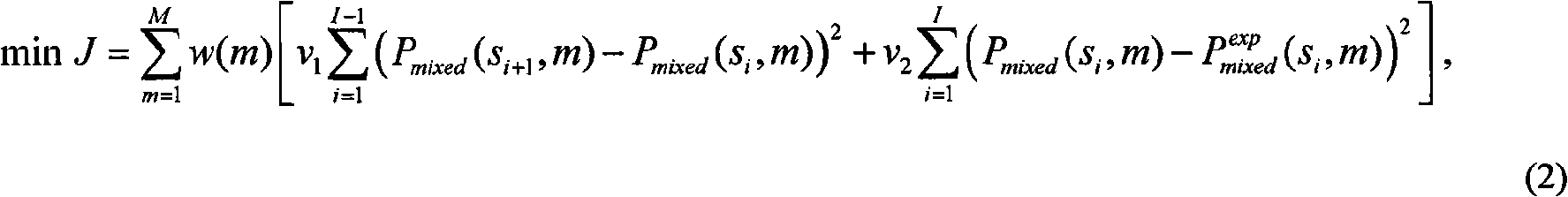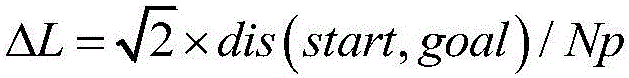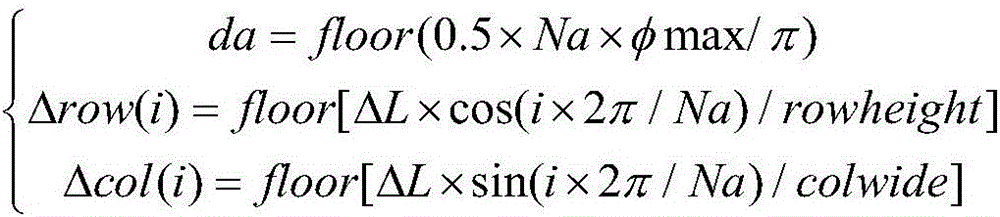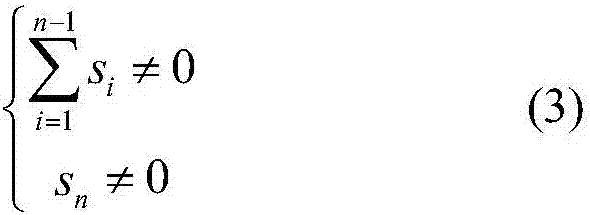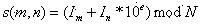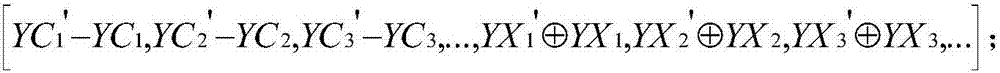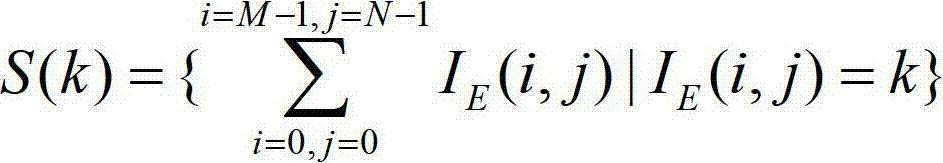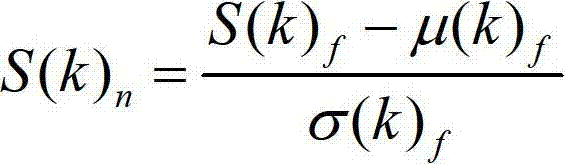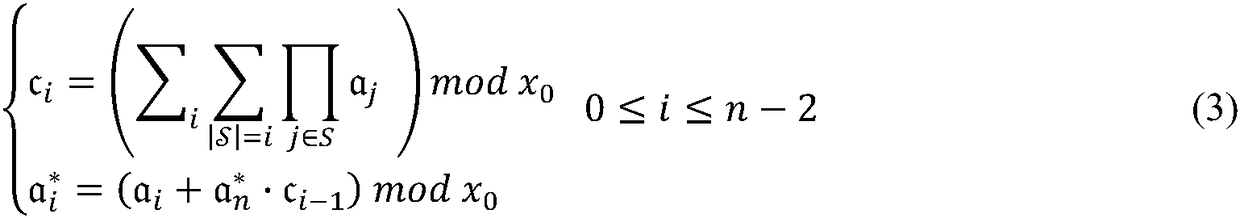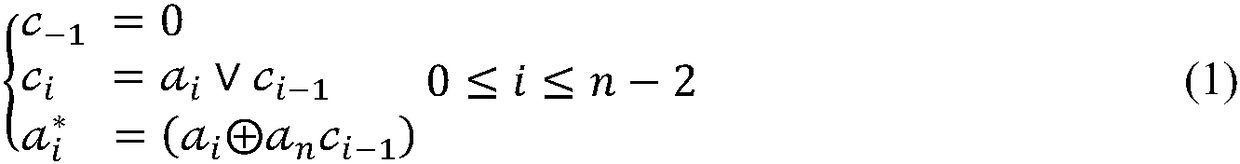Patents
Literature
380 results about "Algorithmic efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
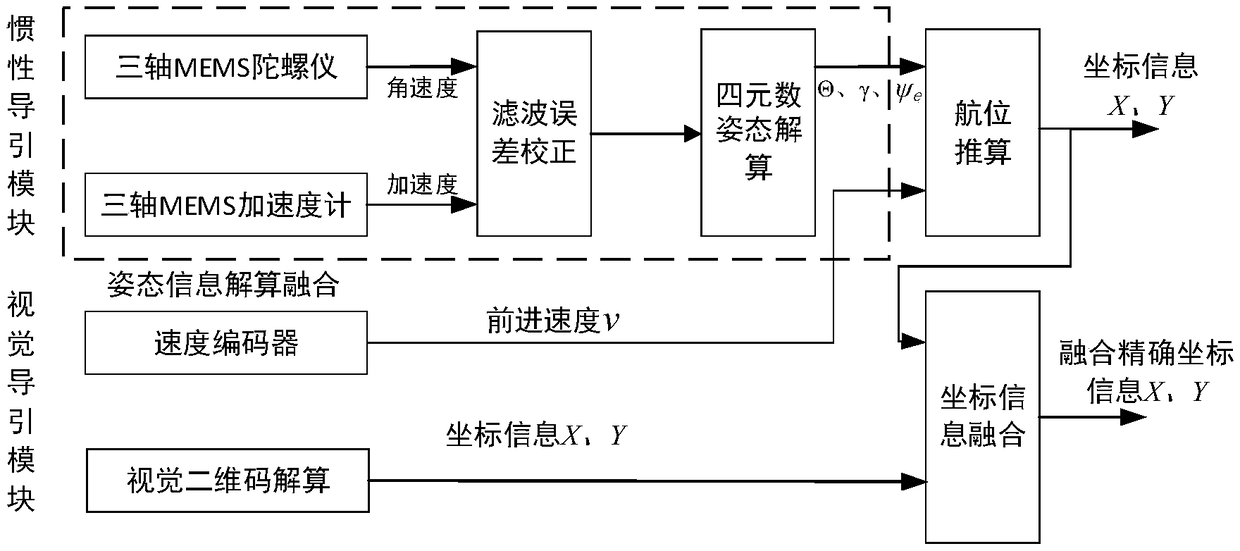
In computer science, algorithmic efficiency is a property of an algorithm which relates to the number of computational resources used by the algorithm. An algorithm must be analyzed to determine its resource usage, and the efficiency of an algorithm can be measured based on usage of different resources. Algorithmic efficiency can be thought of as analogous to engineering productivity for a repeating or continuous process.
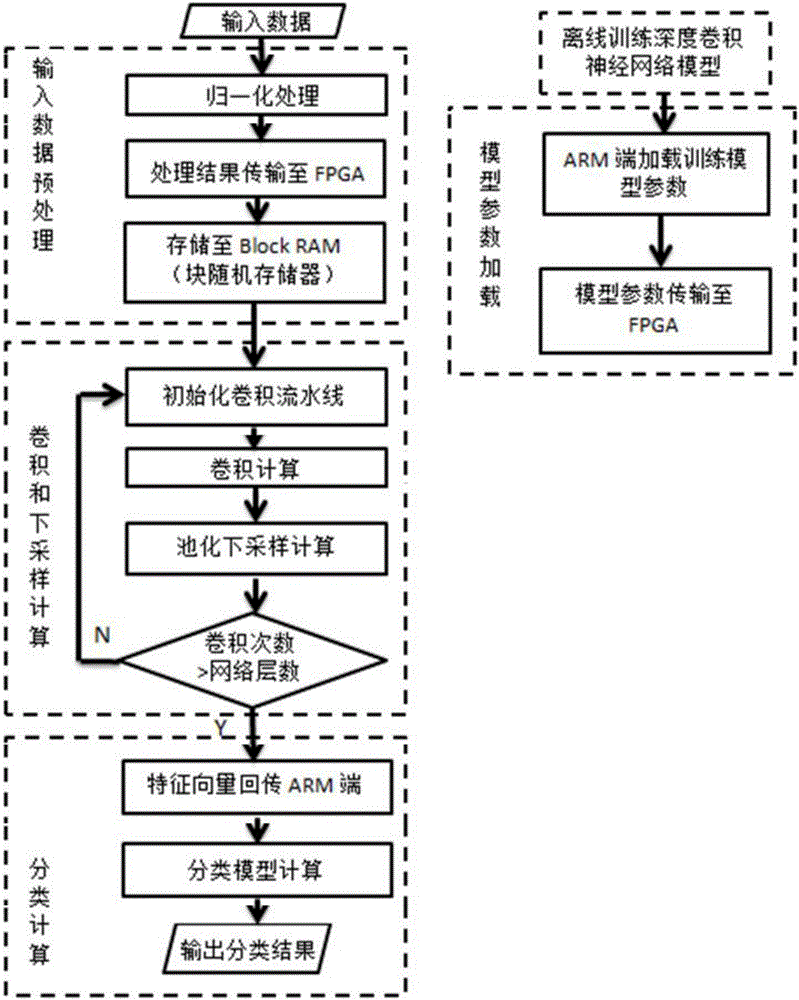
FPGA-based deep convolution neural network realizing method
ActiveCN106228240ASimple designReduce resource consumptionCharacter and pattern recognitionSpeech recognitionFeature vectorAlgorithm
The invention belongs to the technical field of digital image processing and mode identification, and specifically relates to an FPGA-based deep convolution neural network realizing method. The hardware platform for realizing the method is XilinxZYNQ-7030 programmable sheet SoC, and an FPGA and an ARM Cortex A9 processor are built in the hardware platform. Trained network model parameters are loaded to an FPGA end, pretreatment for input data is conducted at an ARM end, and the result is transmitted to the FPGA end. Convolution calculation and down-sampling of a deep convolution neural network are realized at the FPGA end to form data characteristic vectors and transmit the data characteristic vectors to the ARM end, thus completing characteristic classification calculation. Rapid parallel processing and extremely low-power high-performance calculation characteristics of FPGA are utilized to realize convolution calculation which has the highest complexity in a deep convolution neural network model. The algorithm efficiency is greatly improved, and the power consumption is reduced while ensuring algorithm correct rate.
Owner:FUDAN UNIV
Method for planning robot paths on basis of path expansion ant colony algorithms
ActiveCN106225788AImprove search abilityImprove algorithm efficiencyNavigational calculation instrumentsLocal optimumSimulation
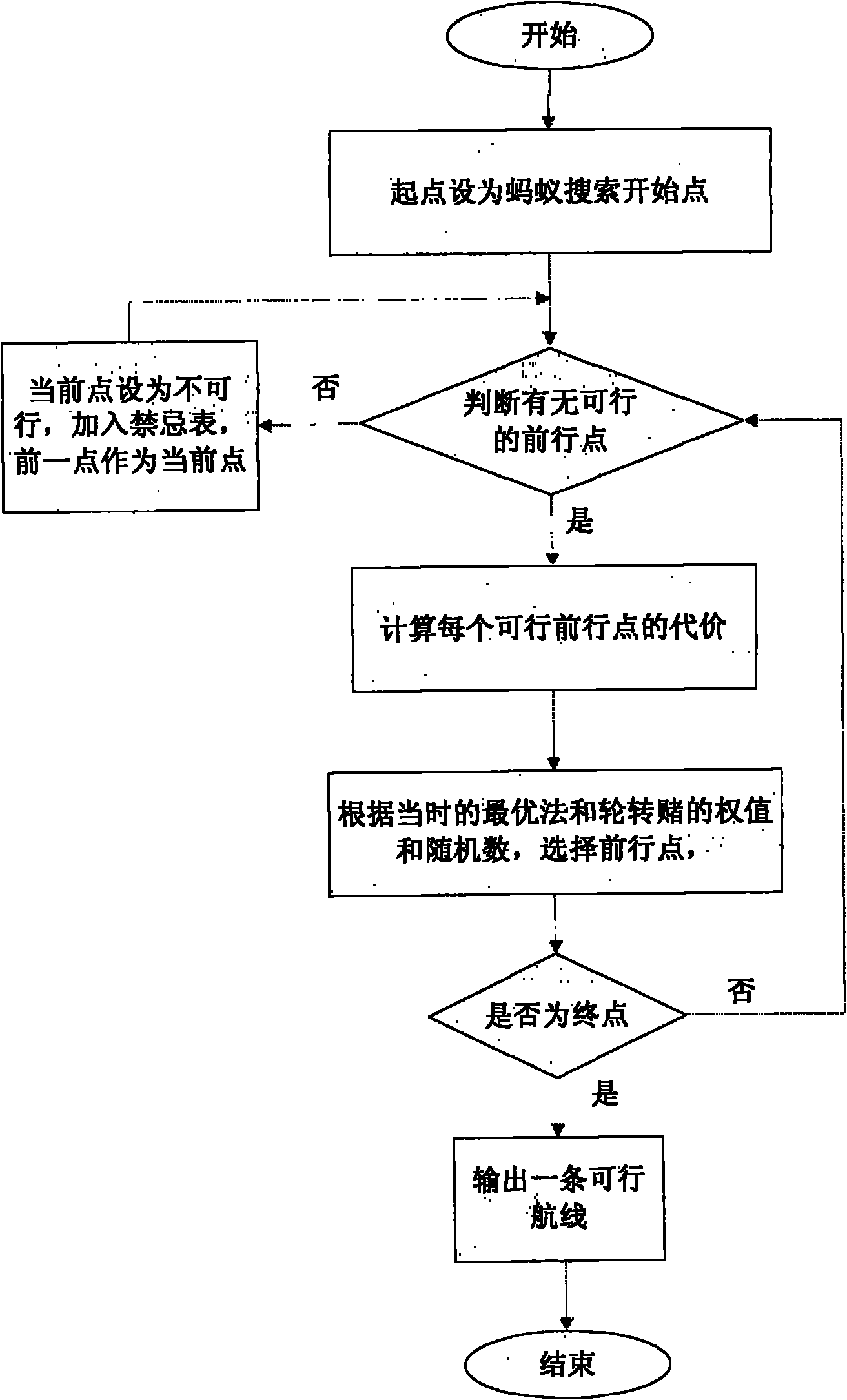
The invention relates to a method for planning robot paths on the basis of path expansion ant colony algorithms. The method has the advantages that the ant colony algorithms are applied to the field of robot path planning, path expansion ant colony algorithm optimization strategies are proposed, the robot path optimizing efficiency can be optimized, information element distribution time-varying characteristics, information element updating strategies, path location inflection point optimization and local optimal path expansion are introduced, and location inflection point parameters and general evaluation are additionally used as evaluation standards for the paths; as verified by simulation analysis and practical experiments on the three algorithms, the method is high in robot path planning and searching capacity on the basis of the path expansion ant colony algorithm optimization strategies and is high in algorithm efficiency, and the found paths are short; phenomena that the algorithms run into local optimization can be effectively inhibited, the optimal paths of robots can be searched, and the robots can quickly avoid obstacles to safely arrive at target points.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
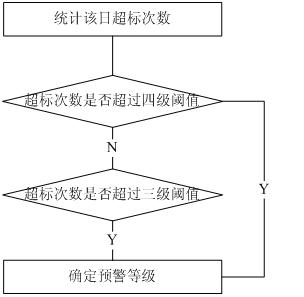
Early warning method of stable-state index of power quality
ActiveCN102170124AStructuredImprove accuracyAc network circuit arrangementsPower qualityQuality data
The invention discloses an early warning method of stable-state index of power quality. The method is realized by support from a power quality online monitoring device and a computer. The method is characterized by comprising the following steps of: (1) selecting power quality indexes in advance, including voltage deviation, voltage total harmonic wave, short time flicking, etc, and setting earlywarning threshold values at four grades; (2) acquiring power quality data in real time, and analyzing each power quality index to carry out early warning grading; and (3) saving the values calculatedand a final early warning grade into a database. The early warning method of stable-state index of power quality establishes an early warning structure with two types, including index standard-exceeding type and index abnormal type, and four grades, and adopts time sequence mining algorithm based on high-order statistics in abnormal mining link to analyze potential abnormity of power quality datawith skewness and peakedness. Practice proves that the early warning method is clear in hierarchy, high in algorithm efficiency, strong in accuracy and good in operability. The early warning method is high-efficient and comprehensive.
Owner:ELECTRIC POWER SCI RES INST OF JIANGSU ELECTRIC POWER +1
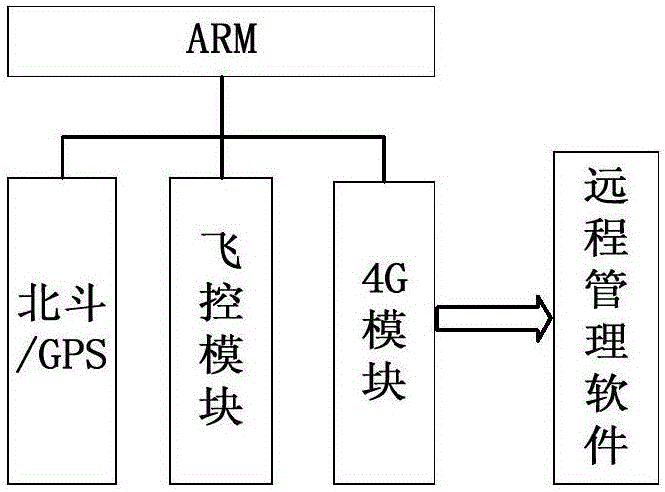
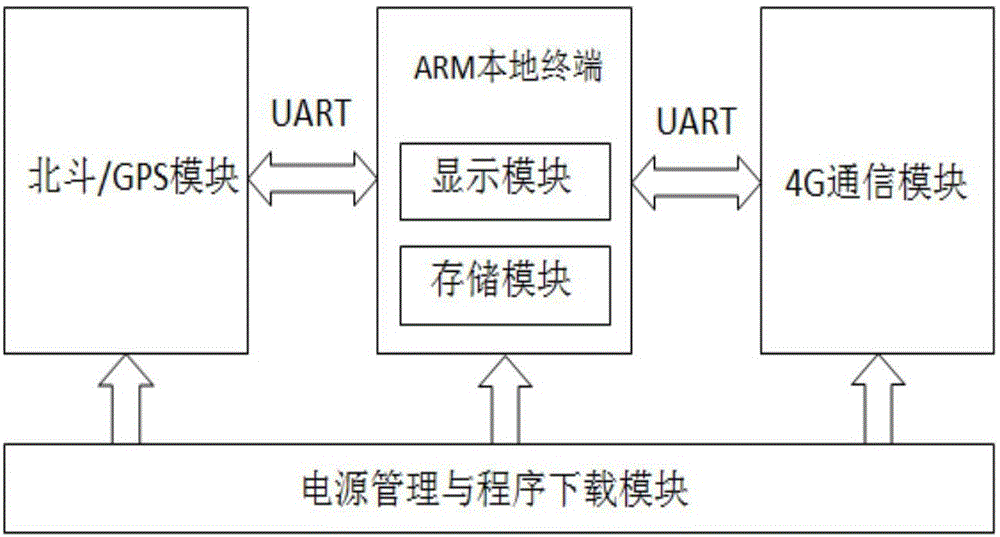
Electric fence monitoring method for unmanned aerial vehicle plant protecting operations
InactiveCN106406189AReliable out-of-bounds determinationEfficient cross-border judgmentProgramme controlComputer controlInformation processingFlight direction
The invention belongs to the technological field of agricultural plant protecting information processing, and discloses an electric fence monitoring method for unmanned aerial vehicle plant protecting operations. An agricultural plant protecting operation plot has boundaries and to ensure the security and efficiency of a plant protection unmanned aerial vehicle in executing the operations of plant protecting, the plant protection unmanned aerial vehicle should not trespass the boundaries. Therefore, it is necessary to monitor the electric fence for the unmanned aerial vehicle plant protecting operations. The method in doing so comprises the following steps: 1) generating in a dynamic manner a security boundary; 2) establishing a dual link communication system based on an unmanned aerial vehicle radio station and a 4G module; and 3) determining the boundary trespassing and the tendency of trespassing of the unmanned aerial vehicle so as to raise the detection efficiency of the boundary trespassing of the unmanned aerial vehicle. According to the invention, it is possible to make pre-warnings when there is tendency for the unmanned aerial vehicle to trespass the boundary so that the user of the unmanned aerial vehicle is able to change the flight direction instantly and that high efficiency unmanned aerial vehicle boundary trespassing can be detected. Therefore, the computational complexity is reduced greatly and the algorithmic efficiency is increased.
Owner:CHINA AGRI UNIV
Mobile robot path planning method in complex environment
InactiveCN104516350AImprove operational efficiencyMeet operational needsAdaptive controlPosition/course control in two dimensionsSimulationArtificial immune algorithm
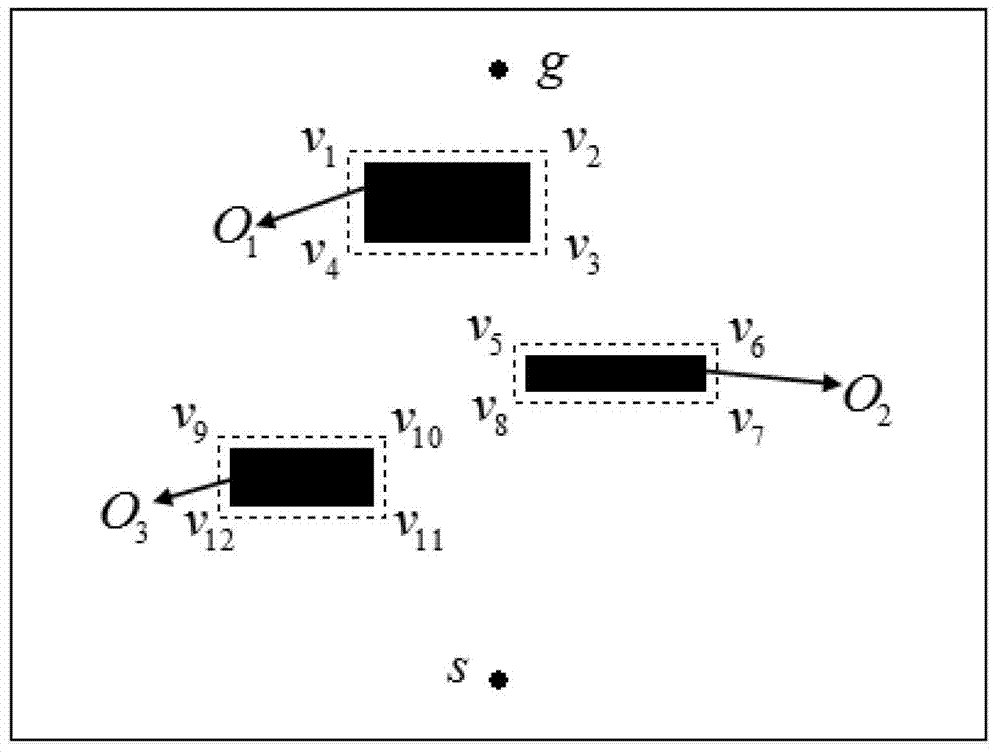
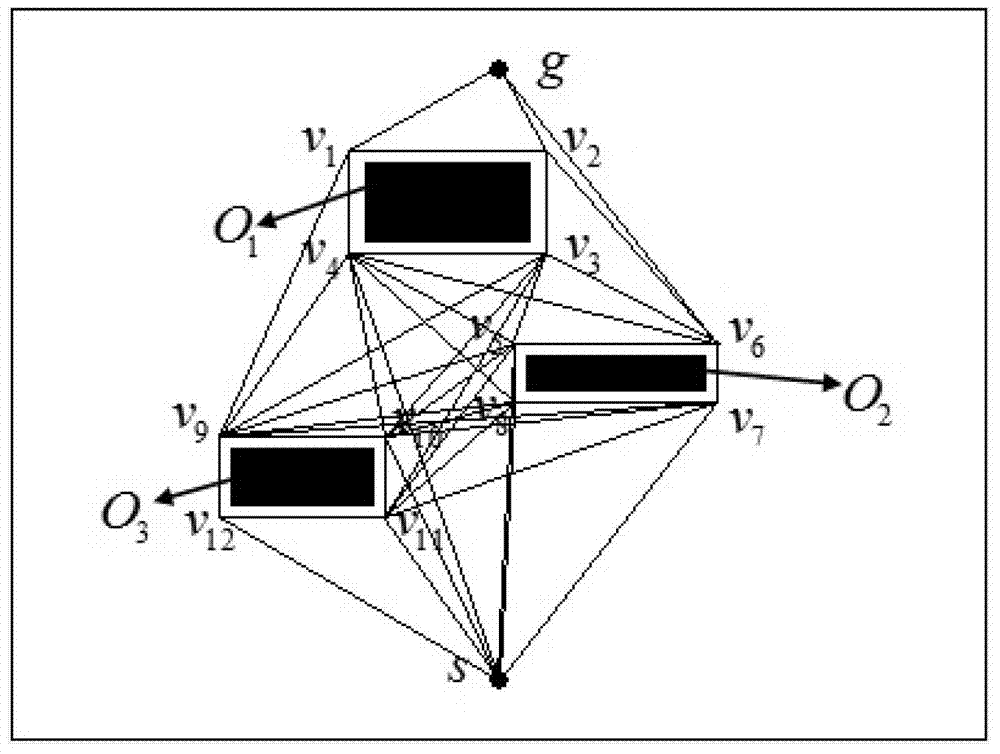
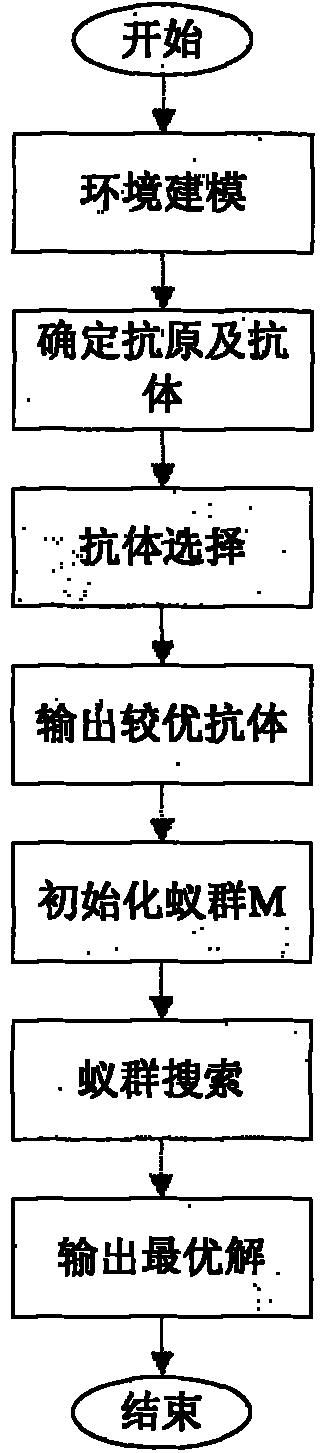
The invention provides a mobile robot path planning method in a complex environment. The method is characterized in that 1. information of environment in which a robot is positioned is acquired, and obstacles in the environmental space are indicated by using rectangular enclosing boxes after processing and displayed on a human-computer interaction module; 2. the initial position of the robot is confirmed and recorded as an initial point; a target position expected to be reached by the robot is confirmed and recorded as a target point; 3. the initial point, the target point and the vertexes of all the obstacle enclosing boxes meeting the condition are connected by using line segments, wherein the requirement indicates that the connecting line of any two points does not penetrate through the enclosing boxes, based on which a visual graph is constructed; 4. the optimal path is planned in the visual graph via an artificial immune algorithm, and key nodes in the optimal path are stored; and 5. The entity robot is controlled to start from the initial point, pass the key nodes in the optimal path one by one and finally reach the target point. Algorithm efficiency and convergence rate can be effectively enhanced under the premise of guaranteeing solution of the optimal path.
Owner:SHENYANG POLYTECHNIC UNIV
Crude oil blending multi-period optimized crude oil concocting and scheduling method
ActiveCN101286065ATotal factory controlAdaptive controlDistillationNonlinear mixed integer programming
The invention provides a crude oil blending scheduling method for crude oil blending multi-period optimization, belonging to the technical field of various crude oil blending. The method is characterized in that the mathematic model of the problem is induced; aiming at the non-linear mixed integer programming model induced from the problem, satisfactory solution of the problem is obtained by a high-effect mixed solving strategy. The method of the invention has the advantages that (1) the proposal takes improving the stability of the blending crude oil property as a main object, and takes improving the expected yield of the products as an object at the same time, can reduce the effects of excessively large fluctuation of blending crude oil property on the stability of distillation devices and subsequent devices of the distillation devices, and increase the expected yield of the products to a certain degree; (2) an algorithm structure of solving discrete decision variables and continuous decision variables by layers is adopted, thus improving the problems that the algorithm has low efficiency and poor searching performance, etc. which are caused by that the two groups of variables are optimized at the same time.
Owner:TSINGHUA UNIV
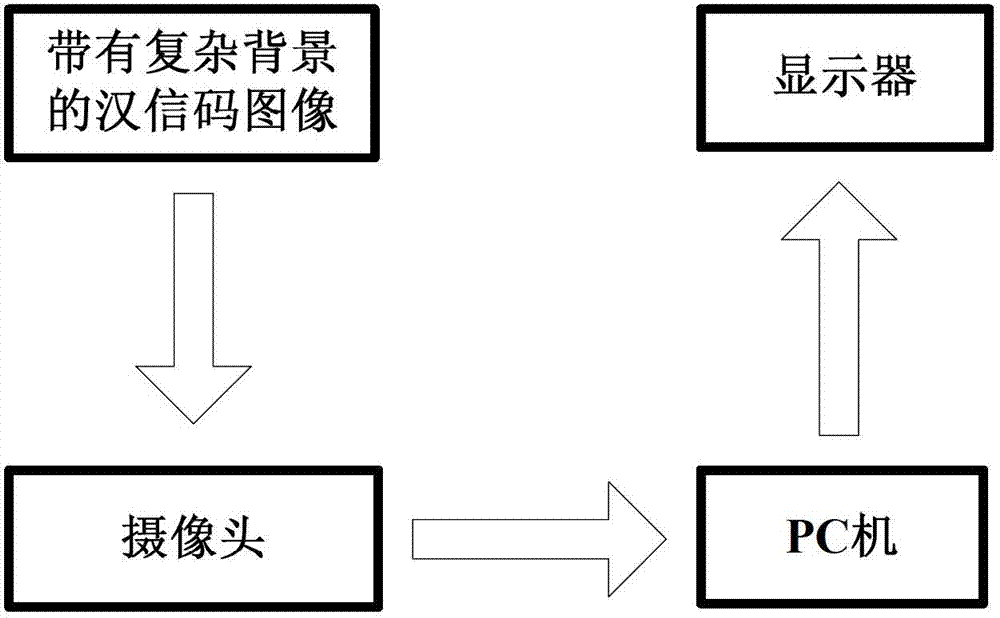
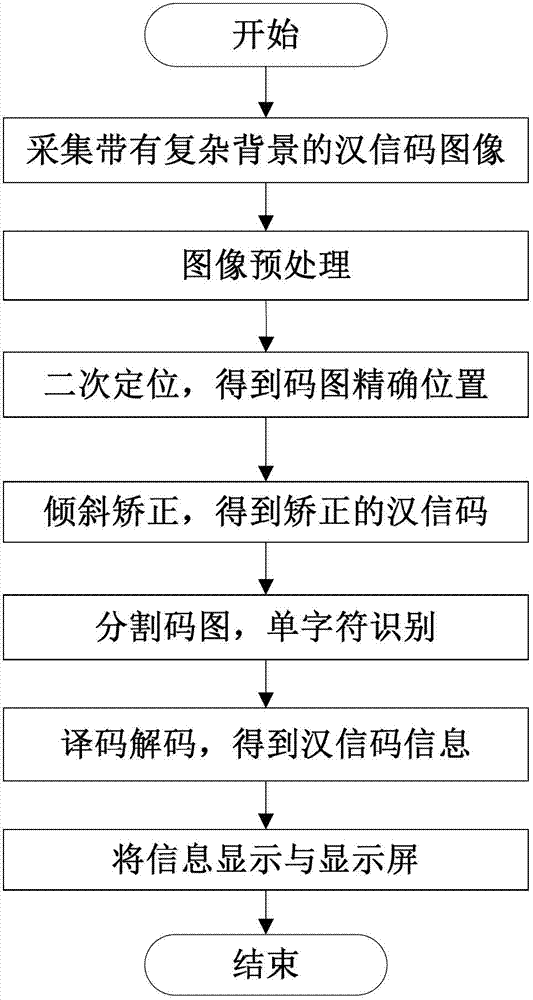
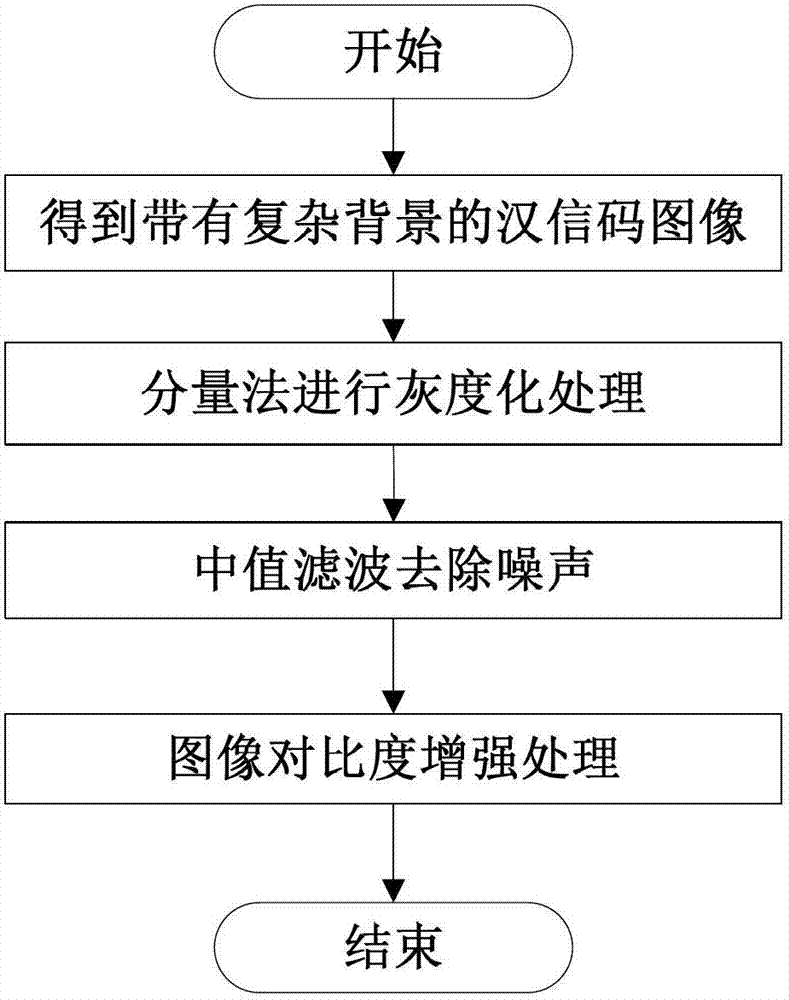
Chinese-sensible code recognition device and Chinese-sensible code recognition method under complicated background
InactiveCN103177235ALow efficiencyImprove efficiencyCharacter and pattern recognitionSensing by electromagnetic radiationImaging processingIdentification device
The invention belongs to the field of two-dimensional code recognition, relates to applications of image processing and character recognition technology and discloses a Chinese-sensible code recognition device and a Chinese-sensible code recognition method under a complicated background. The method comprises the following steps of: collecting a Chinese-sensible code image with a complicated background; preprocessing the collected image; carrying out secondary positioning on a Chinese-sensible code in the image to obtain the accurate position of the Chinese-sensible code; carrying out slant correction on the Chinese-sensible code obtained by positioning, thus obtaining the corrected Chinese-sensible code; partitioning the Chinese-sensible code by using an edge detection and projection algorithm to obtain a single-line Chinese-sensible code, and then carrying out single-character recognition; decoding to obtain Chinese-sensible code information; and displaying the Chinese-sensible code information on a display screen. According to the method disclosed by the invention, the location accuracy is improved, the efficiency of algorithm is high, the rate is fast, the anti-interference property is strong, the robustness is good, single-character bar codes can be recognized rapidly and effectively, the bar codes can be recognized accurately, and the efficiency of Chinese-sensible code recognition is greatly improved.
Owner:HOHAI UNIV CHANGZHOU
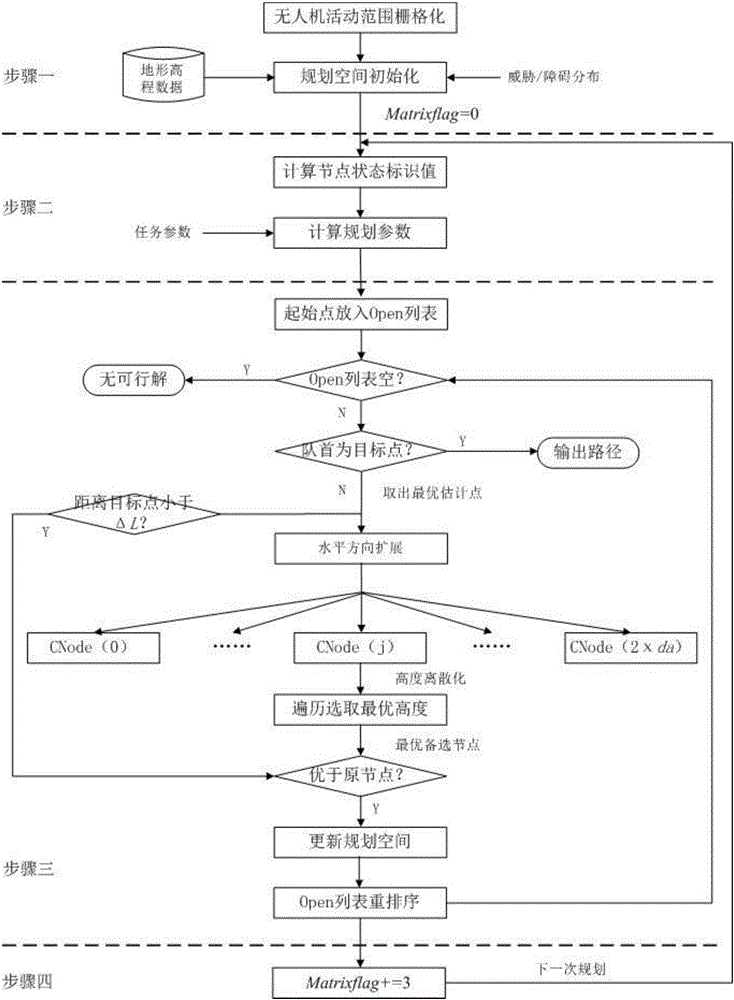
Unmanned aerial vehicle three-dimensional airway planning method based on space compression and table-lookup calculation
ActiveCN105737819AImprove re-planning abilityReduce the numberNavigation instrumentsRelationship - FatherUncrewed vehicle
The invention provides an unmanned aerial vehicle three-dimensional airway planning method based on space compression and table-lookup calculation, and mainly relates to the field of airway planning, in particular to the field of unmanned aerial vehicle three-dimensional airway planning. Unmanned aerial vehicle online rapid three-dimensional airway planning is achieved. On the basis of the standard A* algorithm, jump extension of the similar sparse A * algorithm is adopted, child nodes are changed to plane discretization distribution, and by means of a way of optimal compression in the height direction, the relative relation between the child nodes and a father node is calculated in advance, tabulated and stored; the table is looked up to obtain a value for each time of extension, the search space data structure is improved, the planning space can be repeatedly used during repeated airway planning, and the reinitialization time is saved. According to the method, on the basis of reserving the advantages of an original algorithm, the number of the nodes is greatly reduced, the algorithm efficiency is improved, and the replanning ability of the algorithm is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Image restoration method
InactiveCN101635050AEffective recoveryImprove image qualityImage enhancementImage analysisImaging qualityImage restoration
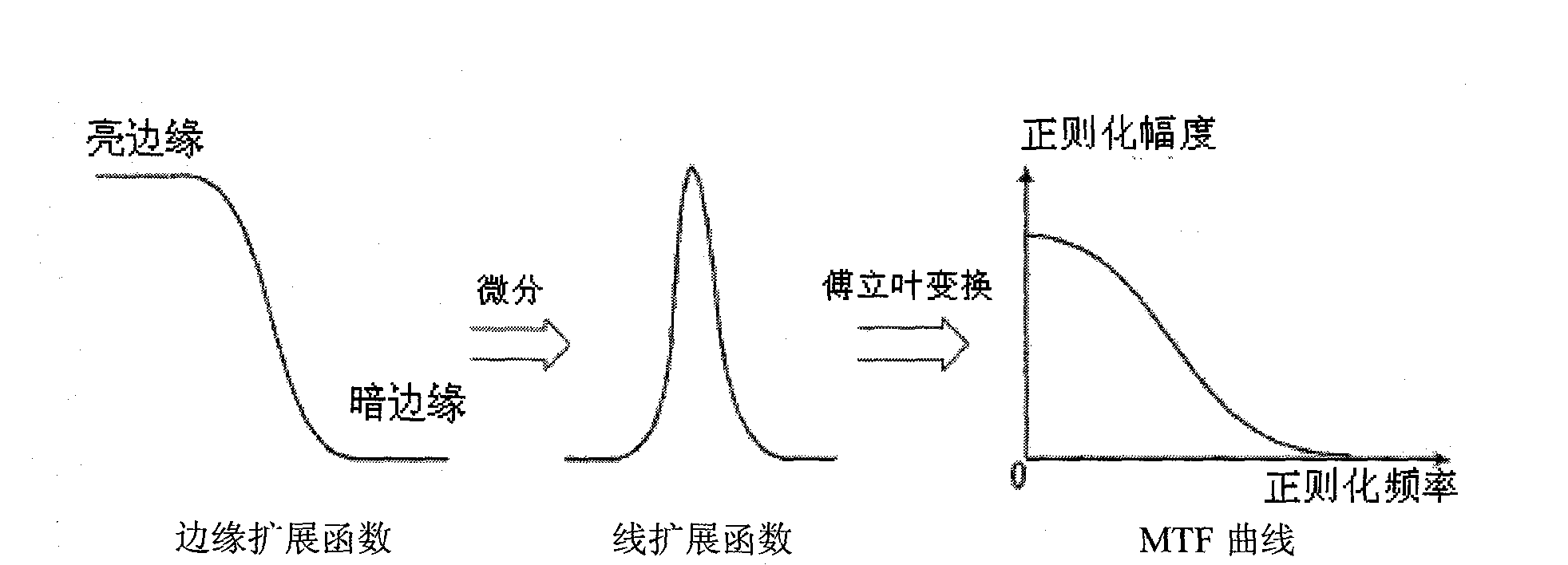
An image restoration method based on MTF includes the following steps: firstly, calculating MTF curve of an image; secondly, constructing dimensional MTF matrix; thirdly, carrying out image restoration in frequency domain by utilizing the MTF matrix. The method aims at remote sensing image with large data volume and is based on MTF theory and image quality degradation theory; and the method provided by the invention is effective for image restoration. Practice shows that the method can effectively restore image and improve image quality and has high algorithm efficiency. Currently, the method is successfully applied in domestic ground satellite pre-treatment system, and practice shows that the method is correct, feasible and universal.
Owner:WUHAN UNIV
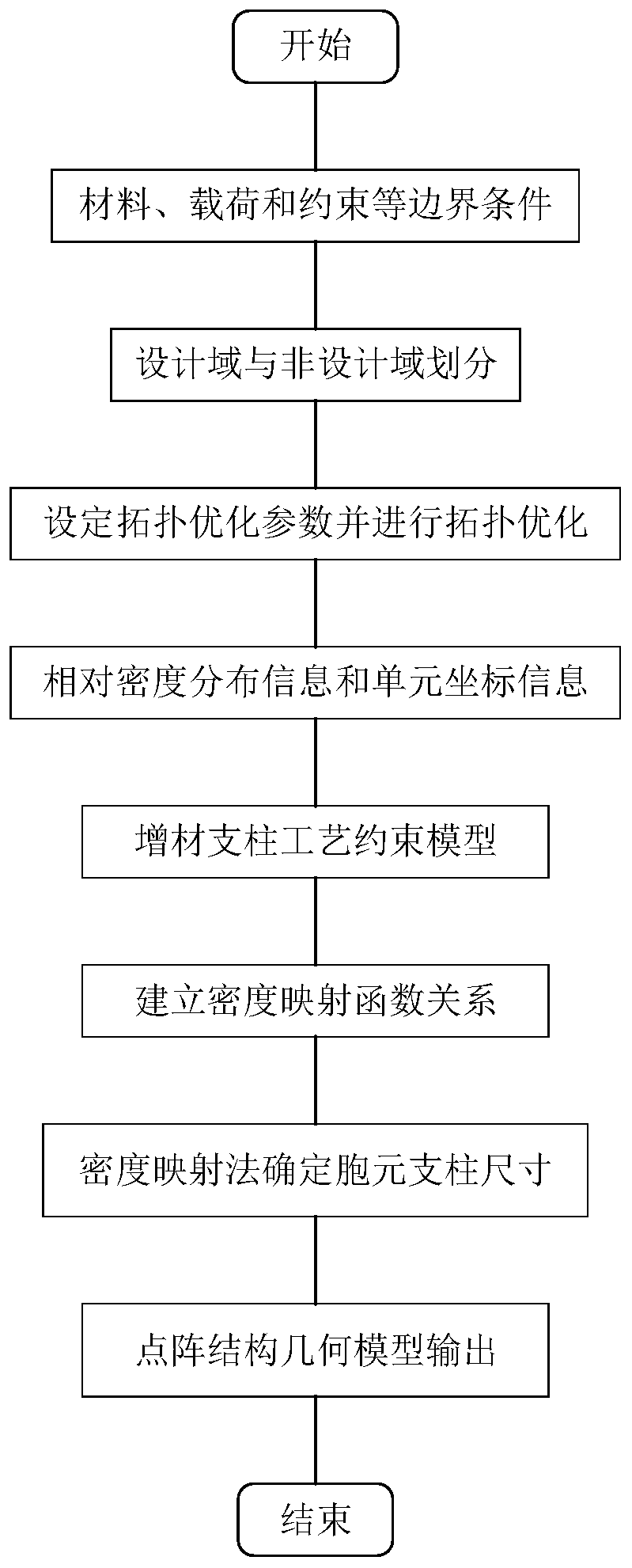
Gradient dot matrix structure design method based on topological optimization
ActiveCN109766656AGuaranteed reasonablenessImprove efficiencySpecial data processing applicationsDot matrixMathematical model
The invention discloses a topological optimization-based gradient lattice structure design method, which comprises the following steps of: 1, establishing a geometric model of an initial structure, and determining a design domain and a non-design domain; 2, setting topological optimization parameters, and determining an optimal force transmission path and relative density distribution informationof the initial structure; 3, extracting relative density information of the finite element unit, a Mizeasts stress value and coordinate information of the finite element unit; 4, selecting a proper cell to fill the structural design domain, and deleting repeated support columns in the lattice structure; 5, establishing a mathematical model of additive manufacturing process constraint; 6, establishing a mapping function relationship among the unit stress value, the relative density value and the lattice cell pillar size, and determining the pillar size; And 7, outputting a final geometric modelof the lattice structure. The distribution reasonability of the structural material can be ensured; The repetition of a topological optimization process is avoided, and the algorithm efficiency is high; The method can be suitable for the lattice design of complex geometric configurations; And a lattice structure with gradient change of the pillar size can be established.
Owner:BEIHANG UNIV
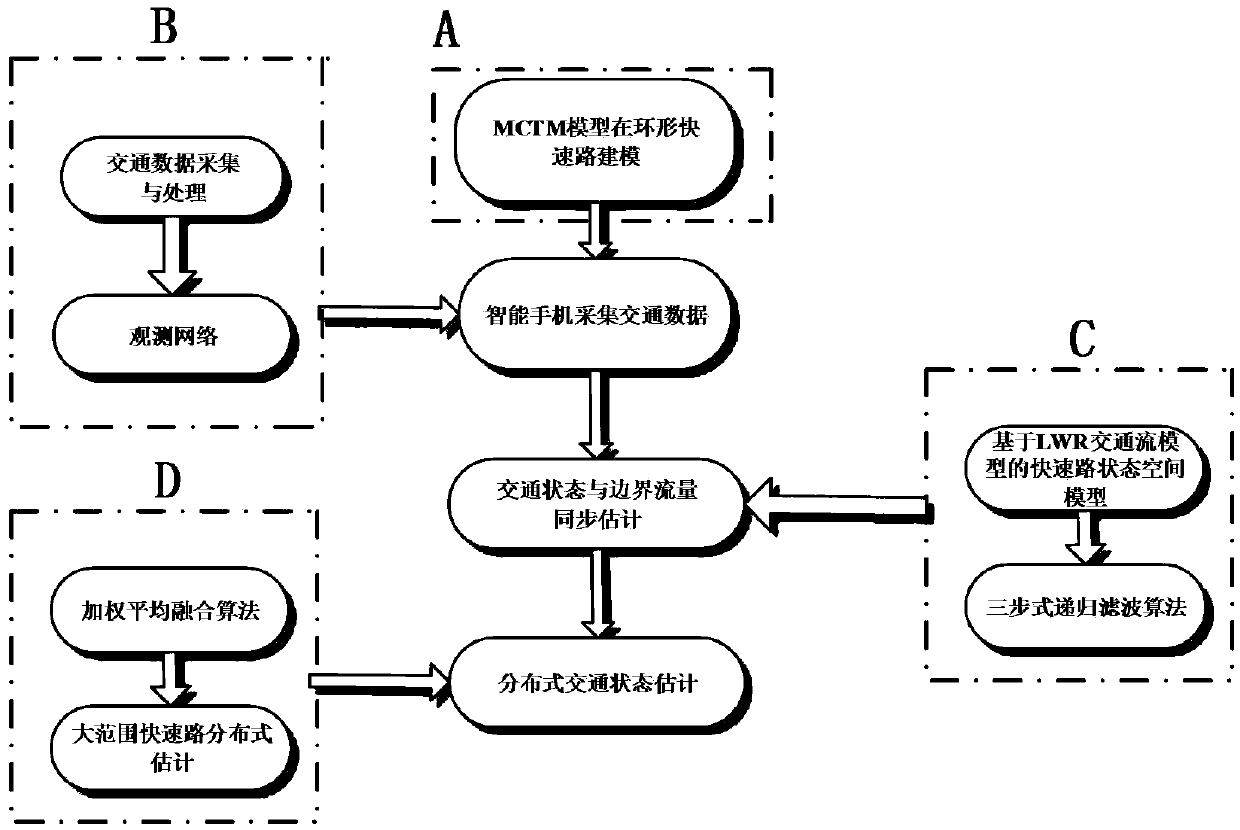
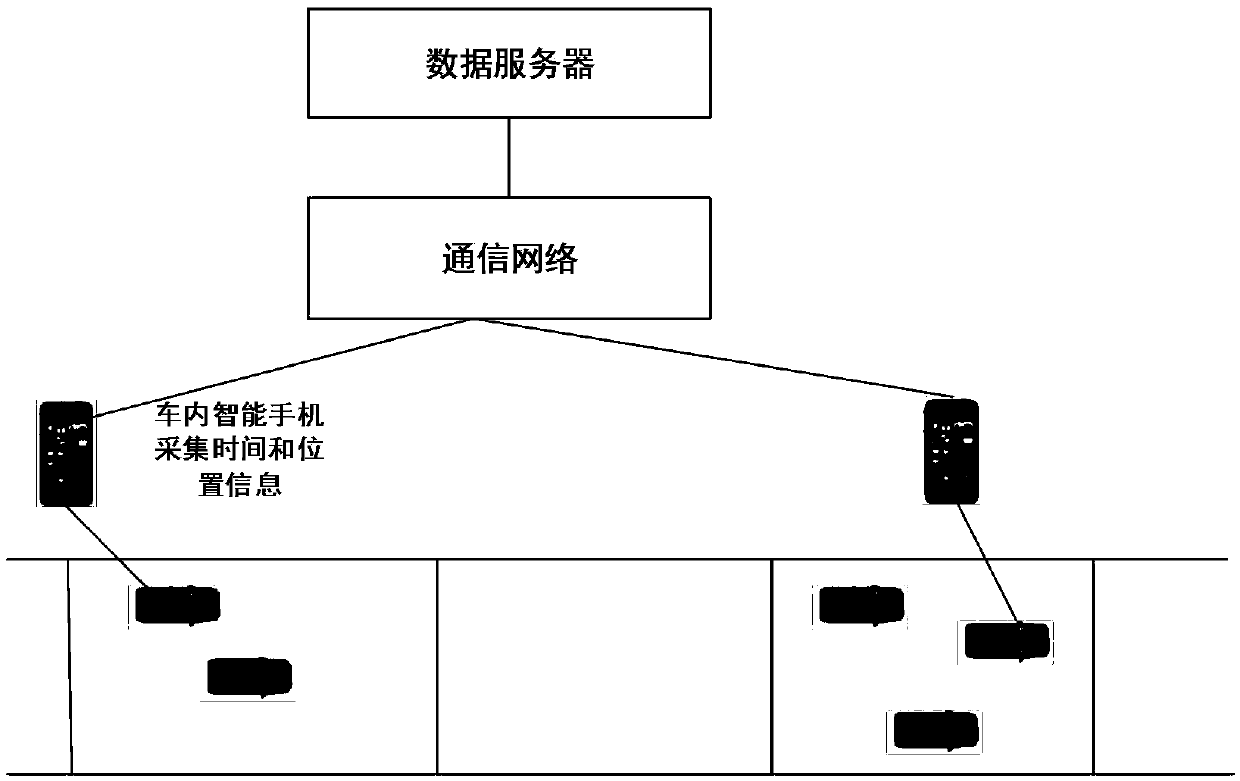
Method for estimating city expressway traffic states based on mobile detection of smartphones
ActiveCN105513359AReduce collection costsSend smallDetection of traffic movementReduced modelTraffic flow modeling
The invention discloses a method for estimating city expressway traffic states based on mobile detection of smartphones, wherein a city expressway cell transmission model is built firstly, a observing network is built by adopting a smartphone to rapidly detect parameters, then a state space model based on a lighthill-whitham-richards (LWR) traffic flow model is designed, a traffic state and a boundary flux are synchronously estimated by utilizing three-step type recursive filters algorithm, then are coalesced with upstream and downstream subsection boundary flux by adopting a weighted average algorithm, and traffic parameter estimation is upgraded, thereby achieving real-time distributed estimation of city expressway network traffic state. The method for estimating the city expressway traffic states based on the mobile detection of the smartphones can collect average speed information of vehicles on any time and space positions of a loop, enables traffic estimation not to be restrained by the position of a detector, can achieve synchronization estimation of traffic density and boundary flux by designing a state-space model and a three-step recursive filter, and achieves the problem of large range expressway network traffic estimation by being coalesced with subsection boundary flux, reduces model order, and improves efficiency of algorithm.
Owner:中国冶金科技成果转化有限公司
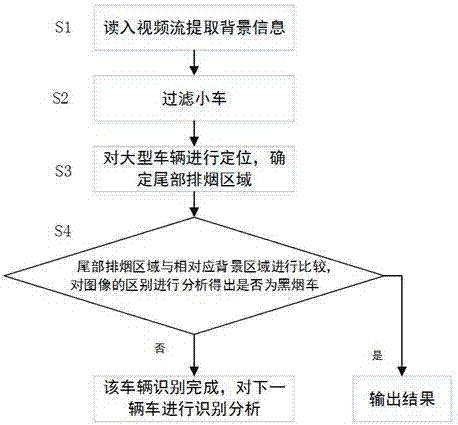
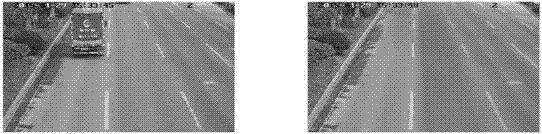
Intelligent monitoring and identification method for vehicles exhausting black smoke based on image processing technology
InactiveCN106951821AImprove efficiencyReduce data volumeCharacter and pattern recognitionData streamFilter algorithm
The invention discloses an intelligent monitoring and identification method for vehicles exhausting black smoke based on an image processing technology. The method comprises the following steps: S1, using a video capture card to collect a high-definition real-time video data stream of a traffic checkpoint; adjusting the time of interval sampling according to the degree of pavement change by use of a variable-interval background mean sampling technology, and extracting payment background information by use of a multi-frame image mean algorithm; S3, according to the collected video stream, removing small vehicles and non-motorized vehicles from each frame of image in real time by use of a small vehicle filtering algorithm, so as to reduce the amount of data of image processing and improve the efficiency of the algorithm; S4, positioning tail flue gas of large vehicles in each frame of image; and S5, comparing the data of a positioning area image and the data of a background area image of exhaust gas emission to judge whether the vehicles are vehicles exhausting black smoke. The intelligent monitoring and identification method for vehicles exhausting black smoke disclosed by the invention can improve the detection efficiency. Whether a vehicle exhausts black smoke is judged by use of the computer technology.
Owner:XIANGTAN UNIV
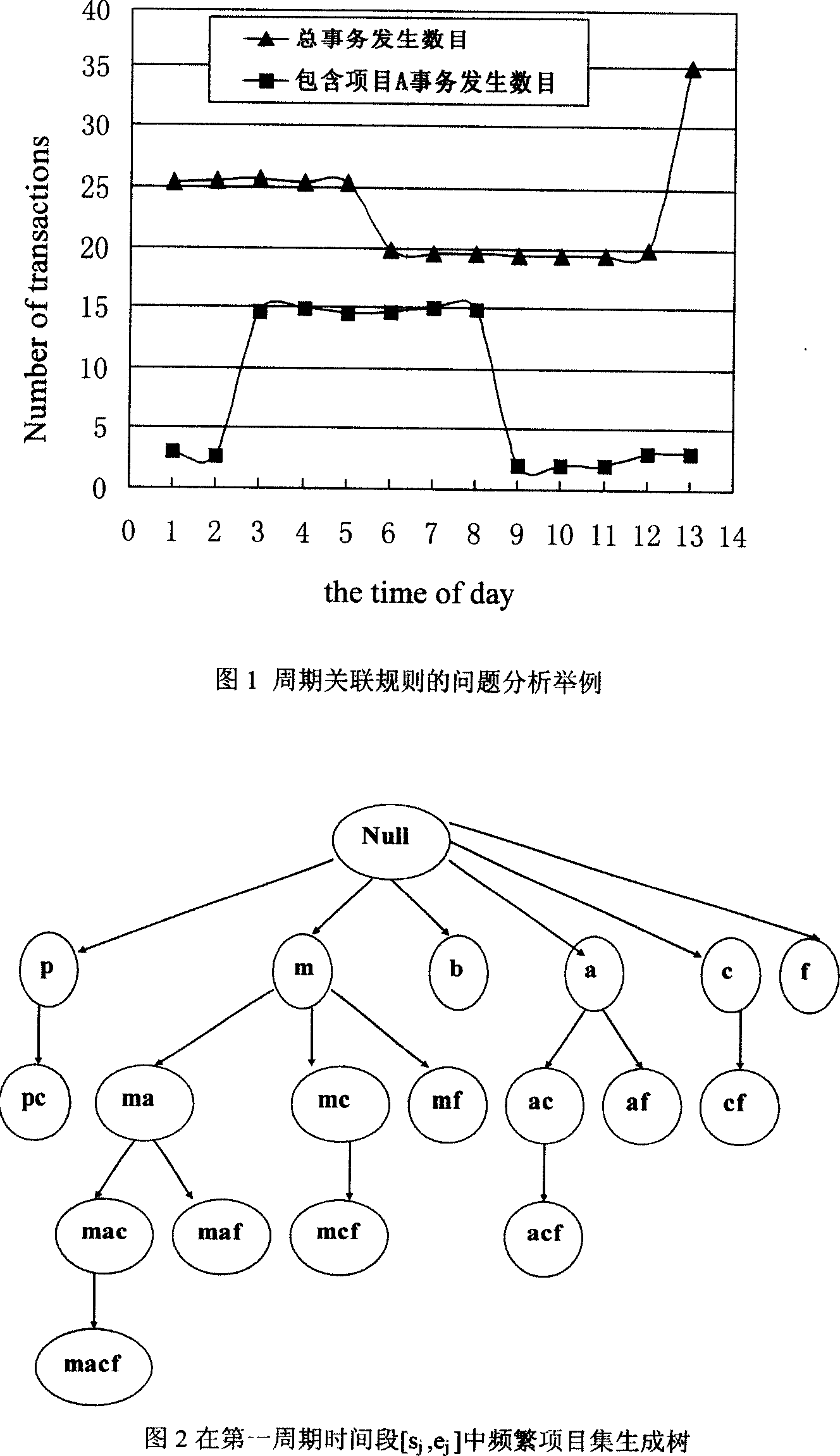
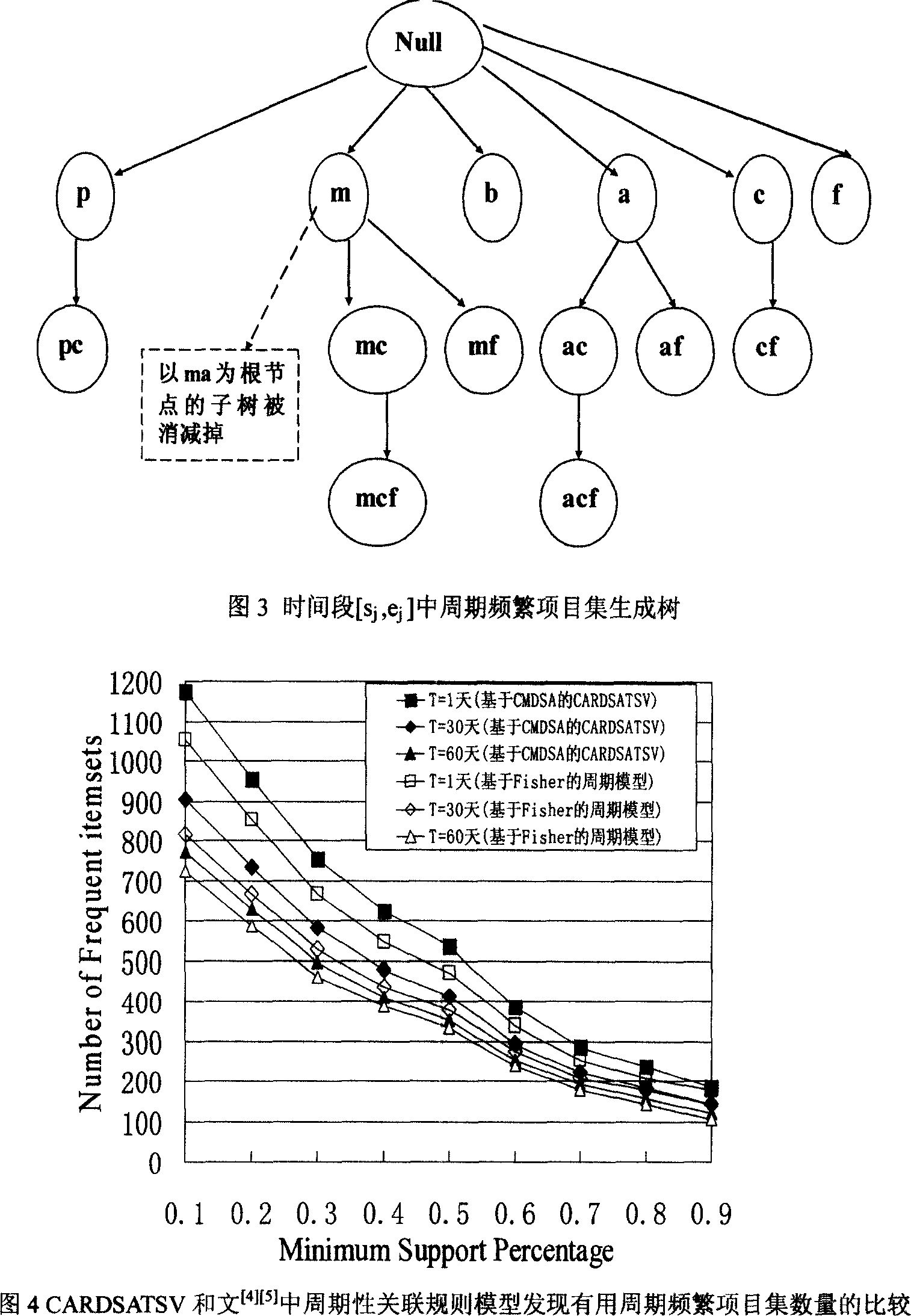
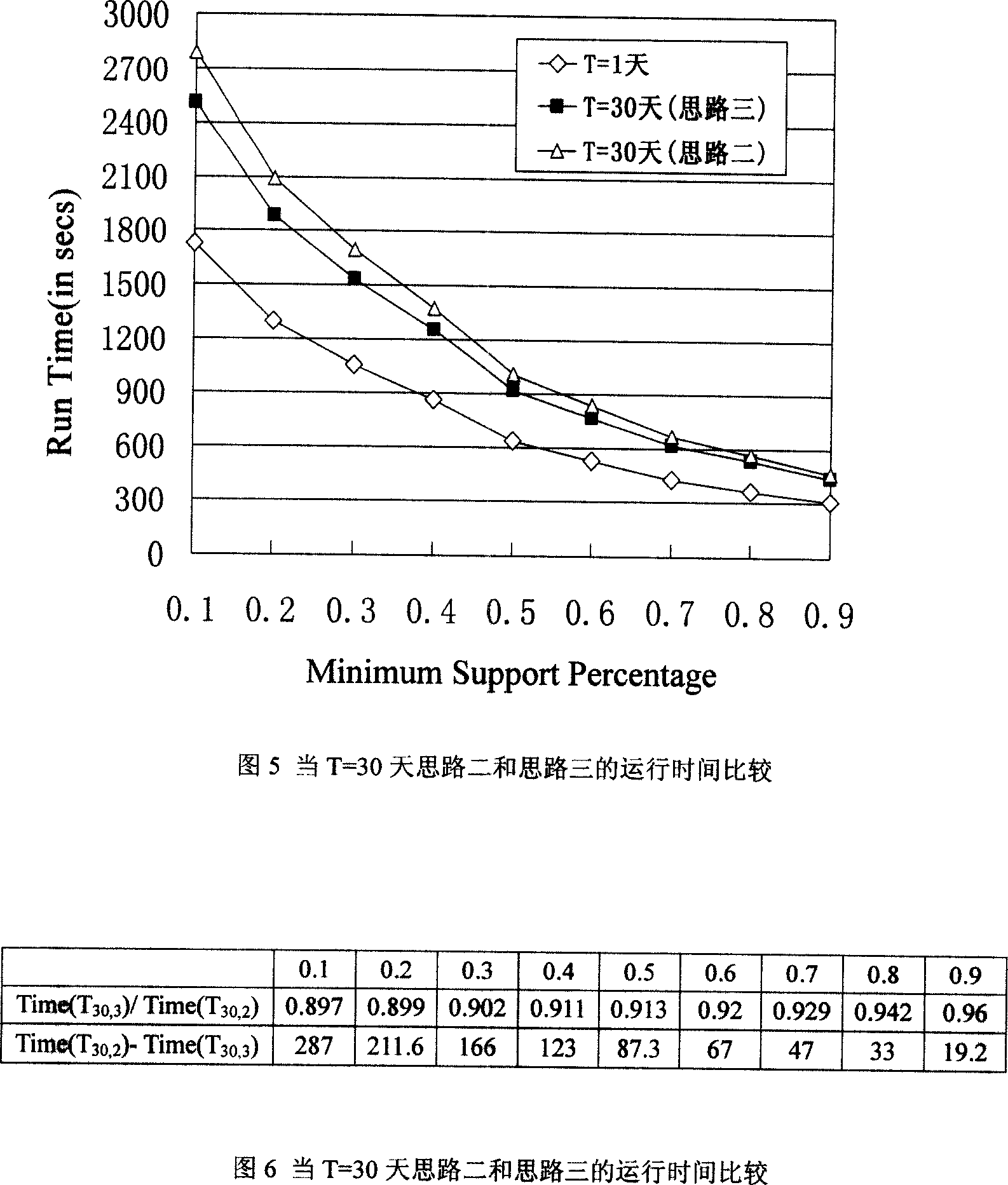
Periodic associated rule discovery algorithm based on time sequence vector diverse sequence method clustering
InactiveCN101127037AImprove efficiencyImprove clustering effectSpecial data processing applicationsTime domainAlgorithm
The utility model relates to a discovering algorithm with clustered cycling associated rule, based on a differing sequence method of time series vector. Firstly, in view of the drawback of the current discovering algorithm with cycling associated rule on the problem of dividing a plurality of time domains, an algorithm called CMDSA is proposed. The algorithm selects a time series vector which comprises a item supporting degree as the data character in time area to cluster; meanwhile, the clustering number is controlled by a DB principle to reach the best clustering result, so that each time area under the cycling associated rule can be identified more accurately and more useful cycling associated rules can be found compared with the current algorithm. Aiming at the fact that all the current algorithm of cycling associated rule are based on the Apriori algorithm and the efficiency is low, an algorithm of CFP-tree based on Fp tree is proposed. The algorithm of CFP-tree adopts cycling tailoring technique based on the condition FP tree to enhance the algorithm efficiency. Thus, the adoption of the discovering algorithm with cycling associated rule of CFP-tree is far better than the prior algorithm based on Apriori in the time and space efficiency.
Owner:杭州龙衍信息工程有限公司
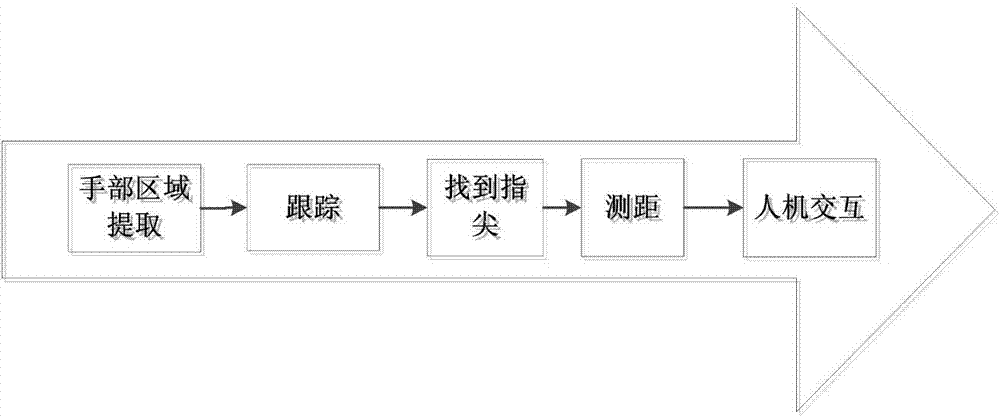
Interactive projection method and system based on active vision
ActiveCN103677274ARobust recognitionEfficient identificationInput/output for user-computer interactionCharacter and pattern recognitionSkin colorHuman–computer interaction
The invention discloses an interactive projection method and system based on active vision. The method includes the steps that frames needing interaction are projected onto any plane by a projector, information of operation on the projected interaction frames carried out by a user is collected through a shooting device, the shot information is transmitted to a processing unit to be analyzed and processed, and thus corresponding operation of the user is acquired so as to achieve human-computer interaction. An offline training mode is adopted for the processing unit, and thus the detection efficiency is promoted. When data are trained, a new training mechanism is provided, and thus a large amount of manual operation is reduced. In the detection process, a model which is updated in real time is adopted, namely, a current skin color model is only relevant to the last several frames of skin colors, and thus influences of illumination on the skin colors can be effectively eliminated, the algorithm efficiency is effectively improved, and the real time requirement can be totally met.
Owner:GUANGDONG VTRON TECH CO LTD
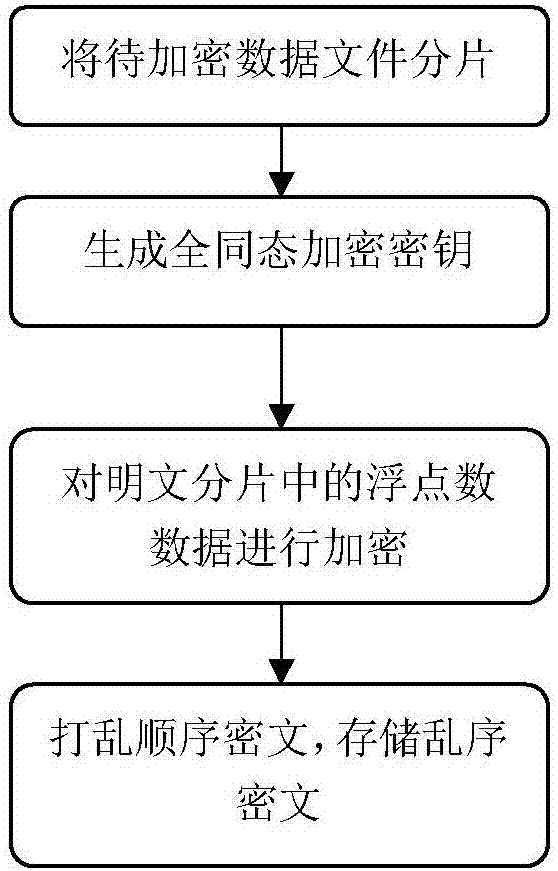
Parallel fully-homomorphic encryption and decryption methods supporting floating point arithmetic
ActiveCN107317666AEnsure safetyWon't swellKey distribution for secure communicationCommunication with homomorphic encryptionPlaintextComputer hardware
The invention provides a parallel fully-homomorphic encryption method supporting floating point arithmetic, and belongs to the technical field of information security. The encryption method comprises the three steps of encryption key initialization, plaintext data encryption and out-of-order storage of child ciphertext, and by means of a parallel computing mechanism of a cloud computing environment and grouped encryption on plaintext data, a whole to-be-encrypted file is encrypted and then stored in a storage system of the cloud computing environment. The invention further provides a decryption method based on the parallel fully-homomorphic encryption method, an addition homomorphic encryption method and a multiplication homomorphic encryption method. According to the methods, the algorithm is simple, easy to achieve, high in security and capable of supporting homomorphic addition and multiplication at any depth and has the compact characteristic; and the efficiency of the algorithm can be further improved through parallel frameworks such as Spark, and the methods are suitable for the cloud computing environment.
Owner:深圳大道云科技有限公司
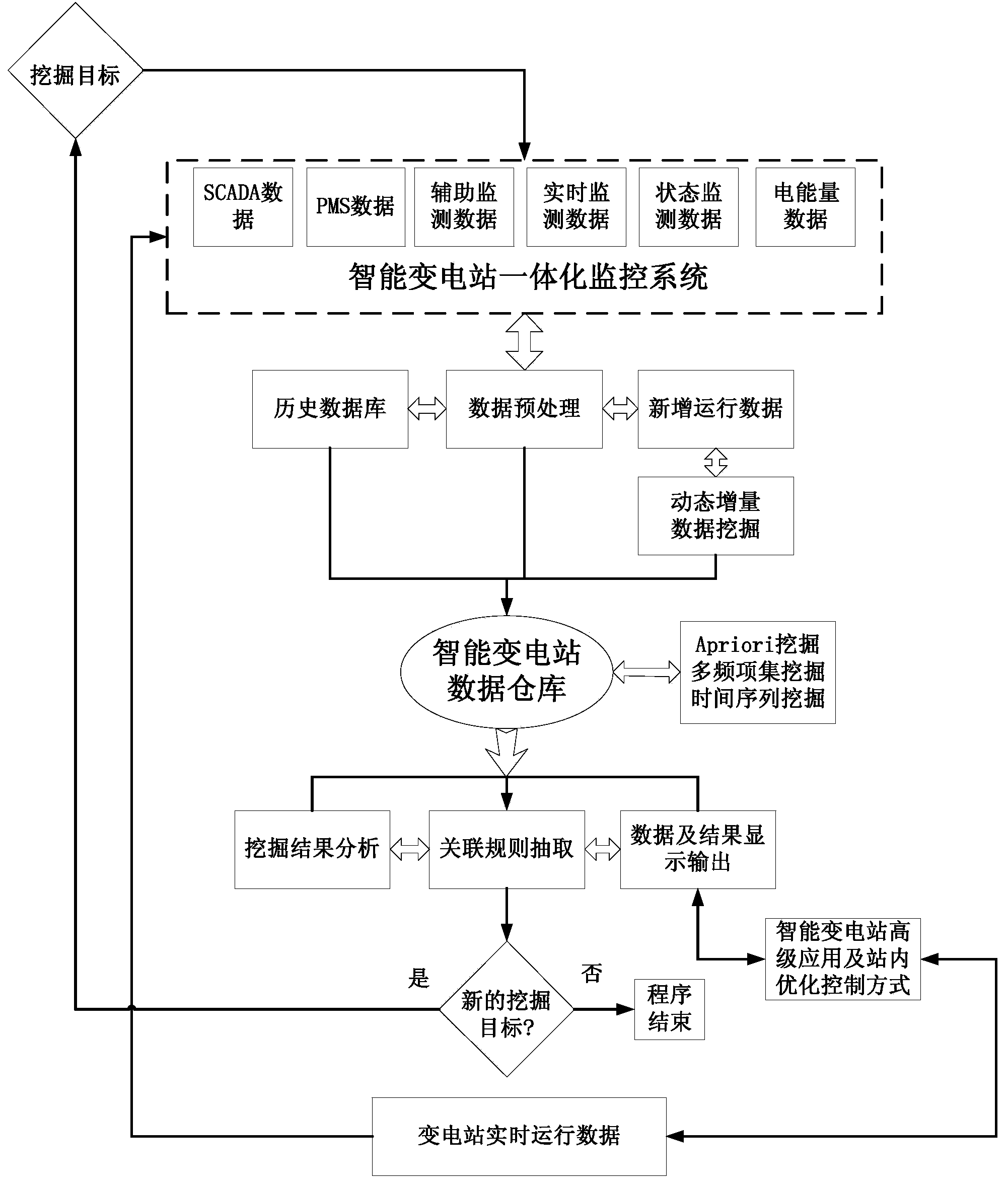
Data mining method applicable to integrated monitoring system of intelligent substation
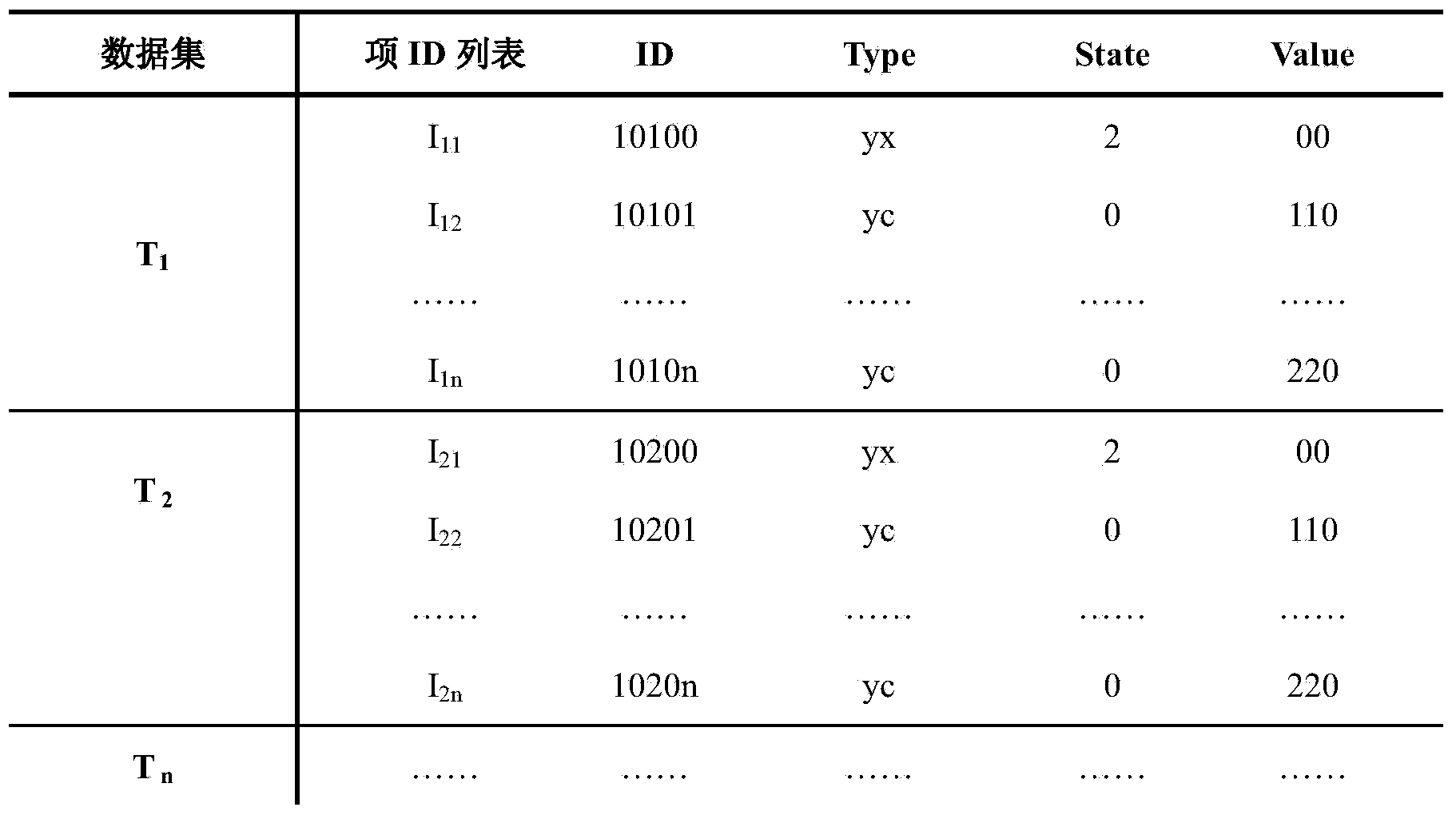
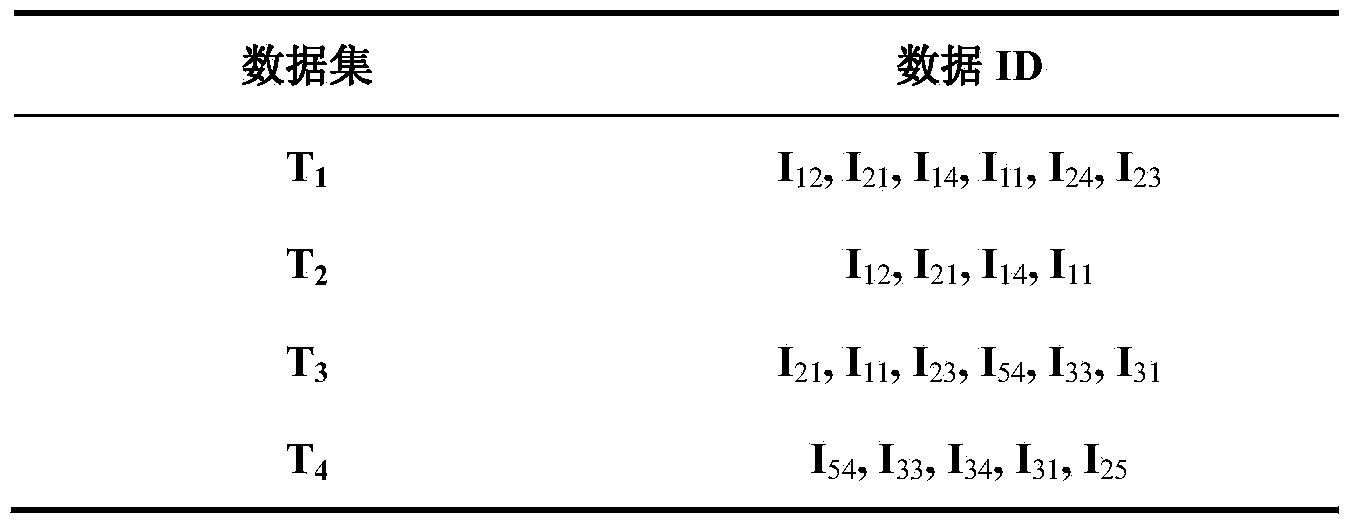
ActiveCN103455563AMeet the requirements of operating proceduresSimple calculationData processing applicationsSpecial data processing applicationsData setSmart substation
The invention provides a data mining method applicable to an integrated monitoring system of an intelligent substation. The data mining method comprises the following steps of: classifying and preprocessing substation data; dividing the discrete time of the preprocessed substation data to form a data set; mining the substation data so as to mine data member association rules in a historical database; mining additional substation data so as to mine the additional substation data and the data member association rules in the historical database; outputting the data member association rules to the outside. By data weight counting, the data rule strength has a quantitative index for subsequent application analysis and processing; the additional data are separately and dynamically mined and the additional data blocks are independently operated, the algorithm efficiency is greatly improved, and a knowledge base can self-learn periodically and can be automatically updated. The same reliable event data are provided for the advanced application of the intelligent substation, and the safe operation level of the intelligent substation is improved.
Owner:STATE GRID CORP OF CHINA +2
Weight matrix-based improved ant colony path planning method
PendingCN109489667AImprove efficiencyIn line with the actual industrial sceneNavigational calculation instrumentsNavigation by speed/acceleration measurementsAlgorithmSite Visit
The invention relates to a weight matrix-based improved ant colony path planning method. The weight matrix-based improved ant colony path planning method innovatively introduces the weight matrix intopath planning to improve the algorithm efficiency, optimize the values of initial pheromones and reasonably limit residual pheromones and path weights. The weight matrix-based improved ant colony path planning method can achieve humanized path planning according to practical application context and avoid repeated site visiting to acquire the shortest and optimal path, thereby greatly improving the practical operation efficiency.
Owner:CHUTIAN INTELLGENT ROBOT CHANGSHA CO LTD
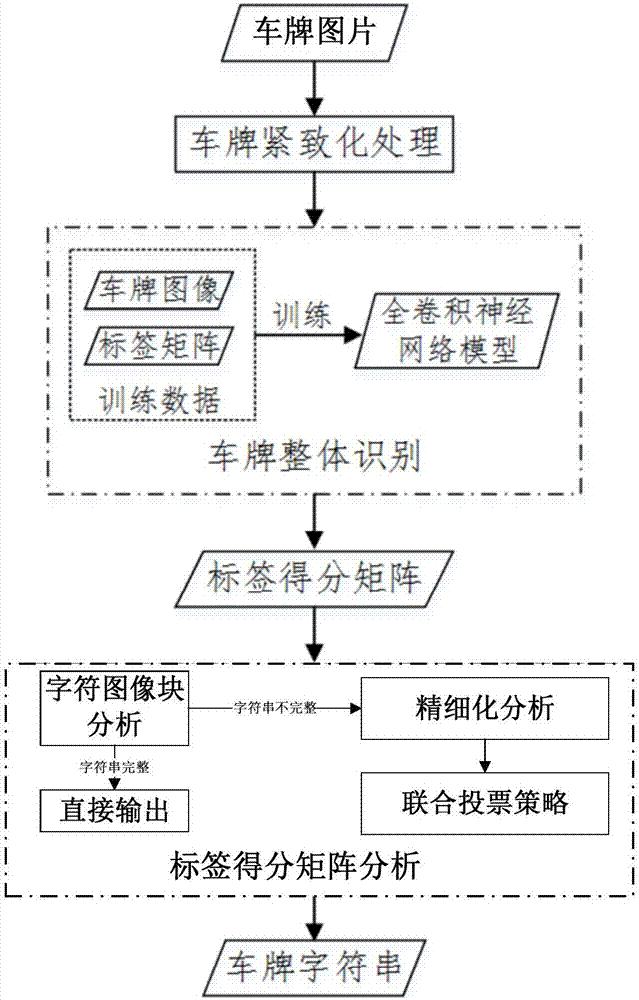
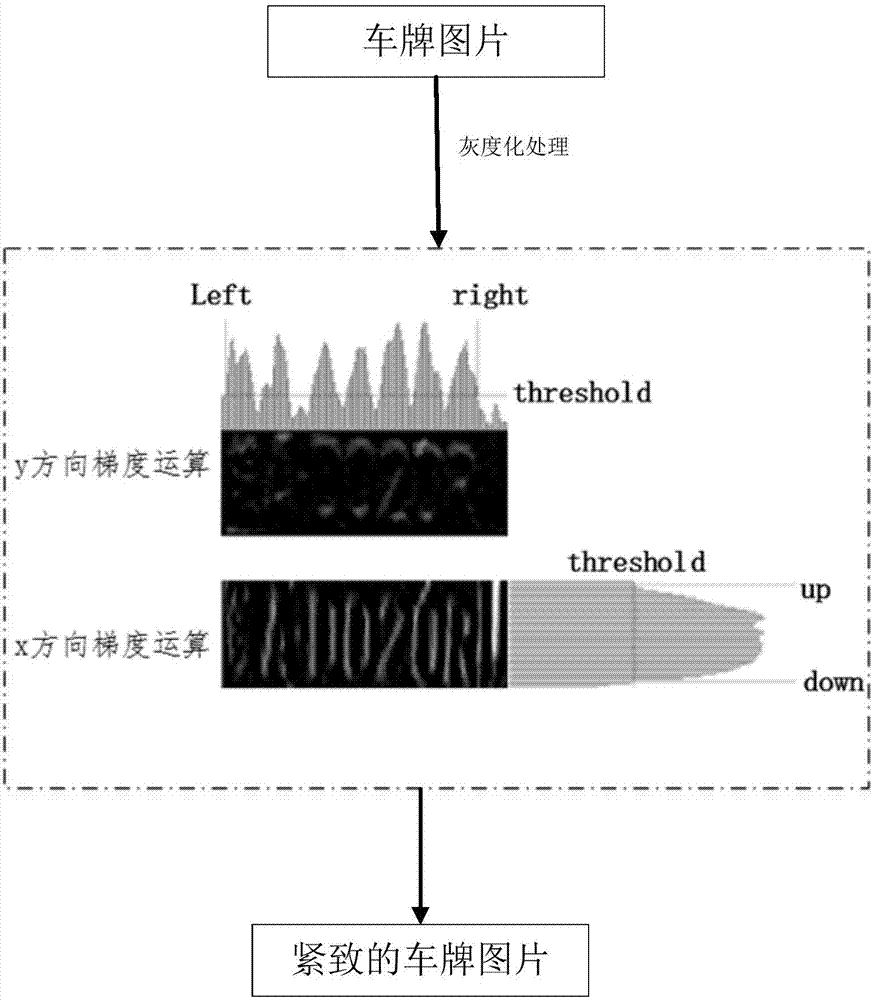
High efficiency accurate license plate identification method
ActiveCN107239778AImprove efficiencyImprove robustnessCharacter and pattern recognitionNerve networkMatrix analysis
The invention discloses a high efficiency accurate license plate identification method comprising the following steps: carrying out license plate compactification treatment on an input license plate image so as to obtain a compactification license plate image; using a pre-trained all convolution nerve network model to carry out license plate integral identification, thus obtaining prediction results of each pixel point character class in the compactification license plate image, and forming a label score matrix; parsing the label score matrix so as to obtain the final license plate string information. The method needs no character segmentation, thus solving the problems that an existing method is poor in character segmentation robustness; in addition, the method uses the all convolution nerve network model to carry out license plate integral identification, only one identification process is needed, so the algorithm efficiency is high; the complete context information of the license plate can be combined in the identification process, thus greatly improving the identification accuracy and robustness; finally, in label matrix analysis, the method can carry out difference treatments on different license plate and characters, thus further improving the algorithmic robustness and applicability.
Owner:UNIV OF SCI & TECH OF CHINA
Association rule mining method for alarm event
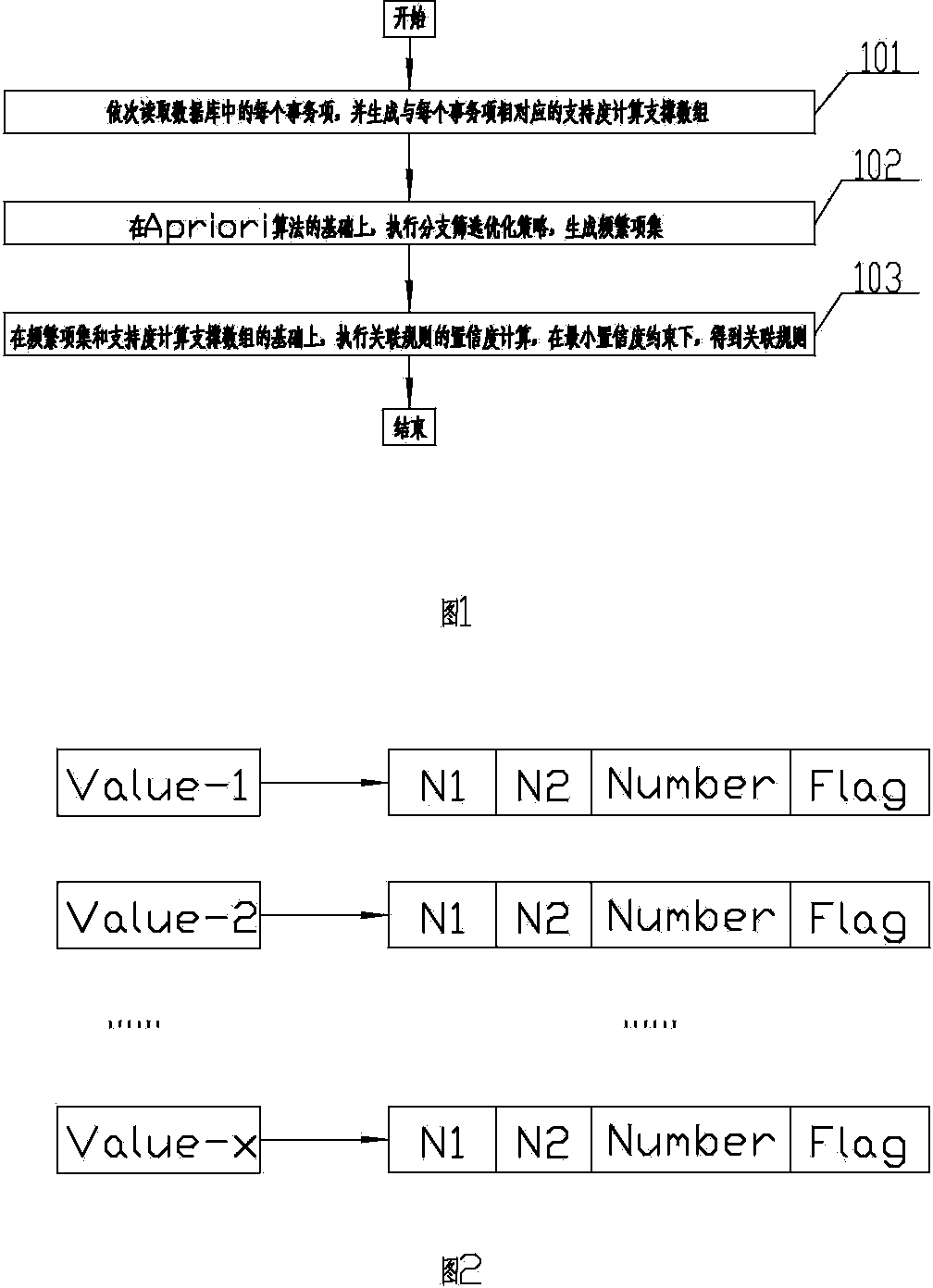
ActiveCN104361036AImprove efficiencySimple calculationSpecial data processing applicationsNetwork managementRule mining
The invention relates to the technical field of network management and discloses an association rule mining method for an alarm event. Based on a branch screening optimization policy and an Apriori algorithm, the method comprises the steps of sequentially reading each event item in a database, and generating a support degree calculation support array corresponding to each event item; on the basis of the Apriori algorithm, executing the branch screening optimization policy, and generating a frequent item set; on the basis of the frequent item set and the support degree calculation support array, calculating the confidence of an association rule to obtain an effective association rule under the restraint of minimum confidence. By constructing the support degree calculation support array, the calculation of a support degree is simplified, the reading frequency of the database is greatly reduced, and the algorithm efficiency is improved; by constructing an adjacent dictionary chain table, a binomial frequent set which meets the requirements on the support degree can be dynamically found, and the execution basis of the branch screening optimization policy is provided; ineffective branches are dynamically deleted, the binomial frequent set is quickly generated, and the algorithm efficiency is improved.
Owner:STATE GRID CORP OF CHINA +3
Improved local anomaly factor algorithm-based power grid topology identification method
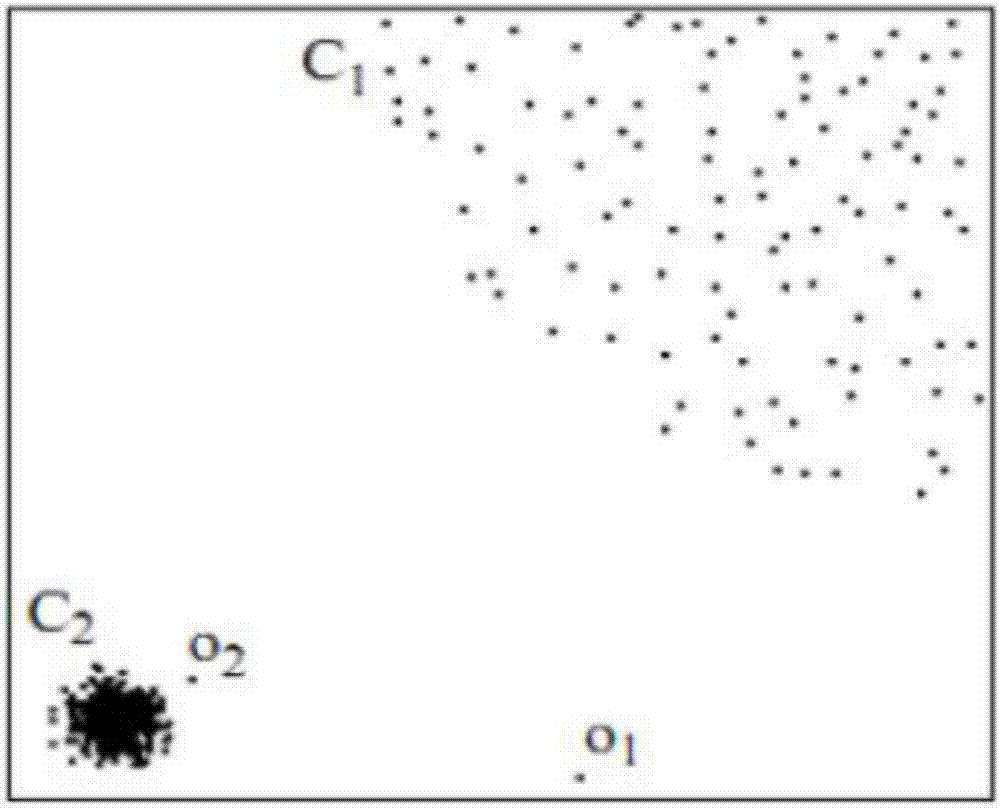
InactiveCN107123989AImprove accuracySimplify complexityCharacter and pattern recognitionAc network circuit arrangementsTopology identificationDensity based
The invention provides an improved local anomaly factor algorithm-based topology identification method. The method comprises the steps of firstly, based on the statistical theory, acquiring the operating state change information of a to-be-predicted device object, such as a switch, a disconnecting link or the like; secondly, according to the acquired data, modeling a to-be-identified data object, and respectively establishing an object set for each device object, wherein the object set represents the operating state change condition of the device object within a certain period of time; thirdly, based on the grid reduction theory in the GDLOF algorithm, reducing data objects in the object set to reduce identification objects and improve the efficiency of the algorithm; fourthly, for non-excluded data objects, subjecting each attribute of each object to weighted treatment by adopting a relative entropy in considering different influences of the telemetry and remote signaling information on topology error identification. In this way, the reliability and the execution efficiency of the algorithm are improved, and the identification topology error of a local anomaly factor is finally confirmed. According to the technical scheme of the invention, the density-based anomaly detection algorithm is applied to the topology error identification of the power grid, so that the application field of the anomaly detection algorithm is expanded. Meanwhile, the topology error problem of the power grid and the identification problem of telemetry bad data in the prior art are solved at the same time.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +3
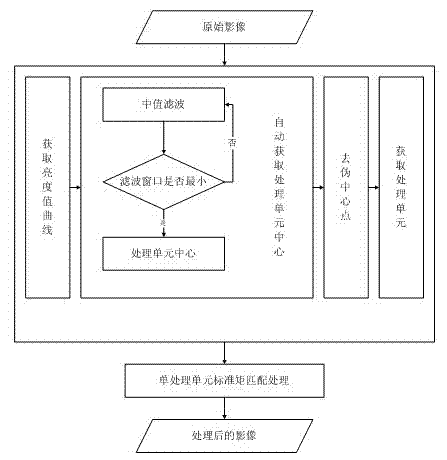
Self-adaption moment matching stripe noise removing method based on gray-level segmentation
ActiveCN102819827AEffective recoveryImprove image qualityImage enhancementImaging processingImaging quality
The invention relates to a self-adaption moment matching stripe noise removing method based on gray-level segmentation, which comprises the following steps: acquiring a brightness value curve for an original noise-containing image; performing median filtering on the brightness value through processing windows with different sizes for removing a base line, and acquiring processing unit centers; adjusting according to the distance between each two adjacent processing unit centers to confirm a processing unit; and performing image processing on single processing unit with the processing way of matching in standard moment. For remote sensing panchromatic images with large data size, an effective noise removing method for the image is provided. The method provided by the invention can effectively recover the image and improve the image quality and has high algorithmic efficiency.
Owner:WUHAN UNIV
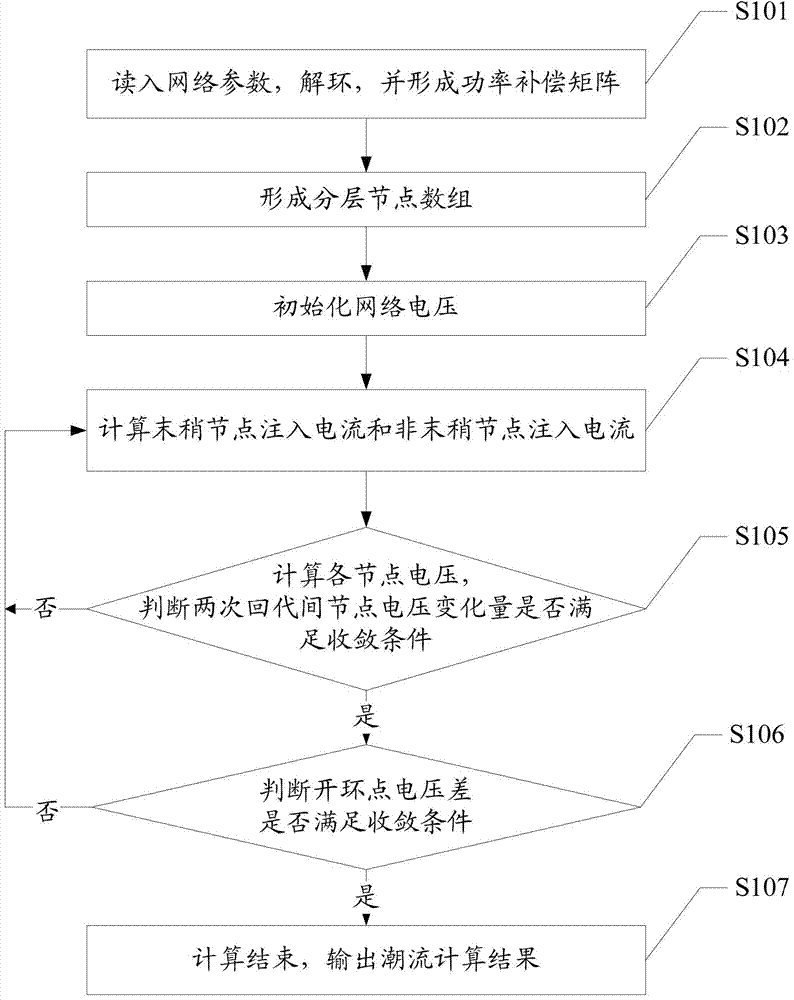
Load flow calculation method and system for power distribution network
InactiveCN103248044AImprove efficiencyImprove computing efficiencyAc network circuit arrangementsElectrical resistance and conductanceHigh resistance
The invention discloses a load flow calculation method and system for a power distribution network. The method and the system are not influenced by high resistance and reactance ratio of the distribution network on the basis that an element module of the distribution network adopts the forward-back substitution method, and have higher computational efficiency and favorable convergence characteristic. During establishing of a layered node array, a distributed power supply model is introduced, so that the method and the system meet the format of the grid to which a distributed power supply is accessed; and in the injection current computation process of nodes, the optimized open-loop model is utilized to simplify the algorithm and improve the algorithm efficiency, so that the method and the system are suitable for various occasions in the distribution network.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID +1
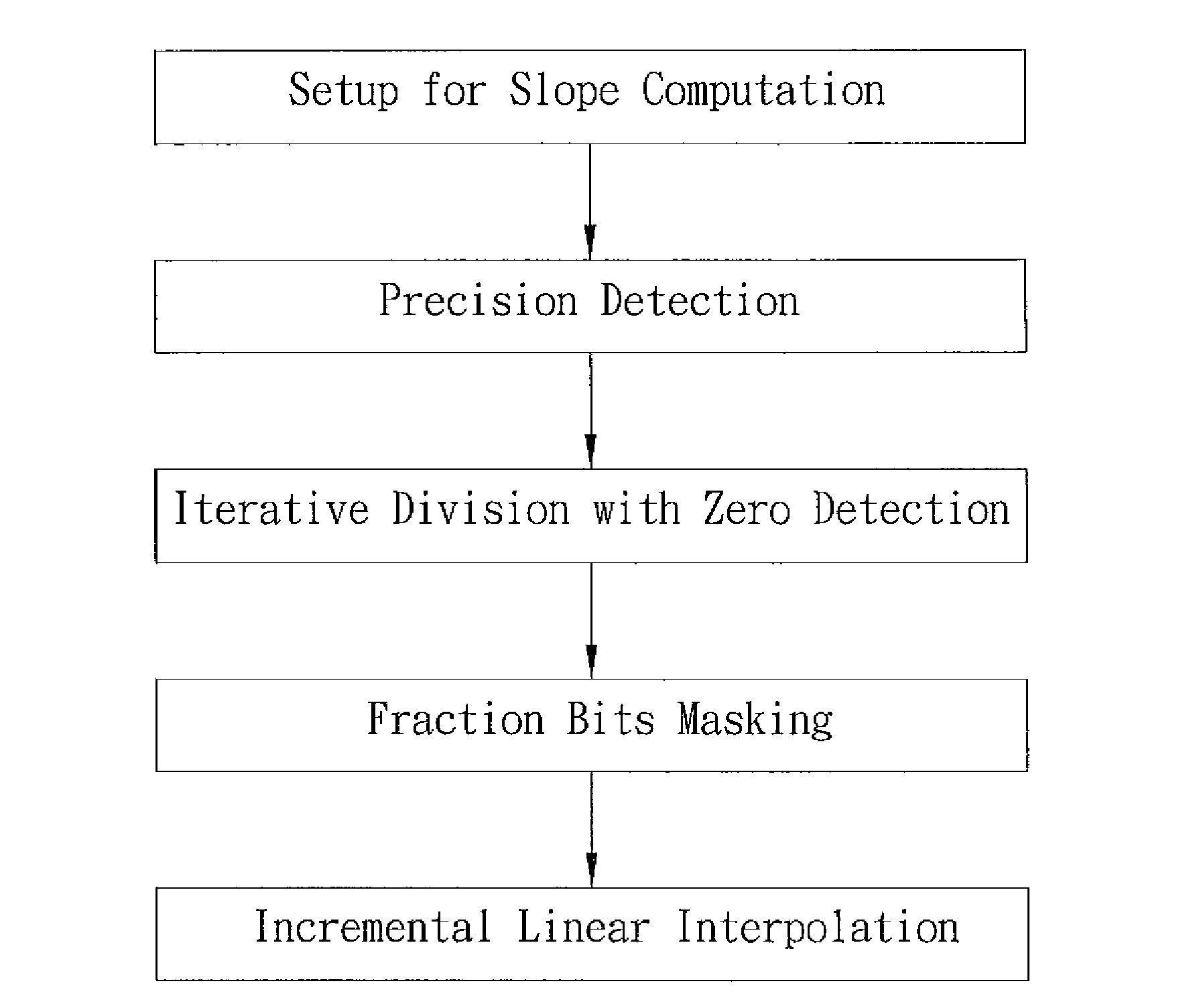
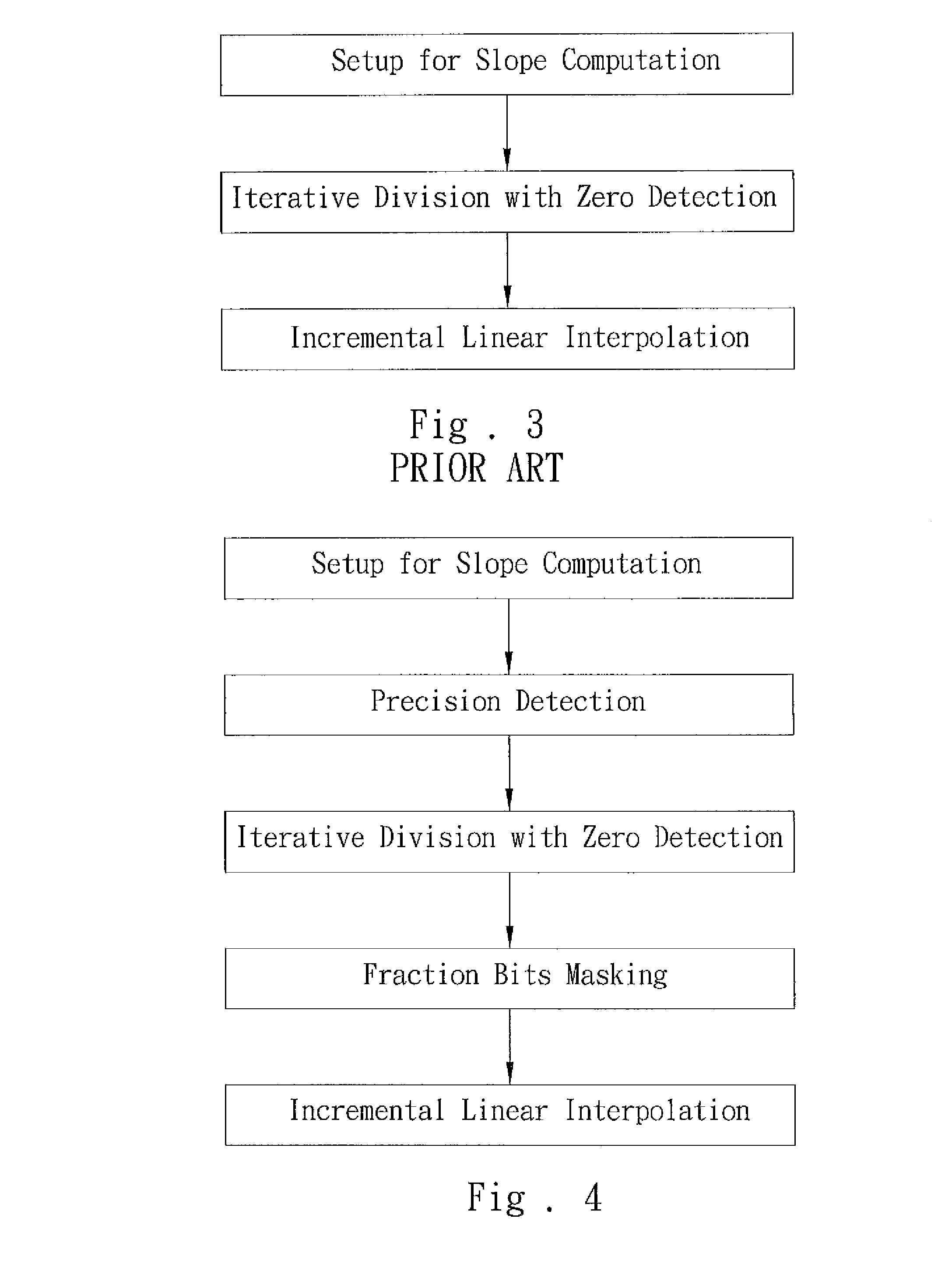
Precision-sensing linear interpolation algorithm
InactiveUS20090138536A1Reduce the number of iterationsImprove toleranceComplex mathematical operationsFilling planer surface with attributesAlgorithmAlgorithmic efficiency
The present invention discloses a precision-sensing linear interpolation algorithm, which is distinct from the conventional technology in that precision detection is performed before iterative division calculations. The iteration number of iterative division calculations is determined according to the required precision. After the iterative division calculations, the bits in the decimal places unnecessary for the required precision are set to be 0 with a bit-masking method. Via the precision detection and bit mask, the present invention can promote algorithm efficiency and reduce dynamic power consumption.
Owner:SITRONIX TECH CORP
Data flow abnormality detection method based on parallel Kalman algorithm
InactiveCN106709250AImprove efficiencyVerification is feasibleSpecial data processing applicationsInformaticsData streamParallel algorithm
The invention discloses a data flow abnormality detection method based on a parallel Kalman algorithm. The data flow abnormality detection method comprises the following steps that 1, measurement data of a sensor in a period of time is acquired; 2, the measurement data is compared with a measurement value in a previous period of time, once a change is generated, an estimation value is calculated through the Kalman algorithm according to the measurement value, an absolute value of a difference between the estimation value and the measurement value is compared with a specified threshold value, and if the absolute value is not smaller than the threshold value, the absolute value is judged to be an abnormal value, and the next step is conducted; 3, the generation reasons of the abnormal value are judged by considering a time influence factor, a space influence factor and other factors such as the flood period, the weather and the human factors which influence abnormality detection and recorded, and information is stored in a database. According to the data flow abnormality detection method, the time influence factor, the space influence factor and the other provenance information influence factor are taken into account; an algorithm task is decomposed and processed in parallel in order to improve the algorithm efficiency, and the detection precision is improved.
Owner:HOHAI UNIV
Ship route intelligent generation method based on combination of artificial immunity and ant colony algorithm
InactiveCN101916312AImprove efficiencyPrevent "premature" problemsBiological modelsSpecial data processing applicationsAlgorithmic efficiencyInitial distribution
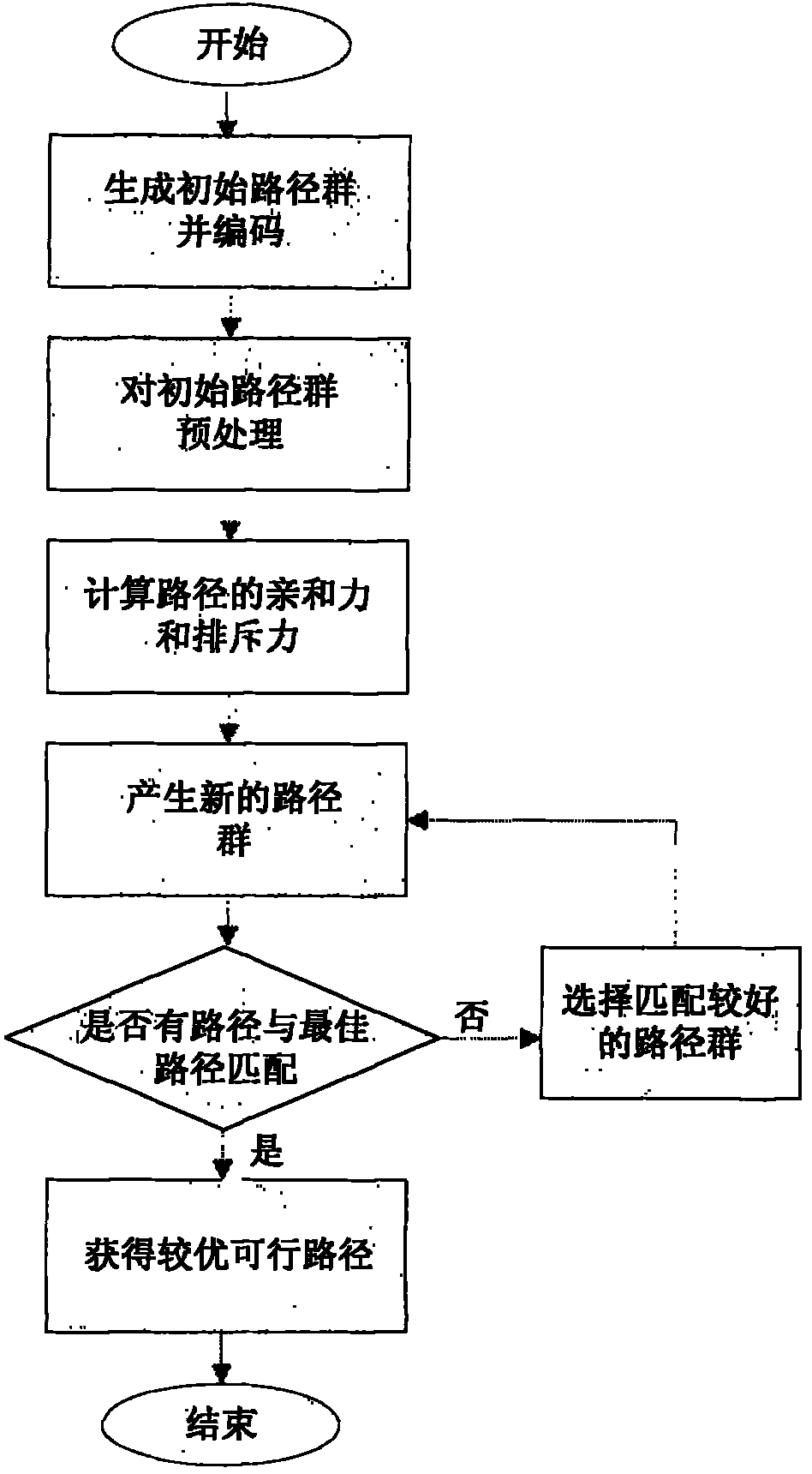
The invention provides a ship route intelligent generation method based on the combination of artificial immunity and an ant colony algorithm, comprising the following steps of: during a first half part, carrying out convex hull extraction and polygon combination on obstacles, describing a navigation environment, then randomly generating an initial path group according to certain rules and preprocessing the initial path group, and finally carrying out matching selection on path groups; during a latter half part, generating the initial distribution of pheromones by utilizing an obtained better feasible solution, and then searching an optimal path by utilizing the ant colony algorithm. In the ship route intelligent generation method, selection update based on affinity is adopted during a previous period, thereby effectively preventing the problem of earliness and leading the searching process to global optimum; in addition, algorithm efficiency is enhanced by utilizing the characteristics of parallel computation and positive feedback of the ant colony algorithm during a later period.
Owner:HARBIN ENG UNIV
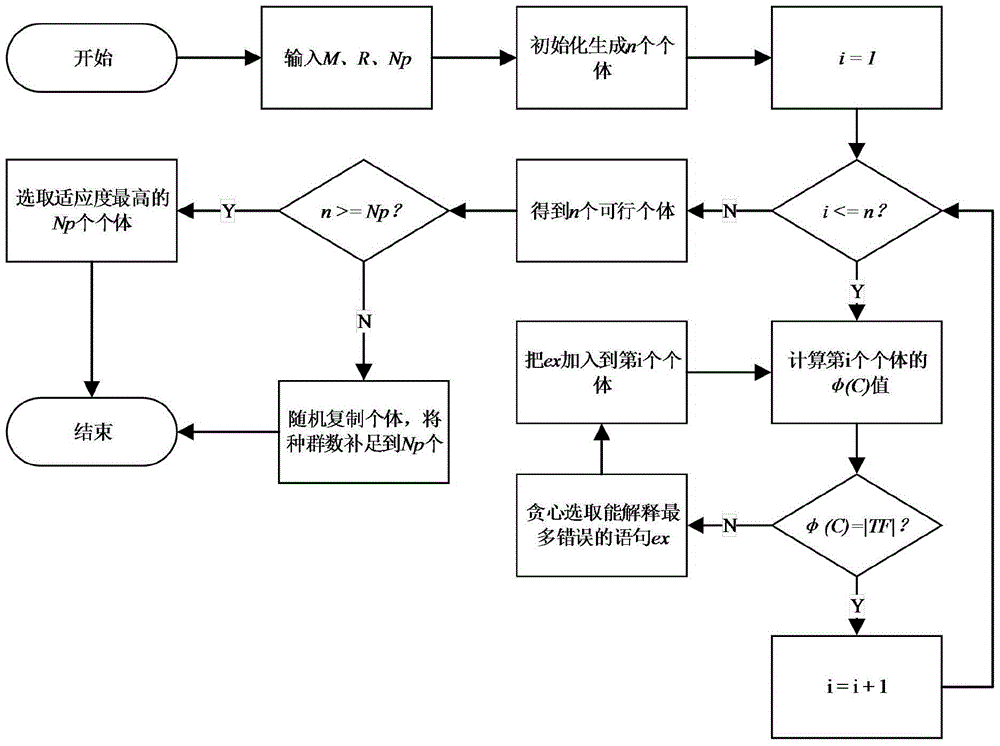
Multi-defect positioning method based on search algorithm
InactiveCN105760295AGood effectEfficiency is feasibleSoftware testing/debuggingMutation operatorGreedy algorithm
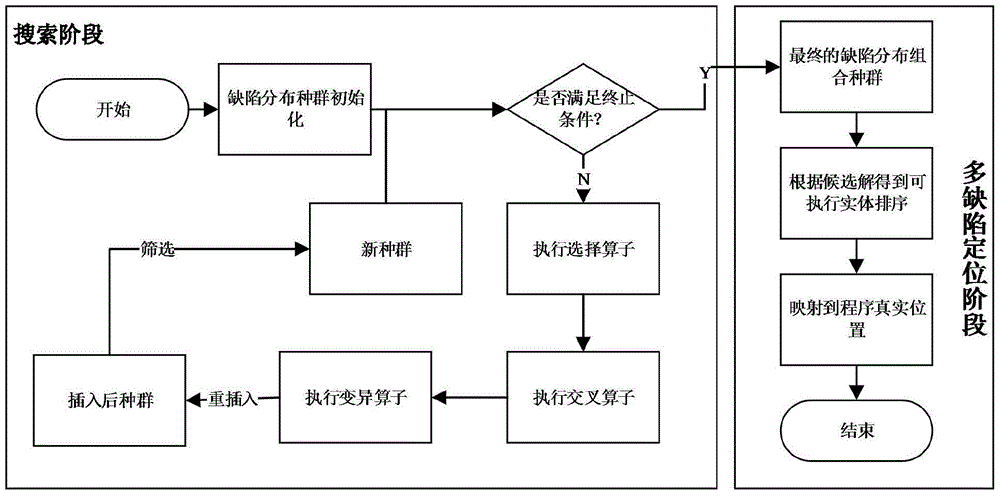
The invention discloses a multi-defect positioning method based on a search algorithm. The method includes the steps that 1, the search algorithm at a first stage is executed, wherein the following processing that firstly, a population with multi-defect distribution is initialized through a greedy algorithm, then a selection operator, a crossover operator and a mutation operator are executed to generate a new individual, the new individual is re-inserted into the original population, a next-generation population is formed, and when a terminal condition of the search algorithm is met, a second stage is executed is specially included; 2, multi-defect positioning at a second stage is executed, wherein a final defect distribution combined population is obtained, an executable entity rank is obtained according to candidate defect distribution populations, the executable entity sequence is mapped to a real position of a program, a rank of equivocation coefficients of corresponding program entities is obtained according to multi-defect distribution in the optimal candidate defect distribution population, and the algorithm is completed. The effect of an adopted GAMFal algorithm on the multi (single) defect positioning problem is superior to that of an existing SFL method; only little artificial participation is needed; the efficiency of the algorithm is feasible.
Owner:TIANJIN UNIV
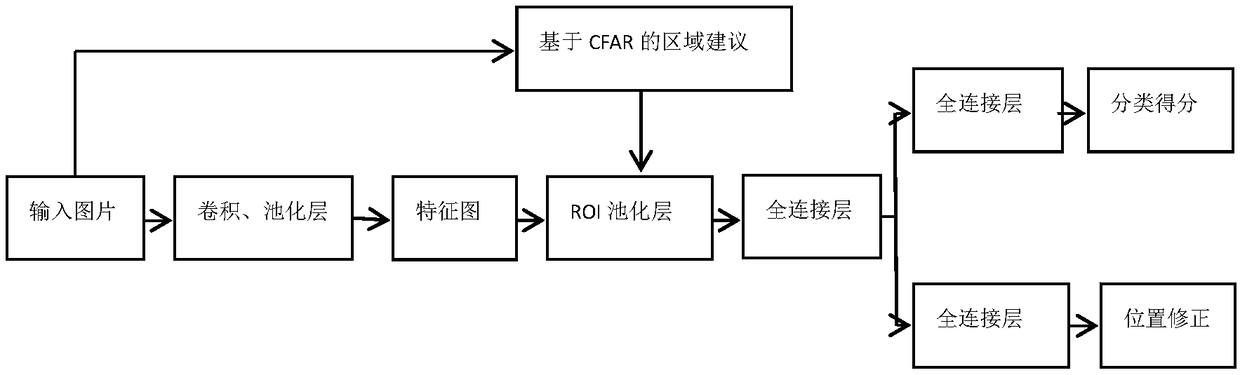
A ship target detection method based on the fusion of CFAR and Fast-RCNN in SAR image
ActiveCN109145872AImprove efficiencyGuaranteed validityScene recognitionNeural architecturesFeature extractionMorphological filtering
The invention discloses a method for SAR image Ship target detection based on based on CFAR and Fast-RCNN fusion. The method is based on Fast-RCNN Target Detection Framework, and based on the featurethat the brightness of ship target is higher than that of background in SAR image, and comprises steps: at first, the suspect target points are obtained by a CFAR algorithm, then morphological filtering based on multiple groups of structural elements is performed to obtain candidate suggestion boxes, which not only reduces the number of candidate regions and improves the efficiency of the algorithm, but also ensures the effectiveness of the suggestion boxes, and overcomes the shortcomings that the same target is divided into multiple parts and the similar targets are mistaken as the same target by using a single filtering factor group; on the basis of the extracted candidate suggestion boxes, Fast-RCNN network model training is completed, and based on the model to achieve any input image of the target classification and calibration box regression, through the use of CNN feature extraction network, the shortcomings of manual feature extraction are overcome, and the data utilization is improved.
Owner:BEIJING INST OF REMOTE SENSING EQUIP
An integrated three-way clustering method based on a Spark platform and employing two-evaluation weight selection
ActiveCN107480694AQuality improvementImprove efficiencyCharacter and pattern recognitionData setMachine learning
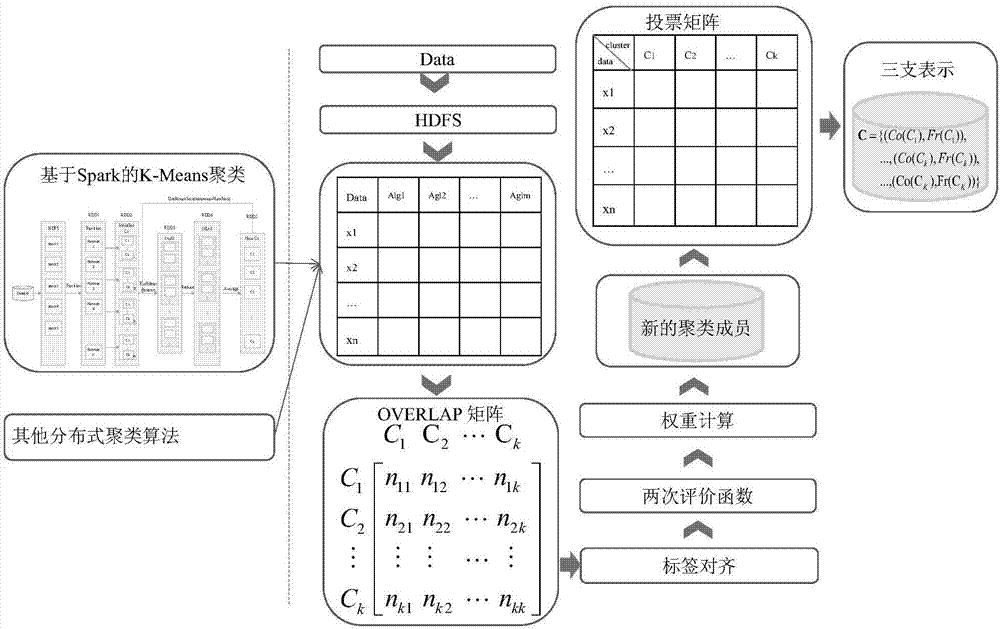
The invention relates to an integration three-way clustering method based on a Spark platform and employing two-evaluation weight selection; the method mainly comprises the following steps: 1, partitioning and managing big data so as to from a corresponding elastic distributed data set (RDD); 2, using a K-Means cluster algorithm based on Spark to cluster the data of each partitioned area, thus forming a plurality of different clustering members; 3, using two evaluations to build a novel evaluation function and weight selection strategy, selecting the clustering members, deleting clustering results with poor clustering effects, and forming new clustering members; 4, integrating the clustering members, building a weighted ballot matrix, dividing clusters according to three-way decision rules, and finally obtaining a three-way clustering result. The method can greatly reduce the algorithm operation time, thus improving the algorithm efficiency.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Ship multi-target detection method based on improved anchor point box generation model
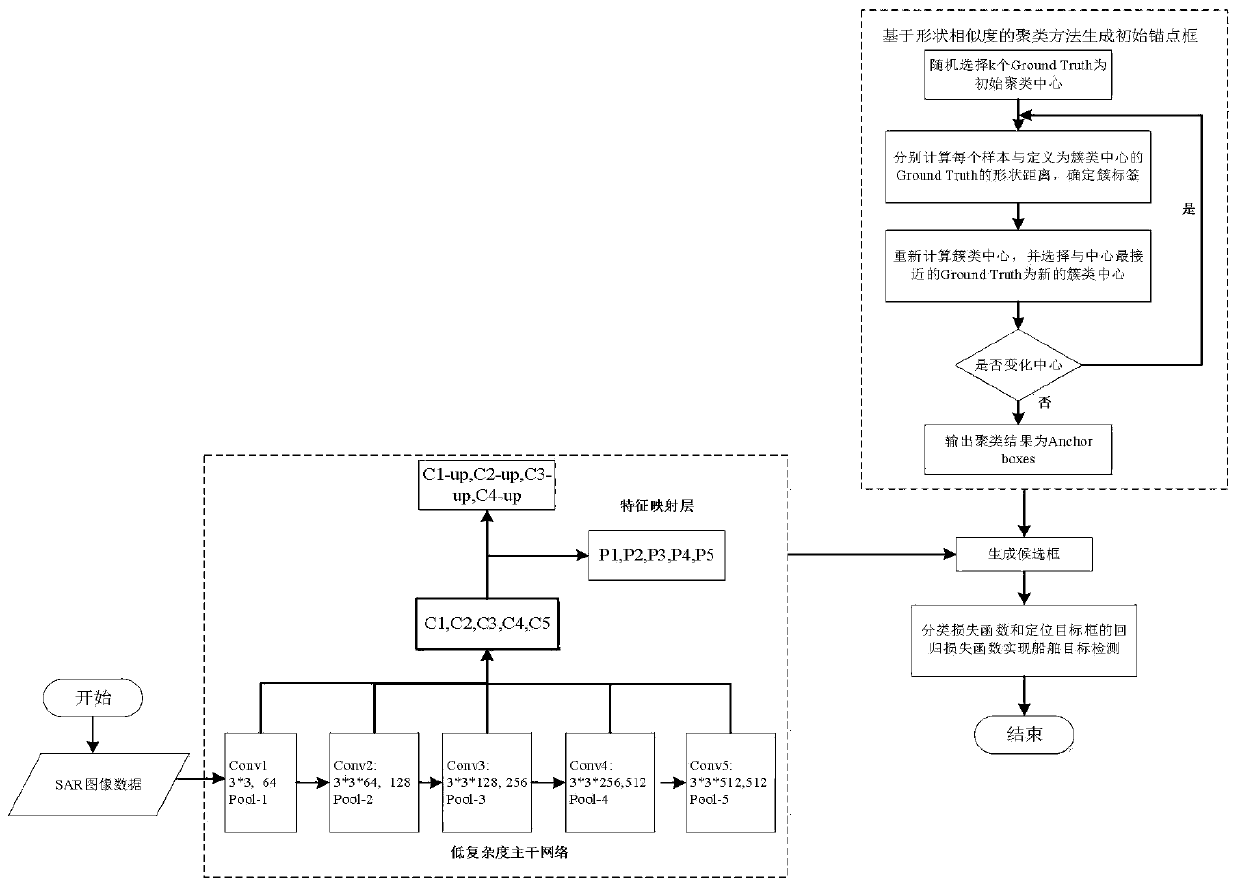
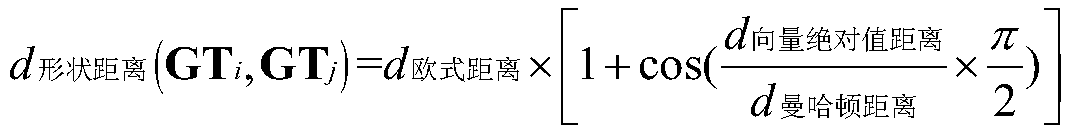
PendingCN111368769AImprove accuracySolve algorithm efficiencyScene recognitionStatistical analysisNetwork architecture
Owner:DALIAN NEUSOFT UNIV OF INFORMATION
Integer ciphertext arithmetic operation method based on homomorphic encryption
ActiveCN109412786AImprove algorithm efficiencyReduce frequencyCommunication with homomorphic encryptionAlgorithmNoise reduction
The invention provides an integer ciphertext arithmetic operation method based on homomorphic encryption, which comprises complement homomorphic calculation, addition subtraction homomorphic calculation, multiplication homomorphic calculation and division homomorphic calculation. This invention refers to the rules of complement, addition, subtraction, multiplication and division of binary integersin computer, and transforms this rule into Boolean polynomials containing only logical AND and XOR operations. In multiplication and division, different calculations are made according to the information of special bits to correct the final calculation results. So we modify the form of Boolean polynomials to represent different computational results, that is, Boolean polynomials include all the inputs and mutually exclusive computational branches of this layer. Then Boolean polynomials are transformed into homomorphic polynomials which can be used in ciphertext computation, and the security of homomorphic polynomials is proved, which meets the requirement of semantic security. The multi-bit parallel operation of integer homomorphic arithmetic operation is realized, the algorithm efficiency of homomorphic operation is improved, the frequency of noise reduction operation is reduced, and the operation efficiency is improved.
Owner:SHENYANG AEROSPACE UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com