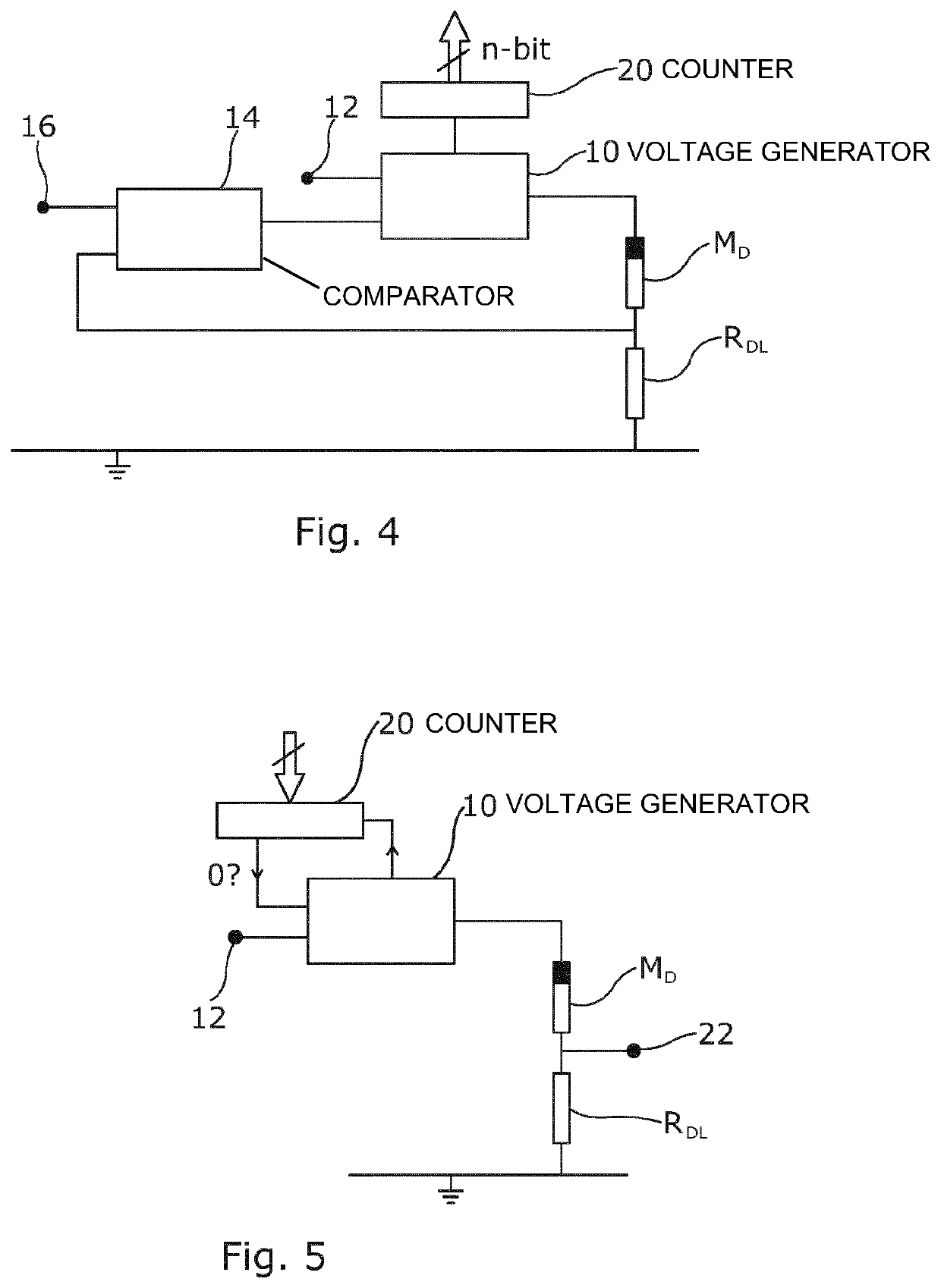
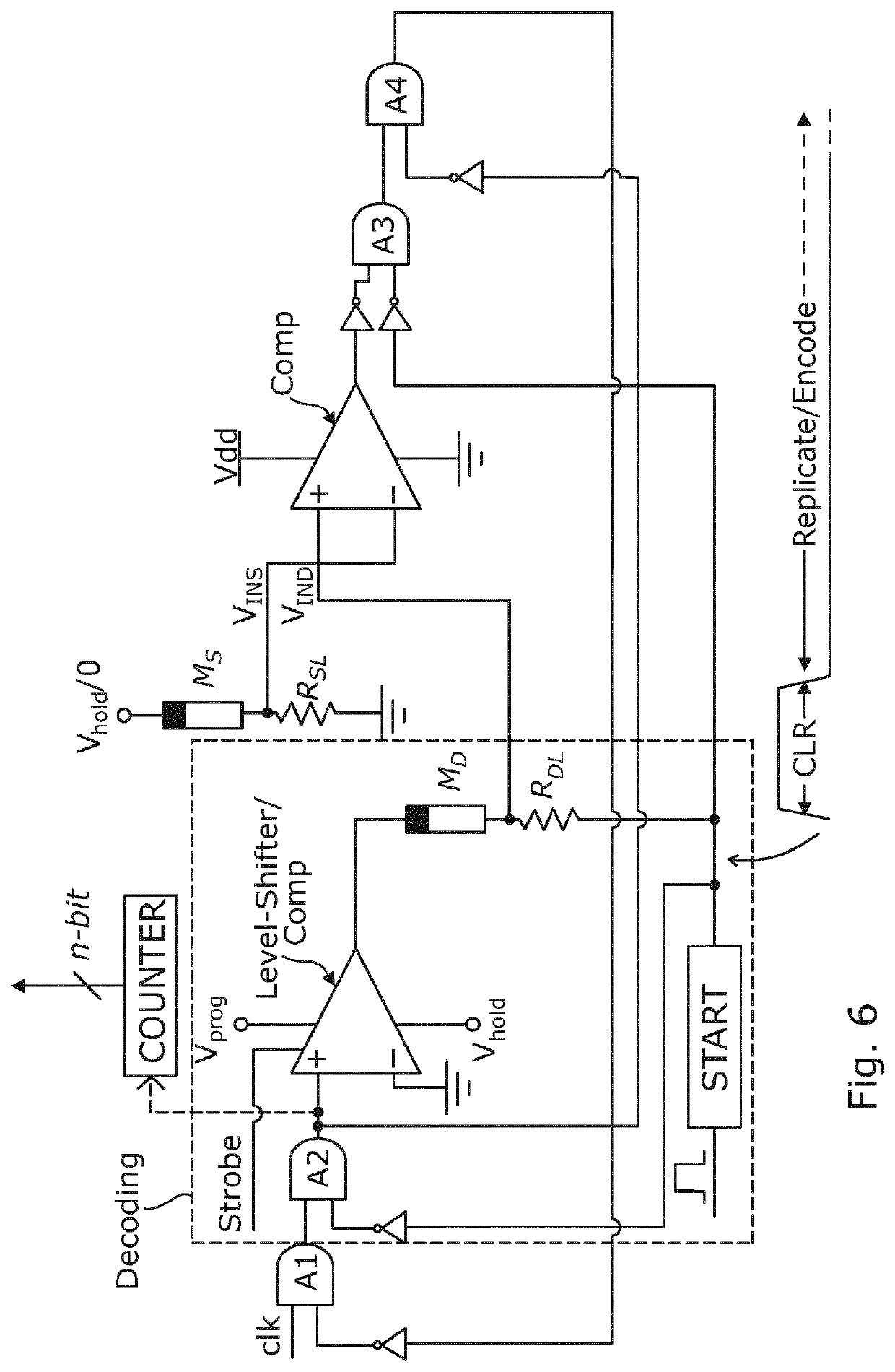
A memristor-based circuit includes a voltage generator that applies a series of voltage pulses to a memristor to progressively change the resistance of the memristor. A comparator: receives an input electrical value; receives an electrical value based on the resistance of the memristor; compares the received values; and, based on the comparison, enables the application of the voltage pulses to the memristor by the voltage generator until a defined condition is satisfied. This circuit can be used to enable the memristor to be programmed to a desired resistance value, such as for use as a non-volatile memory. It can also enable the resistance of one memristor to be replicated to another memristor. By counting the number of applied voltage pulses, the circuit can be used as an encoder or analog-to-digital converter. Other variants of the circuit enable construction of a decoder or digital-to-analog converter, and an authentication circuit.
Owner:OXFORD BROOKES UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com