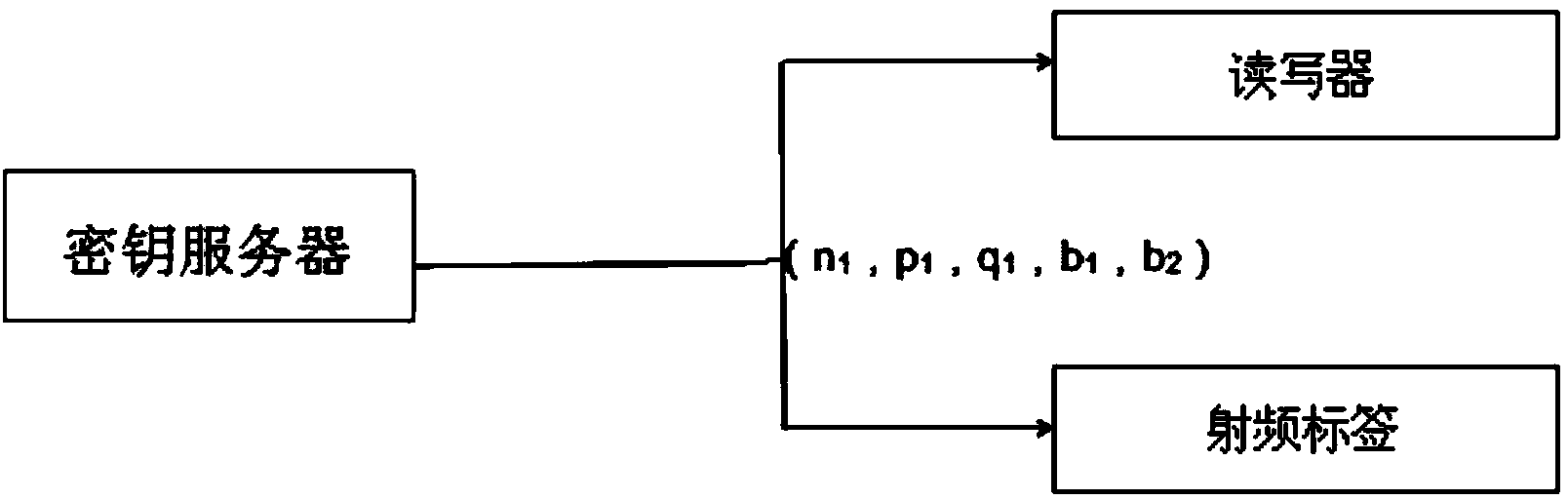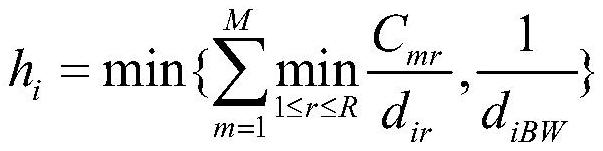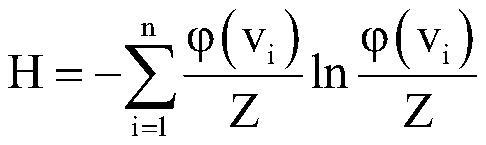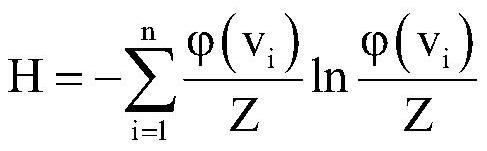Patents
Literature
36 results about "Computation sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
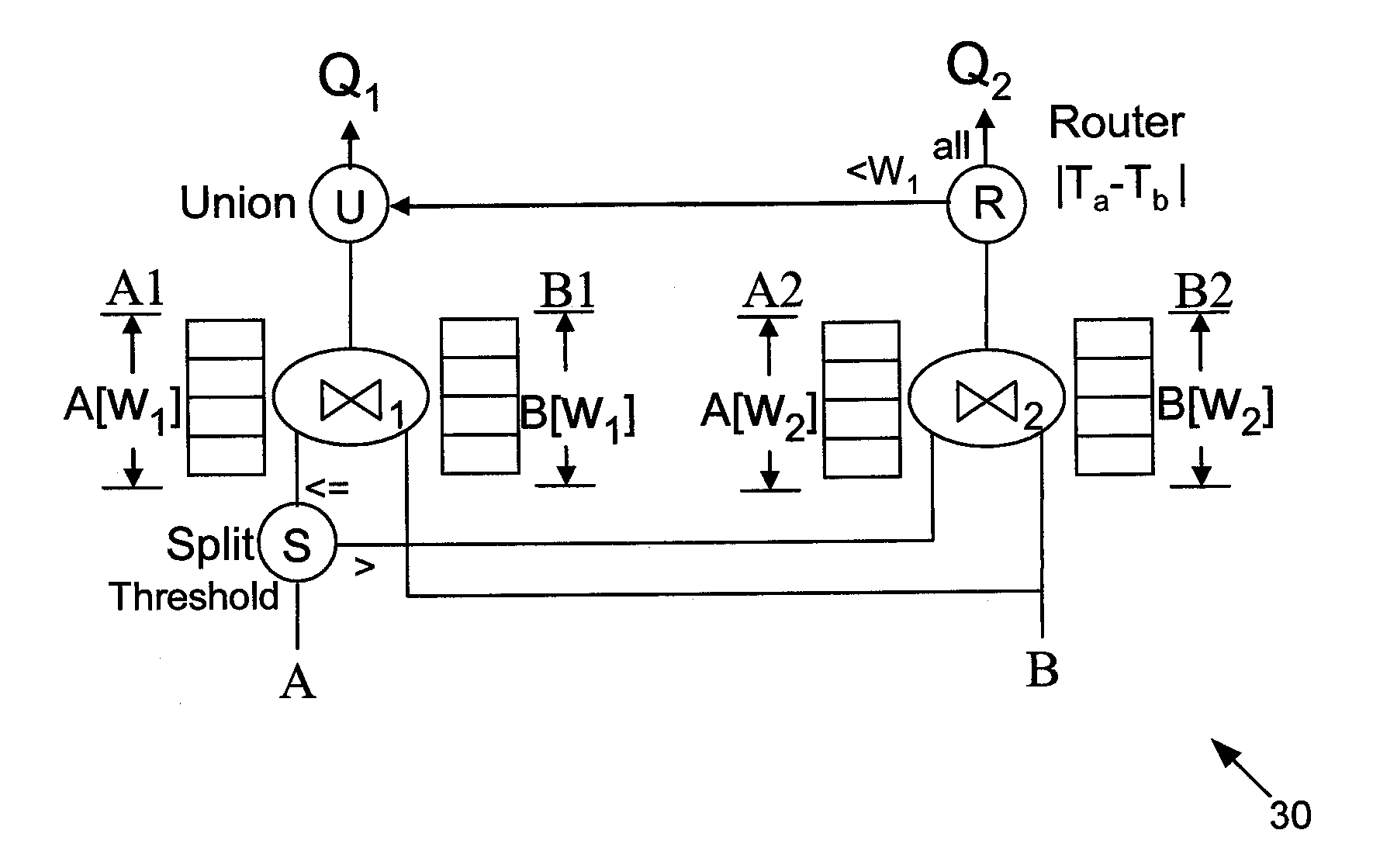
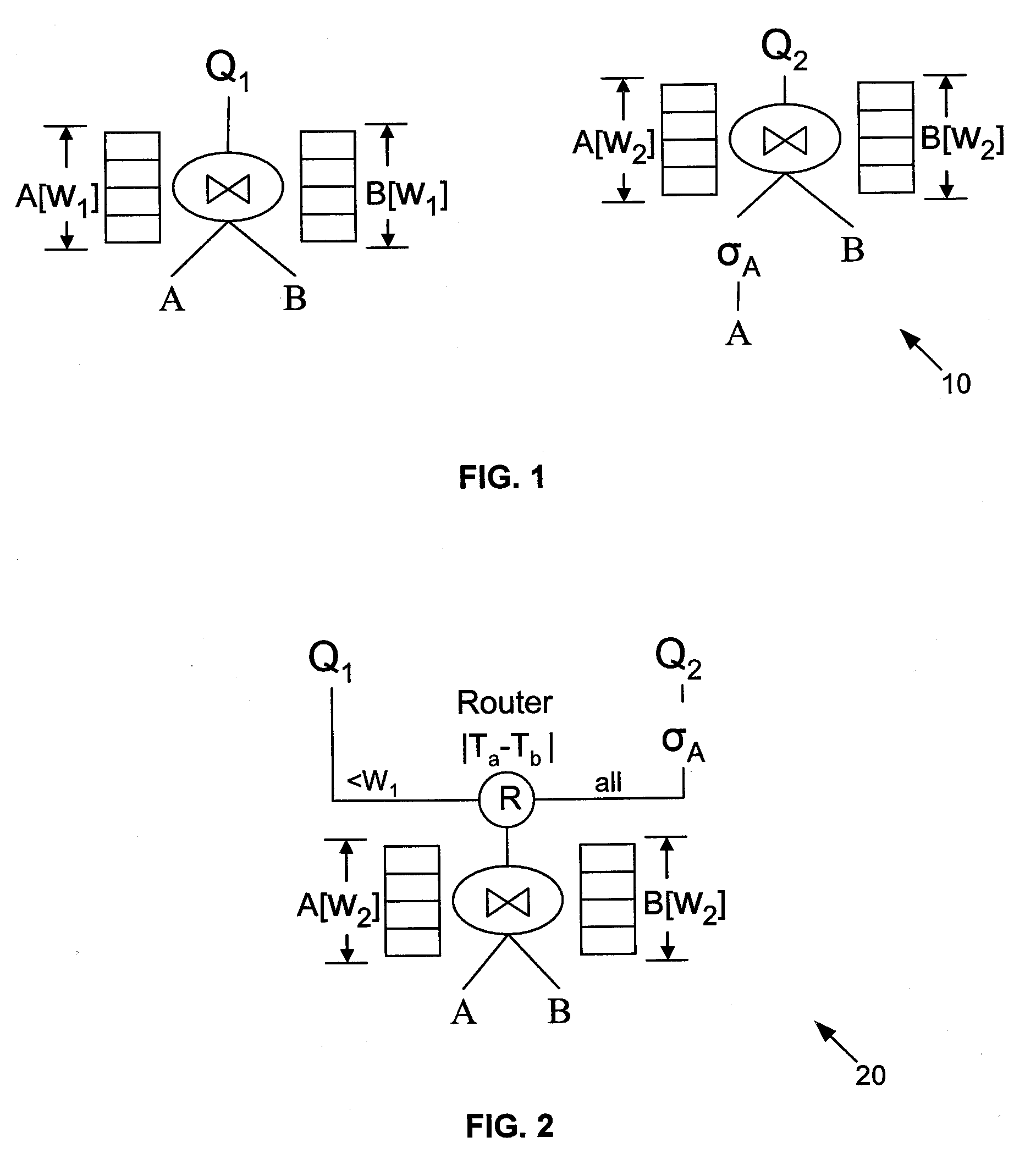
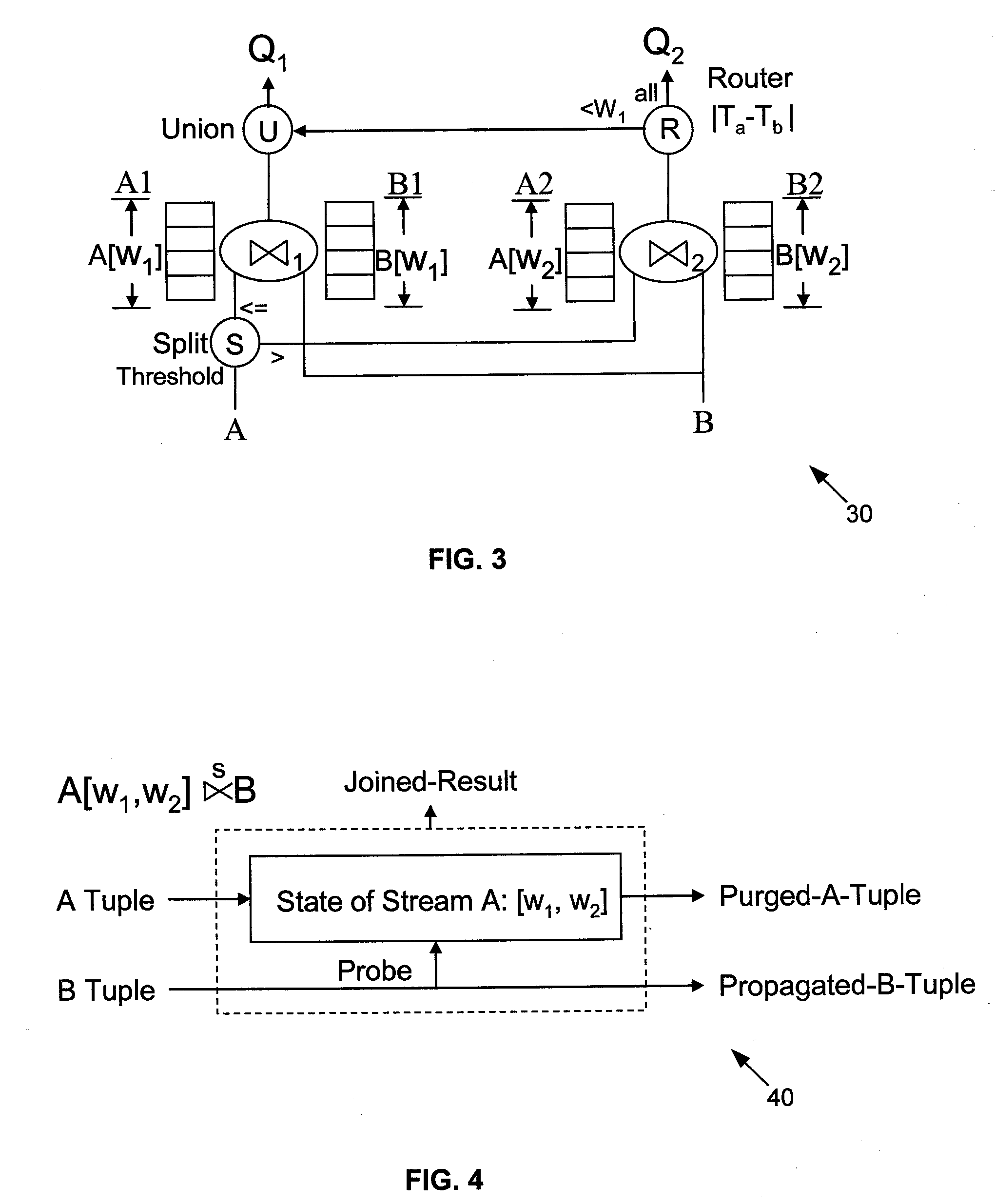
Multi-Query Optimization of Window-Based Stream Queries
InactiveUS20080016095A1Minimizing memory consumptionReduce in quantityDigital data information retrievalSpecial data processing applicationsQuery optimizationComputer science
A method for sharing window-based joins includes slicing window states of a join operator into smaller window slices, forming a chain of sliced window joins from the smaller window slices, and reducing by pipelining a number of the sliced window joins. The method further includes pushing selections down into chain of sliced window joins for computation sharing among queries with different window sizes. The chain buildup of the sliced window joins includes finding a chain of the sliced window joins with respect to one of memory usage or processing usage.
Owner:NEC LAB AMERICA
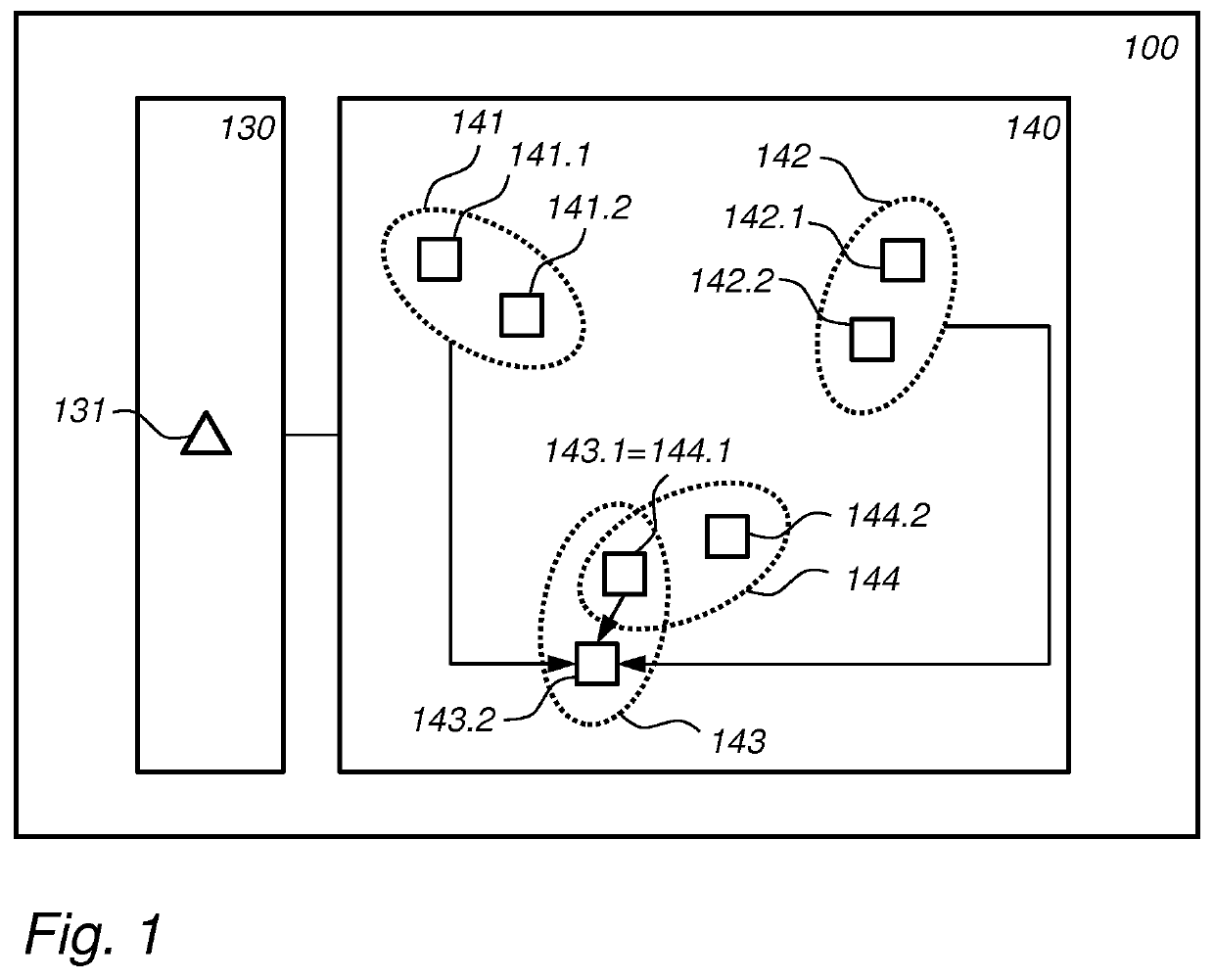
Key agreement devices and method
ActiveUS20200153618A1Simple protocolReduce communication overheadKey distribution for secure communicationMultiple keys/algorithms usageKey exchangeComputer network
A first electronic network node (110) is provided configured for a key exchange (KEX) protocol, the first network node is configured to obtain a shared polynomial (a) shared with a second network node, coefficients of the shared polynomial a being selected modulo a first modulus q, generate a private key polynomial (skI), coefficients of the private key polynomial being bounded in absolute value by a bound (s) generate a public key polynomial (pkI) by computing a polynomial product between the shared polynomial (a) and the private key polynomial (skI) modulo the first modulus (q) and scaling the coefficients of the polynomial product down to a second modulus (p).
Owner:KONINKLJIJKE PHILIPS NV
Shared learning system and method based on a cloud platform, sharing platform and method, and medium
PendingCN109993308AProgramme-controlled manipulatorFuzzy logic based systemsComputer terminalDistributed computing
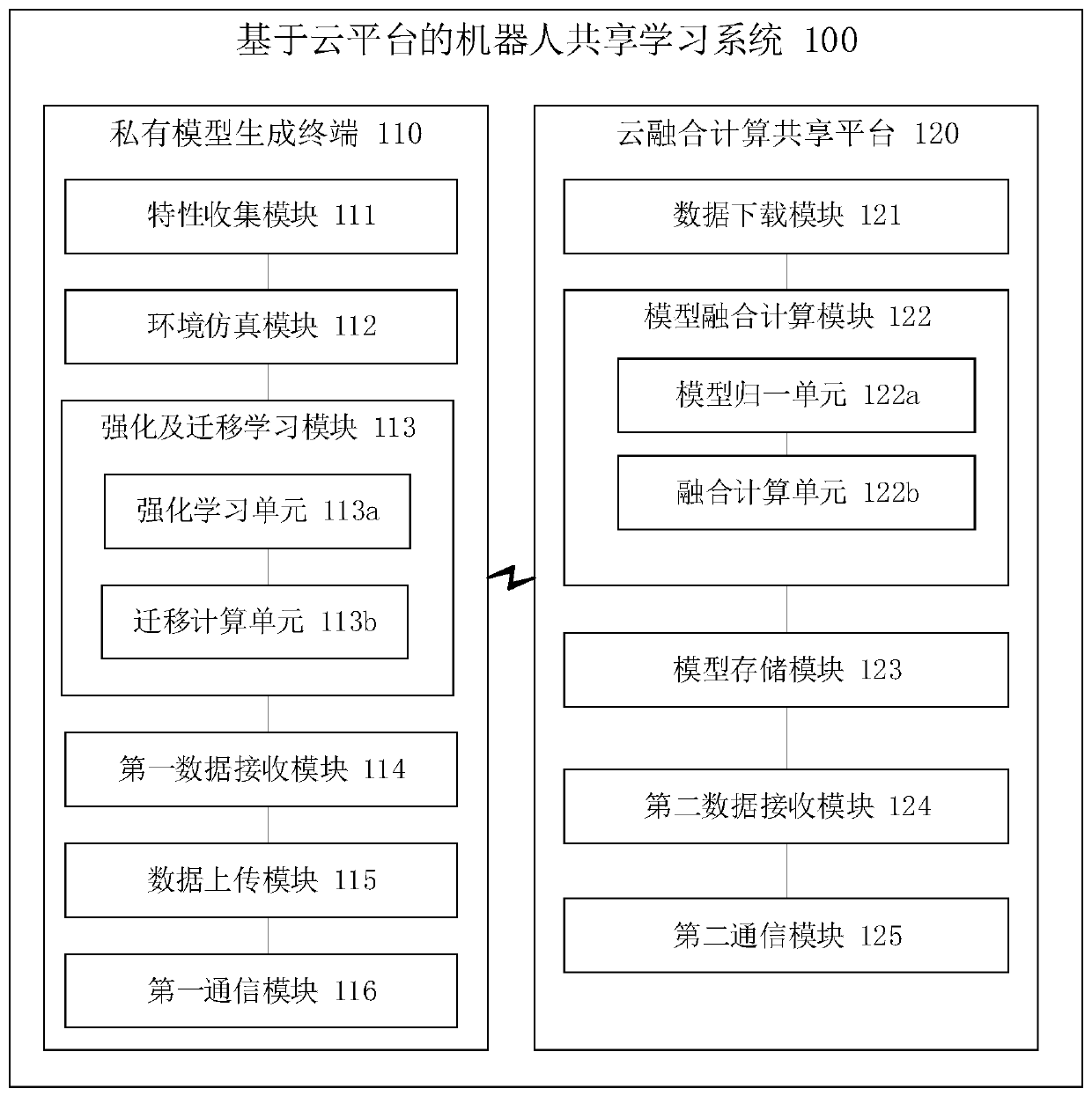
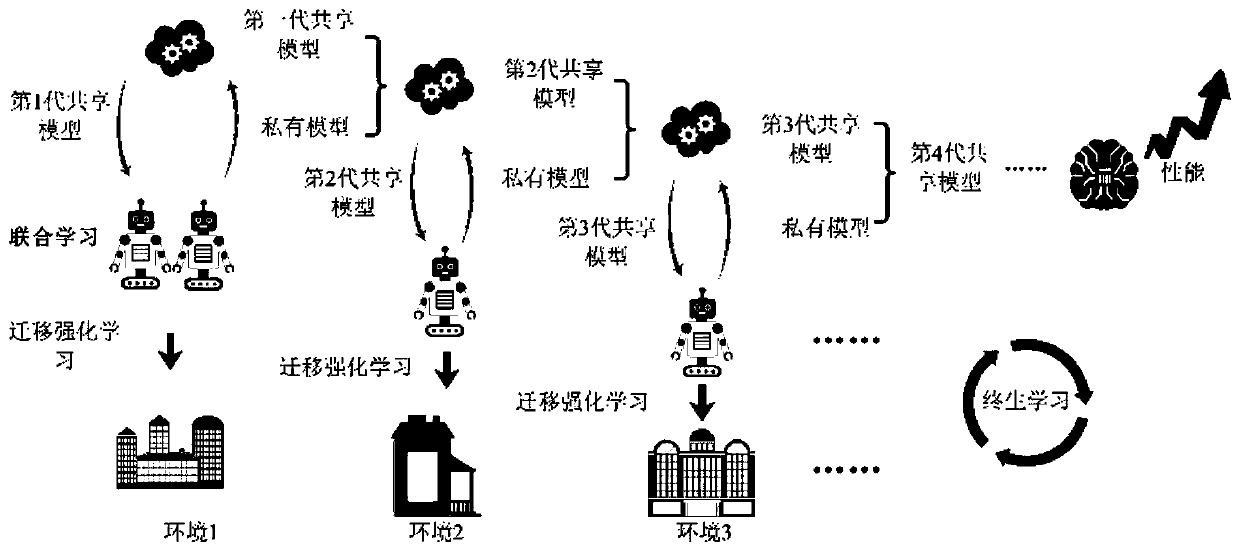
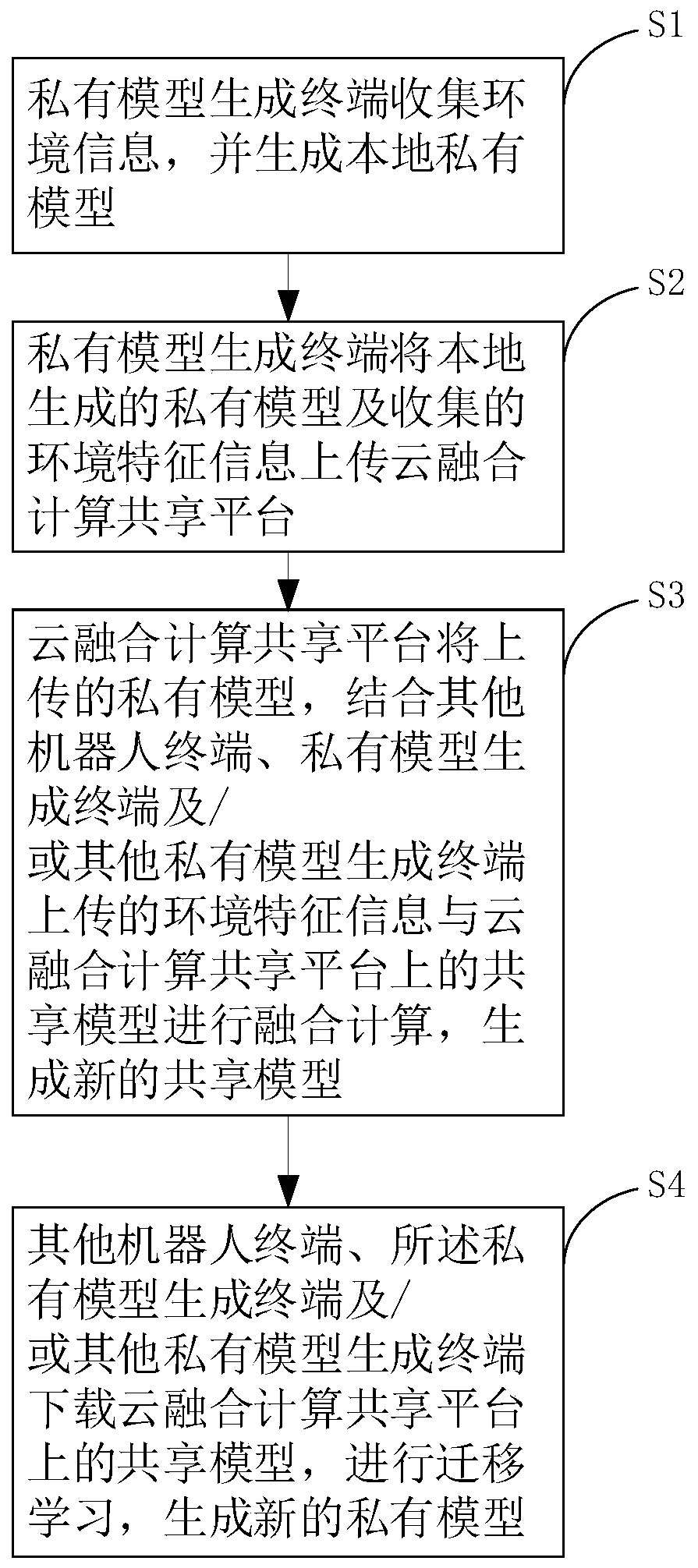
The invention provides a robot shared learning system based on a cloud platform. The system comprises a private model generation terminal and a cloud fusion computing sharing platform. The private model generation terminal is used for uploading the locally generated private model and the environmental feature information collected for generating the private model to the cloud fusion computing sharing platform. The cloud fusion computing sharing platform comprises a model fusion computing module. The model fusion calculation module is used for combinding the uploaded private model with other robot terminals, a private model generation terminal and / or other private models to generate uploaded environment feature information and merging and calculating the information with a sharing model stored on a cloud sharing computation sharing platform to generate a novel sharing model. The novel sharing model is downloaded and / or studied by other robot terminals, the private model generation modeland / or other private model generation models.
Owner:SHENZHEN INST OF ADVANCED TECH
Key exchange method and device, storage medium and computing device
ActiveCN111010277ASimple designReduce consumptionKey distribution for secure communicationPublic key for secure communicationKey exchangeInformation transmission
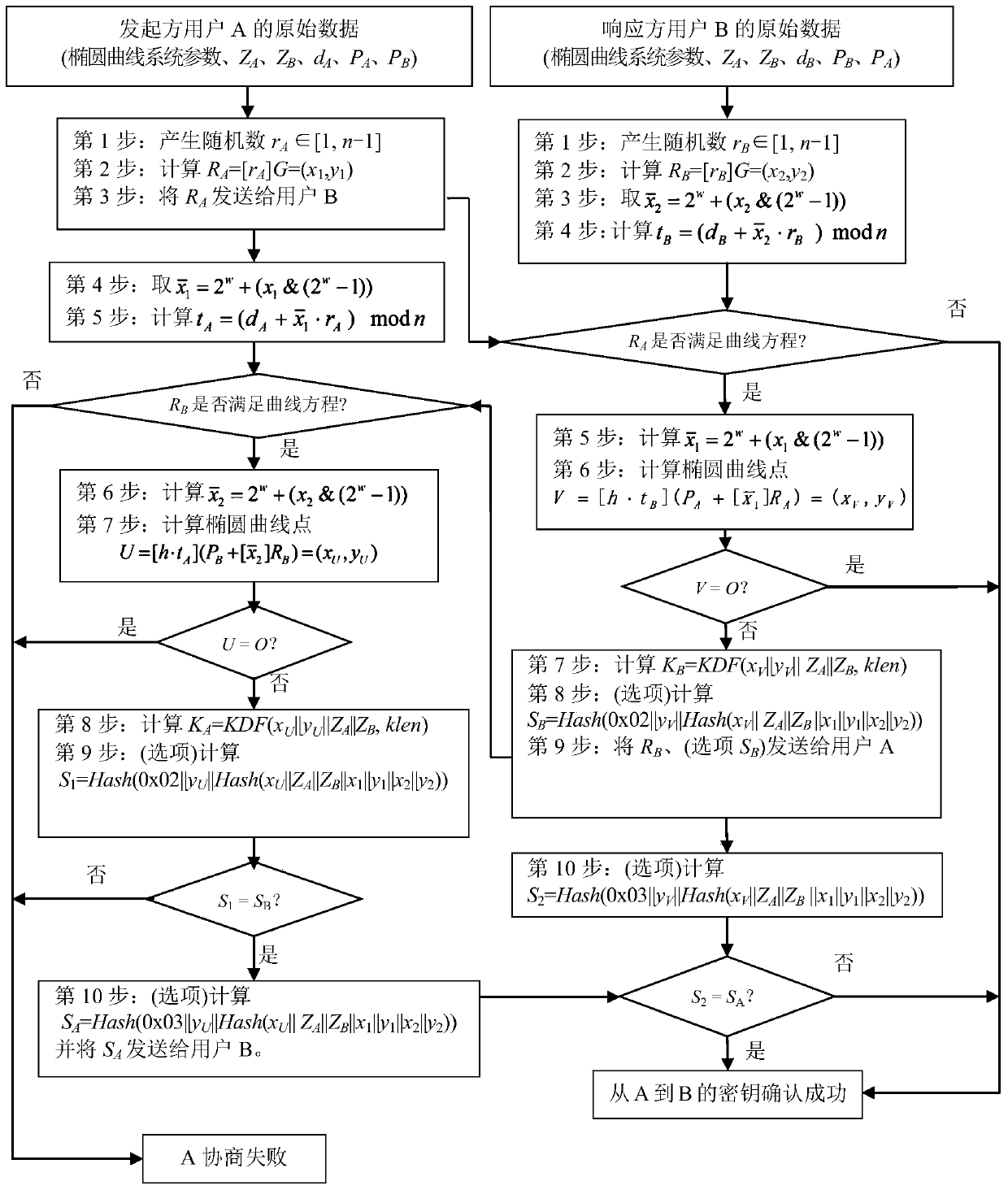
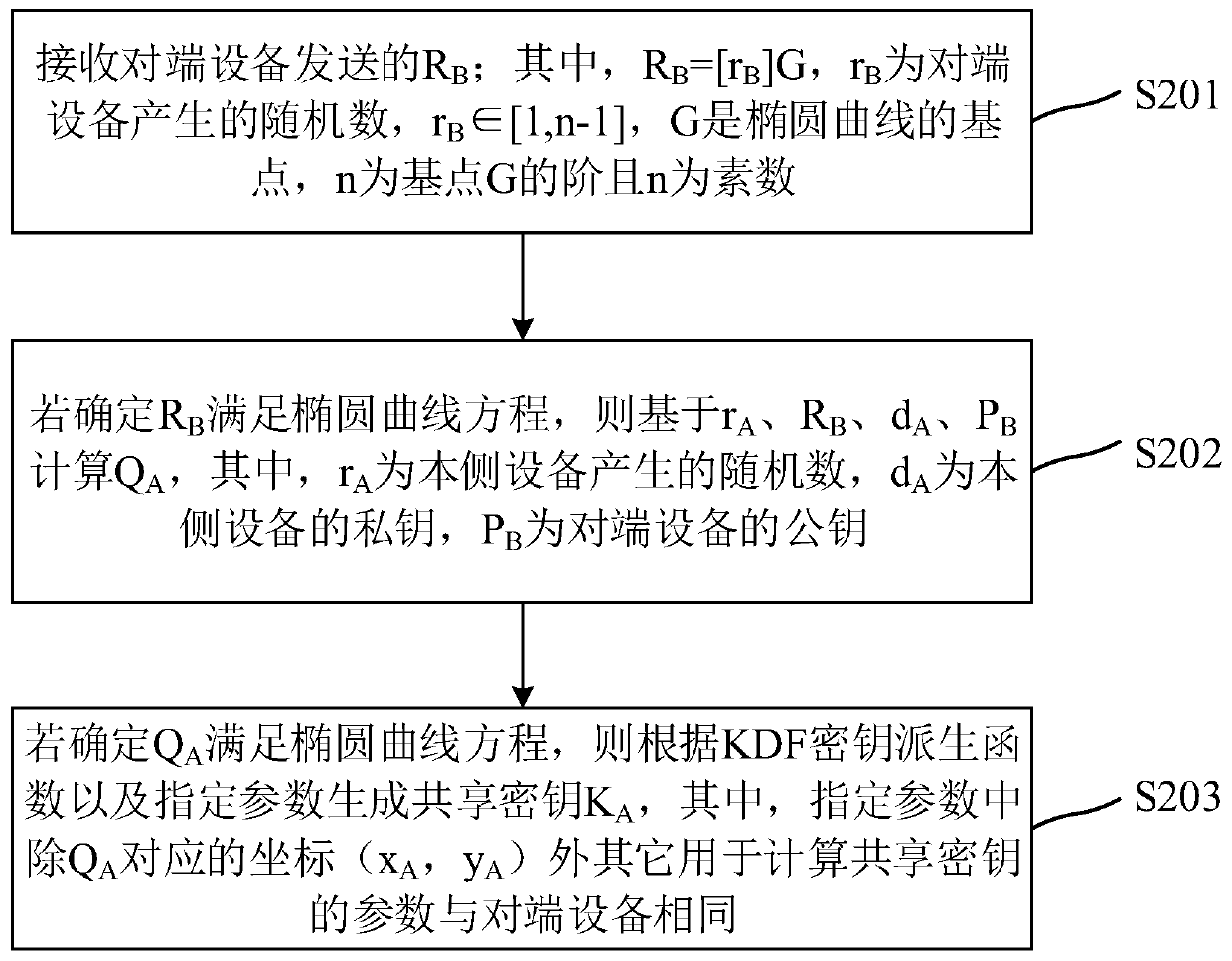
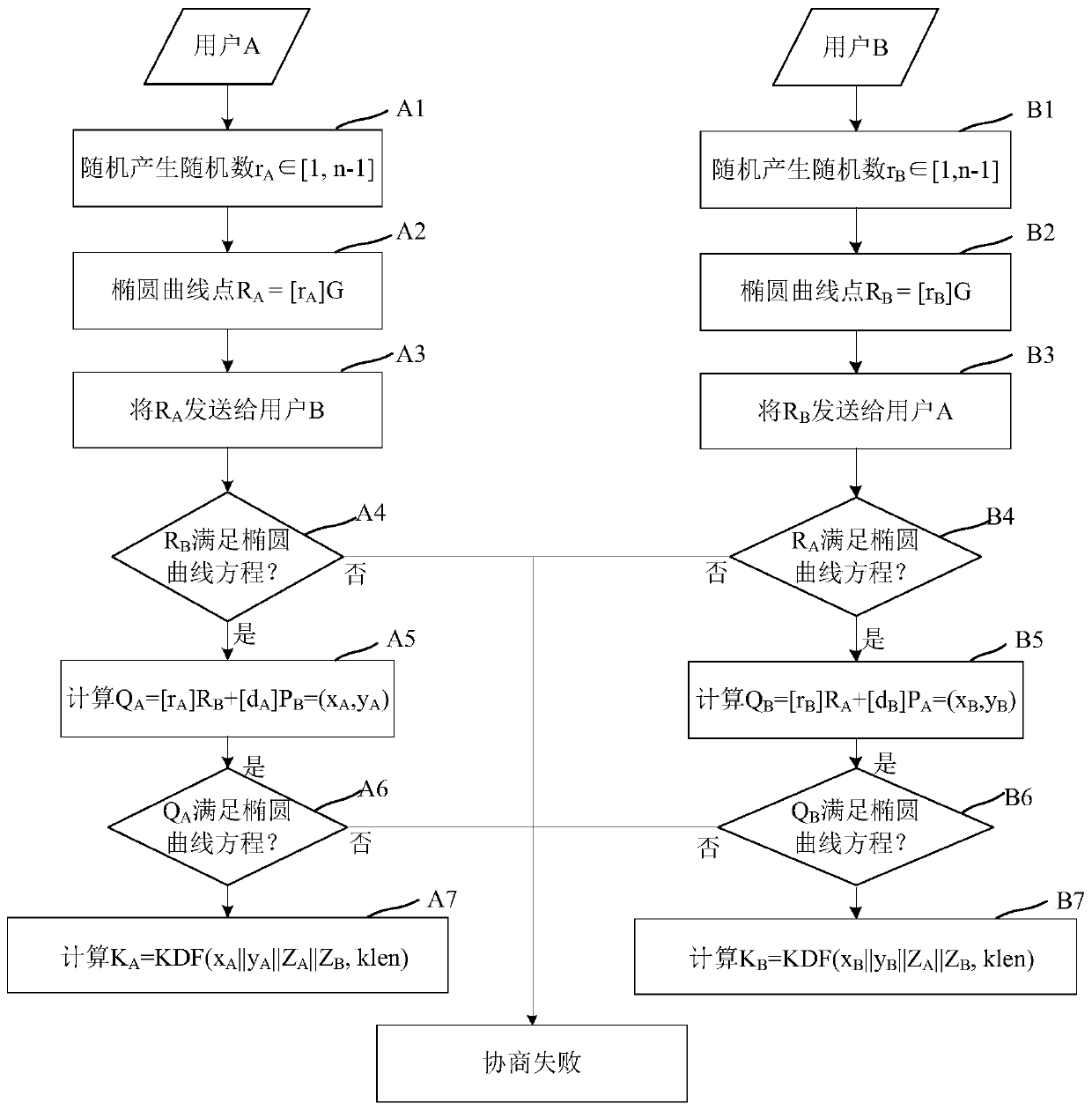
The invention provides a key exchange method and a device, a storage medium and a computing device, and relates to the technical field of information security. The method comprises the following steps: receiving an RB sent by opposite-end equipment; if it is determined that the RB meets the elliptic curve equation, calculating QA based on rA, RB, dA and PB; if it is determined that the QA meets the elliptic curve equation, generating a shared key KA according to a KDF key derivation function and specified parameters, and other parameters, except for the coordinate (xA, yA) corresponding to theQA, in the specified parameters are the same as those of the opposite-end equipment for calculating the shared key. Therefore, the execution steps of the two key exchange parties are the same, the algorithm is simple, and the two key exchange parties are convenient and efficient. And the information is transmitted only once, so that the processing resource consumption caused by multiple times ofinformation interaction is reduced, and the key negotiation efficiency can be improved. Moreover, in the transmission process, even if the RB is intercepted, the shared key cannot be obtained, so thatthe security of the shared key is ensured.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
Chinese remainder theorem based location privacy method in Internet-of-Things sensing layer authentication
InactiveCN103840941ATo achieve the purpose of hiding the label positionUser identity/authority verificationSensing by electromagnetic radiationInternet privacyChinese remainder theorem
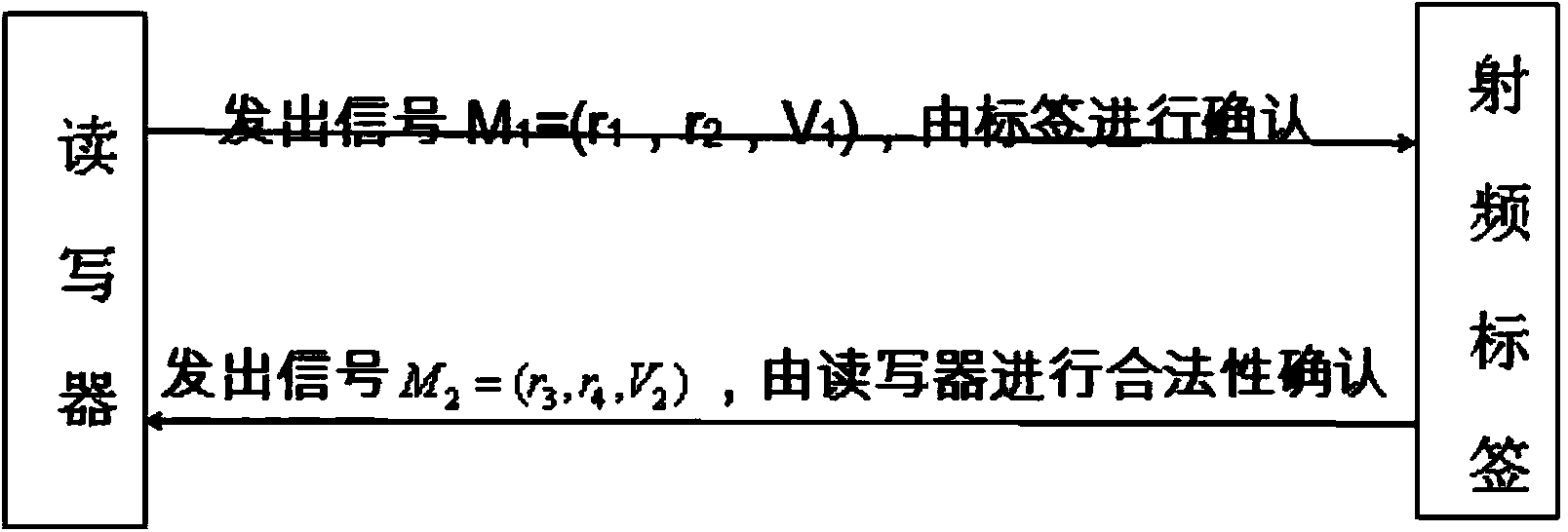
The invention discloses a Chinese remainder theorem based location privacy method in Internet-of-Things sensing layer authentication, and belongs to the technical field of Internet-of-Things safety. The method comprises the following steps that (1) at the distribution stage of key material, the key material is distributed from a key server and written into a radio frequency tag and a reader-writer; (2) at a search and authentication stage, the reader-writer and the radio frequency tag conduct data communication and authenticate validity of each other; (3) at the negotiated generating stage of a symmetric key, the reader-writer and the radio frequency tag calculates the shared key respectively, and the ID of the tag and other information are transmitted under the protection of the key. The method guarantees safety of location privacy in sensing layer authentication, and meets the requirement for safety of passive RFID. The method can enable the position of the tag to be hidden very well, namely, only the legal reader-writer can found that the tag exists nearby, and information of the tag is read; an illegal reader-writer can not found whether the tag exists nearby, and the purpose of hiding the position of the tag is achieved.
Owner:SOUTHEAST UNIV
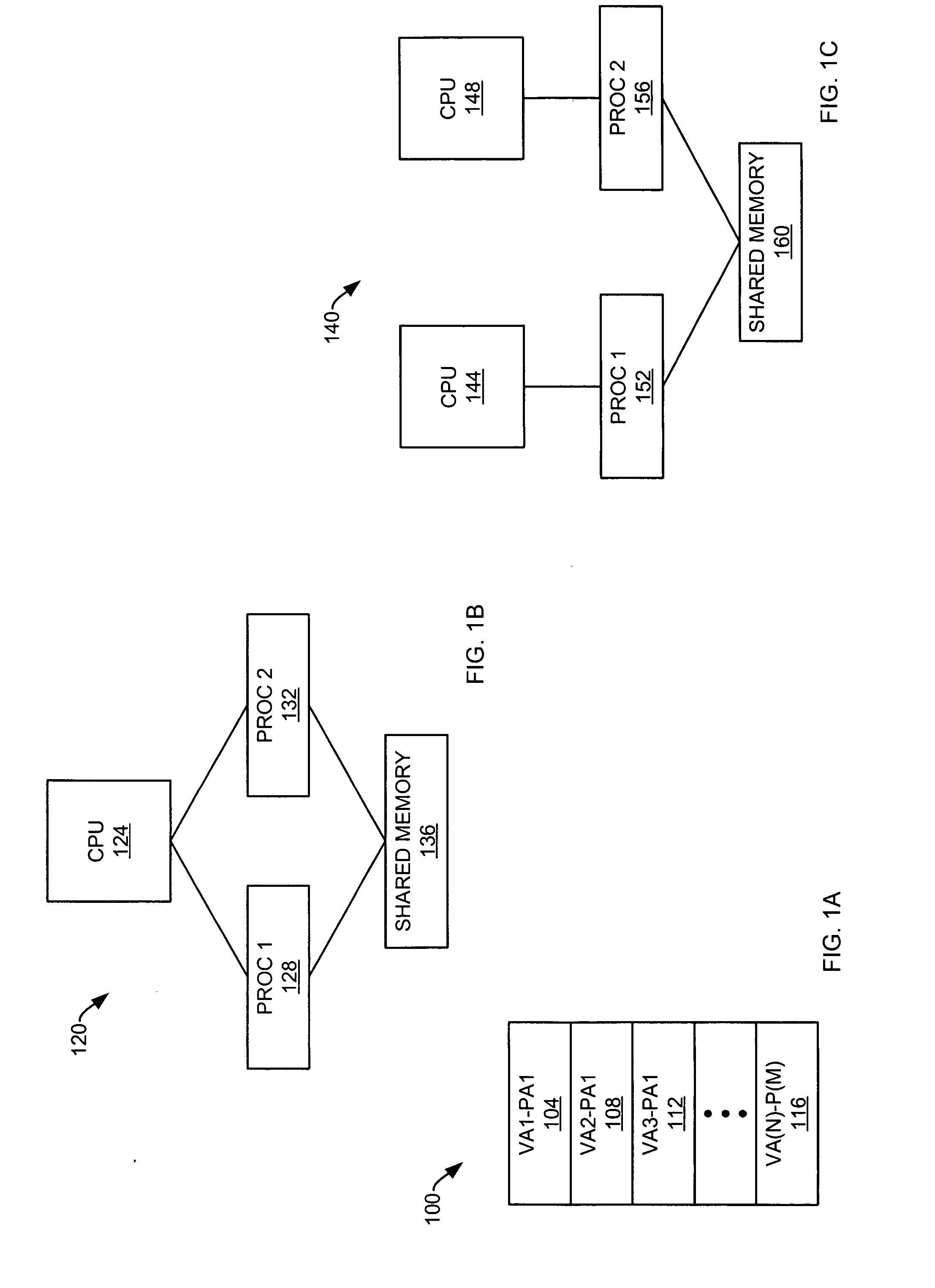
Systems and methods for identifying and registering a range of virtual memory
ActiveUS20060294320A1Great memory management efficiencyReduce in quantityMemory architecture accessing/allocationProgram controlUnique identifierVirtual memory
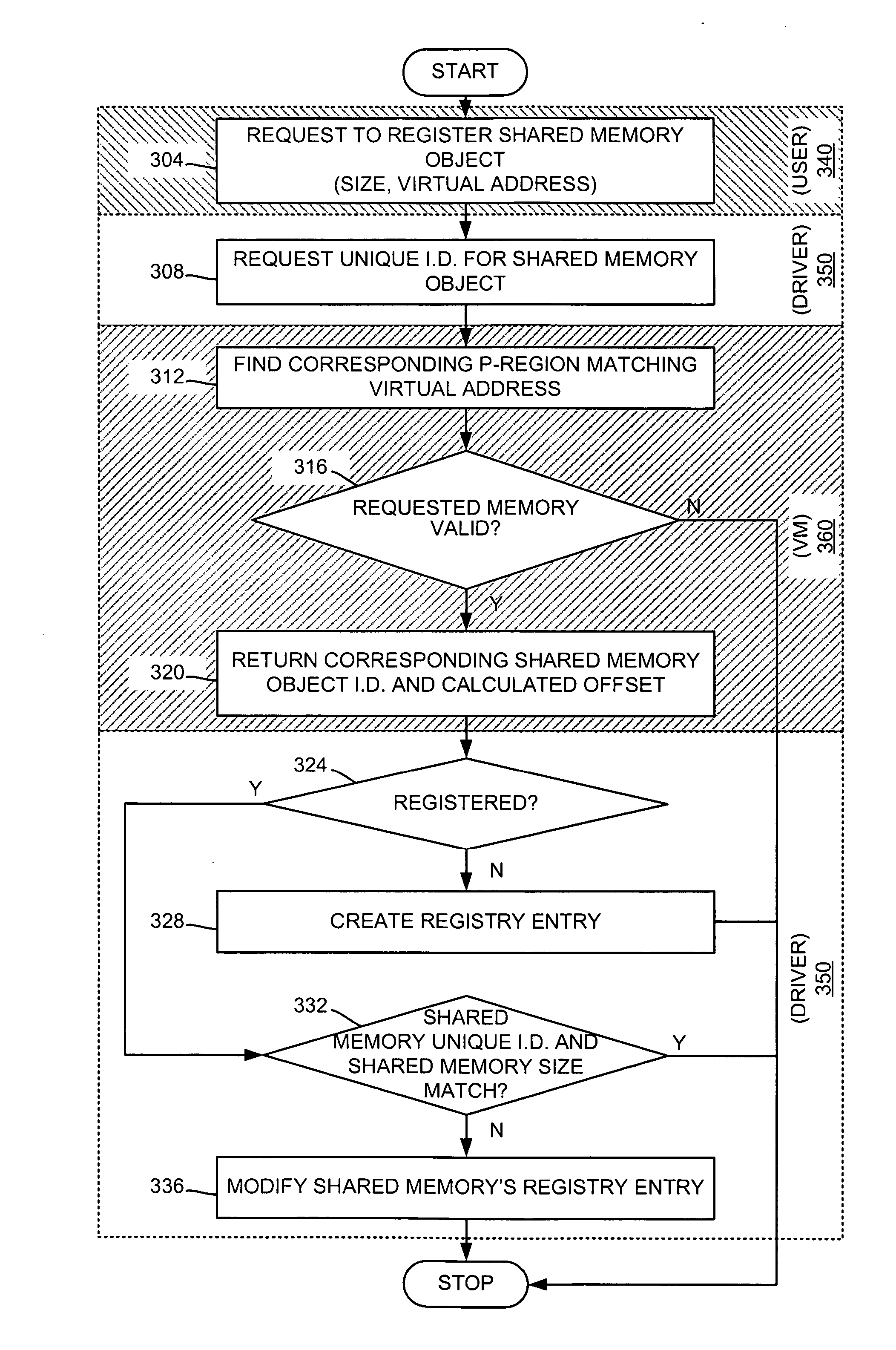
The invention provides apparatus and methods for registering shared memory objects. An exemplary embodiment of the invention is a method for registering a shared memory object are presented including: locating the shared memory object, the shared memory object having a first size and a first virtual address; finding a shared memory region associated with the shared memory object, the shared memory region having a second size and a second virtual address, the second virtual address returned as a unique identifier; and registering the shared memory object using the unique identifier. In some embodiments, the methods further include: calculating a memory offset for the shared memory region; and registering the shared memory range using the memory offset. In some embodiments, the methods further include: storing the unique identifier, the second size, and the memory offset in a persistent shared memory data structure.
Owner:SK HYNIX INC
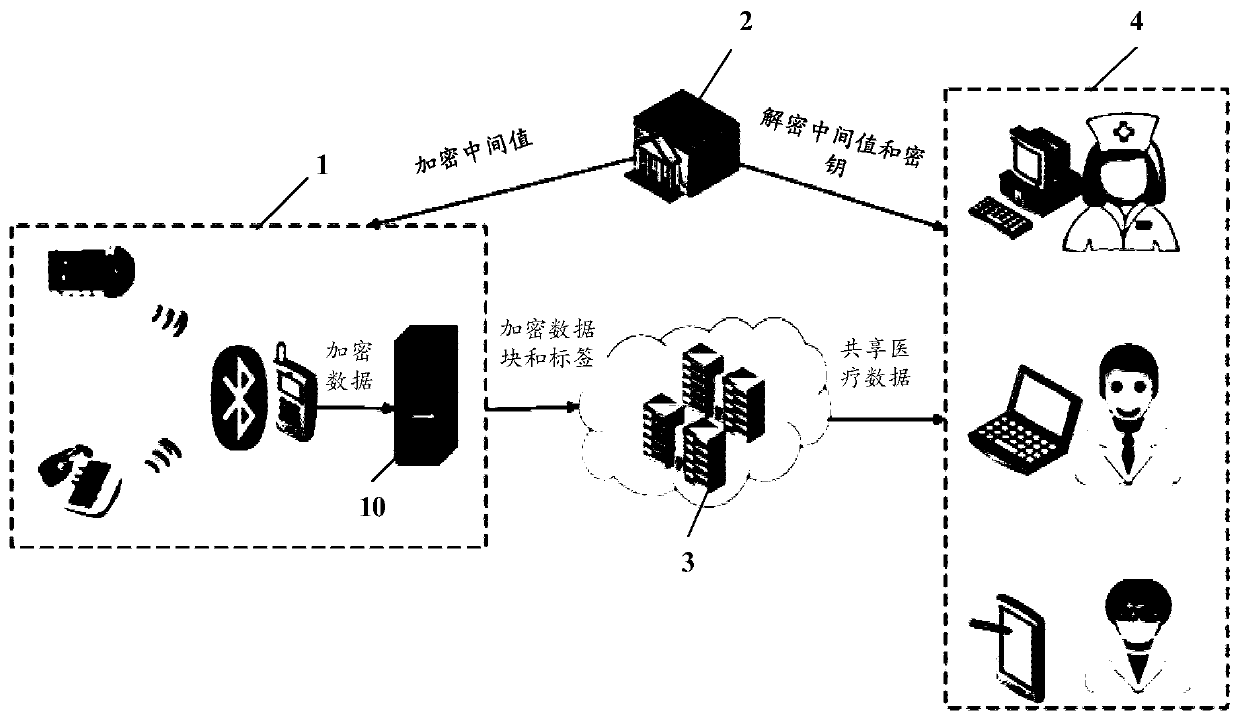
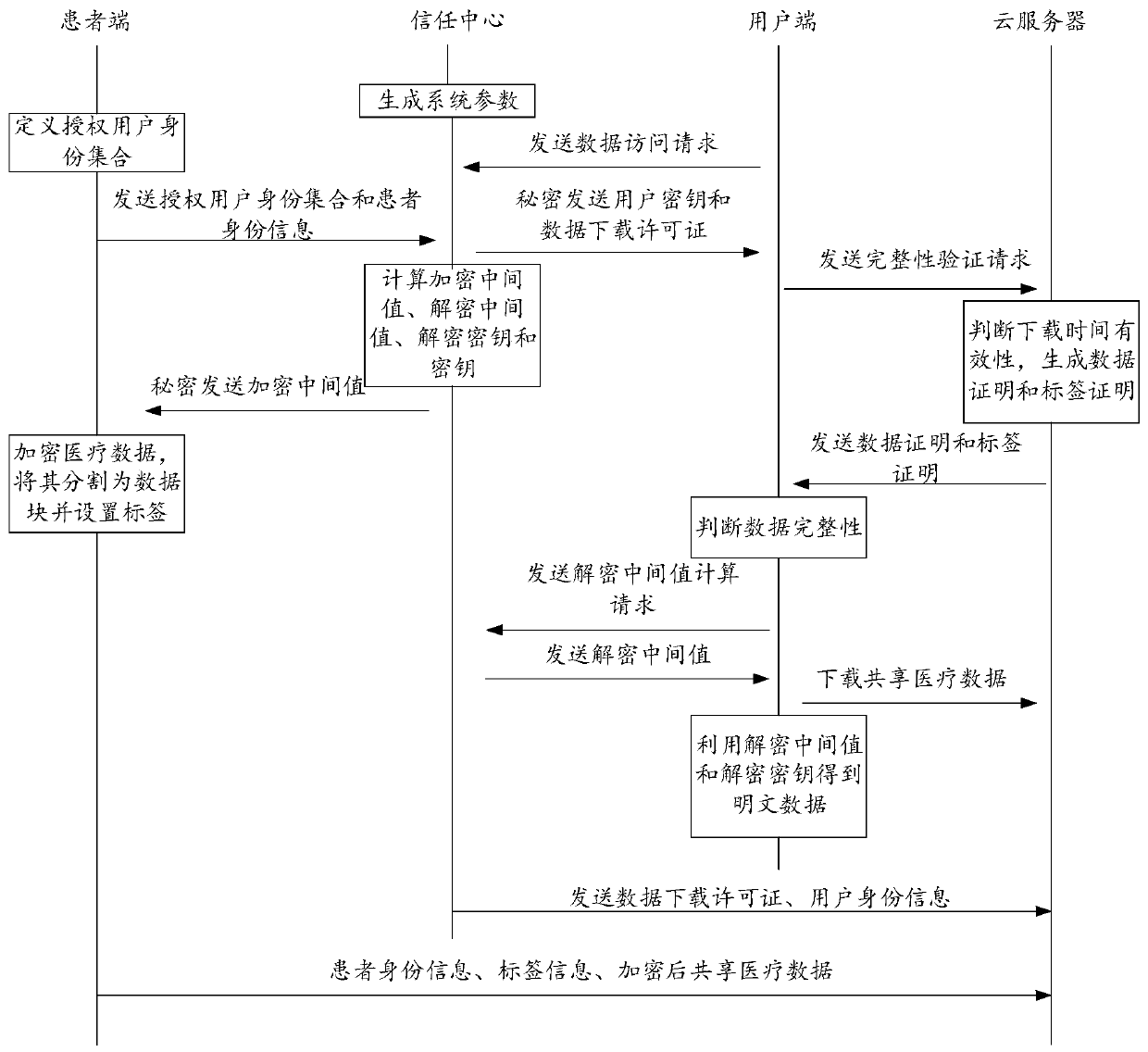
Lightweight ground-to-medical internet of things big data sharing system
The invention discloses a big data sharing system for a lightweight ground-to-medical internet of things. The big data sharing system comprises a patient terminal with built-in safety middleware, a trust center, a cloud server and a user terminal. The patient side performs data encryption on the shared medical data and sets an authorized user identity set, the encrypted shared medical data is divided into a plurality of data blocks by utilizing safety middleware, and labels are generated for the data blocks; the trust center calculates an encryption intermediate value and a decryption intermediate value of the shared medical data for the patient side and the user side based on the system parameters, and generates a data downloading license and a private key for the user; after the cloud server verifies that the data downloading time in the user data downloading license is valid, a data certificate and a label certificate are generated; and the client downloads the encrypted data from the cloud server and calculates a decryption key to obtain plaintext data after determining that the data is complete according to the data proof and the label proof. Safe and lightweight medical big data sharing is realized, and the privacy and integrity of the shared data are ensured.
Owner:QINGDAO UNIV
Determining time calibration value for user equipment
ActiveCN109154665ASynchronisation arrangementPosition fixationTelecommunicationsWireless transmission
In an embodiment, a given entity obtains a location of at least one terrestrial transmit station of a Synchronized Wireless Transmission Network (SWTN), transmit station calibration information associated with the at least one terrestrial transmit station and a location of a user equipment (UE) that is in wireless communication range with the at least one terrestrial transmit station. The given entity estimates the time calibration value for the UE based on the obtained transmit station location, the determined transmit station calibration information and the determined location of the UE. Inanother embodiment, a server obtains time calibration values that are estimated for each UE in the population of UEs. The server aggregates the estimated time calibration values based on device modeland / or device operation mode, and calculates a representative time calibration value for UEs sharing the device model and / or device operation mode.
Owner:QUALCOMM INC
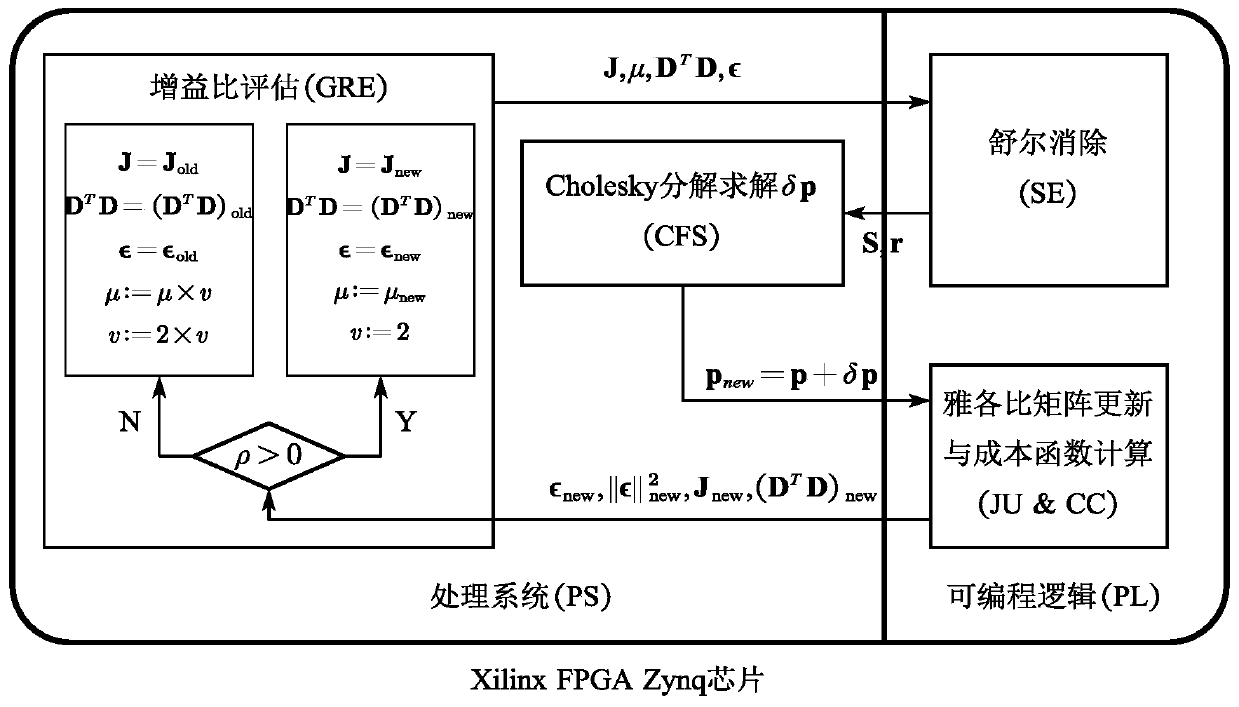
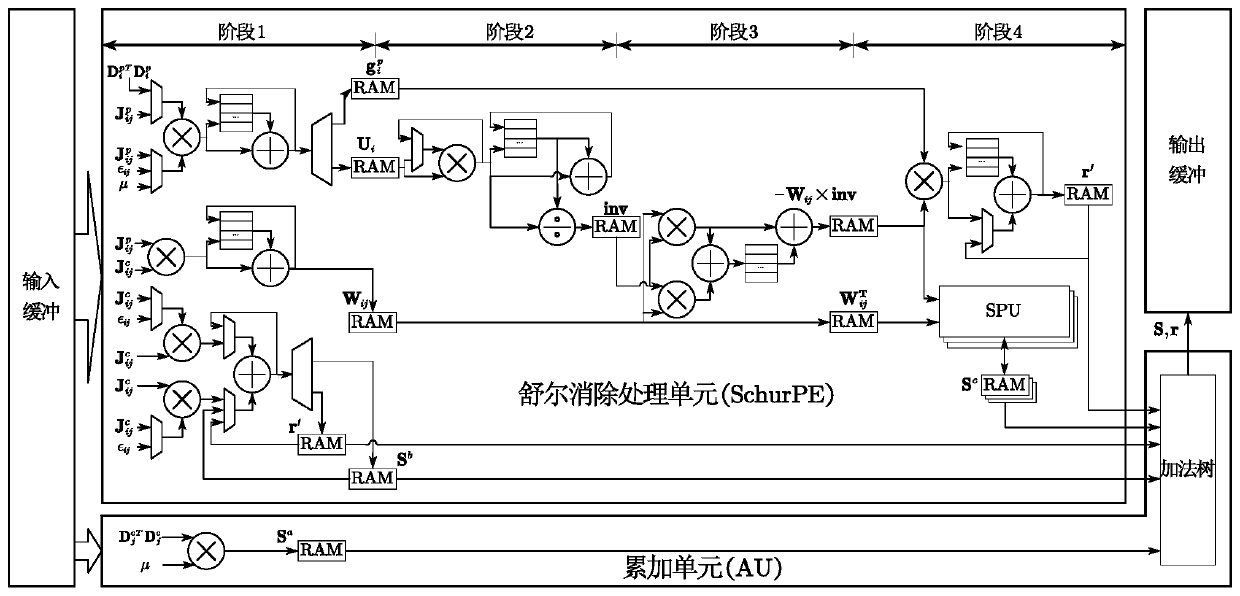
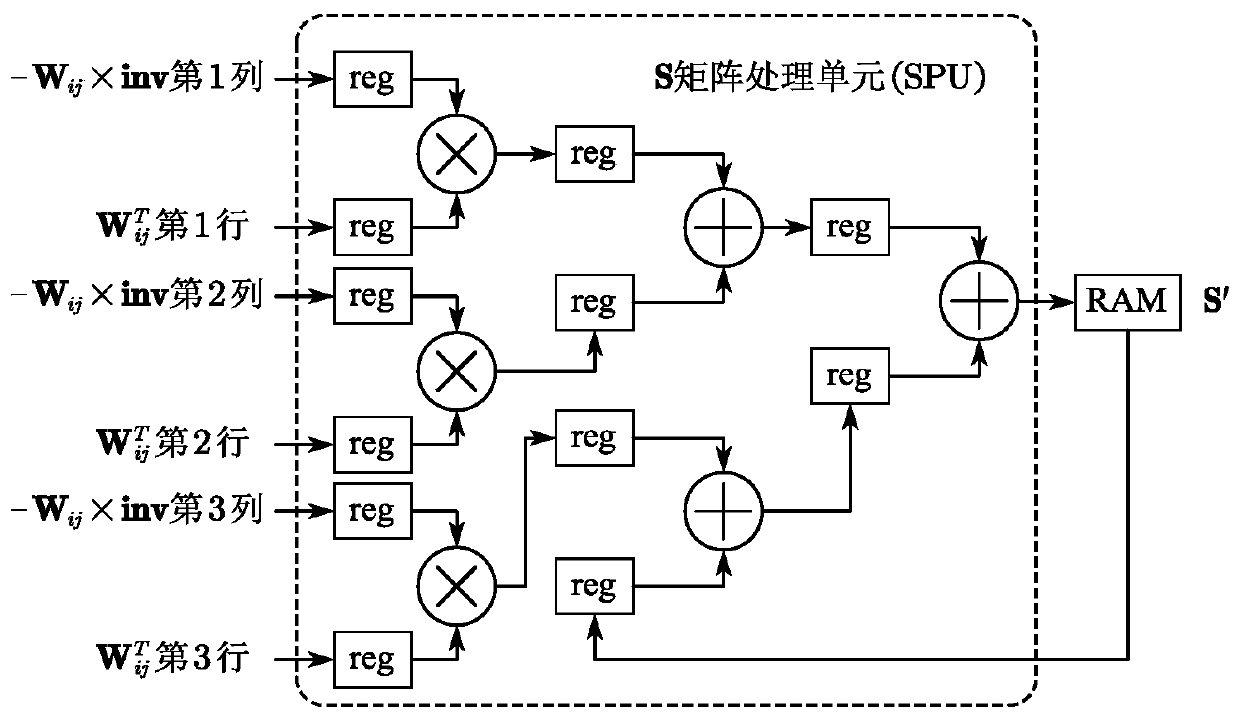
Beam adjustment method hardware accelerator based on Zynq FPGA
ActiveCN110928605AReduce consumptionImprove parallelismExecution paradigmsArchitecture with single central processing unitRandom access memoryParallel computing
The invention discloses a beam adjustment method hardware accelerator based on a Zynq FPGA. Shuer elimination, jacobian matrix updating and cost function calculation parts in a beam adjustment methodare realized at a PL end of Zynq through circuit design, and other parts are realized at a PS end of Zynq through software programming; an accelerator PL end splits two hardware circuits according toan algorithm, independent hardware is used for Shuer elimination, and Jacobian matrix updating and cost function calculation share the same hardware; wherein different computing units are formed in aninternal circuit of the accelerator, data transmission is carried out between the computing units by adopting a dual-port RAM (Random Access Memory) on an FPGA (Field Programmable Gate Array) chip, afinite-state machine is adopted in each computing unit, and read-in, read-out and storage of each step of data are controlled through state conversion; the Jacobian matrix updating and cost functioncalculating module calculates a Jacobian matrix by adopting a mode of combining analytic differential and automatic differential and calculates a cost function at the same time. BA calculation energyconsumption can be greatly reduced.
Owner:TIANJIN UNIV
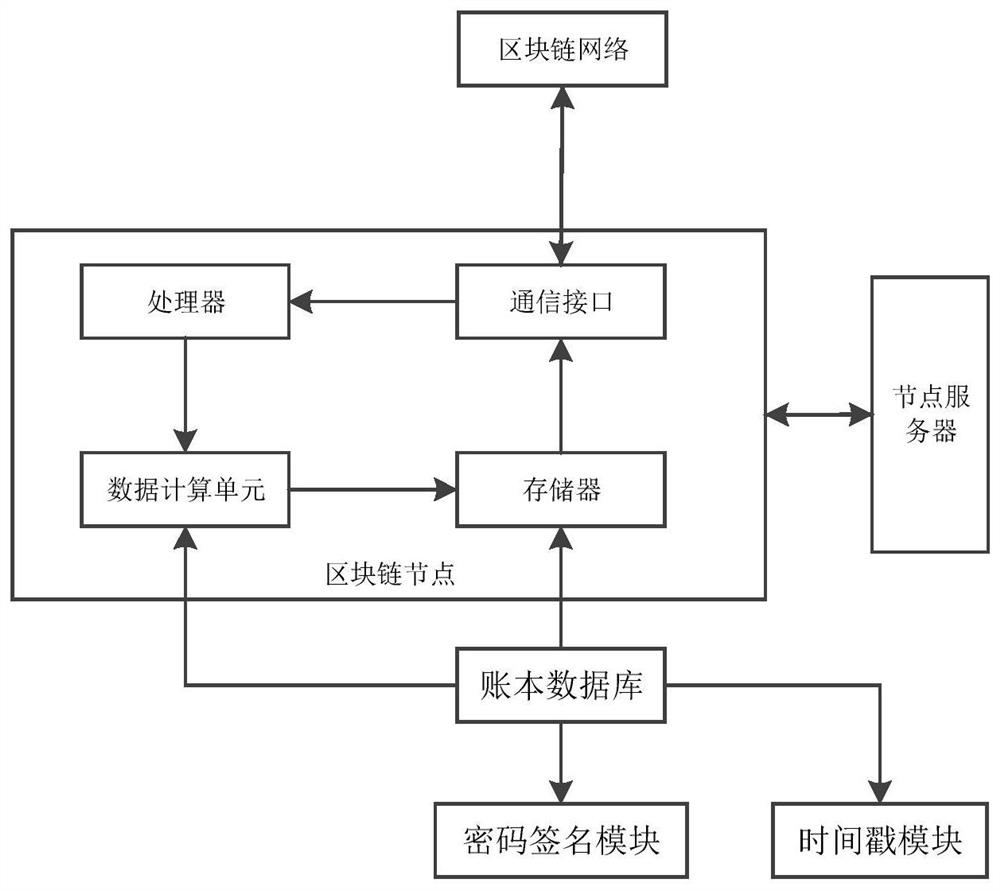
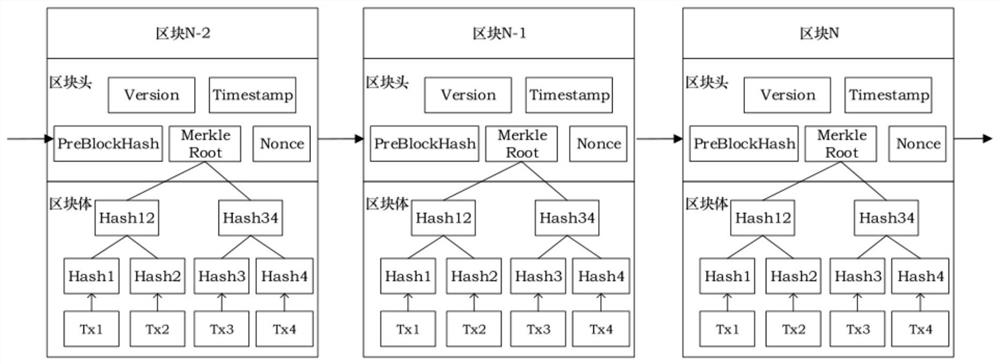
System and method for realizing data query by applying account book of block chain
PendingCN111949735AImprove reliabilityIncrease diversityDatabase distribution/replicationCharacter and pattern recognitionPasswordSoftware engineering
The invention discloses a system and a method for realizing data query by applying an account book of a blockchain, and relates to the technical field of block chains. By constructing a blockchain account book architecture, reliability, comprehensiveness, safety and accuracy of a novel family account book of the blockchain are further improved, so that the reform and development of the traditionalaccount book are promoted. Various big data algorithm models are integrated into the blockchain account book architecture to realize data calculation and processing, so that simple processing of various complex data is realized, the information latitude of big data is reduced, and data query is facilitated. Encryption calculation after data processing is achieved through an encryption unit, and safety performance of data is improved. A modular blockchain solution supporting platform based on Hyperleder Fabric is used, a blockchain data calculation, sharing and transmission platform is provided, and data processing, calculation and query are realized; and data packaging and processing are realized through a password signature module and a timestamp module.
Owner:鲁泽军
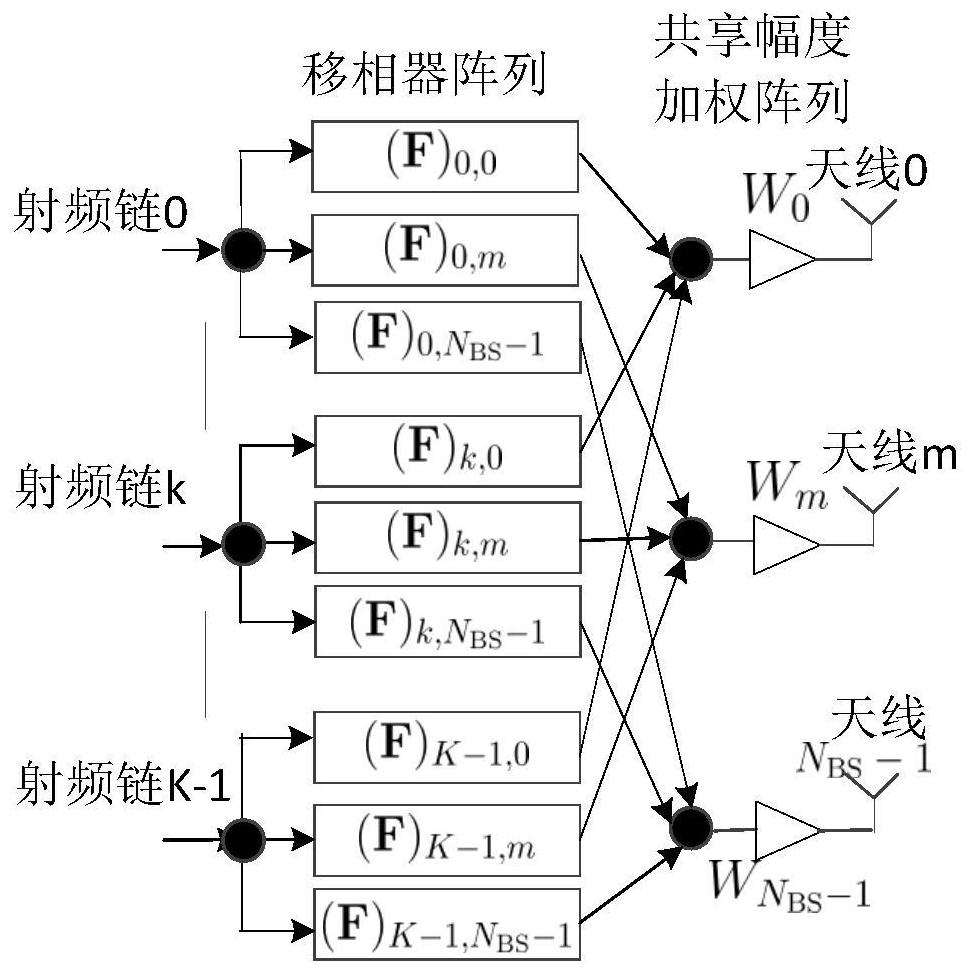
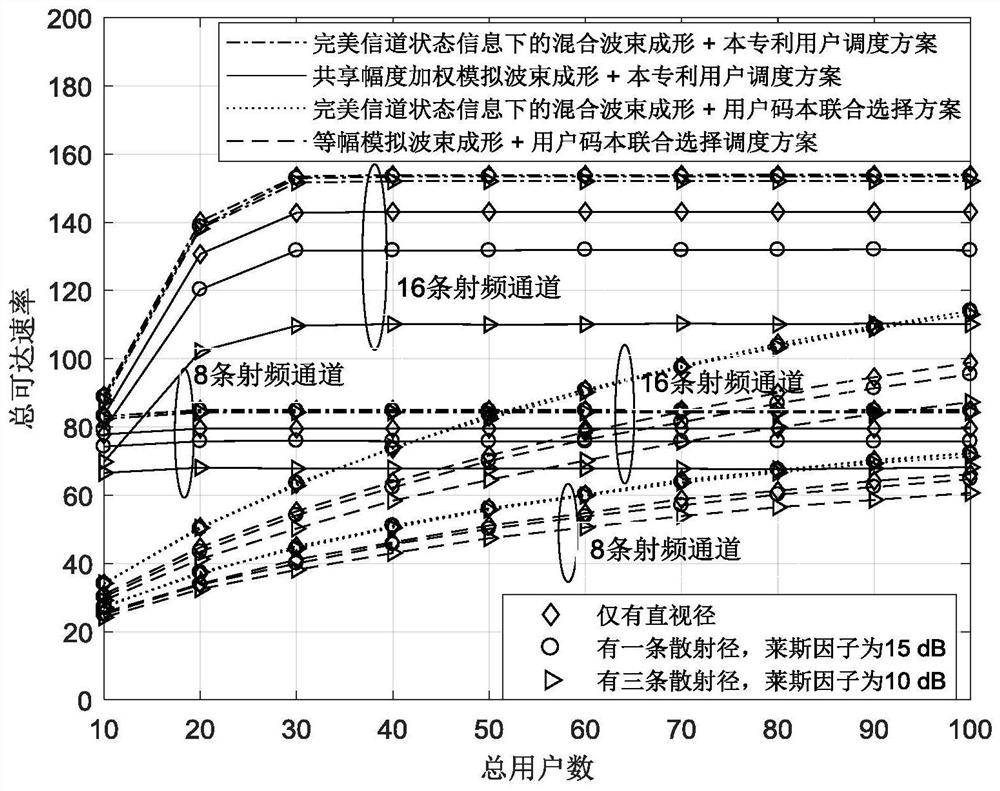
Millimeter wave pure analog beamforming user scheduling method
ActiveCN112165347AAvoid serious distractionsLow costSpatial transmit diversityInterference (communication)Service user
The invention provides a millimeter wave pure analog beamforming user scheduling method. The method comprises the following steps: S1, enabling a channel of a k-th user side to adopt a Rician channelmodel hk; S2, enabling a base station end to adopt an equidistant linear array antenna, and calculating an antenna array response vector alpha(theta) with an departure angle theta; S3, supposing thatthe base station has K*1 original signal s to be sent to K clients, and calculating a shared amplitude weighted analog beam forming matrix FRF; S4, conducting service user selection through a heuristic user scheduling method; S5, designing a shared amplitude weight; and S6, designing a k-th column fk of the first-stage analog domain precoding matrix F. The user scheduling mode is applied to a pureanalog domain beam forming technology, interference among multiple users is greatly reduced in a multi-path sparse scene, and the inherent defect that a pure analog beam forming scheme is not suitable for multi-user communication is overcome; only the departure angle of the downlink path of each user is needed, the path coefficient of the channel is not needed, only little channel information isneeded, and the training overhead is greatly reduced.
Owner:HEFEI IC VALLEY MICROELECTRONICS CO LTD
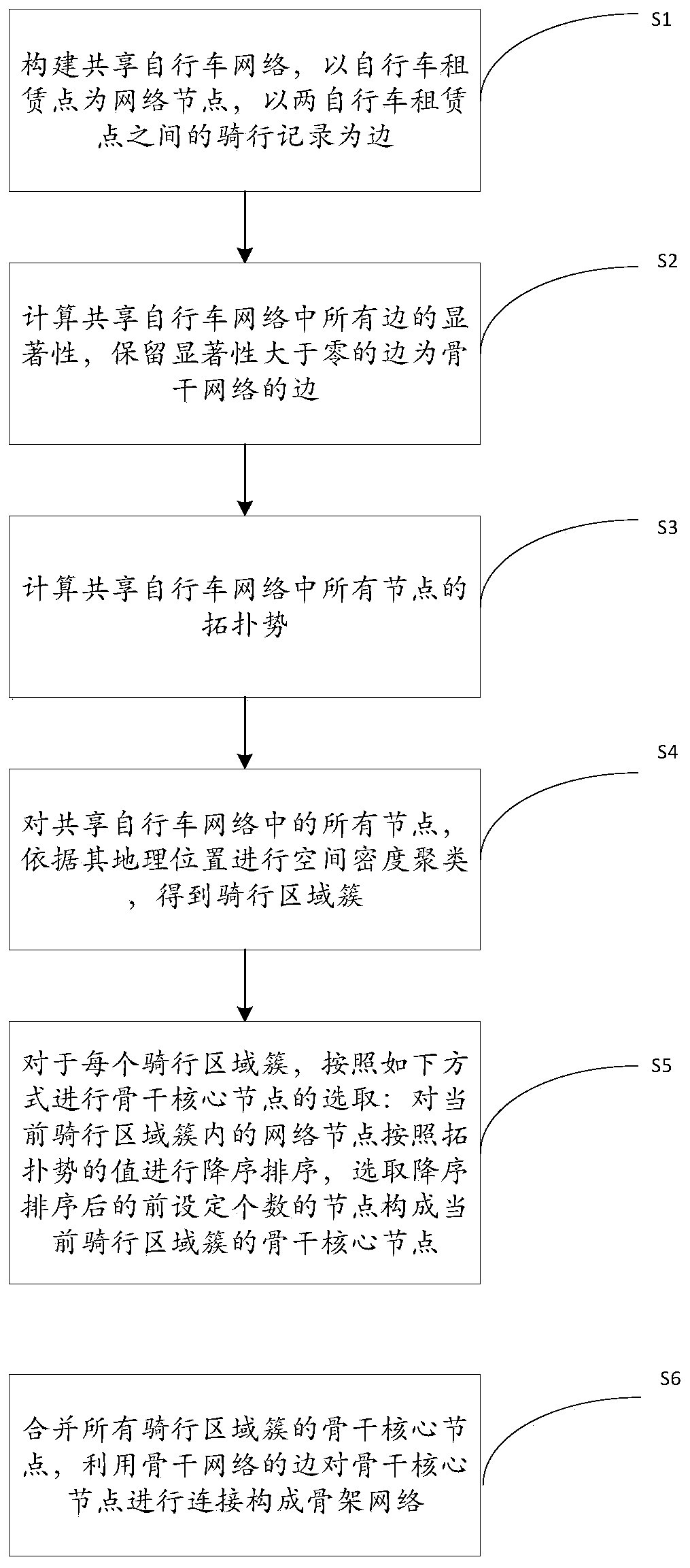
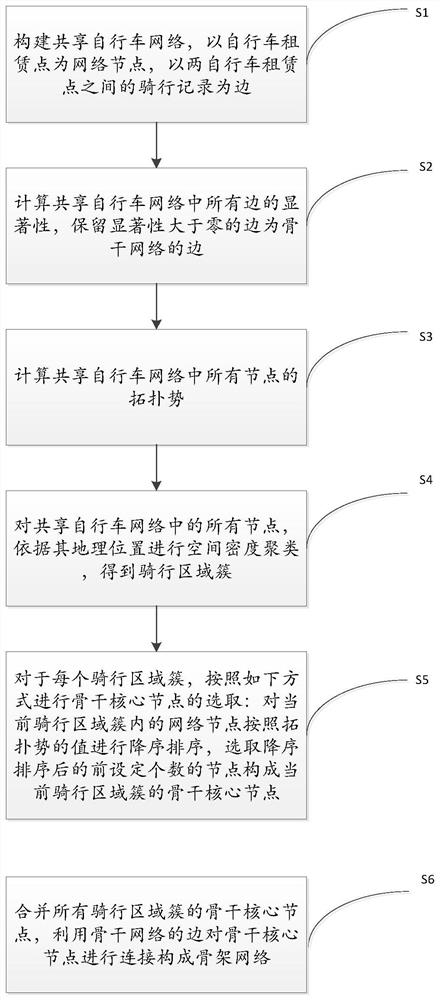
Shared bicycle skeleton network extraction method
ActiveCN110798802AGuaranteed stabilityRestoring Basic Topology PropertiesParticular environment based servicesNetwork topologiesEngineeringComputation sharing
The invention discloses a shared bicycle skeleton network extraction method, belongs to the technical field of computer application, and can perform backbone network extraction on a network composed of network nodes with spatial position features. The method comprises the following steps: constructing a shared bicycle network; and calculating the significance of all edges in the shared bicycle network, and keeping the edges with the significance greater than zero as the edges of the backbone network; and calculating the topological potential of all nodes in the shared bicycle network; performing spatial density clustering on all nodes in the shared bicycle network according to the geographic positions of the nodes, and acquiring a riding area cluster ; For each riding area cluster, performing descending sorting on the network nodes in the current riding area cluster according to the value of the topological potential, and selecting the front set number of nodes after descending sortingto form a backbone core node of the current riding area cluster; and combining the backbone core nodes of all the riding area clusters, and connecting the backbone core nodes by using the edges of the backbone network to form a skeleton network.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
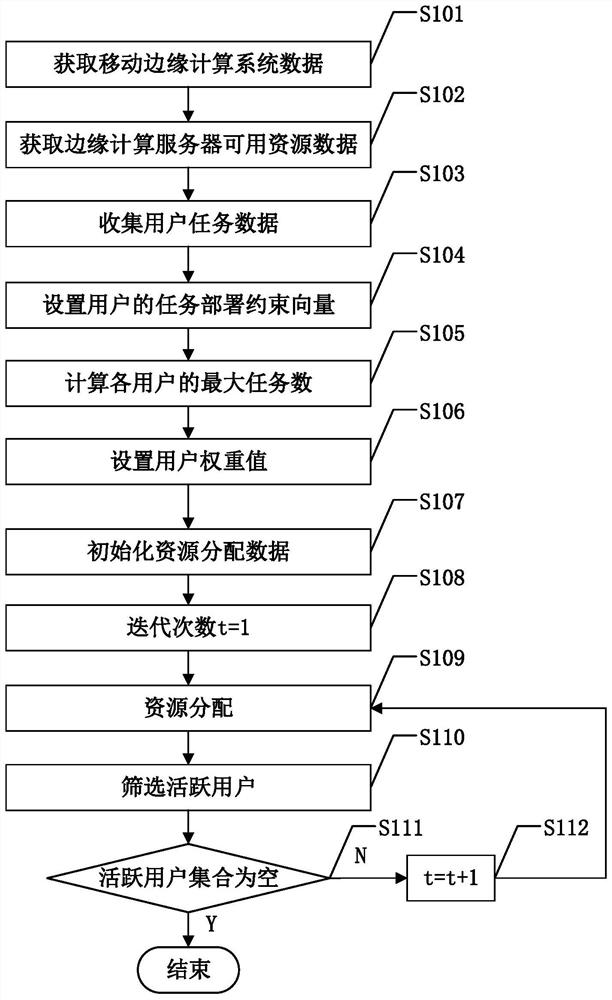
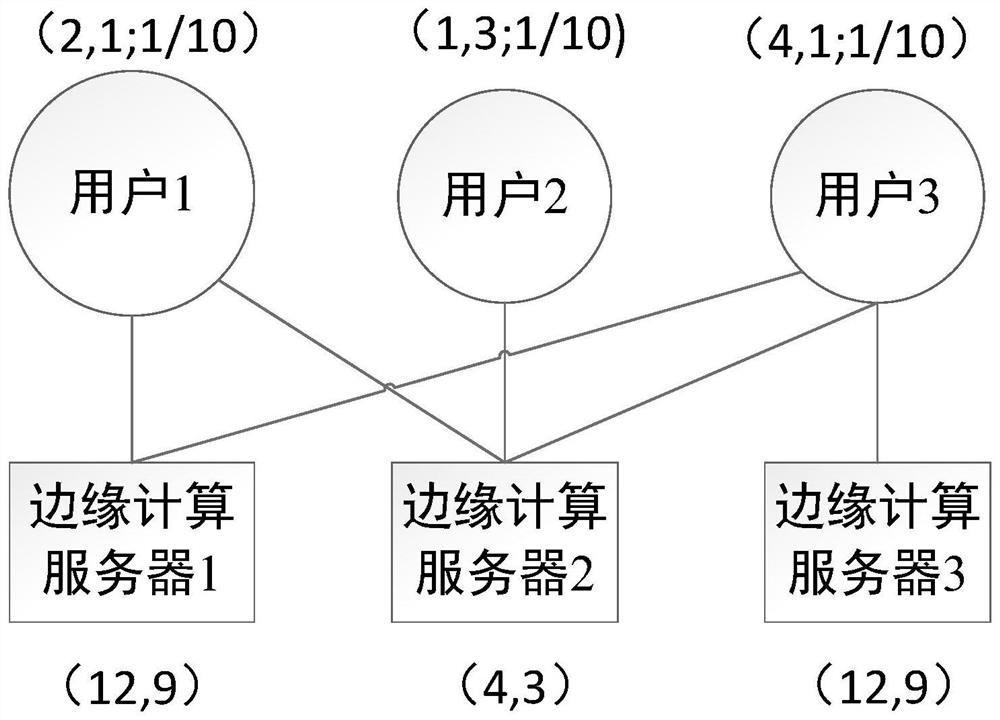
Fair allocation method for mobile edge computing shared resources under task deployment constraints
ActiveCN111611076AGuarantee individual interestsEfficient and fair distributionResource allocationResource assignmentEdge computing
The invention discloses a fair allocation method for mobile edge computing shared resources under task deployment constraints. The method comprises the following steps of firstly, determining an edgecomputing server set and available resource capacity; obtaining a resource demand vector and a task deployment constraint vector of a user; calculating the maximum number of tasks which can be executed under the condition that the user monopolizes resources and setting the weight of the user; when resources allocation, setting active user sets and allocating the active users based on a task sharemaximum and minimum allocation principle; with the task shares of other inactive users unchanged, screening the active users after each round of allocation is completed, wherein the users whose taskshares cannot be continuously increased in the next round of resource allocation are converted into the inactive users, and finishing resource allocation until all the users are the inactive users. The individual interests of the users are fully guaranteed under the task deployment constraint condition of the edge computing environment, and the resource allocation efficiency and fairness are improved.
Owner:YUNNAN UNIV
Key agreement devices and method
ActiveUS11050557B2Reduce communicationReduce computationKey distribution for secure communicationMultiple keys/algorithms usageKey exchangeComputer network
A first electronic network node (110) is provided configured for a key exchange (KEX) protocol, the first network node is configured to obtain a shared polynomial (a) shared with a second network node, coefficients of the shared polynomial a being selected modulo a first modulus q, generate a private key polynomial (skI), coefficients of the private key polynomial being bounded in absolute value by a bound (s) generate a public key polynomial (pkI) by computing a polynomial product between the shared polynomial (a) and the private key polynomial (skI) modulo the first modulus (q) and scaling the coefficients of the polynomial product down to a second modulus (p).
Owner:KONINKLJIJKE PHILIPS NV
Multi-source remote sensing big data processing method and device based on Chord ring
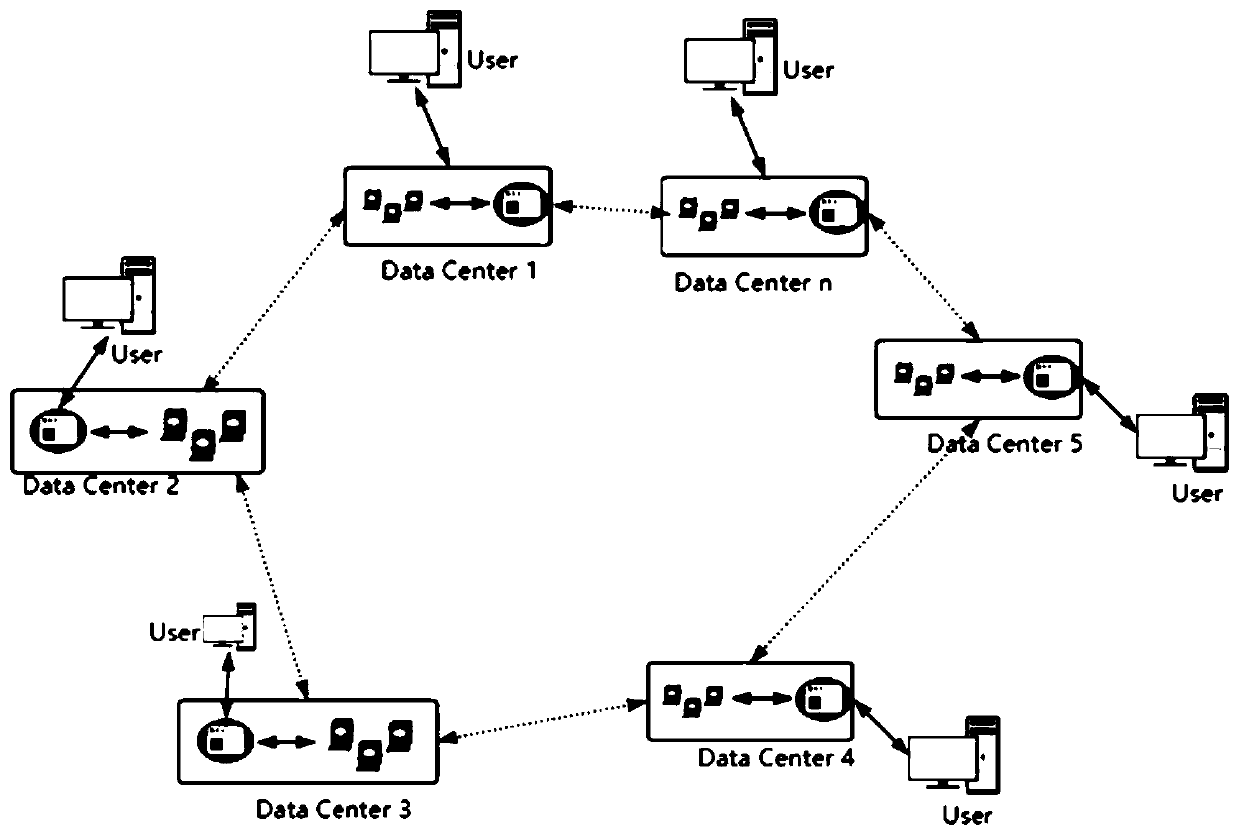
InactiveCN110955731ARealize computing sharingIndependentDatabase distribution/replicationSpecial data processing applicationsSensing dataRouting table
The invention relates to the field of remote sensing big data, in particular to a multi-source remote sensing big data processing method and device based on a Chord ring. According to the multi-sourceremote sensing big data processing method and device, each data center is used as a node of a Chord ring, is provided with an external interface and is provided with a routing table for inquiring routing work. Each data center has certain independence, has an independent task submission site, and can access data of other data centers at the same time. And a plurality of data centers form a Chordring logically. The multi-source remote sensing big data processing method has good transverse expansion capability, can thoroughly solve the migration problem of the remote sensing data while realizing data sharing, and can realize calculation sharing of the remote sensing data.
Owner:SHENZHEN INST OF ADVANCED TECH
Multi-channel video storage method and system
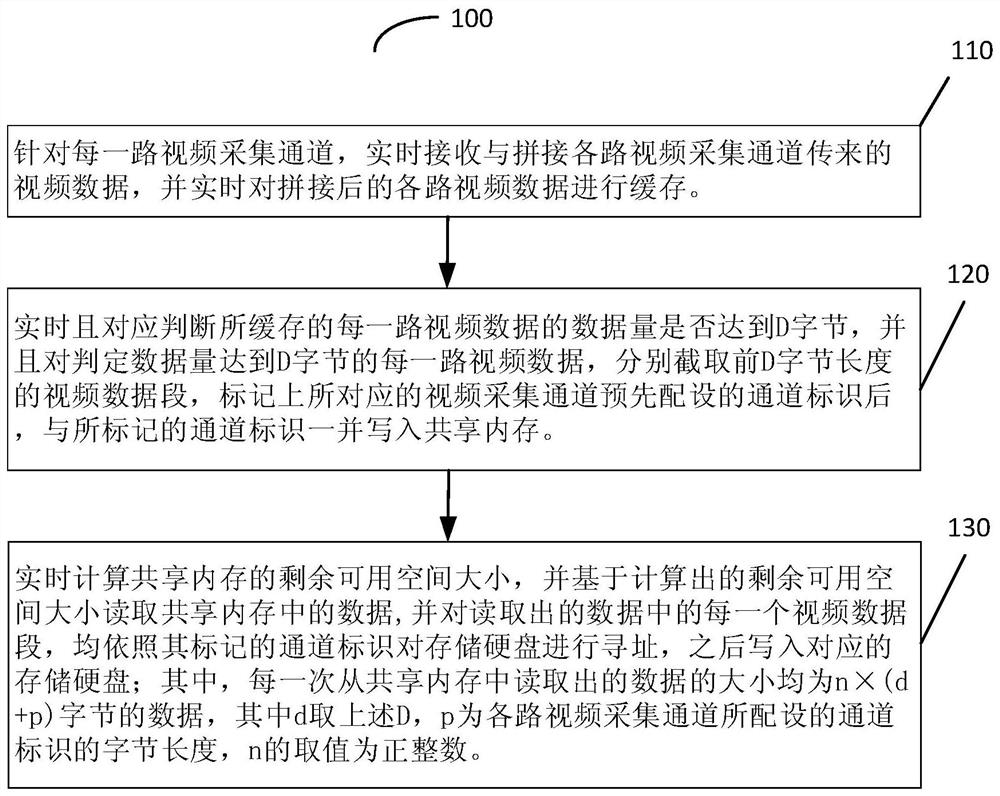
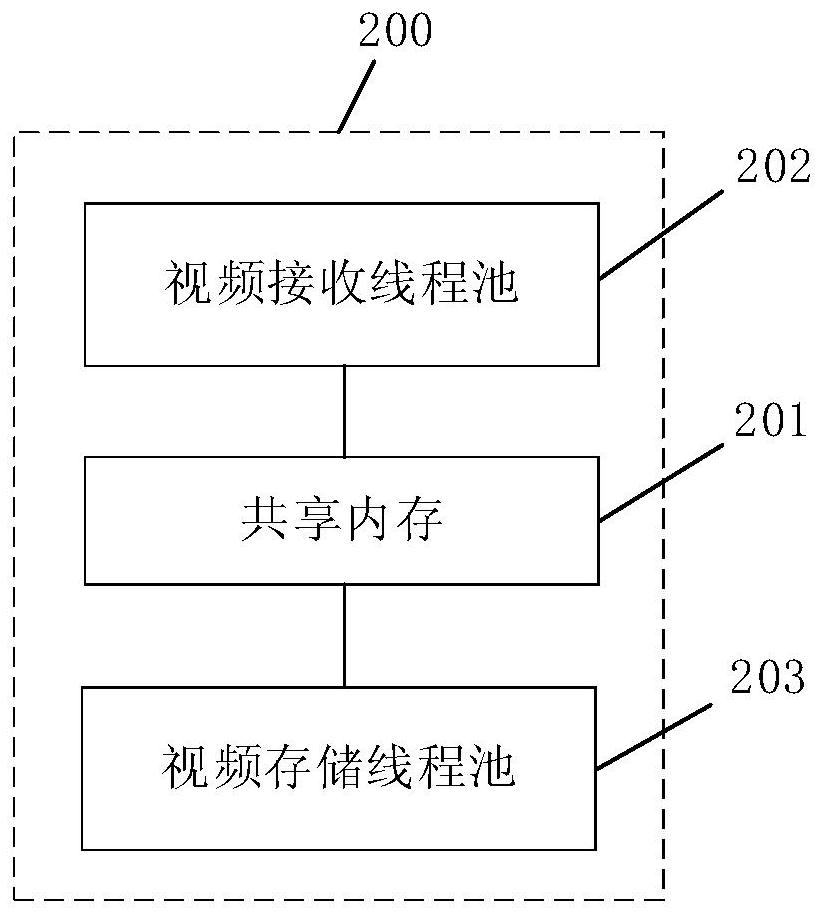
ActiveCN113473039ASolve the problem of excessive memory space requirementsTemporary memory space avoidanceTelevision system detailsVideo data indexingVideo storageData segment
The invention provides a multi-channel video storage method and system, and the method comprises the steps: receiving, splicing and caching video data transmitted by each video collection channel in real time for each video collection channel; correspondingly judging whether the data size of each path of cached video data reaches D bytes or not in real time, wherein video data segments with the length of the front D bytes are cut for each path of video data with the data size reaching D bytes, and the video data segments are written into a shared memory after channel identifiers are marked; and calculating the size of the remaining available space of the shared memory in real time, reading the data in the shared memory based on the calculated size of the remaining available space, addressing the storage hard disk for each read video data segment according to the marked channel identifier, and then writing in the corresponding storage hard disk. According to the method, the number of hard disk operation times is reduced, the requirement for temporary memory storage space is lowered, and the rationality of hard disk space utilization is improved.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Field hexapod robot control training method based on double operators
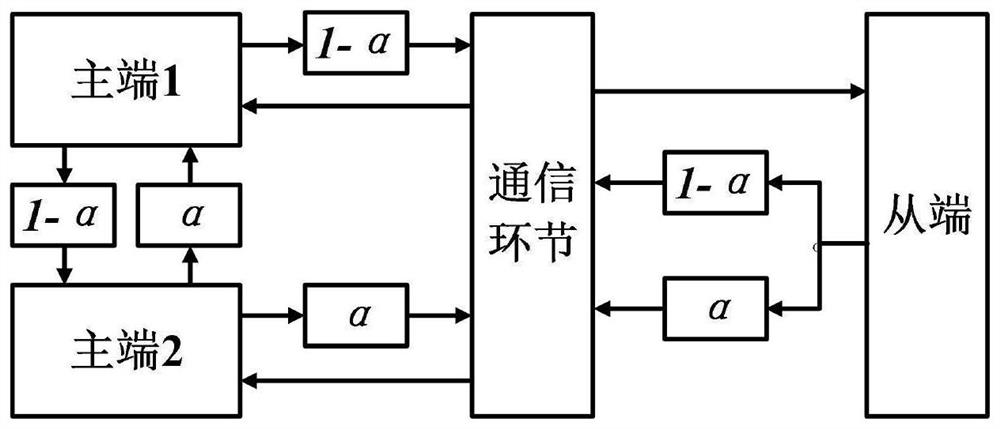
The invention belongs to the technical field of teleoperation of foot-type robots. The invention discloses a field hexapod robot control training method based on double operators. The problem of control weight distribution of a trainer to a trainee in hexapod robot control training is solved. The invention discloses a field hexapod robot control training method based on double operators, is applied to a double-master single-slave structure system, and provides a system transparency analysis and application method, a sharing factor calculation method and the like. The system transparency analysis and application method comprises the following steps: calculating transparency deviation ratios of a master end and a slave end, analyzing system transparency, and calculating a sharing factor value range based on the transparency deviation ratios. According to the sharing factor calculation method, a new calculation method is used, and the value range of the sharing factor is combined to calculate the sharing factor. The control training efficiency of the hexapod robot can be effectively improved, and the safety of the system can be improved while the transparency is ensured.
Owner:HARBIN UNIV OF SCI & TECH
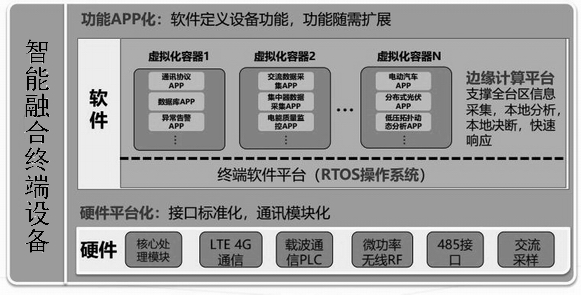
Intelligent fusion terminal equipment
InactiveCN112421777AReduce computing pressureWeaken high dependenceCircuit arrangementsInformation technology support systemDecision controlFull data
The invention discloses intelligent fusion terminal equipment. The equipment comprises a core processing module, a communication module, a micro-power wireless RF module, a serial interface module, acarrier communication PLC module, an alternating current sampling voltage source module, a data sampling module, a virtualization container module and the like. Full data acquisition and full management and control are realized, and key operation data exchange between the intelligent fusion terminal equipment and a power distribution main station is realized in real time. In order to meet the real-time quick response requirement, reduce the calculation pressure of the main station and weaken the high dependence on the main station, the terminal adopts an edge calculation technology to locallyrealize the online monitoring, intelligent analysis and decision control of the operation state of a power distribution area, and supports the calculation sharing and data interaction with the cloud of the power distribution main station at the same time.
Owner:JIANGSU FRONTIER ELECTRIC TECH
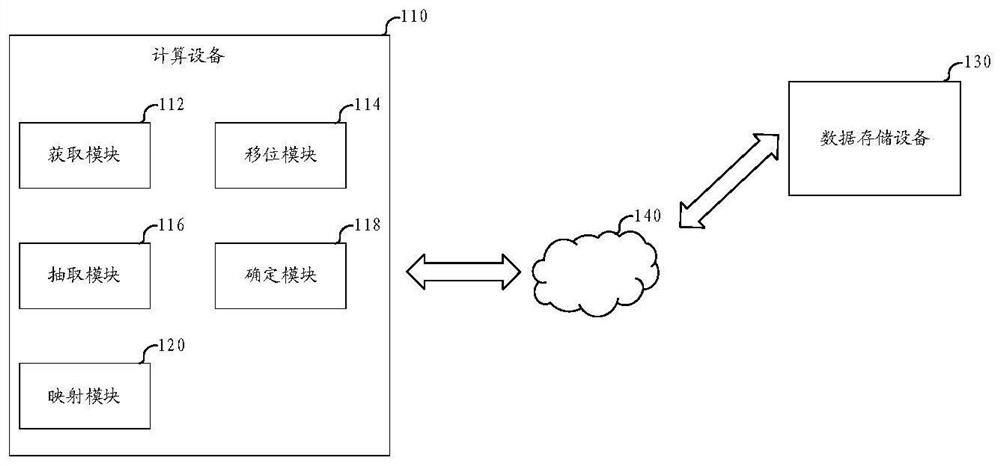
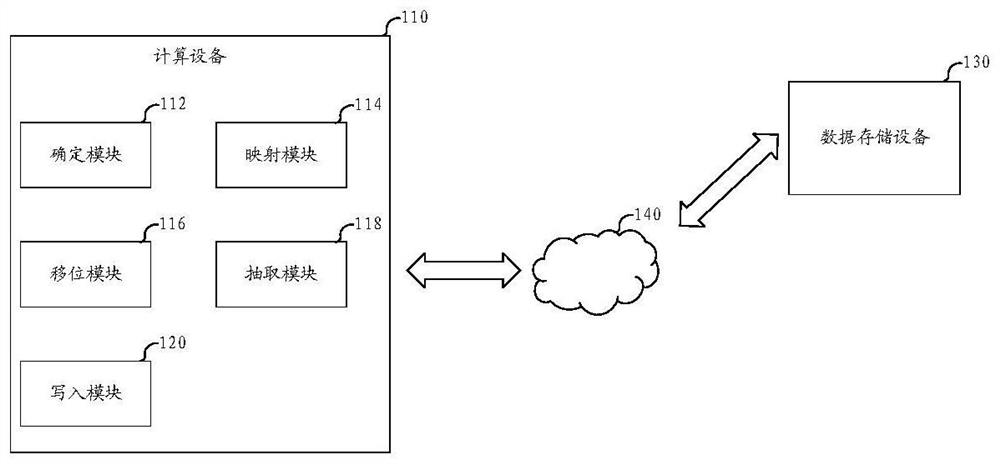
Method, equipment and medium for realizing data arrangement
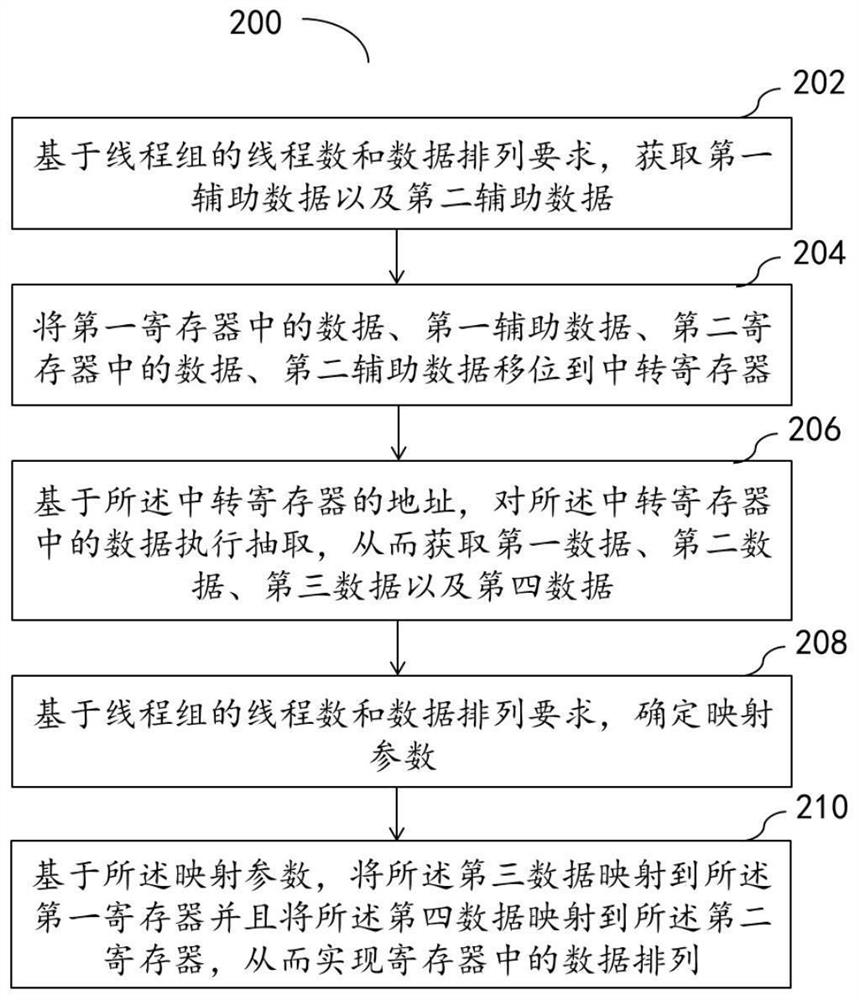
The embodiment of the invention relates to a method and device for achieving data arrangement and a medium, and the method comprises the steps that first auxiliary data and second auxiliary data are obtained based on the thread count of a thread group and the data arrangement requirement; shifting the data in the first register, the first auxiliary data, the data in the second register and the second auxiliary data to a transfer register; extracting the data in the transfer register based on the address of the transfer register so as to obtain first data, second data, third data and fourth data; determining a mapping parameter based on the thread count of the thread group and the data arrangement requirement; and based on the mapping parameter, mapping the third data to the first register and mapping the fourth data to the second register, thereby realizing data arrangement in the registers. Therefore, data arrangement among a plurality of registers can be realized more quickly under the condition that the shared memory address is not calculated.
Owner:SHANGHAI BIREN TECH CO LTD
Data distribution method based on SRIO global memory sharing
PendingCN111767135AIncrease profitImplement schedulingResource allocationData graphParallel computing
The invention discloses a data distribution method based on SRIO global memory sharing, which adopts an SRIO exchange mode based on a star architecture and is mainly applied to systems such as a multi-unit server, a multi-computer module group, a multi-computing unit workstation, a multi-computing unit graphic workstation, a multi-resource data sharing platform and the like. Distributed calculation of big data calculation is mainly realized, a global memory is shared, the resource utilization rate and the calculation efficiency are improved, and the high efficiency and the real-time performance of data and image processing in the system are effectively improved.
Owner:江苏和正特种装备有限公司
A Wi-Fi positioning method for shared bicycles based on 3D calibration
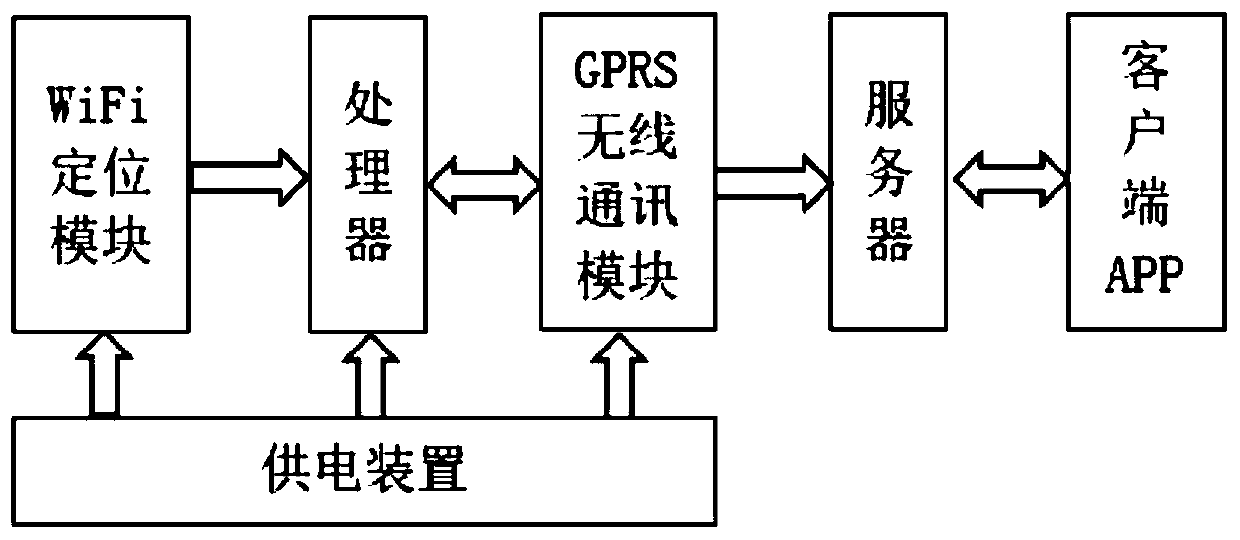
ActiveCN108834044BReduce loadReduce workloadTransmission systemsParticular environment based servicesEngineeringBicycle sharing
The invention relates to the field of shared bicycle communication positioning, and provides a shared bicycle WiFi positioning method based on three-dimensional calibration. The method comprises the following steps: before a shared bicycle is put into operation, performing AP (Access Point) three-dimensional calibration and establishing an AP information database; after the shared bicycle is put into operation, acquiring AP positioning information in an area by a WiFi positioning module, and transferring the acquired AP positioning information to a processor; processing the AP positioning information by the processor and controlling a GPRS module to upload the processed information to a server; calculating the current position of the shared bicycle by the server according to the received information and the AP information database; and responding to a positioning request of a display client by the server, performing data screening and calculation according to the positioning request, and transmitting calculated position information to a positioning display client in real time. According to the shared bicycle WiFi positioning method based on the three-dimensional calibration provided by the invention, when the AP information database is established, only a database of AP label number coordinate information in the area is established, thus the workload is saved and the load of the server is reduced.
Owner:JIANGSU UNIV
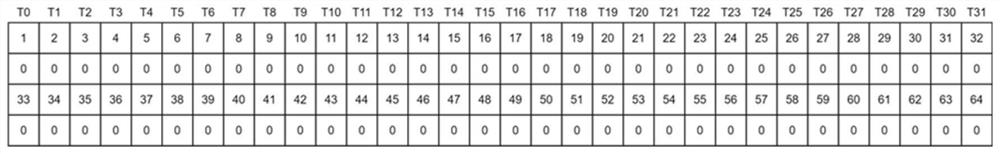
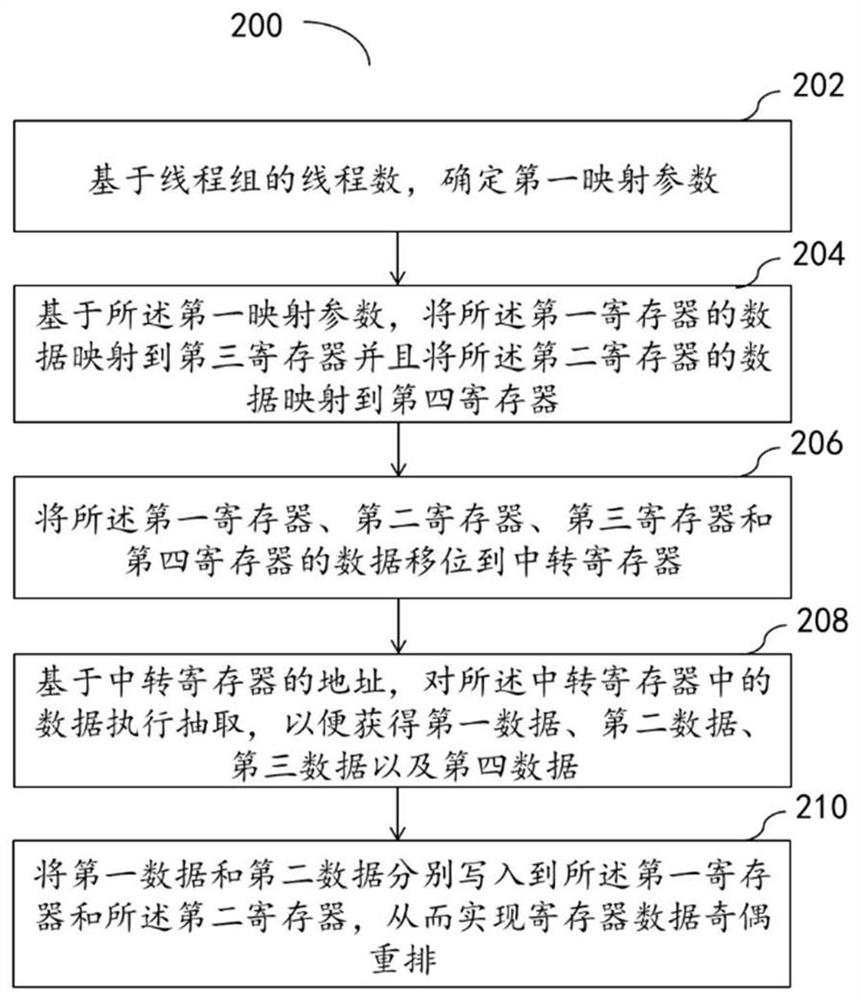
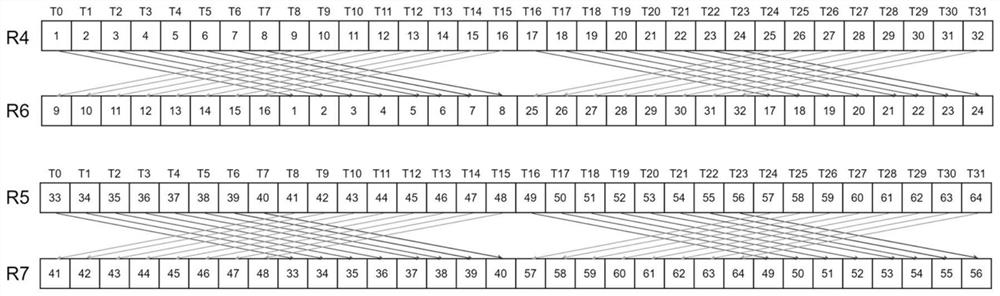
Method, equipment and medium for realizing data parity rearrangement
The embodiment of the invention relates to a method and equipment for realizing data parity rearrangement and a medium, and the method comprises the steps: determining a first mapping parameter based on the thread count of a thread group; based on the first mapping parameter, mapping data of the first register to the third register and mapping data of the second register to a fourth register; shifting data of the first register, the second register, the third register and the fourth register to a transfer register; based on the address of the transfer register, executing extraction on the data in the transfer register so as to obtain first data, second data, third data and fourth data; first data and second data are written into the first register and the second register respectively, and therefore register data odd-even rearrangement is achieved. Therefore, odd-even rearrangement of the data between the two registers can be realized more quickly under the condition that the address of the shared memory is not calculated.
Owner:SHANGHAI BIREN TECH CO LTD
Shared station intelligent distribution method, server, equipment and system
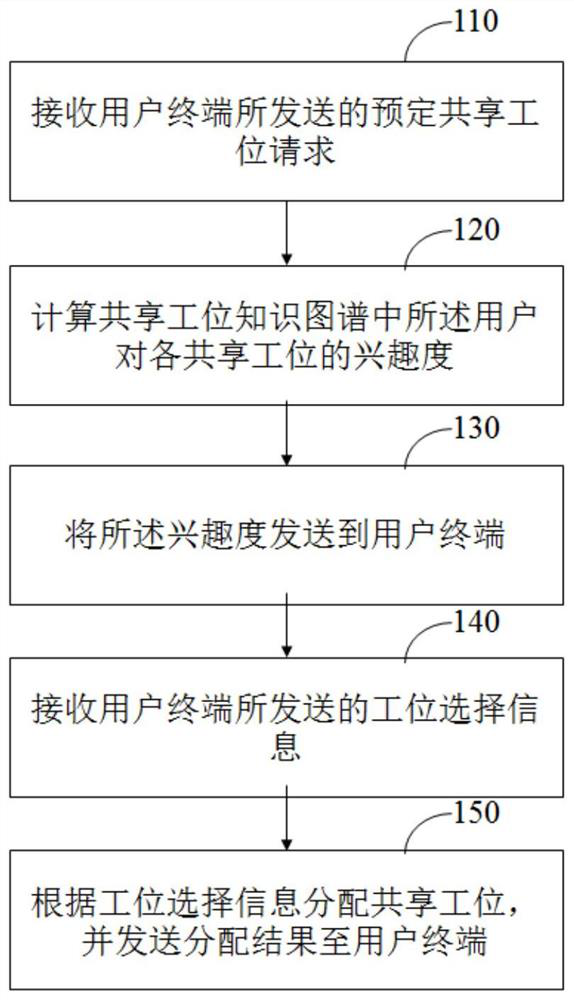
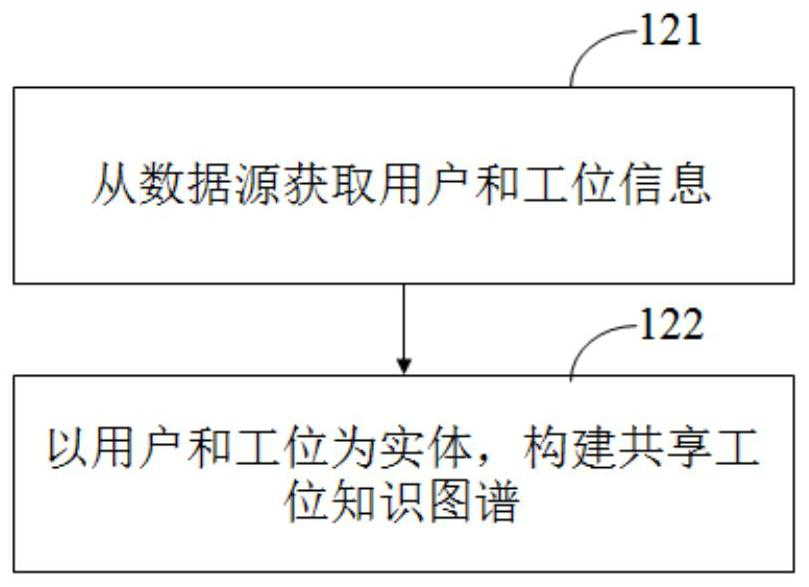
The invention provides a shared station intelligent distribution method. The method comprises the steps: receiving a preset shared station request transmitted by a user terminal; calculating the interestingness of the user to each shared station in the shared station knowledge graph; sending the interestingness to a user terminal so that the user terminal can display stations identified accordingto the interestingness and generate a station selection interface; receiving station selection information sent by the user terminal, wherein the station selection information comprises a station identifier and a predetermined time period; and allocating shared stations according to the station selection information, and sending an allocation result to the user terminal, so that the user terminaldisplays the allocation result. The invention solves the problem of lack of a reasonable and efficient shared station allocation method in the prior art, and provides the intelligent reservation method, the server, the equipment and the system which can enable a user to find and reserve a proper shared station more quickly, reduce the time cost of the user and improve the user experience. The system can be applied to the fields of incubator offices, office buildings implementing shared stations, enterprises and the like.
Owner:广州腾新科技有限公司
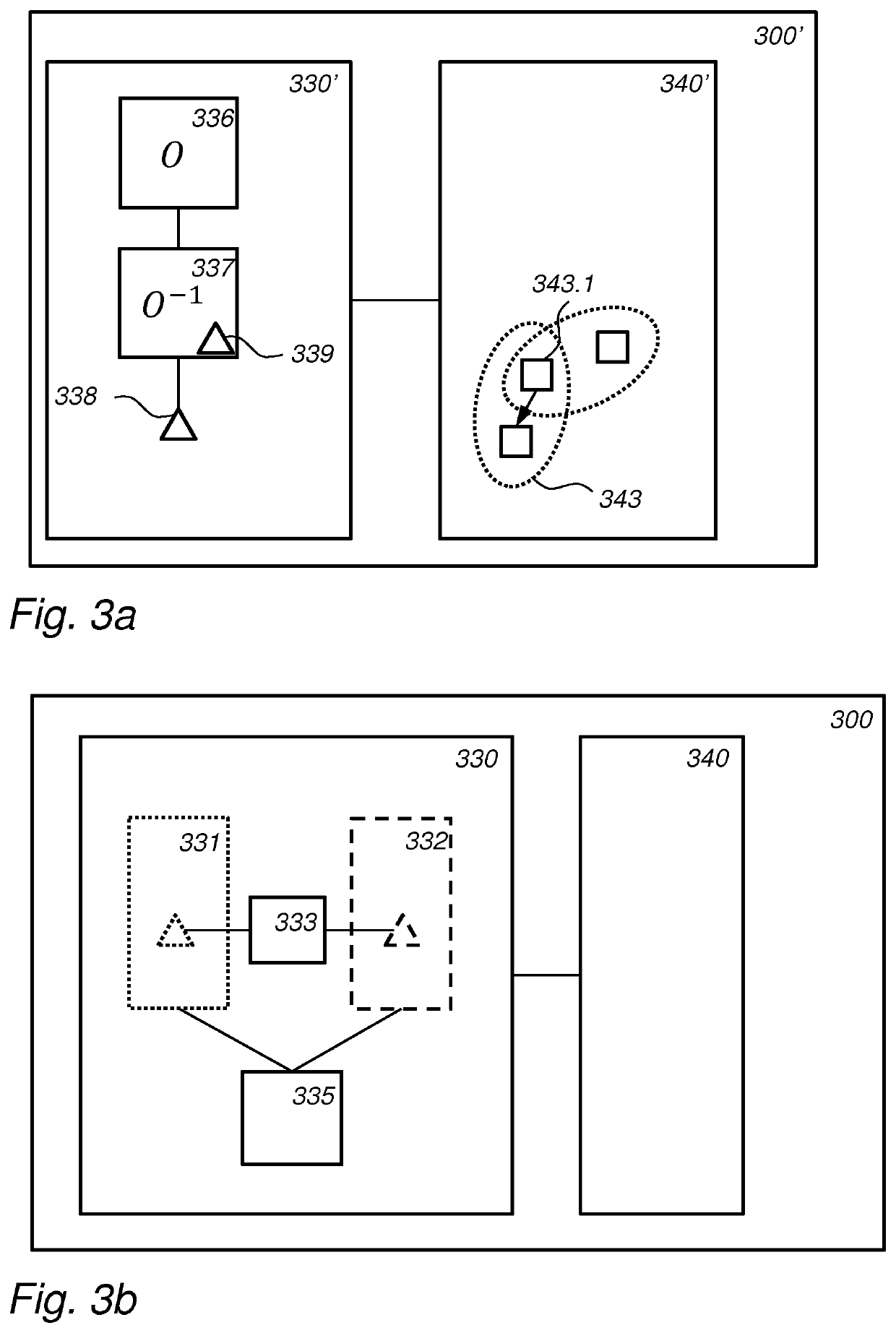
Key agreement method for identity-unpaired wireless network cross-domain handover authentication
ActiveCN107360567BEfficiency improvement for switching authenticationReduce computational overheadSecurity arrangementAttackInternet privacy
Owner:SOUTHWEST JIAOTONG UNIV
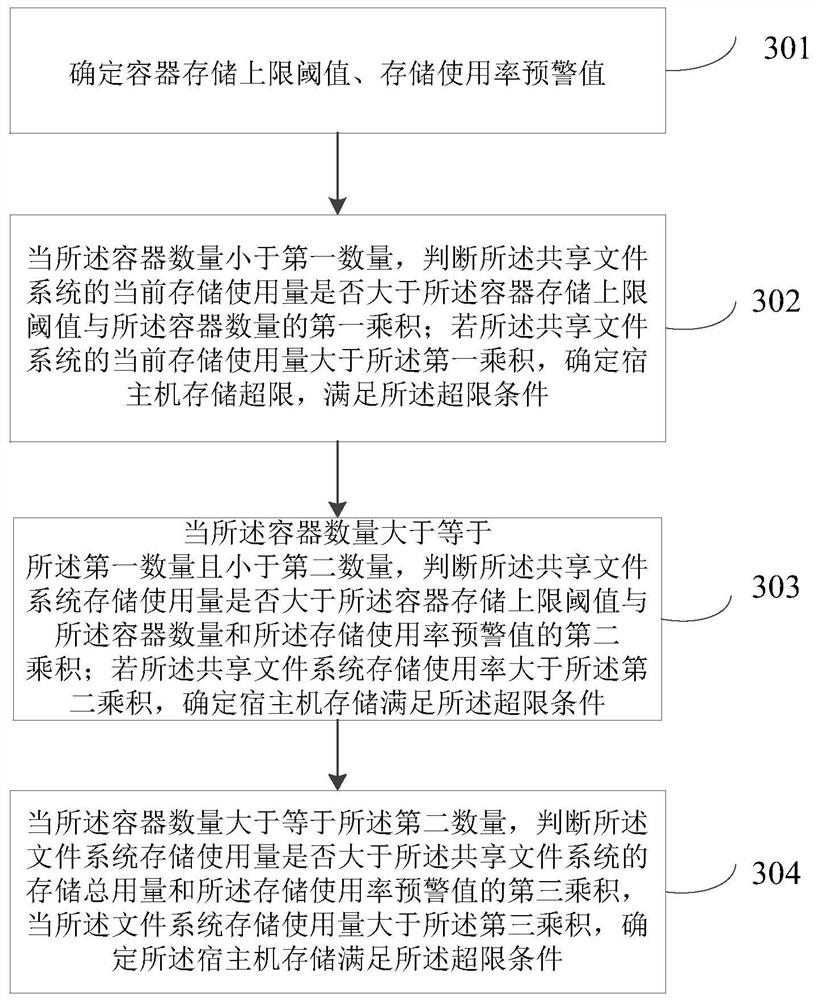
Container storage utilization rate monitoring method and device, computer equipment and storage medium
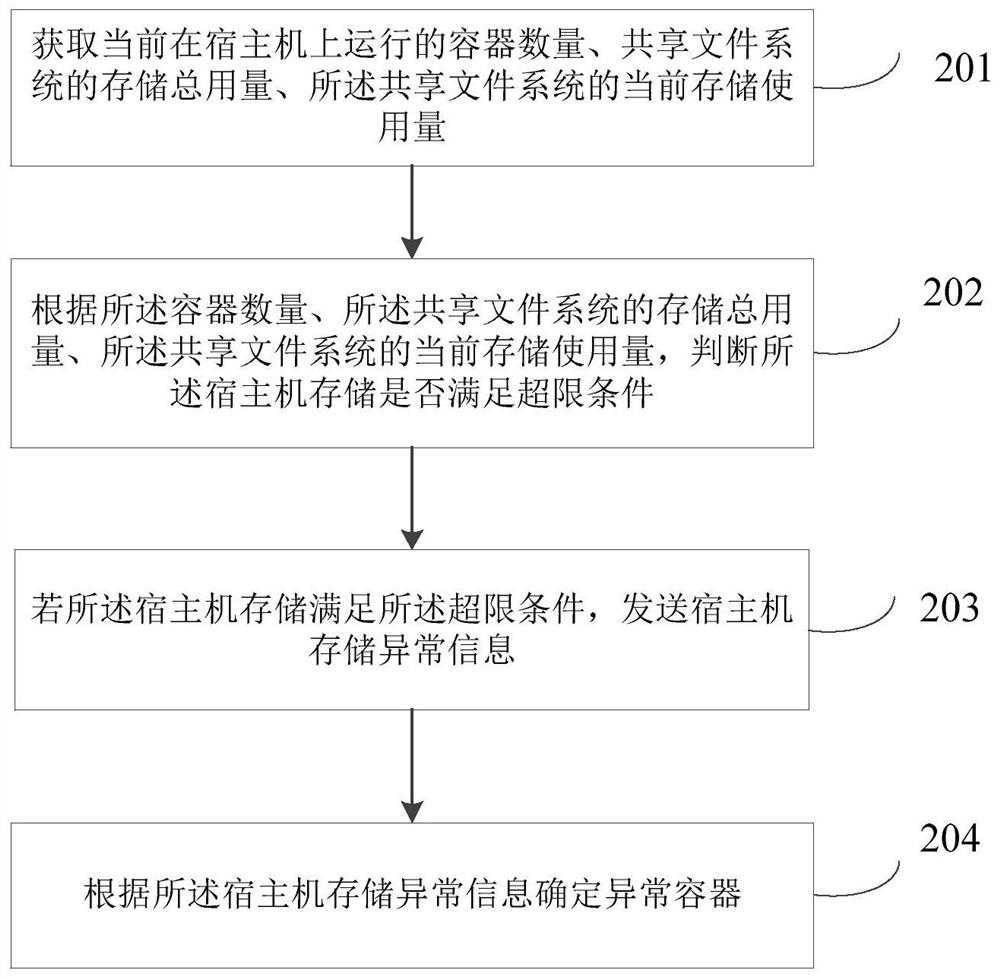
PendingCN113608963AReduce the impact of input and outputImprove experienceResource allocationHardware monitoringComputer hardwareFile system
The invention relates to the technical field of information security, is suitable for the financial field, and particularly relates to a container storage utilization rate monitoring method and device, computer equipment and a storage medium. The method comprises the steps of obtaining the number of containers currently running on a host machine, the total storage usage amount of a shared file system and the current storage usage amount of the shared file system; according to the number of the containers, the total storage usage amount of the shared file system and the current storage usage amount of the shared file system, judging whether the storage of the host machine meets an over-limit condition or not; if the host machine storage meets the over-limit condition, sending host machine storage exception information; and determining an abnormal container according to the host machine storage abnormal information. According to the method, the storage resource utilization rate of the shared file system is calculated through the cluster monitoring system, an alarm is given to the container exceeding the storage upper limit threshold value, the disk input and output influence caused by full-disk scanning is accurately and effectively reduced, the service efficiency is improved, and the user experience is further optimized.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
A network extraction method for shared bicycle skeleton
ActiveCN110798802BGuaranteed stabilityRestoring Basic Topology PropertiesParticular environment based servicesNetwork topologiesEngineeringComputation sharing
The invention discloses a shared bicycle skeleton network extraction method, belongs to the technical field of computer application, and can perform backbone network extraction on a network composed of network nodes with spatial position features. The method comprises the following steps: constructing a shared bicycle network; and calculating the significance of all edges in the shared bicycle network, and keeping the edges with the significance greater than zero as the edges of the backbone network; and calculating the topological potential of all nodes in the shared bicycle network; performing spatial density clustering on all nodes in the shared bicycle network according to the geographic positions of the nodes, and acquiring a riding area cluster ; For each riding area cluster, performing descending sorting on the network nodes in the current riding area cluster according to the value of the topological potential, and selecting the front set number of nodes after descending sortingto form a backbone core node of the current riding area cluster; and combining the backbone core nodes of all the riding area clusters, and connecting the backbone core nodes by using the edges of the backbone network to form a skeleton network.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
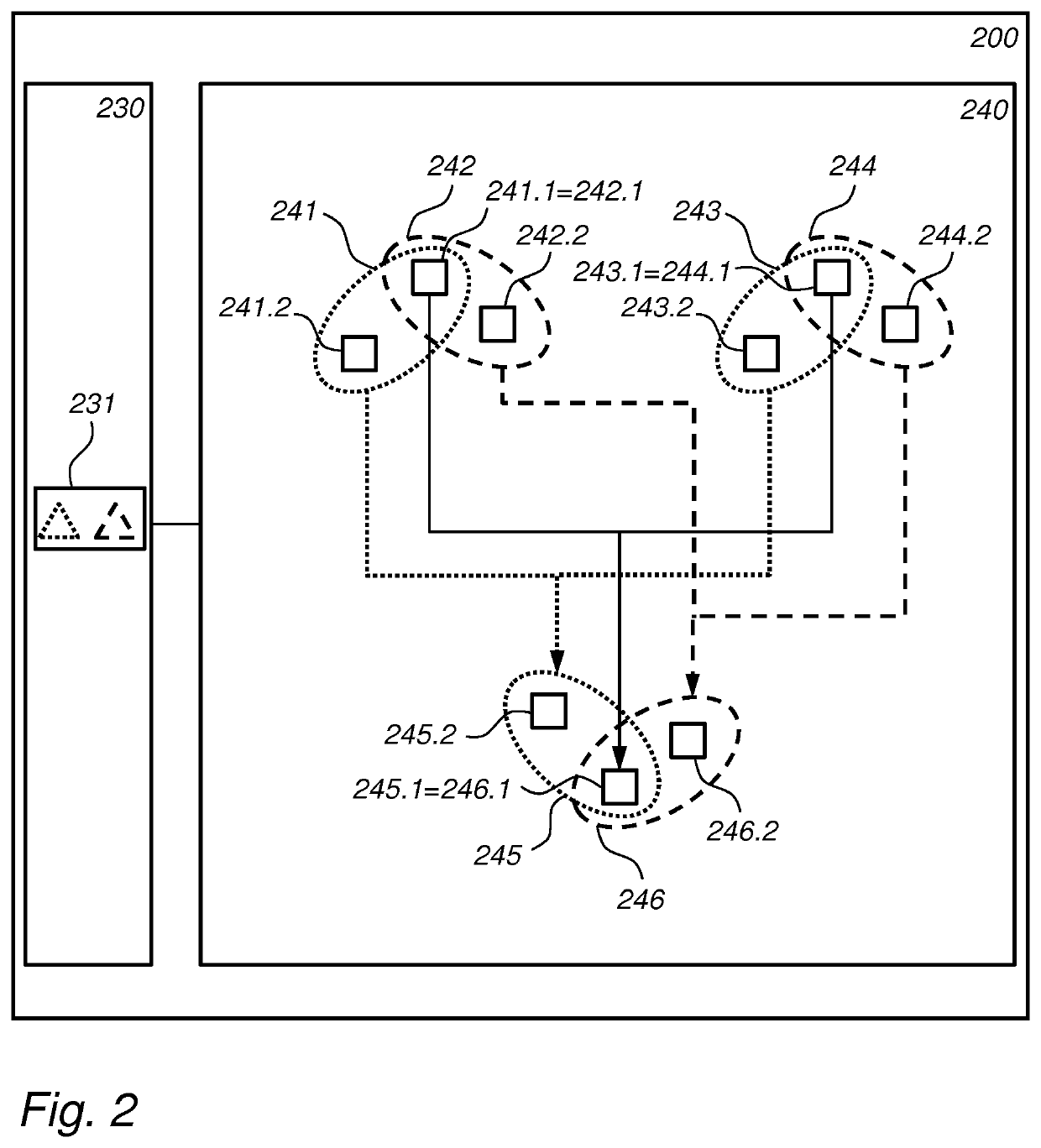
A computation device using shared shares
PendingUS20210367766A1Increase unpredictabilityNot easy to attackKey distribution for secure communicationEncryption apparatus with shift registers/memoriesParallel computingComputer engineering
Owner:KONINKLJIJKE PHILIPS NV
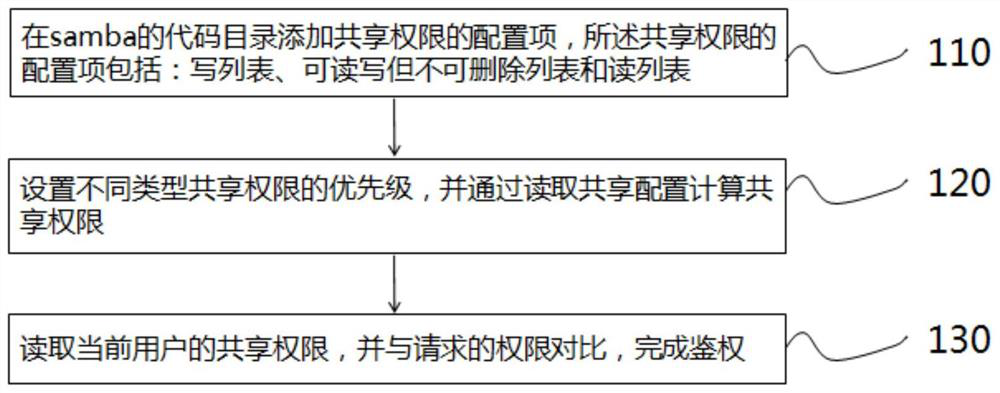
Samba sharing permission authentication method and system, terminal and storage medium
PendingCN113282953ARealize read and writeMake up for the lack of shared authority authenticationDigital data protectionConfiguration itemEngineering
The invention provides a samba sharing permission authentication method and system, a terminal and a storage medium, and the method comprises the steps: adding a sharing permission configuration item in a code directory of samba, the sharing permission configuration item comprising a write list, a readable-writable but non-deletable list and a read list; setting priorities of different types of sharing permissions, and calculating the sharing permissions by reading the sharing configuration; and reading the shared authority of the current user, and comparing the shared authority with the requested authority to complete authentication. The invention provides a method for efficiently realizing read-write but non-deletable permission control by adding a new shared permission type in samba.
Owner:SHANDONG YINGXIN COMP TECH CO LTD
Ecological biological recognition method based on R-FCN algorithm
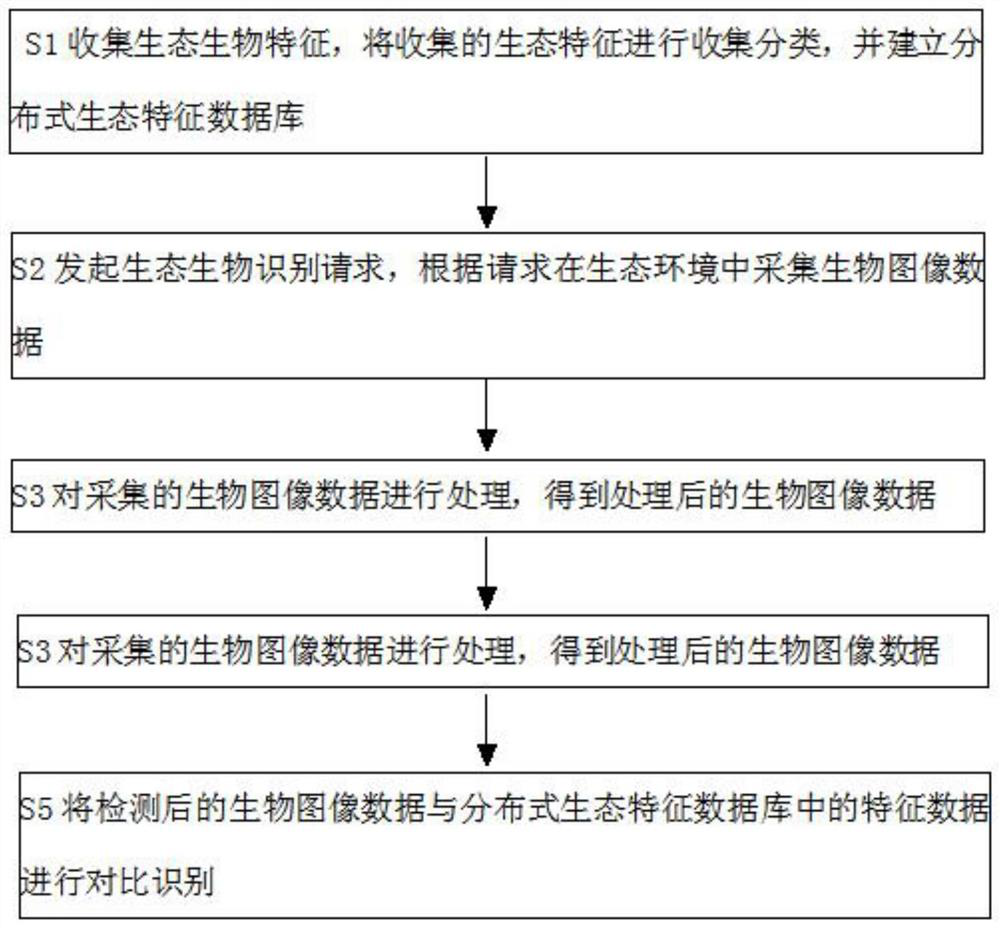
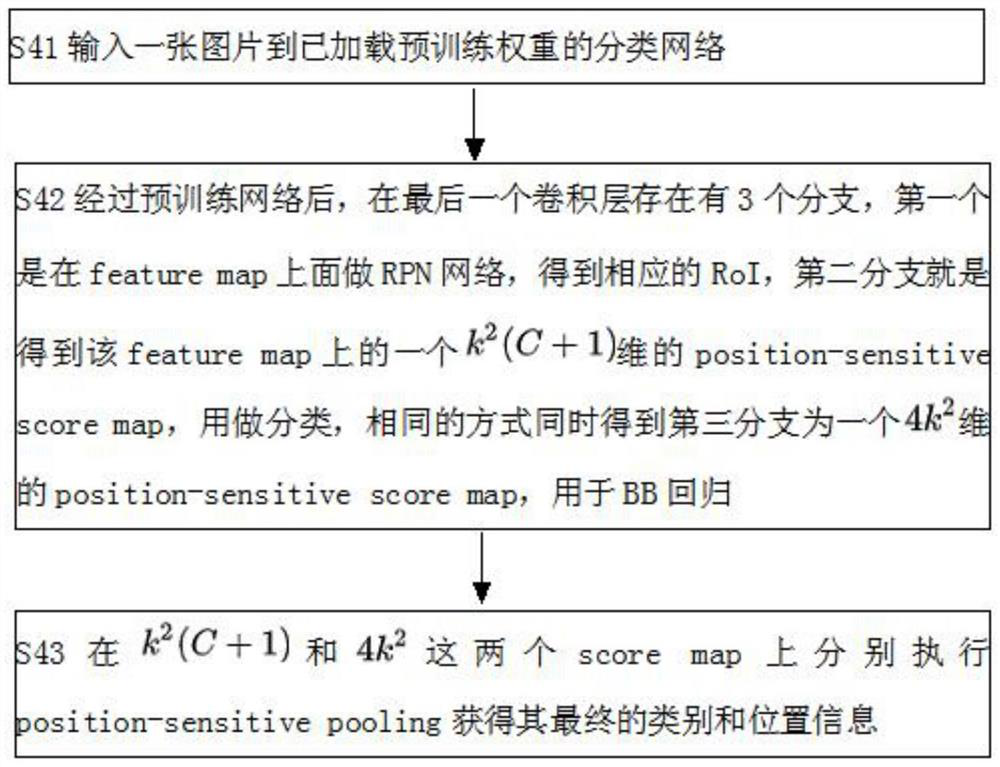
PendingCN114581937ARealize computing sharingAnalyzing displacement sensitivityGeneral water supply conservationCharacter and pattern recognitionEcologyComputation sharing
The invention discloses an ecological biological recognition method based on an R-FCN algorithm, and the method comprises the following steps: collecting ecological biological characteristics, carrying out the collection and classification of the collected ecological characteristics, and building a distributed ecological characteristic database; initiating an ecological biological recognition request, and collecting biological image data in the ecological environment according to the request; processing the acquired biological image data to obtain processed biological image data; performing target detection on the processed biological image data through an R-FCN algorithm; and carrying out comparison identification on the detected biological image data and the feature data in the distributed ecological feature database. According to the method, the full convolution network is used, complete calculation sharing is achieved, the speed is 2.5-20 times higher than that of the Faster R-CNN and reaches 0.17 s / img, the accuracy is slightly improved under the condition of speed advantage compared with that of the Faster R-CNN, the displacement sensitivity of classification and detection is analyzed, and a solution is provided.
Owner:澜途集思(深圳)数字科技有限公司
Key exchange devices and methods
ActiveUS11070367B2Reduce communicationReduce computationKey distribution for secure communicationKey exchangeComputer network
Owner:KONINKLJIJKE PHILIPS NV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com